SERVICES TCP 22 Protocoles ARP RARP Protocole ARP































![Exec Commands Show active translations show ip nat translations [ verbose ] Show translation Exec Commands Show active translations show ip nat translations [ verbose ] Show translation](https://slidetodoc.com/presentation_image_h/f47d01ae8ed71fdfe2278f0507bd90bb/image-58.jpg)
![Debugging debug ip nat [ <list> ] [ detailed ] Debugging debug ip nat [ <list> ] [ detailed ]](https://slidetodoc.com/presentation_image_h/f47d01ae8ed71fdfe2278f0507bd90bb/image-59.jpg)














- Slides: 108

SERVICES TCP (2/2)

Protocoles ARP / RARP

Protocole ARP • Address Resolution Protocol - RFC 826 – Permet de résoudre l'adresse physique d'une machine à partir de son adresse logique (IP) – Principe de fonctionnement : • A souhaite dialoguer avec B via un réseau (Ethernet par exemple) • A ne connaît pas l'adresse Ethernet de B, mais son adresse IP • A envoie une requête ARP en diffusion sur le réseau • B transmet son adresse Ethernet dans une réponse ARP • A conserve cette adresse en mémoire dans une table ARP (prévoir un temporisateur de validité des données pour s'assurer de l'existence des stations)

Protocole ARP • Address Resolution Protocol - RFC 826 – Evite d'avoir une base de données (couple d'adresses) centrale – Les requêtes ARP restent locales (non transmises par les routeurs) – ARP est un protocole de résolution d'adresse ouvert ; il n'est pas restreint à la résolution des adresses Ethernet et IP – Le datagramme ARP est transporté avec un champ type Ethernet 0806

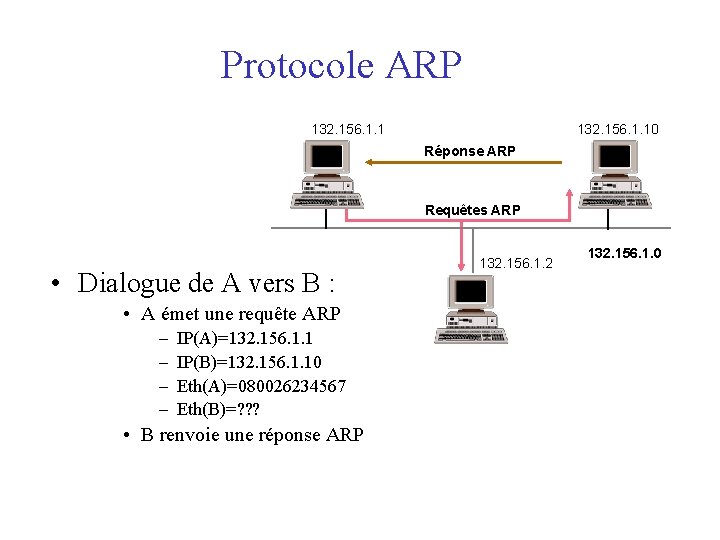
Protocole ARP 132. 156. 1. 1 A 132. 156. 1. 10 Réponse ARP B Requêtes ARP • Dialogue de A vers B : • A émet une requête ARP – – IP(A)=132. 156. 1. 1 IP(B)=132. 156. 1. 10 Eth(A)=080026234567 Eth(B)=? ? ? • B renvoie une réponse ARP 132. 156. 1. 2 C 132. 156. 1. 0

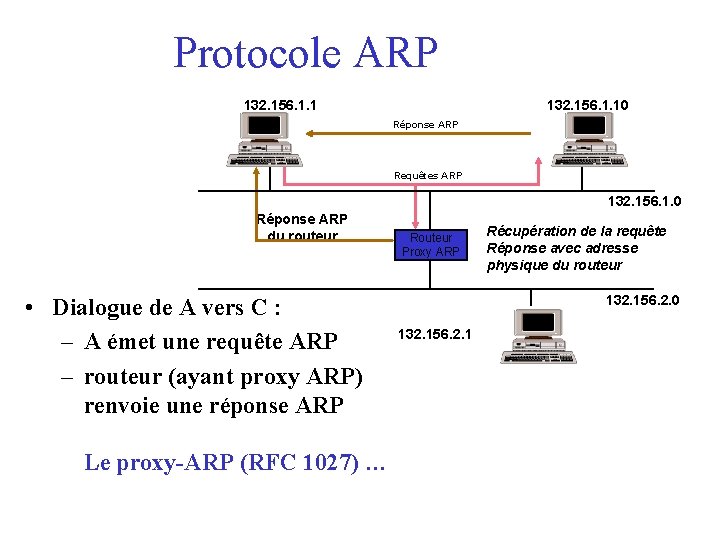
Protocole ARP 132. 156. 1. 1 A 132. 156. 1. 10 B Réponse ARP Requêtes ARP 132. 156. 1. 0 Réponse ARP du routeur • Dialogue de A vers C : – A émet une requête ARP – routeur (ayant proxy ARP) renvoie une réponse ARP Le proxy-ARP (RFC 1027) … Routeur Proxy ARP Récupération de la requête Réponse avec adresse physique du routeur 132. 156. 2. 0 132. 156. 2. 1 C

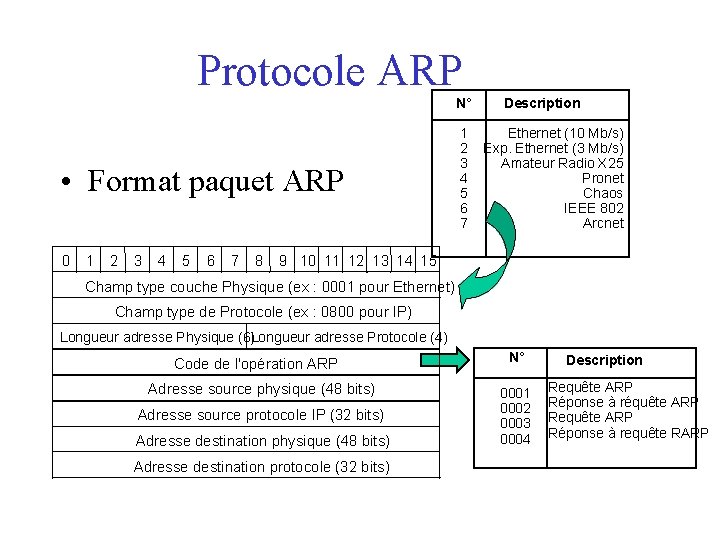
Protocole ARP N° • Format paquet ARP 0 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 Description Ethernet (10 Mb/s) Exp. Ethernet (3 Mb/s) Amateur Radio X 25 Pronet Chaos IEEE 802 Arcnet 9 10 11 12 13 14 15 Champ type couche Physique (ex : 0001 pour Ethernet) Champ type de Protocole (ex : 0800 pour IP) Longueur adresse Physique (6)Longueur adresse Protocole (4) Code de l'opération ARP Adresse source physique (48 bits) Adresse source protocole IP (32 bits) Adresse destination physique (48 bits) Adresse destination protocole (32 bits) N° 0001 0002 0003 0004 Description Requête ARP Réponse à réquête ARP Requête ARP Réponse à requête RARP

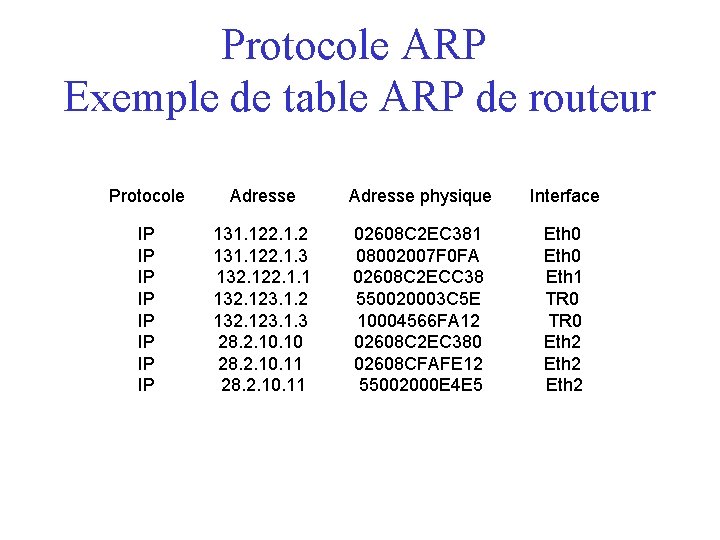
Protocole ARP Exemple de table ARP de routeur Protocole Adresse physique Interface IP IP 131. 122. 1. 2 131. 122. 1. 3 132. 122. 1. 1 132. 123. 1. 2 132. 123. 1. 3 28. 2. 10. 11 02608 C 2 EC 381 08002007 F 0 FA 02608 C 2 ECC 38 550020003 C 5 E 10004566 FA 12 02608 C 2 EC 380 02608 CFAFE 12 55002000 E 4 E 5 Eth 0 Eth 1 TR 0 Eth 2

Cas du Proxy ARP: fonction intégrée de base à un routeur

DHCP

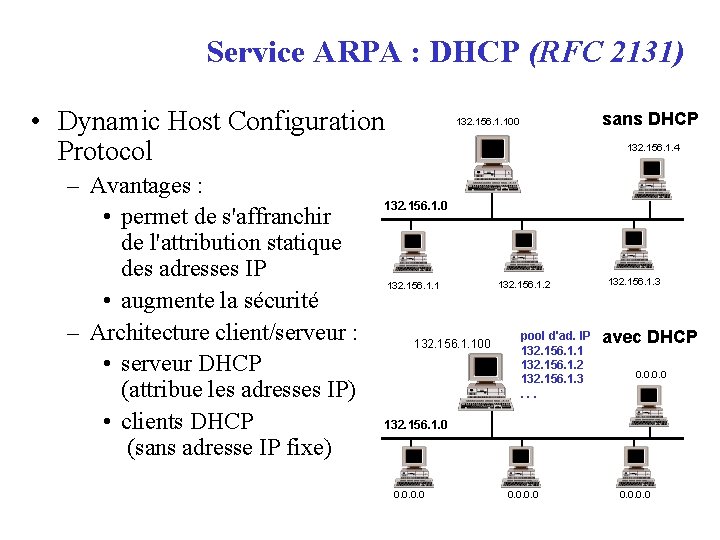
Service ARPA : DHCP (RFC 2131) • Dynamic Host Configuration Protocol – Avantages : • permet de s'affranchir de l'attribution statique des adresses IP • augmente la sécurité – Architecture client/serveur : • serveur DHCP (attribue les adresses IP) • clients DHCP (sans adresse IP fixe) sans DHCP 132. 156. 1. 100 S 132. 156. 1. 4 D 132. 156. 1. 0 A B C 132. 156. 1. 1 132. 156. 1. 2 132. 156. 1. 3 132. 156. 1. 100 S pool d'ad. IP 132. 156. 1. 1 132. 156. 1. 2 132. 156. 1. 3. . . avec DHCP 0. 0 D 132. 156. 1. 0 A 0. 0 B C 0. 0

• Le protocole BOOTP permet aux clients sans disque de démarrer et de configurer automatiquement TCP/IP. Le protocole DHCP (Dynamic Host Configuration Protocol) constitue une extension de BOOTP. Il centralise et gère l’attribution des informations de configuration TCP/IP en affectant automatiquement des adresses IP à des ordinateurs configurés pour utiliser DHCP. • Un serveur DHCP donne les informations suivantes à son client : 1 Une @ IP 2 Un masque de sous-réseau 3 Une adresse de passerelle par défaut, une adresse DNS et une adresse WINS.

