Session 2 Core Infrastructure Design Andrew Hill Consultant











- Slides: 36

Session 2: Core Infrastructure Design Andrew Hill – Consultant Rob Lowe – Consultant MCS Talks Infrastructure Architecture

Live Meeting Information. . . Feedback Panel Questions & Answers Blog - http: //blogs. technet. com/MCSTalks

Session 2: Core Infrastructure Design Andrew Hill – Consultant Rob Lowe – Consultant MCS Talks Infrastructure Architecture

Purpose: To provide design guidance for Microsoft Windows Server 2008 Active Directory Agenda Determine process for Active Directory design Assist designers in the decision-making process Provide design assistance based on bestpractice and real-world experience

Active Directory Design Overview Forest and domain design Organizational Units (OUs) Group Policy Objects (GPOs) Security Groups Domain Controller Placement (inc. RODC) Sites Topology Domain Controller Configuration DNS

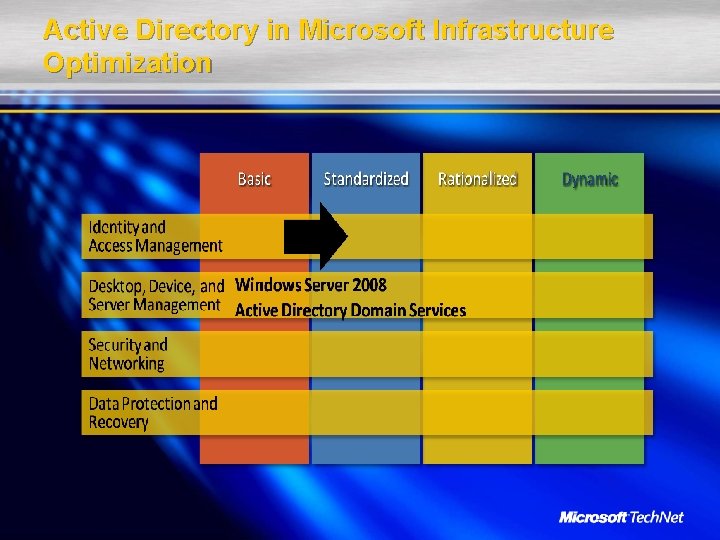
Active Directory in Microsoft Infrastructure Optimization

Tips for the Planning Process Considerations at each design phase Complexity Cost Fault Tolerance Performance Scalability Security

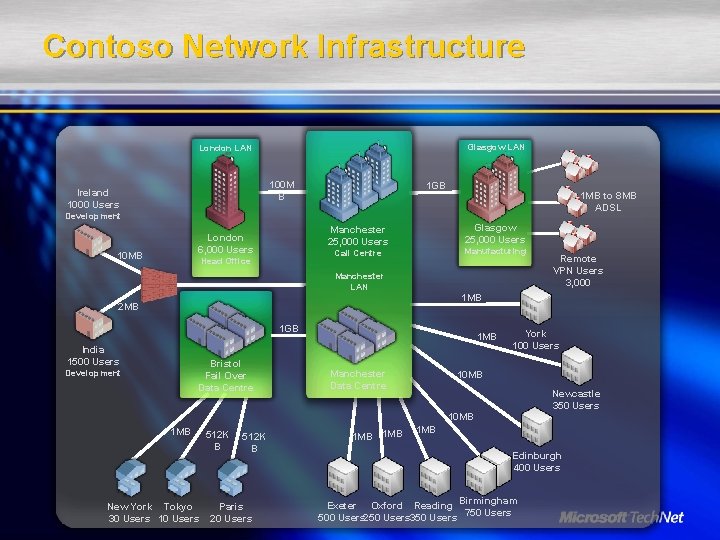
Contoso Network Infrastructure Glasgow LAN London LAN 100 M B Ireland 1000 Users 1 GB 1 MB to 8 MB ADSL Development 10 MB Glasgow 25, 000 Users Manchester 25, 000 Users London 6, 000 Users Manufacturing Call Centre Head Office Manchester LAN 1 MB 2 MB 1 GB India 1500 Users Bristol Fail Over Data Centre Development 1 MB Manchester Data Centre York 100 Users 10 MB Newcastle 350 Users 10 MB 1 MB New York Tokyo 30 Users 10 Users 512 K B Paris 20 Users 1 MB Remote VPN Users 3, 000 1 MB Edinburgh 400 Users Exeter Oxford Reading Birmingham 500 Users 250 Users 350 Users 750 Users