– Fonctionnement • Un serveur DHCP configure son client grâce à un processus en quatre phases : 1 Demande de bail (DHCPDISCOVER). En effet, le poste client va demander une adresse IP au()x serveur(s) en utilisant 0. 0 comme adresse source et 255 comme adresse de destination. 2 Proposition de bail (DHCPOFFER). Le serveur DHCP va envoyer une proposition au client (@ IP, durée de bail, @ matérielle du client, masque et @ IP du serveur DHCP). 3 Sélection de bail (DHCPREQUEST). Le client va accepter la première proposition qu’il a reçu en informant les autres serveurs DHCP de sa sélection.

4 Accusé de réception du bail IP (DHCPACK). Le serveur DHCP va envoyer au client un accusé de réception validant le bail. Il se peut que le serveur DHCP renvoie le message DHCPNACK pour confirmer la non conclusion du bail. – Une adresse IP proposé par un serveur DHCP a une durée de vie limitée appelé bail. Lorsque le client aura atteint 50% de sa durée, il envoiera un DHCPREQUEST à son serveur DHCP afin de le renouveler.

·Lorsqu’on rallume l’ordinateur, celui-ci a gardé, dans son registre, son @ IP. Il envoie un message au serveur DHCP demandant s’il peut réutiliser cette @. ·Si un réseau d’entreprise est en formé de sousréseaux, il faut que les routeurs agissent en tant qu’agents de relais DHCP. ·Si les routeurs ne sont pas des agents de relais, alors il faut un serveur DHCP sur chaque sousréseau.

– Installation • Un service DHCP s’installe sur un serveur Windows ou UNIX Il a besoin d’une @ IP statique, d’un masque de sous-réseau, et d’une étendue DHCP. • Attention, certains serveurs sensibles ont besoin d’une @ IP statique tel que le PDC. – Commandes (sur MS Windows) • IPCONFIG /ALL permet d’obtenir la configuration IP du système d’exploitation de l’ordinateur et de la carte réseau. • IPCONFIG /RELEASE permet la libération d’un bail. • IPCONFIG /RENEW permet la mise à jour d’un bail….

– Configuration sur un routeur Cisco • ip dhcp excluded-address 172. 16. 1. 100 172. 16. 1. 103 • ip dhcp pool 0 network 172. 16. 0. 0 /16 • domain-name cisco. com • dns-server 172. 16. 1. 102 172. 16. 2. 102 • netbios-name-server 172. 16. 1. 103 172. 16. 2. 103 • netbios-node-type h-node • default-router 172. 16. 1. 100 • lease 30 (en JJ : HH : MM ou infinite, default = 1 jour)

Service ARPA : DHCP – le format du paquet DHCP est similaire à celui de Boot. P Code (53) – Options DHCP – – – 2 Offre DHCP 3 Demande DHCP 4 Décline DHCP 5 Ack DHCP 6 Nack DHCP 7 Résilier DHCP longueur Type (1 -7)

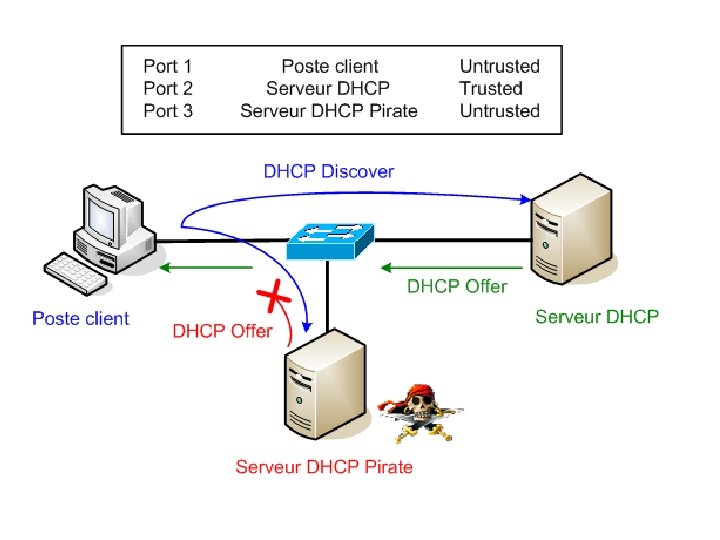
Inconvénients: Disponibilité des serveurs DHCP Sécurité (wifi, serveur non officiel)

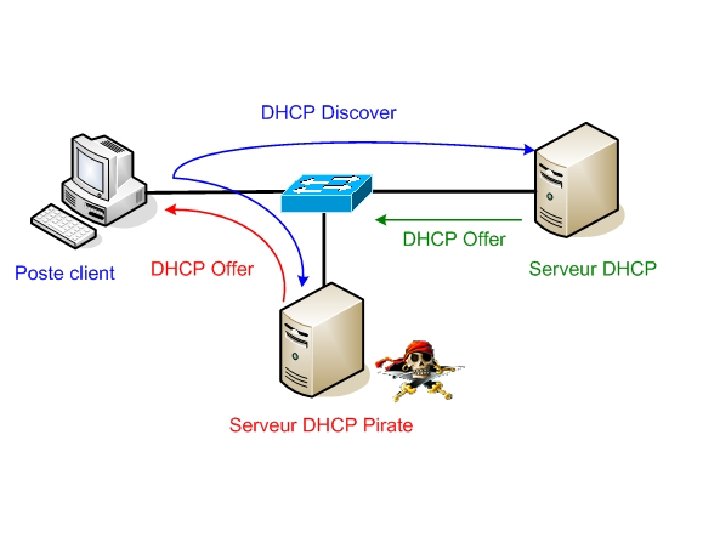
Les requêtes DHCP étant envoyées en broadcast (à tout le monde) sur le réseau, il est possible pour une personne mal intentionnée d’utiliser son propre serveur DHCP afin de diffuser des configurations malicieuses. En effet, cela est possible en laissant le serveur DHCP pirate répondre plus rapidement aux requêtes DHCP que le serveur DHCP présent sur le réseau, offrant ainsi aux utilisateurs des configurations prédéfinies et destinées à des actions malicieuses


Réseau avec DHCP Snooping Le principe de fonctionnement du DHCP Snooping est simple. Etant donné que les requêtes DHCP Offer et DHCP ACK peuvent provenir uniquement des serveurs DHCP, il suffit donc de déterminer sur les commutateurs (switchs) les ports autorisés à diffuser ces requêtes. De cette manière, seuls les ports configurés comme étant des ports de confiance (trusted port), pourrons renvoyer aux postes clients des configurations réseaux.


Class ID DHCP But: personnaliser les informations données par DHCP à chaque poste d’une même étendue

ICMP

• Protocole ICMP RFC 792, 896, 1256 – Principales caractéristiques : • protocole de report d'erreurs dans l'environnement IP • fonctionne en mode non connecté • messages ICMP acheminés par IP • fait partie obligatoirement des modules logiciels IP – Quelques utilisations : • commande "ping" • commande "traceroute"

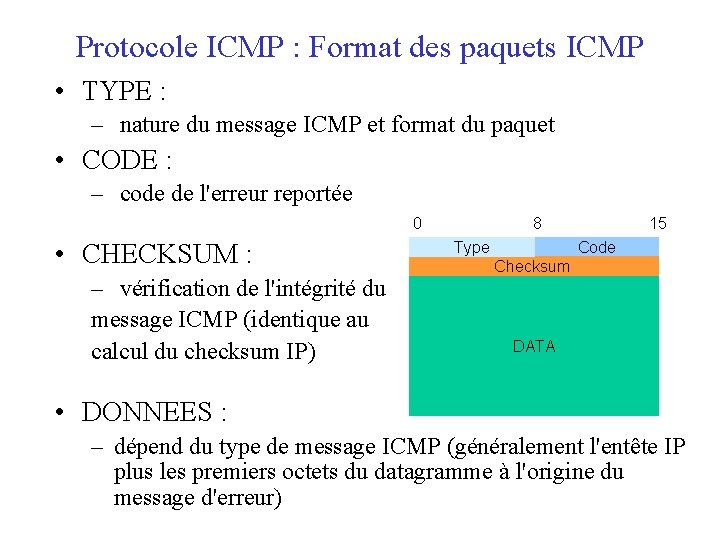
Protocole ICMP : Format des paquets ICMP • TYPE : – nature du message ICMP et format du paquet • CODE : – code de l'erreur reportée 0 • CHECKSUM : – vérification de l'intégrité du message ICMP (identique au calcul du checksum IP) 8 Type 15 Code Checksum DATA • DONNEES : – dépend du type de message ICMP (généralement l'entête IP plus les premiers octets du datagramme à l'origine du message d'erreur)

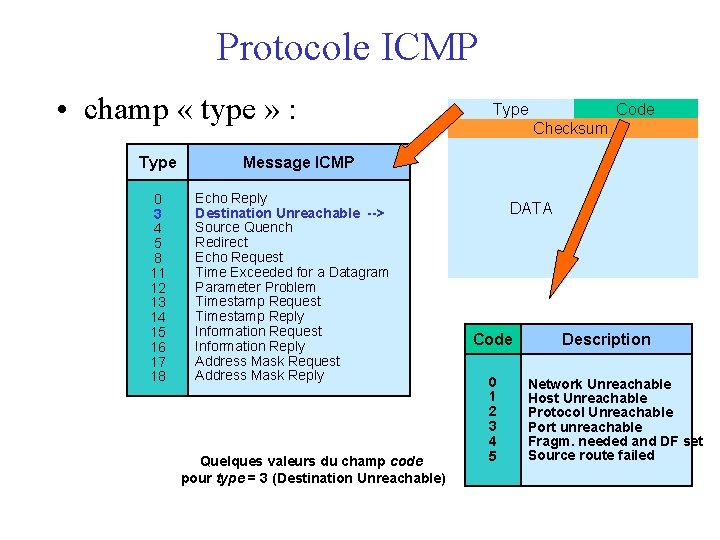
Protocole ICMP • champ « type » : Type 0 3 4 5 8 11 12 13 14 15 16 17 18 Type Code Checksum Message ICMP Echo Reply Destination Unreachable --> Source Quench Redirect Echo Request Time Exceeded for a Datagram Parameter Problem Timestamp Request Timestamp Reply Information Request Information Reply Address Mask Request Address Mask Reply Quelques valeurs du champ code pour type = 3 (Destination Unreachable) DATA Code 0 1 2 3 4 5 Description Network Unreachable Host Unreachable Protocol Unreachable Port unreachable Fragm. needed and DF set Source route failed