Determine the Number of Forests How Many Forests? Option 1: Single Forest Option 2: Multiple Forests Multiple Forest Drivers Multiple Schemas Resource Forests Forest Administrator Distrust Legal Regulations for Application or Data Access Requirements to be disconnected for long periods (e. g. Military)

Single Organizational Forest Model Users Workstations Applications Exchange Share. Point

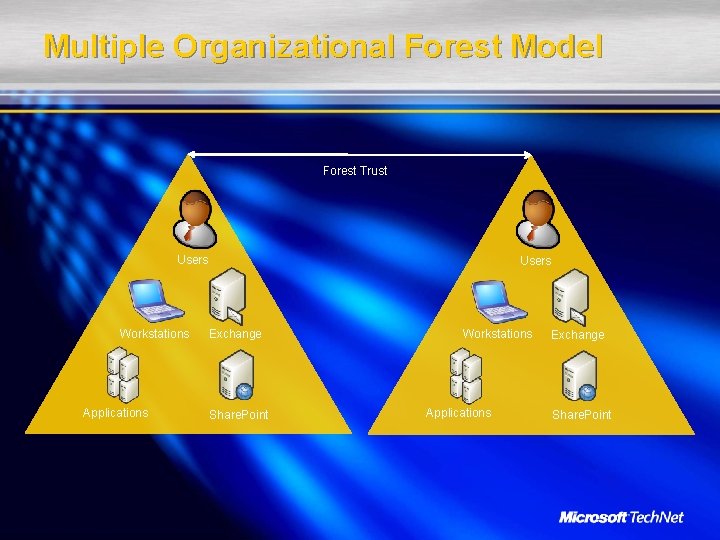
Multiple Organizational Forest Model Forest Trust Users Workstations Applications Users Exchange Share. Point Workstations Applications Exchange Share. Point

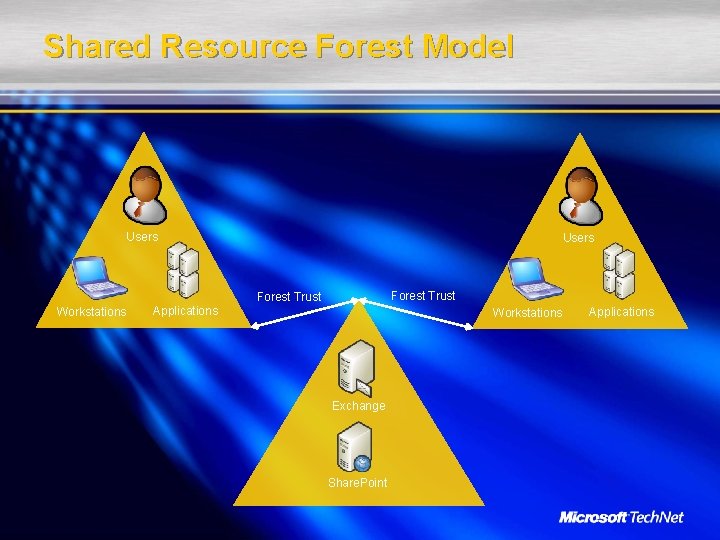
Shared Resource Forest Model Users Forest Trust Workstations Applications Workstations Exchange Share. Point Applications

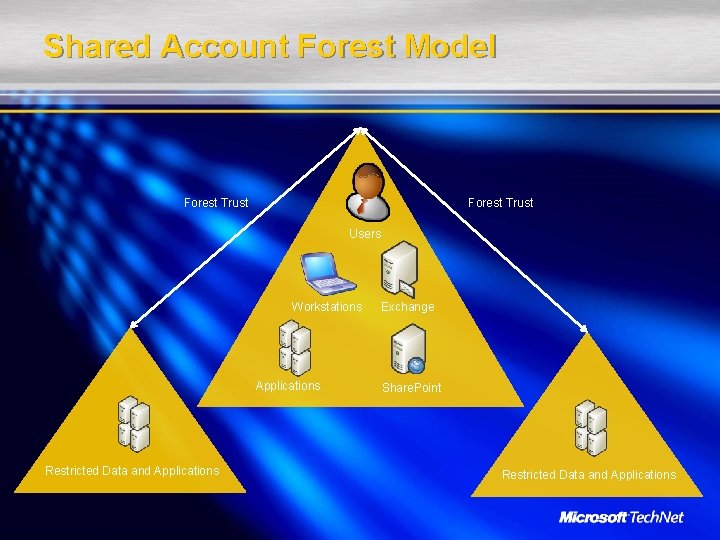
Shared Account Forest Model Forest Trust Users Workstations Applications Restricted Data and Applications Exchange Share. Point Restricted Data and Applications