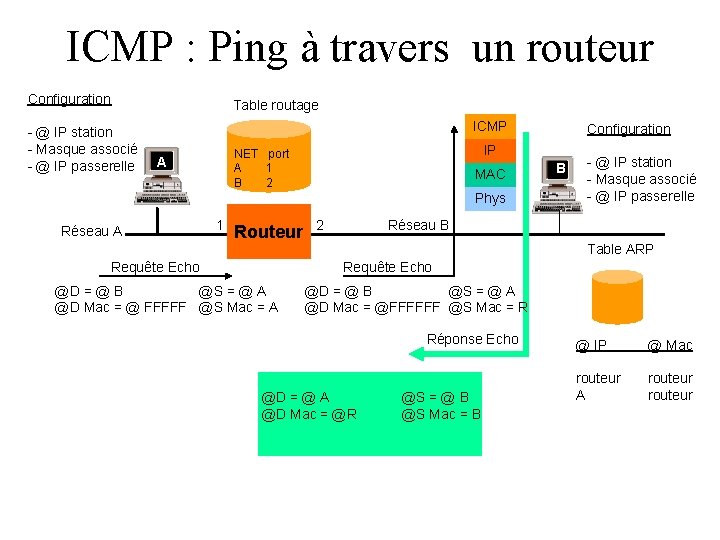
ICMP : Ping à travers un routeur Configuration - @ IP station - Masque associé - @ IP passerelle Table routage ICMP IP NET port A 1 B 2 A MAC Phys Réseau A 1 Routeur Requête Echo Configuration 2 B - @ IP station - Masque associé - @ IP passerelle Réseau B Table ARP Requête Echo @D = @ B @S = @ A @D Mac = @ FFFFF @S Mac = A @D = @ B @S = @ A @D Mac = @FFFFFF @S Mac = R Réponse Echo @D = @ A @D Mac = @R @S = @ B @S Mac = B @ IP @ Mac routeur A routeur

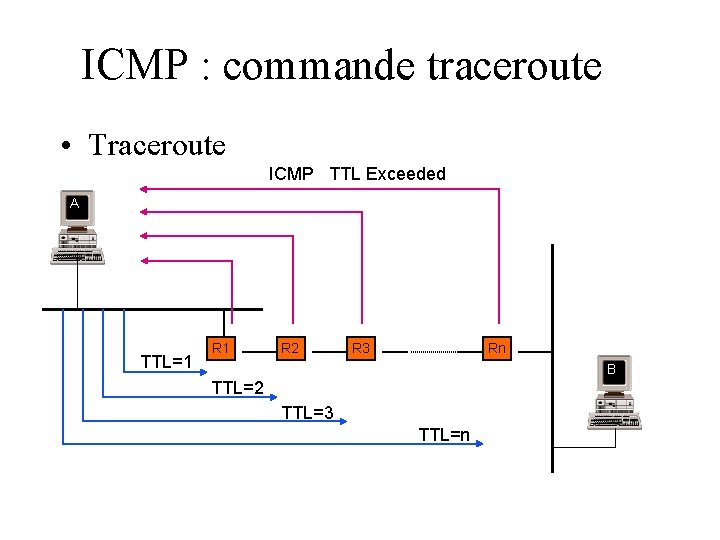
ICMP : commande traceroute • Traceroute ICMP TTL Exceeded A TTL=1 R 2 R 3 Rn B TTL=2 TTL=3 TTL=n

• Traceroute est un outil logiciel (couche applicative) : –permet d'identifier les différents noeuds (routeurs) traversés par un datagramme IP destiné à une machine distante –basé sur l'utilisation des messages ICMP de type «TTL Exceeded»

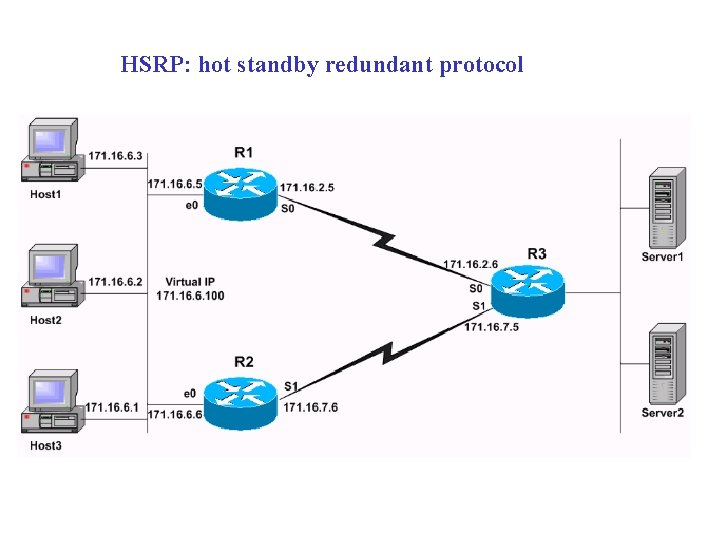
HSRP: hot standby redundant protocol

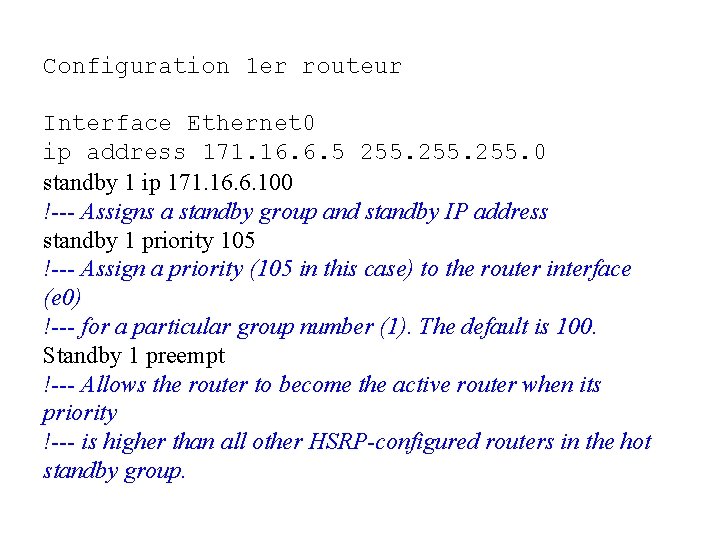
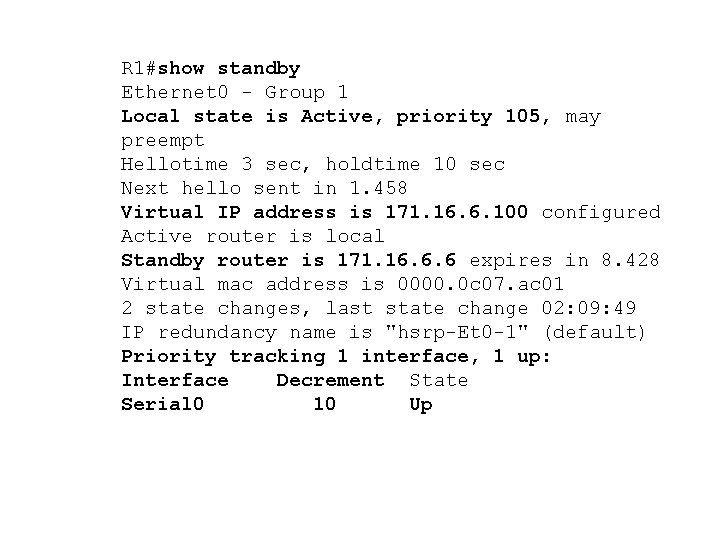
Configuration 1 er routeur Interface Ethernet 0 ip address 171. 16. 6. 5 255. 0 standby 1 ip 171. 16. 6. 100 !--- Assigns a standby group and standby IP address standby 1 priority 105 !--- Assign a priority (105 in this case) to the router interface (e 0) !--- for a particular group number (1). The default is 100. Standby 1 preempt !--- Allows the router to become the active router when its priority !--- is higher than all other HSRP-configured routers in the hot standby group.

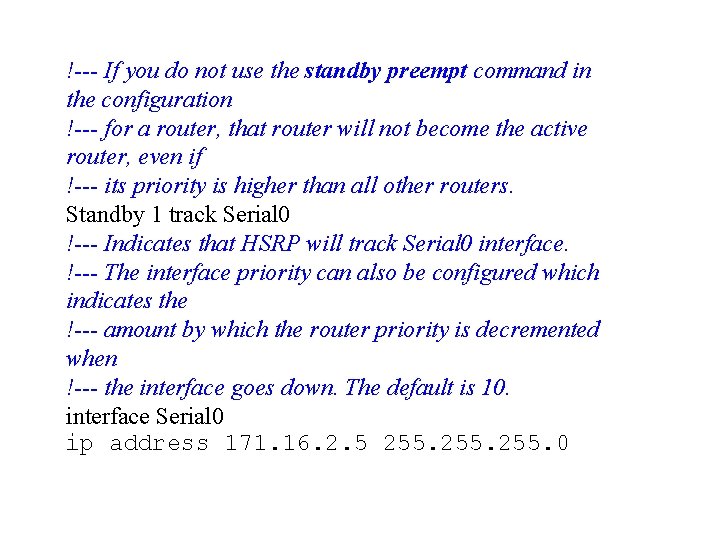
!--- If you do not use the standby preempt command in the configuration !--- for a router, that router will not become the active router, even if !--- its priority is higher than all other routers. Standby 1 track Serial 0 !--- Indicates that HSRP will track Serial 0 interface. !--- The interface priority can also be configured which indicates the !--- amount by which the router priority is decremented when !--- the interface goes down. The default is 10. interface Serial 0 ip address 171. 16. 2. 5 255. 0

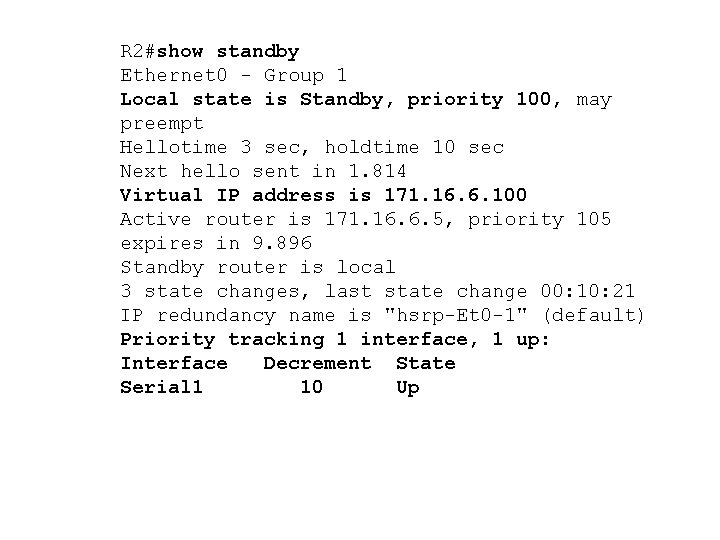
Configuration 2 nd routeur interface Ethernet 0 ip address 171. 16. 6. 6 255. 0 !--- Assigns an IP address to the interface. standby 1 ip !--- Indicates the hot standby group. Here the IP address of the virtual router !--- is not configured. See the note below. standby 1 preempt !--- Allows the router to become the active router when its priority !--- is higher than all other HSRP-configured routers in the hot standby group. !--- If you do not use the standby preempt command in the configuration !--- for a router, that router will not become the active router, even if

!--- its priority is higher than all other routers. standby 1 track Serial 1 !--- Indicates that HSRP will track Serial 1 interface. !--- The interface priority can also be configured which indicates the !--- amount by which the router priority is decremented when !--- the interface goes down. The default is 10. !--- The priority is also not configured and hence the default !--- priority value of 100 is applied. interface Serial 1 ip address 171. 16. 7. 6 255. 0

Note: R 2 does not have a standby IP address configured. This is intentional in order to demonstrate that this is a valid configuration. When R 1 and R 2 exchange HSRP hellos, R 2 learns the standby IP address from R 1. Configuring R 2 with a standby IP address (same standby address configured on R 1) is also a valid configuration.

R 1#show standby Ethernet 0 - Group 1 Local state is Active, priority 105, may preempt Hellotime 3 sec, holdtime 10 sec Next hello sent in 1. 458 Virtual IP address is 171. 16. 6. 100 configured Active router is local Standby router is 171. 16. 6. 6 expires in 8. 428 Virtual mac address is 0000. 0 c 07. ac 01 2 state changes, last state change 02: 09: 49 IP redundancy name is "hsrp-Et 0 -1" (default) Priority tracking 1 interface, 1 up: Interface Decrement State Serial 0 10 Up

R 2#show standby Ethernet 0 - Group 1 Local state is Standby, priority 100, may preempt Hellotime 3 sec, holdtime 10 sec Next hello sent in 1. 814 Virtual IP address is 171. 16. 6. 100 Active router is 171. 16. 6. 5, priority 105 expires in 9. 896 Standby router is local 3 state changes, last state change 00: 10: 21 IP redundancy name is "hsrp-Et 0 -1" (default) Priority tracking 1 interface, 1 up: Interface Decrement State Serial 1 10 Up

Translation d’adresse NAT Principes d’adressage public/privé Pénurie d’adresses officielles Sécurité RFC 1918 10. 0 - 10. 255 ( ? prefix) 172. 16. 0. 0 - 172. 31. 255 ( ? prefix) 192. 168. 0. 0 - 192. 168. 255 ( ? prefix) Discard des trames par 1 er routeur Internet traversé Solution : translation d’adresses … mais : Important : Sensibilité des applications …

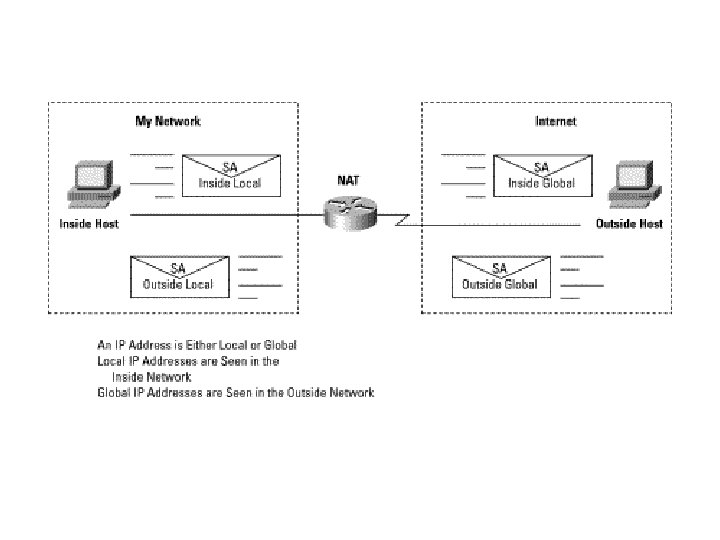
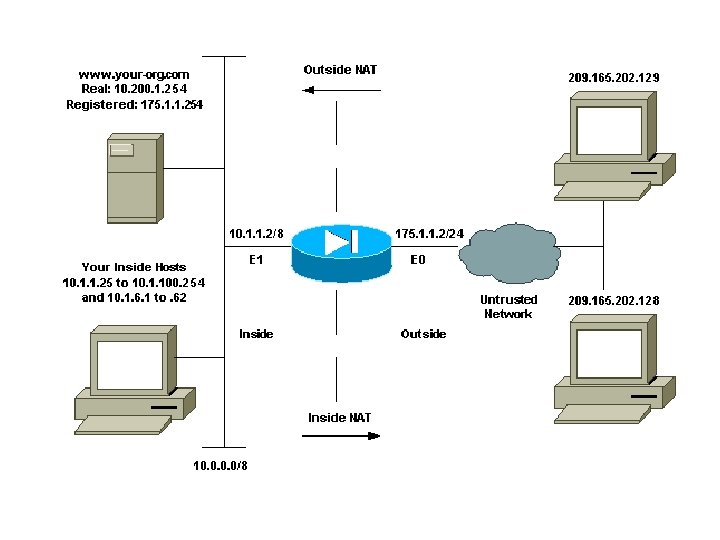
Network Address. Translation Dans sa plus simple configuration, le NAT s’opère sur un routeur à 2 interfaces : une “ inside ” avec des adresses non autorisées ou non routées sur Internet qui doivent donc être translatées (converties) en adresses légales (officielles, publiques) avant de sortir vers l’extérieur (par la seconde interface : “ outside ”). NAT est défini notamment dans le RFC 1631


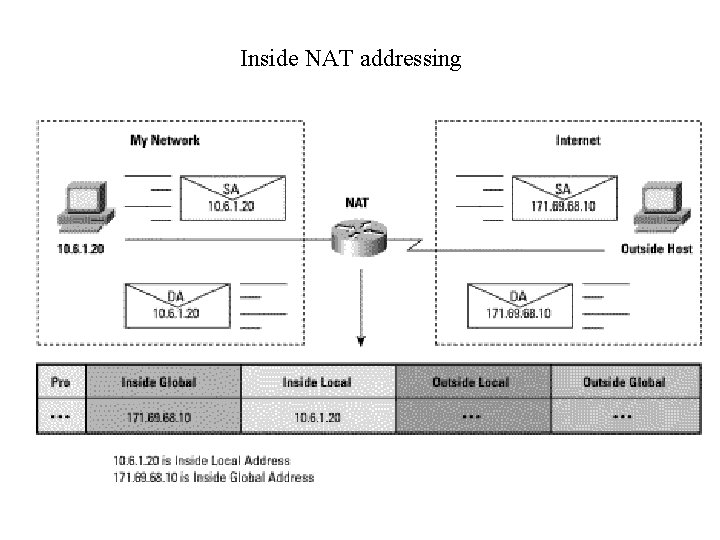
Inside NAT addressing

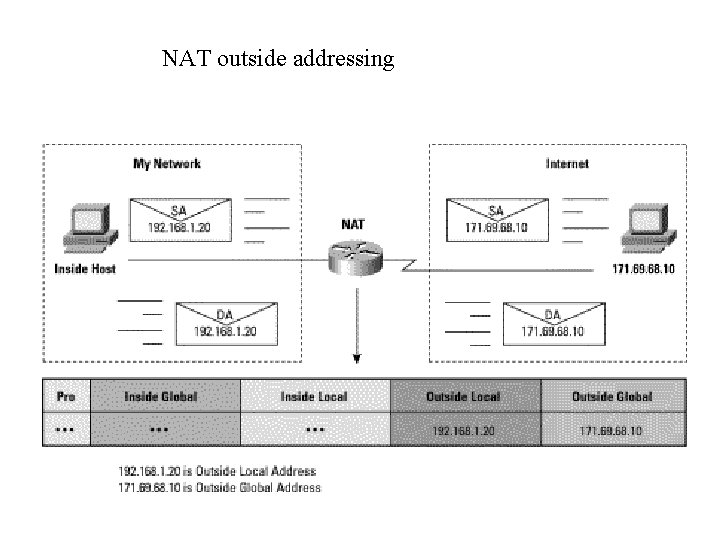
NAT outside addressing

·Inside local; Configured IP address assigned to a host on the inside network. Address may be globally unique, allocated out of the private address space defined in RFC 1918, or might be officially allocated to another organization. ·Inside global; The IP address of an inside host as it appears to the outside network, "Translated IP Address. " Addresses can be allocated from a globally unique address space, typically provided by the ISP (if the enterprise is connected to the global Internet). ·Outside local; The IP address of an outside host as it appears to the inside network. ·Outside global; The configured IP address assigned to a host in the outside network.

Principales caractéristiques Static Address Translation Etablissement d’un mapping un-pour-un entre adresses locales and globales Dynamic Address Translation Etablissement d’un dynamic mapping entre adresses locales and globales Définition d’un pool d’adresses pour l’allocation des global addresses. Intéressant lorsque le nombre d’adresses officielles est inférieur au nombre d’adresses locales (fréquent). Match Host Affecter la même Host portion d’une IP Address et translater seulement le Network prefix. Utile pour identifier les users.

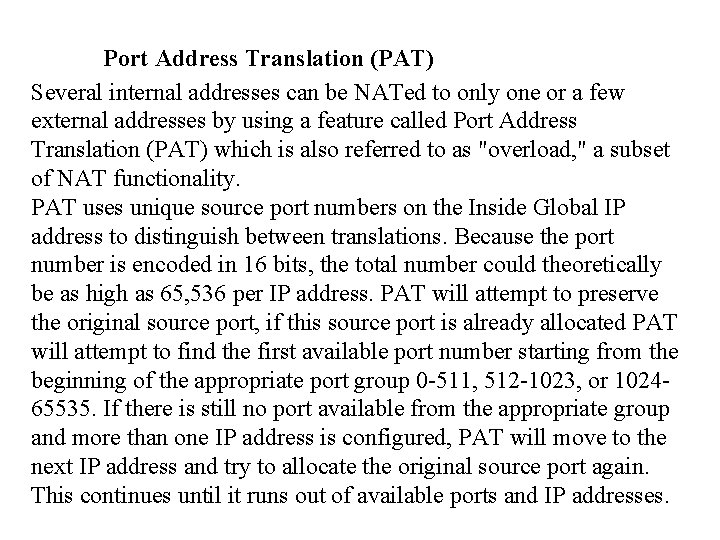
Port Address Translation (PAT) Several internal addresses can be NATed to only one or a few external addresses by using a feature called Port Address Translation (PAT) which is also referred to as "overload, " a subset of NAT functionality. PAT uses unique source port numbers on the Inside Global IP address to distinguish between translations. Because the port number is encoded in 16 bits, the total number could theoretically be as high as 65, 536 per IP address. PAT will attempt to preserve the original source port, if this source port is already allocated PAT will attempt to find the first available port number starting from the beginning of the appropriate port group 0 -511, 512 -1023, or 102465535. If there is still no port available from the appropriate group and more than one IP address is configured, PAT will move to the next IP address and try to allocate the original source port again. This continues until it runs out of available ports and IP addresses.