Determine the Number of Domains How many Domains? Option 1: Single Domain Option 2: Multiple Domains Multiple Domain drivers Large number of frequently changing attributes Reduced replication traffic Control replication traffic over slow links Preserve legacy active directory

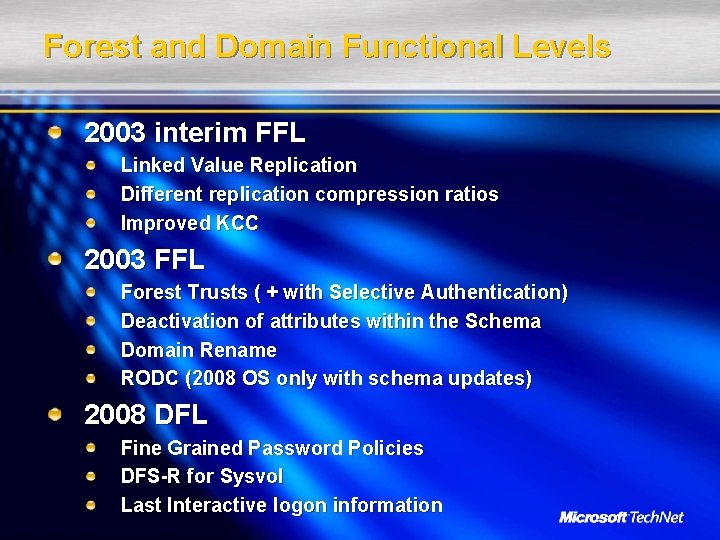
Forest and Domain Functional Levels 2003 interim FFL Linked Value Replication Different replication compression ratios Improved KCC 2003 FFL Forest Trusts ( + with Selective Authentication) Deactivation of attributes within the Schema Domain Rename RODC (2008 OS only with schema updates) 2008 DFL Fine Grained Password Policies DFS-R for Sysvol Last Interactive logon information

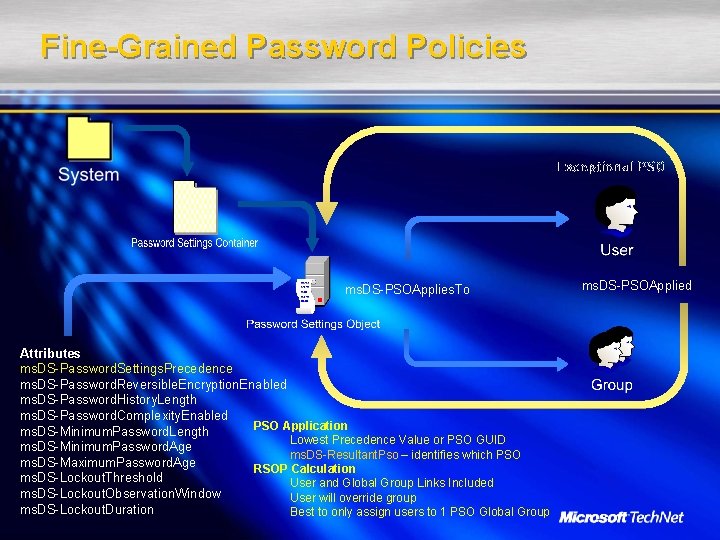
Fine-Grained Password Policies Exceptional PSO ms. DS-PSOApplies. To Attributes ms. DS-Password. Settings. Precedence ms. DS-Password. Reversible. Encryption. Enabled ms. DS-Password. History. Length ms. DS-Password. Complexity. Enabled PSO Application ms. DS-Minimum. Password. Length Lowest Precedence Value or PSO GUID ms. DS-Minimum. Password. Age ms. DS-Resultant. Pso – identifies which PSO ms. DS-Maximum. Password. Age RSOP Calculation ms. DS-Lockout. Threshold User and Global Group Links Included ms. DS-Lockout. Observation. Window User will override group ms. DS-Lockout. Duration Best to only assign users to 1 PSO Global Group ms. DS-PSOApplied

Assign Domain Names Assign the Net. BIOS Name Maximum effective length of 15 characters Use a Net. BIOS name that is unique across organisation Assign DNS Name Ensure uniqueness by not duplicating existing registered Internet domain names Register all domain names with Internic Name should not represent business unit or division Avoid usingle-label names

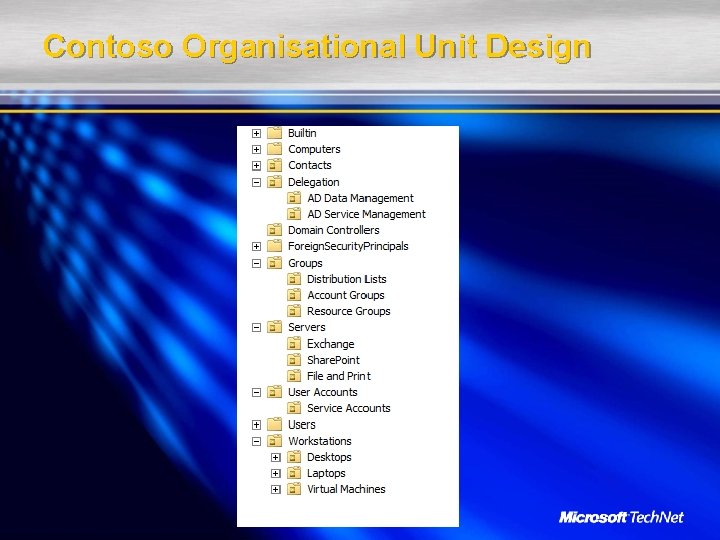
Organisational Units Choose an OU Design: Task 1: Design OU Configuration for Delegation of Administration Task 2: Design OU Configuration for Group Policy Application Other OU (and container) related recommended practices Do not move DCs out of the Domain Controllers OU Do not move built-in users and groups from users container OUs and child objects now protected from accidental deletion by default in 2008

Contoso Organisational Unit Design

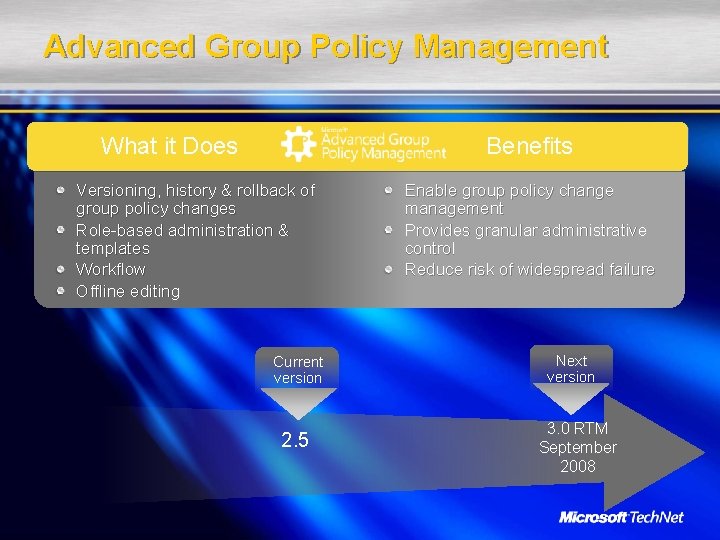
Group Policy Objects Very powerful, but consider management of group policies in design Best practices Specify user and computer settings in separate GPOs Use many small GPOs with few settings each rather than fewer large GPOs with many settings Make GPO descriptive for its purpose Do not unlink Default Domain and DDC policies Advanced Group Policy Management Change Control Workflow V 3. 0 (2008) increases granular permissions

Advanced Group Policy Management Benefits What it Does Versioning, history & rollback of group policy changes Role-based administration & templates Workflow Offline editing Current version 2. 5 Enable group policy change management Provides granular administrative control Reduce risk of widespread failure Next version 3. 0 RTM September 2008