Concepts PAT

Destination Address Rotary Translation A dynamic form of destination translation can be configured for some outside-to-inside traffic. Once a mapping is set up, a destination address matching one of those on an access list will be replaced with an address from a rotary pool. Allocation is done in a round-robin basis, performed only when a new connection is opened from the outside to the inside. All non-TCP traffic is passed untranslated (unless other translations are in effect). This feature was designed to provide protocol translation load distribution. It is not designed to be used as a substitute technology for Cisco's Local. Director product. Destination address rotary translation should not be used to provide Web service load balancing because it knows nothing about service availability. As a result, if a Web server were to become offline, the destination address rotary translation feature would continue to send requests to the downed server.


Limites du NAT Traffic Types/Applications supportés Tout TCP/UDP traffic qui ne comporte pas de source and/or destination IP addresses dans la partie application de la trame. + Applications avec « verrue NAT » HTTP TFTP telnet … Problème résiduel: Netmeeting v 3 …

Conclusions: Eviter NAT au sein d’une même entreprise Cas des fusions de 2 sociétés Pérennité de connectivité ? ? Redéfinition d’un nouveau plan d’adressage : lourd mais préférable

Cisco Configuration Commands Interface Configuration Commands ip nat { inside | outside } Interfaces need to be marked whether they are on the inside or the outside. Global Configuration Commands: Defining a pool ip nat pool <name> <start-ip> <end-ip> { netmask <netmask> | prefix-length <prefix-length> } [type {rotary}] Defines a pool of addresses using start address, end address, and netmask. These addresses will be allocated as needed.

Enabling translation of inside source addresses ip nat inside source { list <acl> pool <name> [overload] | static <local-ip><global-ip> } The first form enables dynamic translation. Packets from addresses that match those on the simple access list are translated using global addresses allocated from the named pool. The optional keyword overload enables port translation for UDP and TCP. The term overload is equivalent to Port Address Translation (PAT). The second form of the command sets up a single static translation.

Enabling translation of inside destination addresses ip nat inside destination { list <acl> pool <name> | static <global-ip> <local-ip> } Commande similaire à la « source translation command » . For dynamic destination translation to make any sense, the pool should be a rotary-type pool. (option rotary dans l’IP nat pool correspondant). Mais quel besoin ? ? ? voir le dernier exemple de ce chapitre …

Enabling translation of outside source addresses ip nat outside source { list <acl> pool <name> | static <global-ip> <local-ip> } The first form (list. . pool. . ) enables dynamic translation. Packets from addresses that match those on the simple access list are translated using local addresses allocated from the named pool. The second form (static) of the command sets up a single static translation. Quel besoin : par exemple cas d’un réseau outside de même adresse réseau que le réseau inside …cas d’une société qui n’aurait pas choisi des adresses officielles ou conformes au RFC 1918…

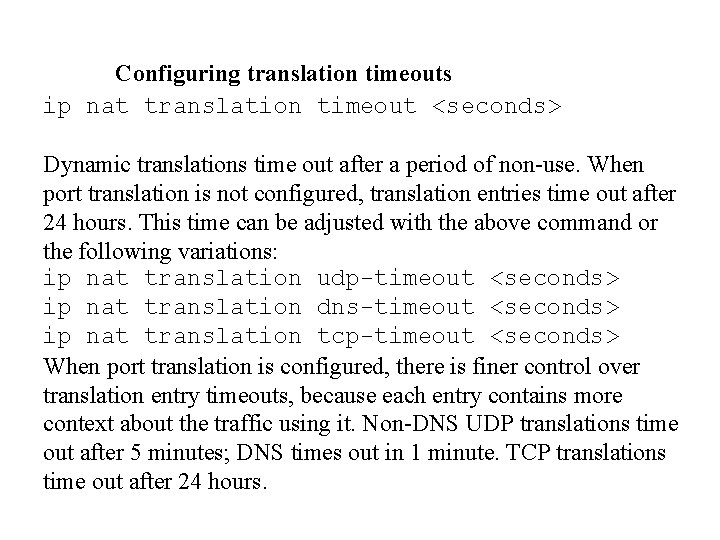
Configuring translation timeouts ip nat translation timeout <seconds> Dynamic translations time out after a period of non-use. When port translation is not configured, translation entries time out after 24 hours. This time can be adjusted with the above command or the following variations: ip nat translation udp-timeout <seconds> ip nat translation dns-timeout <seconds> ip nat translation tcp-timeout <seconds> When port translation is configured, there is finer control over translation entry timeouts, because each entry contains more context about the traffic using it. Non-DNS UDP translations time out after 5 minutes; DNS times out in 1 minute. TCP translations time out after 24 hours.
![Exec Commands Show active translations show ip nat translations verbose Show translation Exec Commands Show active translations show ip nat translations [ verbose ] Show translation](https://slidetodoc.com/presentation_image_h/f47d01ae8ed71fdfe2278f0507bd90bb/image-58.jpg)
Exec Commands Show active translations show ip nat translations [ verbose ] Show translation statistics show ip nat statistics Clearing dynamic translations clear ip nat translation * Clears all dynamic translations. clear ip nat translation <global-ip> Clears a simple translation. clear ip nat translation <global-ip> <local-ip> <proto> <global-port> <localport> Clears a particular dynamic translation.
![Debugging debug ip nat list detailed Debugging debug ip nat [ <list> ] [ detailed ]](https://slidetodoc.com/presentation_image_h/f47d01ae8ed71fdfe2278f0507bd90bb/image-59.jpg)
Debugging debug ip nat [ <list> ] [ detailed ]

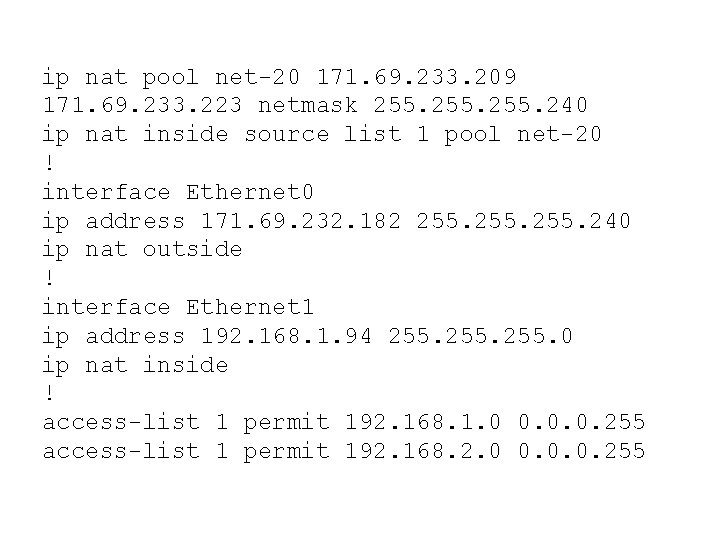
Exemples de Configuration The following sample configuration translates between inside hosts addressed from either the 192. 168. 1. 0 or 192. 168. 2. 0 nets to the globally-unique 171. 69. 233. 208/28 network. La translation ne concerne que ces 2 seuls réseaux.

ip nat pool net-20 171. 69. 233. 209 171. 69. 233. 223 netmask 255. 240 ip nat inside source list 1 pool net-20 ! interface Ethernet 0 ip address 171. 69. 232. 182 255. 240 ip nat outside ! interface Ethernet 1 ip address 192. 168. 1. 94 255. 0 ip nat inside ! access-list 1 permit 192. 168. 1. 0 0. 0. 0. 255 access-list 1 permit 192. 168. 2. 0 0. 0. 0. 255

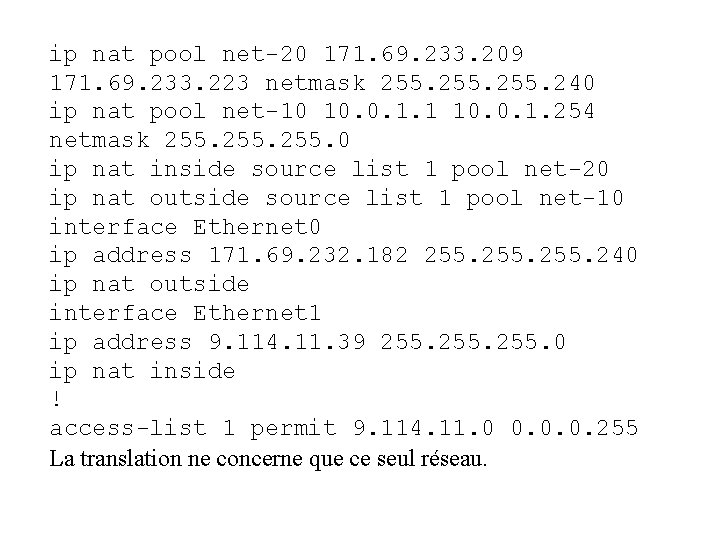
The next sample configuration translates between inside hosts addressed from the 9. 114. 11. 0 net to the globally unique 171. 69. 233. 208/28 network. Packets from outside hosts addressed from 9. 114. 11. 0 net (the "true" 9. 114. 11. 0 net) are translated to appear to be from net 10. 0. 1. 0/24. Cas d’une société qui n’aurait pas choisi comme adressage interne un adressage public ou conforme au RFC 1918.

ip nat pool net-20 171. 69. 233. 209 171. 69. 233. 223 netmask 255. 240 ip nat pool net-10 10. 0. 1. 1 10. 0. 1. 254 netmask 255. 0 ip nat inside source list 1 pool net-20 ip nat outside source list 1 pool net-10 interface Ethernet 0 ip address 171. 69. 232. 182 255. 240 ip nat outside interface Ethernet 1 ip address 9. 114. 11. 39 255. 0 ip nat inside ! access-list 1 permit 9. 114. 11. 0 0. 0. 0. 255 La translation ne concerne que ce seul réseau.

Configuration du pool: The pool configuration syntax has been extended to allow discontiguous ranges of addresses : ip nat pool <name> { netmask <mask> | prefix-length <length> } This command will put the user into IP NAT Pool configuration mode, where a sequence of address ranges can be configured. There is only one command in this mode: address <start> <end> Router(config)#ip nat pool fred prefix-length 24 Router(config-ipnat-pool)#address 171. 69. 233. 225 171. 69. 233. 226 Router(config-ipnat-pool)#address 171. 69. 233. 228 171. 69. 233. 238 This configuration creates a pool containing addresses 171. 69. 233. 225 -226 and 171. 69. 233. 228 -238 (171. 69. 233. 227 has been omitted).