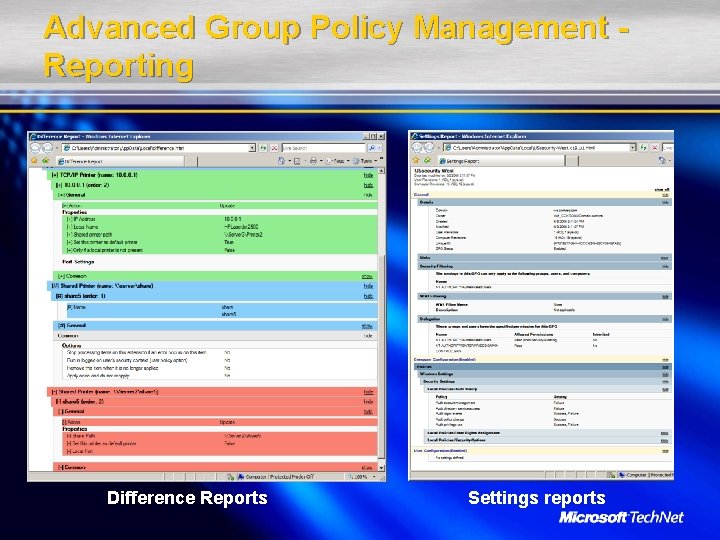
Advanced Group Policy Management Reporting Difference Reports Settings reports

Group Policy Preferences

Security Groups Group Scope Account groups – for group users and computers Global Universal Resource groups – for controlling rights and permissions Domain Local Built-in Local Complex Group nesting makes audit and reconciliation more difficult

Domain Controller Placement of the Domain Controllers: Hub Locations Satellite (Branch) Locations Heavily dictated by network and application requirements Global Catalog (GC) Very few reasons now not to make all DCs a GC Read-Only Domain Controllers New in Windows Server 2008 (Read-Only AD and no passwords) Primarily a security feature to mitigate against high risk sites

RODC Deployment Consider the following: Application needs – Exchange? Applications make Write / Read back calls? Site topology – BASL turned off? Password Replication Policy – which model for you? Remember no cached accounts means more WAN / HUB DC impact Cache computer and User accounts Deployment: Start with min 2 x 2008 RW Hub DCs Add 2008 RWDC to NS records (for RSO) Delegate deployment – don’t use Domain Admins

Create the Site Design Option 1: create a logical site for each physical location Assign subnets for each physical location to corresponding site Site coverage Option 2: create a logical site only for physical locations with domain controllers Assign subnets for each physical location to most appropriate site depending on underlying network

Create a Site Link Design Site links map to underlying network Set cost and schedule Bridge all site links (on by default) Appropriate if network is fully routable (all domain controllers can communicate with all other domain controllers) Generally not recommended for Branch Office – KCC overheads Use Repadmin /siteoptions to disable! Custom Site Link Bridges Use when the network is not fully routed, e. g. when network firewalls restrict communications between domain controllers

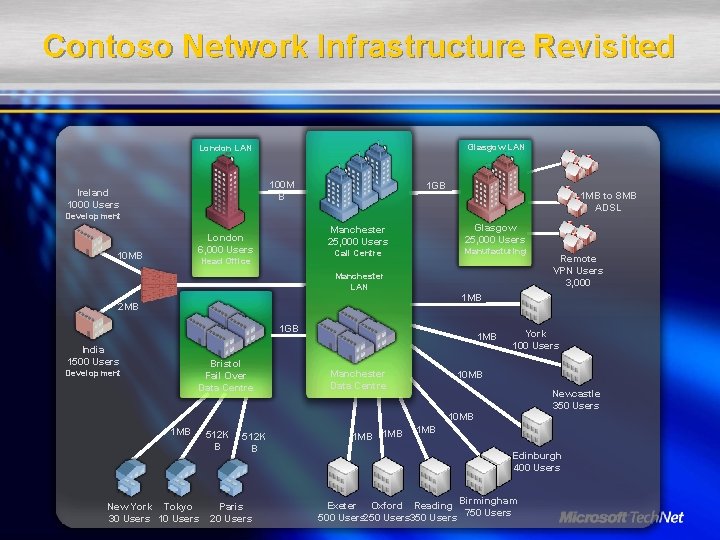
Contoso Network Infrastructure Revisited Glasgow LAN London LAN 100 M B Ireland 1000 Users 1 GB 1 MB to 8 MB ADSL Development 10 MB Glasgow 25, 000 Users Manchester 25, 000 Users London 6, 000 Users Manufacturing Call Centre Head Office Manchester LAN 1 MB 2 MB 1 GB India 1500 Users Bristol Fail Over Data Centre Development 1 MB Manchester Data Centre York 100 Users 10 MB Newcastle 350 Users 10 MB 1 MB New York Tokyo 30 Users 10 Users 512 K B Paris 20 Users 1 MB Remote VPN Users 3, 000 1 MB Edinburgh 400 Users Exeter Oxford Reading Birmingham 500 Users 250 Users 350 Users 750 Users