Translating to interface's address As a convenience for users wishing to translate all inside addresses to the address assigned to an interface on the router, the NAT code allows one to simply name the interface when configuring the dynamic translation rule: ip nat inside source list <number> interface <interface> overload If there is no address on the interface, or it the interface is not up, no translation will occur. Example: ip nat inside source list 1 interface Serial 0 overload

Static translations with ports: Services on the inside network (like mail) will require additional configuration. This command allows the user to map certain services of certain inside hosts. ip nat inside source static { tcp | udp } <localaddr> <localport> <globaladdr> <globalport> Example: ip nat inside source static tcp 192. 168. 10. 1 25 171. 69. 232. 209 25

Translation Entry Limit Using the following command, Cisco IOS NAT can be configured to limit the number of translation entries it creates. The default is that there is no limit. ip nat translation max-entries <n>

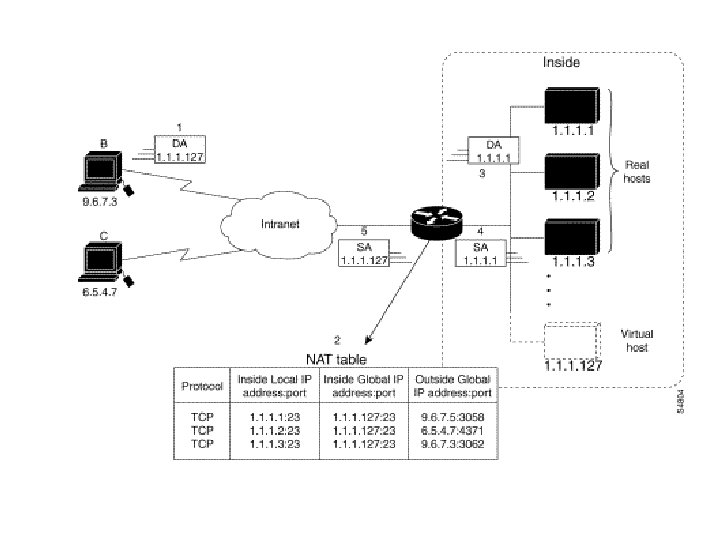
Provide TCP Load Distribution Another use of NAT is unrelated to Internet addresses. Your organization may have multiple hosts that must communicate with a heavily used host. Using NAT, you can establish a virtual host on the inside network that coordinates load sharing among real hosts. Destination addresses that match an access list are replaced with addresses from a rotary pool. Allocation is done in a round-robin basis, and only when a new connection is opened from the outside to the inside. Non-TCP traffic is passed untranslated (unless other translations are in effect).

The router performs the following process when translating rotary addresses: 1. The user on Host B (9. 6. 7. 3) opens a connection to virtual host at 1. 127. 2. The router receives the connection request and creates a new translation, allocating the next real host (1. 1) for the inside local IP address. 3. The router replaces the destination address with the selected real host address and forwards the packet. 4. Host 1. 1 receives the packet and responds. 5. The router receives the packet, performs a NAT table lookup using the inside local address and port number, and the outside address and port number as the key. The router then translates the source address to the address of the virtual host and forwards the packet. The next connection request will cause the router to allocate 1. 1. 1. 2 for the inside local address.

Note The access list must permit only those addresses that are to be translated. (Remember that there is an implicit "deny all" at the end of each access list. ) An access list that is too permissive can lead to unpredictable results. In the following example, the goal is to define a virtual address, connections to which are distributed among a set of real hosts. The pool defines the addresses of the real hosts. The access list defines the virtual address. If a translation does not already exist, TCP packets from serial 0 (the outside interface) whose destination matches the access list are translated to an address from the pool.

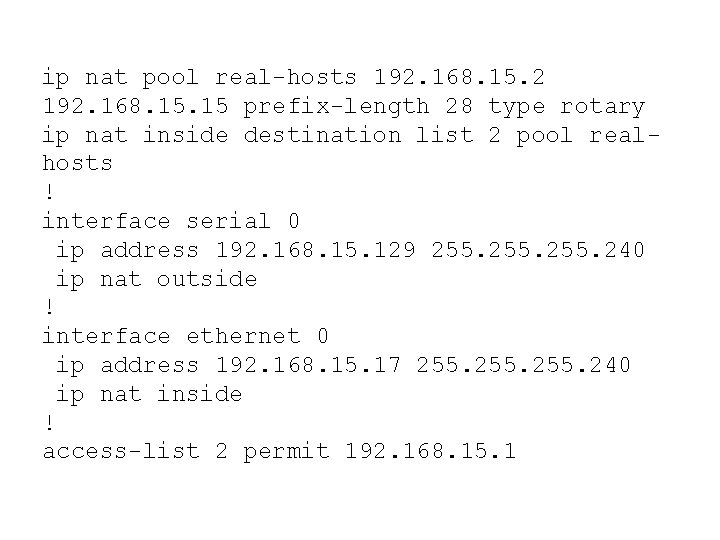
ip nat pool real-hosts 192. 168. 15. 2 192. 168. 15 prefix-length 28 type rotary ip nat inside destination list 2 pool realhosts ! interface serial 0 ip address 192. 168. 15. 129 255. 240 ip nat outside ! interface ethernet 0 ip address 192. 168. 15. 17 255. 240 ip nat inside ! access-list 2 permit 192. 168. 15. 1

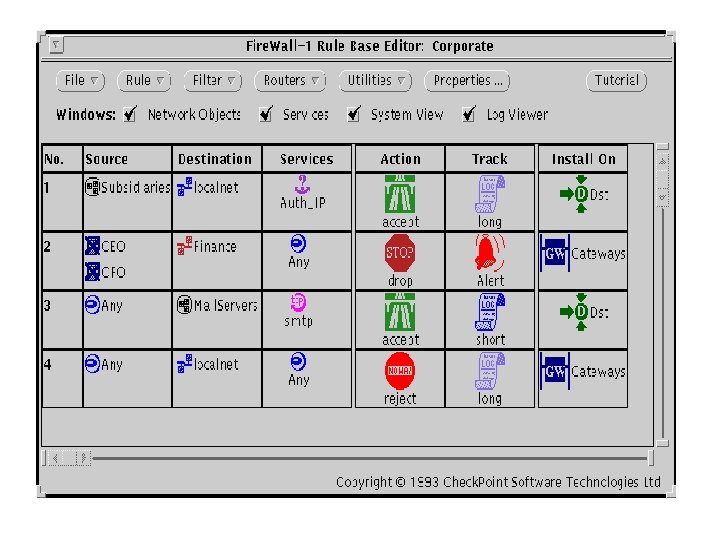
Firewall – Pare-feux -Caractéristiques générales et offre du marché Firewall applicatifs basé sur PC + OS connu (Unix, NT, Win 2 K, …) Exemple : Firewall-1 de Checkpoint Software Notion statefull Firewall basé sur boitier standalone et OS propriétaire Exemple : PIX Cisco Offre Cisco : Cisco PIX 501 (option failover) IOS firewall pour routeur Cisco (mémoires requises)


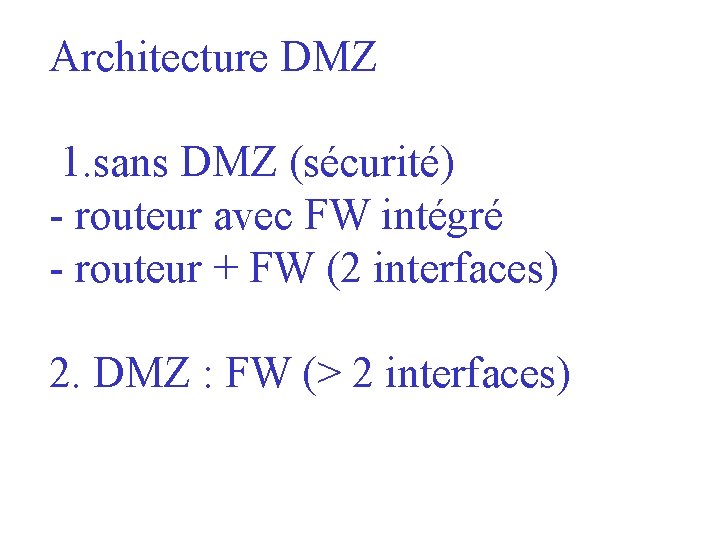
Architecture DMZ 1. sans DMZ (sécurité) - routeur avec FW intégré - routeur + FW (2 interfaces) 2. DMZ : FW (> 2 interfaces)

PIX Cisco OS Similaire à IOS Cisco mais ce n’est pas un IOS, commandes différentes Modes d’accès : identique IOS ·Unprivileged mode : ">" prompt. ·Privileged mode : t "#" ·Enable, disable, exit, or quit ·Configuration mode "(config)#" prompt avec la commade configure terminal 0 represents 0. 0. Backups ·write memory ·tftp-server, write net

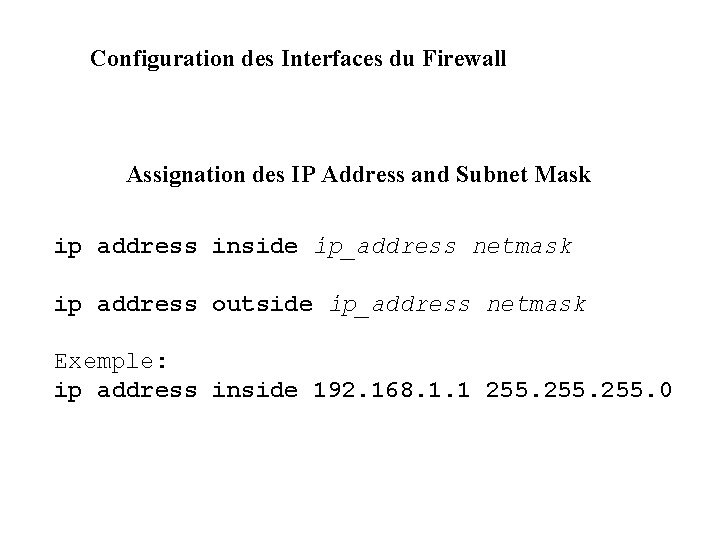
Configuration des Interfaces du Firewall Assignation des IP Address and Subnet Mask ip address inside ip_address netmask ip address outside ip_address netmask Exemple: ip address inside 192. 168. 1. 1 255. 0

Changer les noms d’Interface et les Security Levels (optionnel) nameif ethernet 0 outside security 0 (default) nameif ethernet 1 inside security 100 (default) nameif ethernet 2 intf 2 security 10 (default) Show nameif Donner des noms significatifs : exemple : dmz 1 Niveaux de sécurité : 100 est maximale, 0 minimale Ils servent à contrôler les accès entre les systèmes différentes interfaces.

Principes Pour accéder à une interface de basse sécurité depuis une interface de sécurité haute utiliser les commandes nat et global (voir exemples qui suivent). Par défaut pas de restriction (si une commande nat est activée). Utiliser des access-list pour restreindre les droits (selon l’adresse IP et/ou le port TCP/UDP). Remarques : implicit deny (permit) all existe comme avec IOS. Le wildcard mask n’est pas utilisé on utilise le masque “ normal ”

Pour accéder à un interface de haute sécurité depuis une interface de sécurité basse utiliser les commandes static et access-list (voir exemples qui suivent). Par défaut tout est interdit. Remarques : dans les anciennes versions de PIX software (< v 5), la commande conduit était utilisée (au lieu de static et access-list).

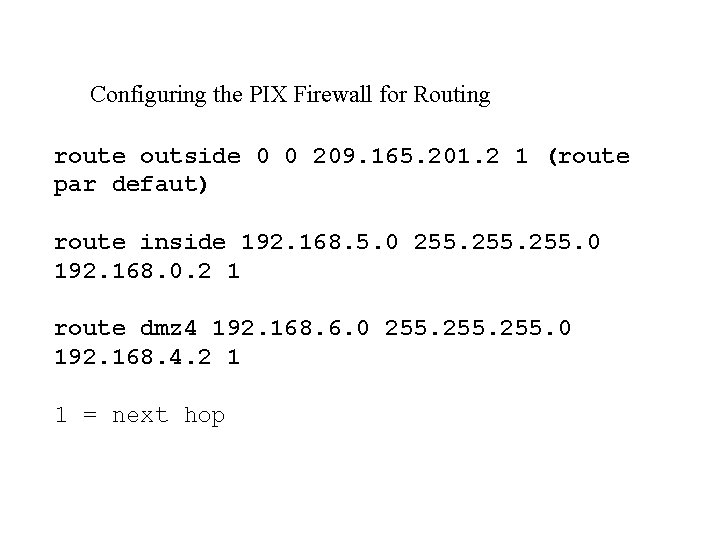
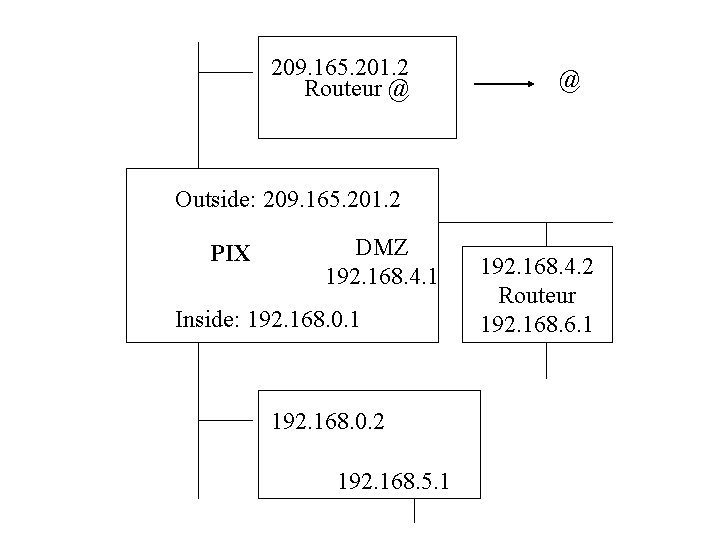
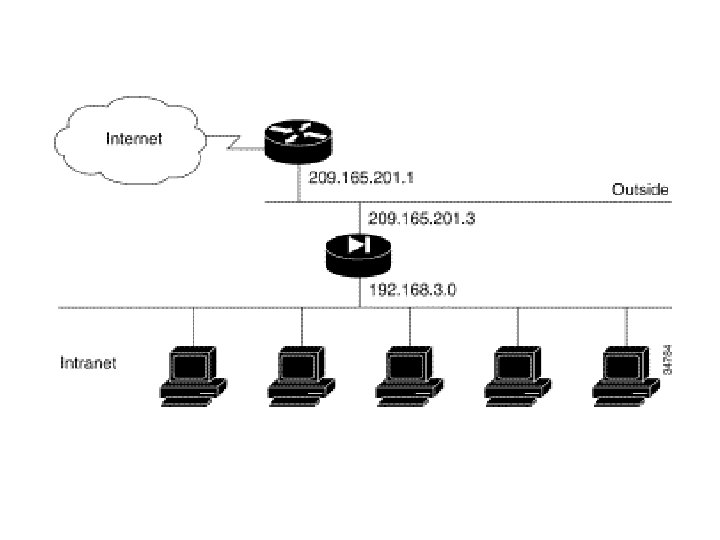
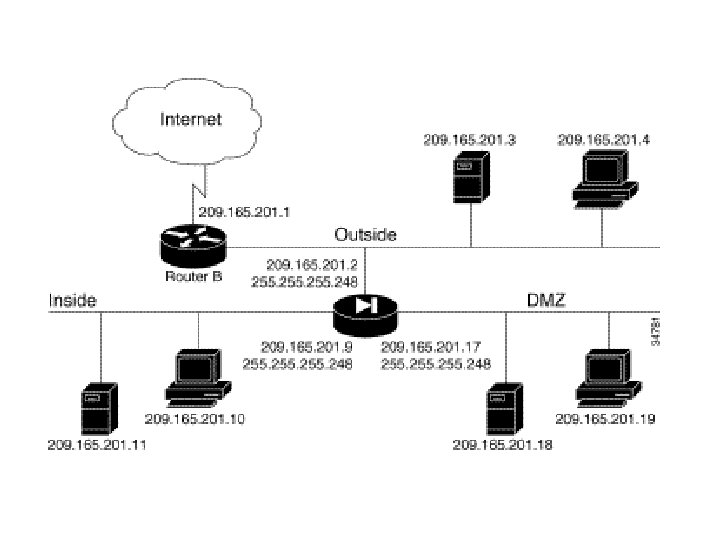
Configuring the PIX Firewall for Routing route outside 0 0 209. 165. 201. 2 1 (route par defaut) route inside 192. 168. 5. 0 255. 0 192. 168. 0. 2 1 route dmz 4 192. 168. 6. 0 255. 0 192. 168. 4. 2 1 1 = next hop

209. 165. 201. 2 Routeur @ @ Outside: 209. 165. 201. 2 PIX DMZ 192. 168. 4. 1 Inside: 192. 168. 0. 1 192. 168. 0. 2 192. 168. 5. 1 192. 168. 4. 2 Routeur 192. 168. 6. 1

Etablir la connectivité Outbound avec NAT et PAT Network Address Translation (NAT). Port Address Translation (PAT) avec une seule globale IP address 64, 000 ports sont en théorie disponibles (port codé sur 16 bits) Le PIX Firewall associe une adresse interne avec une adresse globale en utilisant un NAT identifier (NAT ID).

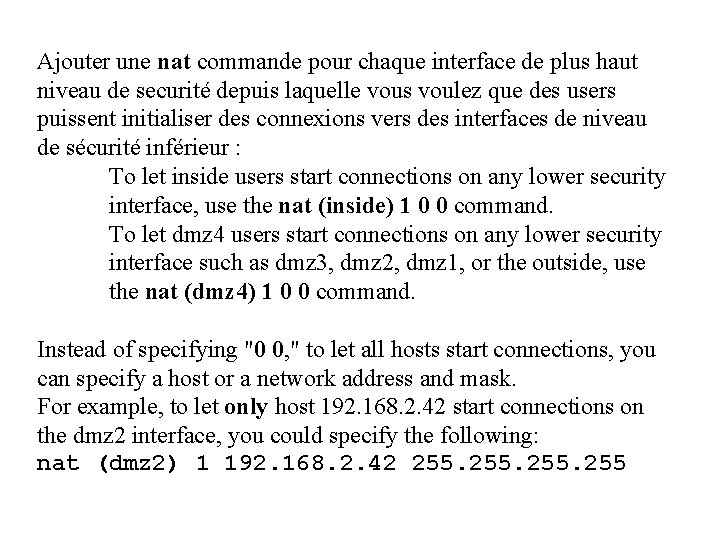
Ajouter une nat commande pour chaque interface de plus haut niveau de securité depuis laquelle vous voulez que des users puissent initialiser des connexions vers des interfaces de niveau de sécurité inférieur : To let inside users start connections on any lower security interface, use the nat (inside) 1 0 0 command. To let dmz 4 users start connections on any lower security interface such as dmz 3, dmz 2, dmz 1, or the outside, use the nat (dmz 4) 1 0 0 command. Instead of specifying "0 0, " to let all hosts start connections, you can specify a host or a network address and mask. For example, to let only host 192. 168. 2. 42 start connections on the dmz 2 interface, you could specify the following: nat (dmz 2) 1 192. 168. 2. 42 255

LE "1" après l’interface est le NAT ID 0 means to disable Network Address Translation. Le NAT ID in the nat command has to be the same NAT ID you use for the corresponding global command. global (outside) 1 209. 165. 201. 5 netmask 255. 224 global (outside) 1 209. 165. 201. 10209. 165. 201. 20 netmask 255. 224

The first global command statement specifies a single IP address, which the PIX Firewall interprets as a PAT. The PAT lets up to 65, 535 hosts start connections to the outside. PIX Firewall permits one PAT global command statement for each interface. The second global command statement augments the pool of global addresses on the outside interface. The PAT creates a pool of addresses used only when the addresses in the first global command statement are in use.

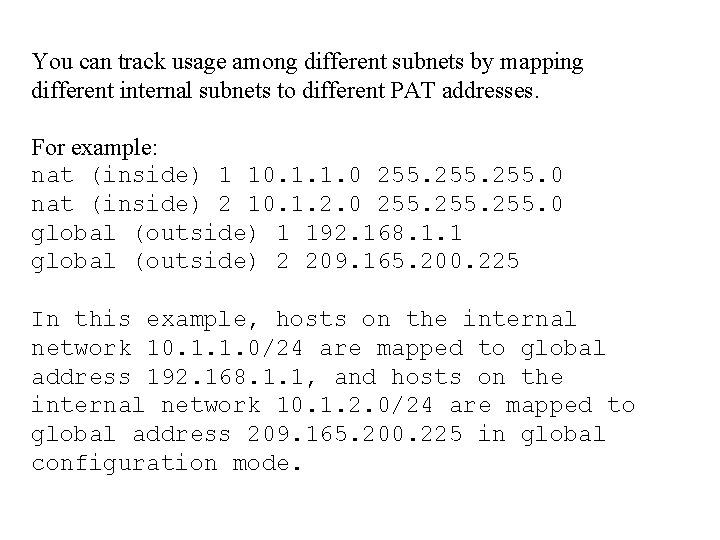
global (dmz 1) 1 192. 168. 1. 10 -192. 168. 1. 100 netmask 255. 0 global (dmz 2) 1 192. 168. 2. 10 -192. 168. 2. 100 netmask 255. 0 The global command statement for dmz 1 lets users on the inside, dmz 2, dmz 3, and dmz 4 start connections on the dmz 1 interface. The global command statement for dmz 2 lets users on the inside, dmz 3, and dmz 4 start connections on the dmz 2 interface. If you use network subnetting, specify the subnet mask with the netmask option.

You can track usage among different subnets by mapping different internal subnets to different PAT addresses. For example: nat (inside) 1 10. 1. 1. 0 255. 0 nat (inside) 2 10. 1. 2. 0 255. 0 global (outside) 1 192. 168. 1. 1 global (outside) 2 209. 165. 200. 225 In this example, hosts on the internal network 10. 1. 1. 0/24 are mapped to global address 192. 168. 1. 1, and hosts on the internal network 10. 1. 2. 0/24 are mapped to global address 209. 165. 200. 225 in global configuration mode.