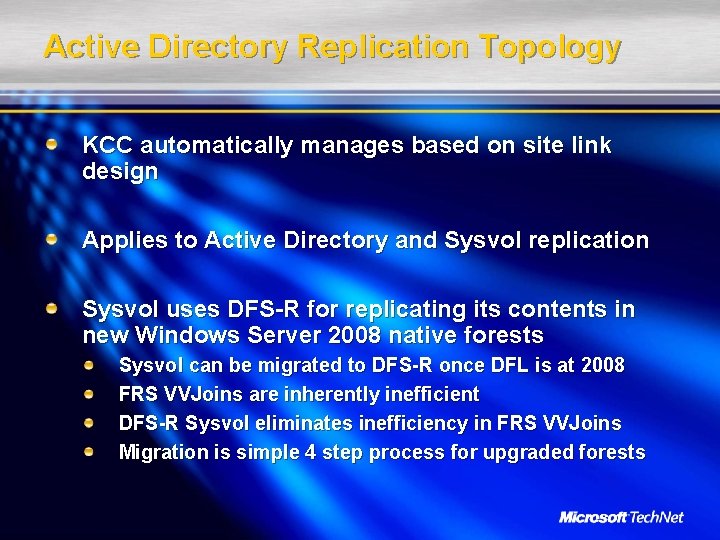
Active Directory Replication Topology KCC automatically manages based on site link design Applies to Active Directory and Sysvol replication Sysvol uses DFS-R for replicating its contents in new Windows Server 2008 native forests Sysvol can be migrated to DFS-R once DFL is at 2008 FRS VVJoins are inherently inefficient DFS-R Sysvol eliminates inefficiency in FRS VVJoins Migration is simple 4 step process for upgraded forests

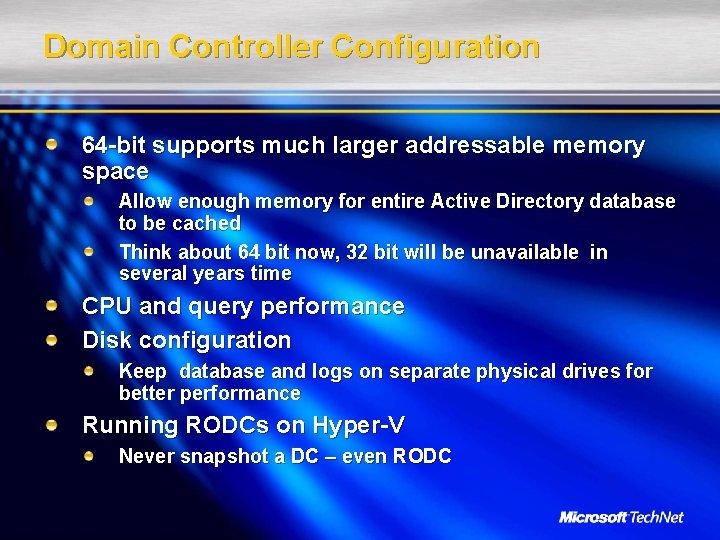
Domain Controller Configuration 64 -bit supports much larger addressable memory space Allow enough memory for entire Active Directory database to be cached Think about 64 bit now, 32 bit will be unavailable in several years time CPU and query performance Disk configuration Keep database and logs on separate physical drives for better performance Running RODCs on Hyper-V Never snapshot a DC – even RODC

DNS Critical for Active Directory AD-integrated DNS recommended Consider Forwarding model Root hints can introduce additional management overhead. Forwarding is recommended approach for AD New in Windows Server 2008 Storage of Conditional Forwarding settings in Active Directory

What’s Next? Discuss, Rinse, Repeat Implement your design Test and refine design along the way

Summary and Conclusion Organizations should base the design of their Active Directory infrastructure on business and technical requirements Considerations should include: The scope of the network and environment Technical requirements and considerations Additional business requirements Designing an Active Directory infrastructure to meet these requirements Validating the overall approach

Questions and Answers Please enter your questions using the Q&A panel for the presenters!

Thank you for attending this Tech. Net Event Find these slides at: http: //www. microsoft. com/uk/technetslides Visit our blog at: http: //blogs. technet. com/mcstalks Register for the next session, Messaging, at: http: //msevents. microsoft. com/CUI/Event. Detail. aspx? Event. I D=1032386416&Culture=en-GB Please fill out your evaluations!