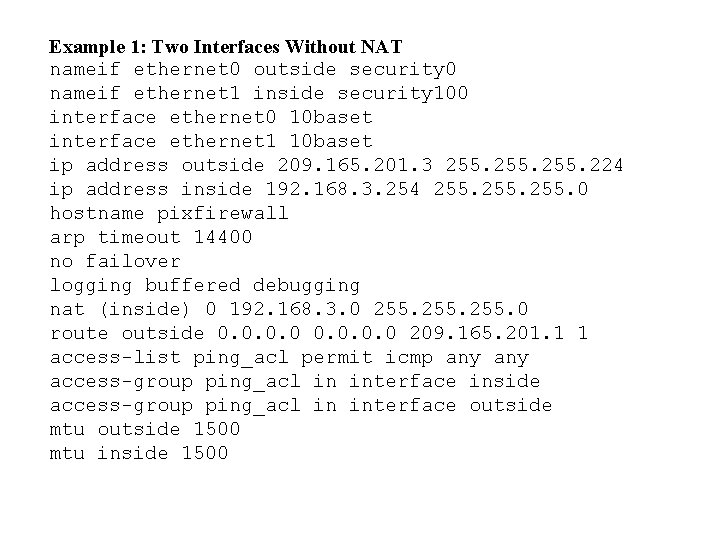
Example 1: Two Interfaces Without NAT nameif ethernet 0 outside security 0 nameif ethernet 1 inside security 100 interface ethernet 0 10 baset interface ethernet 1 10 baset ip address outside 209. 165. 201. 3 255. 224 ip address inside 192. 168. 3. 254 255. 0 hostname pixfirewall arp timeout 14400 no failover logging buffered debugging nat (inside) 0 192. 168. 3. 0 255. 0 route outside 0. 0 209. 165. 201. 1 1 access-list ping_acl permit icmp any access-group ping_acl in interface inside access-group ping_acl in interface outside mtu outside 1500 mtu inside 1500

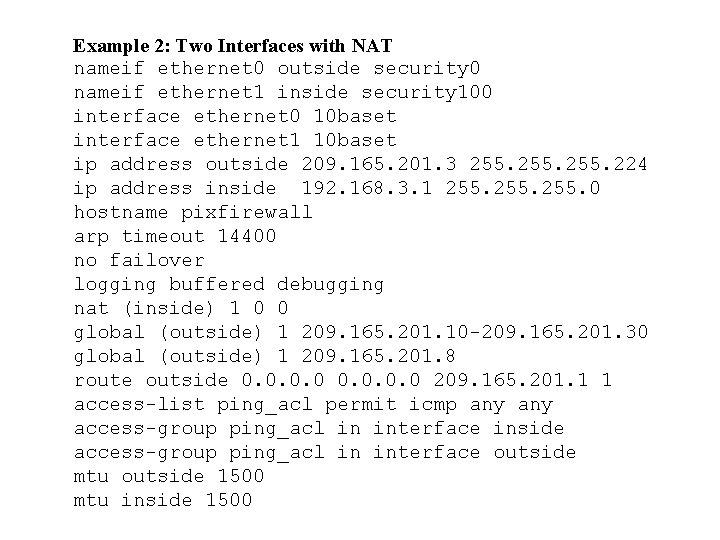
Example 2: Two Interfaces with NAT nameif ethernet 0 outside security 0 nameif ethernet 1 inside security 100 interface ethernet 0 10 baset interface ethernet 1 10 baset ip address outside 209. 165. 201. 3 255. 224 ip address inside 192. 168. 3. 1 255. 0 hostname pixfirewall arp timeout 14400 no failover logging buffered debugging nat (inside) 1 0 0 global (outside) 1 209. 165. 201. 10 -209. 165. 201. 30 global (outside) 1 209. 165. 201. 8 route outside 0. 0 209. 165. 201. 1 1 access-list ping_acl permit icmp any access-group ping_acl in interface inside access-group ping_acl in interface outside mtu outside 1500 mtu inside 1500


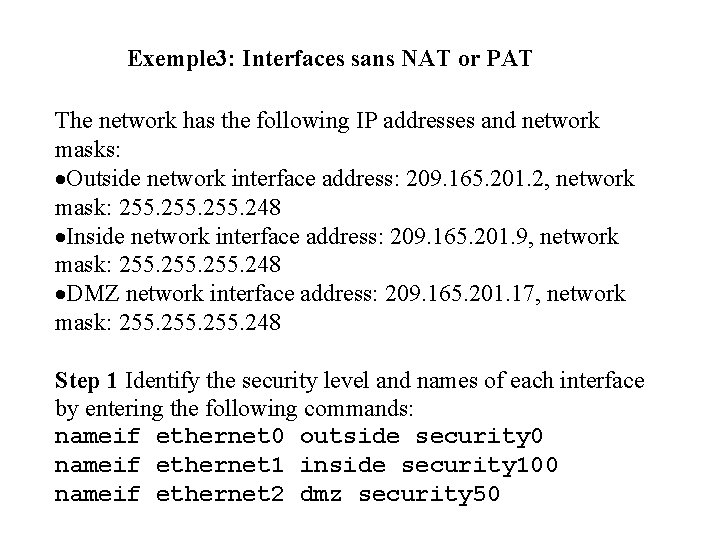
Exemple 3: Interfaces sans NAT or PAT The network has the following IP addresses and network masks: ·Outside network interface address: 209. 165. 201. 2, network mask: 255. 248 ·Inside network interface address: 209. 165. 201. 9, network mask: 255. 248 ·DMZ network interface address: 209. 165. 201. 17, network mask: 255. 248 Step 1 Identify the security level and names of each interface by entering the following commands: nameif ethernet 0 outside security 0 nameif ethernet 1 inside security 100 nameif ethernet 2 dmz security 50

An additional nameif command is required for the third interface in this example. Step 2 Identify the line speed of each interface by entering the following commands: interface ethernet 0 10 baset interface ethernet 1 10 baset interface ethernet 0 100 basetx Step 3 Identify the IP addresses for each interface: ip address outside 209. 165. 201. 2 255. 248 ip address inside 209. 165. 201. 9 255. 248 ip address dmz 209. 165. 201. 17 255. 248

Step 4 Map access to the 209. 165. 201. 19 host on the outside interface: static (dmz, outside) 209. 165. 201. 5 209. 165. 201. 19 Step 5 Use the access-list command to let any outside user access the DMZ host on any port: access-list acl_out permit tcp any host 209. 165. 201. 5 access-group acl_out in interface outside Remarques : on peut spécifier un host extérieur autorisé à la place de any ou spécifier un port qui serait le seul autorisé (eq www en fin de commande).

The access-list command lets any outside user access the host on any port. nameif ethernet 0 outside security 0 nameif ethernet 1 inside security 100 nameif ethernet 2 dmz security 50 interface ethernet 0 10 baset interface ethernet 1 10 baset interface ethernet 0 100 basetx ip address outside 209. 165. 201. 2 255. 224 ip address inside 209. 165. 201. 9 255. 224 ip address dmz 209. 165. 201. 17 255. 224 hostname pixfirewall arp timeout 14400

Configuration (suite) no failover logging buffered debugging nat (inside) 0 209. 165. 201. 8 255. 248 static (dmz, outside) 209. 165. 201. 5 209. 165. 201. 19 access-list acl_out permit tcp any host 209. 165. 201. 5 access-group acl_out in interface outside route outside 0. 0 209. 165. 201. 1 1 mtu outside 1500 mtu inside 1500

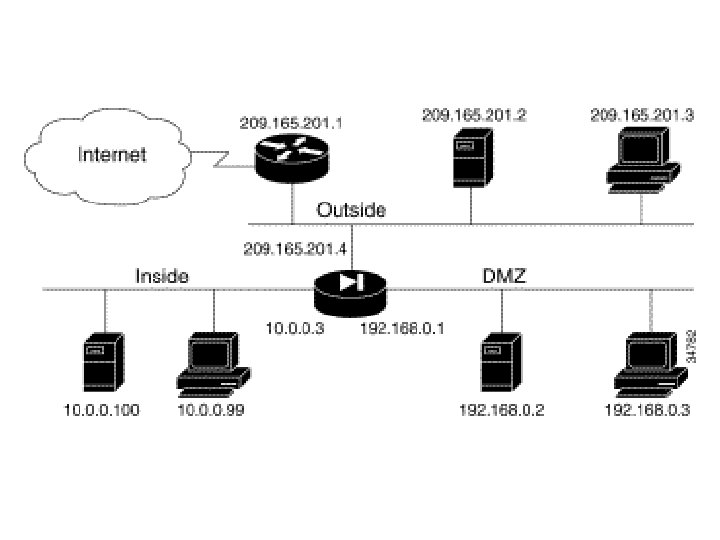
Exemple 4: 3 interfaces avec PAT et NAT The network has the following IP addresses and network masks: ·Outside network interface address: 209. 165. 201. 4, network mask: 255. 224 ·Allowable global and static addresses on the outside network: 209. 165. 201. 5 -209. 165. 201. 30, network mask: 255. 224 ·Inside network interface address: 10. 0. 0. 3, network mask: 255. 0. 0. 0 ·DMZ network interface address: 192. 168. 0. 1, network mask: 255. 0

Exemple 4: 3 interfaces avec PAT ni NAT the PIX Firewall has three interfaces and these attributes: ·Address translation is performed between the interfaces. ·A web server on the DMZ interface is publicly accessible. The name command maps its host address to the name "webserver. " ·The inside network has RFC 1918 addresses (10. 0), the DMZ interface has RFC 1918 addresses (192. 168. 0. 0), and the outside network has legal, registered addresses (209. 165. 201. 0). ·TCP and UDP connections from the inside are allowed to go out on the DMZ and outside.


Step 1 Create a pool of global addresses for the outside and DMZ interfaces. Because there are limited outside IP addresses, add a PAT global to handle overflow. The global (dmz) command gives inside users access to the web server on the DMZ interface. global (outside) 1 209. 165. 201. 10209. 165. 201. 30 global (outside) 1 209. 165. 201. 5 global (dmz) 1 192. 168. 0. 10 -192. 168. 0. 20

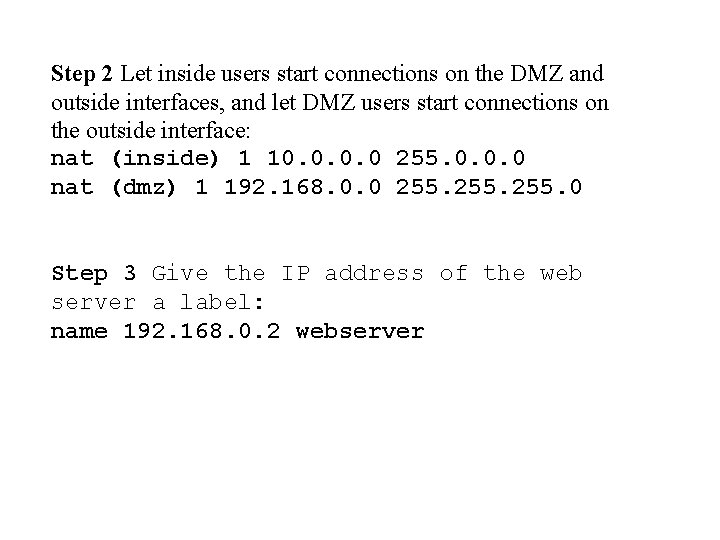
Step 2 Let inside users start connections on the DMZ and outside interfaces, and let DMZ users start connections on the outside interface: nat (inside) 1 10. 0 255. 0. 0. 0 nat (dmz) 1 192. 168. 0. 0 255. 0 Step 3 Give the IP address of the web server a label: name 192. 168. 0. 2 webserver

Step 4 Let any user on the outside interface access the web server on the DMZ interface: static (dmz, outside) 209. 165. 201. 6 webserver access-list acl_out permit tcp any host 209. 165. 201. 6 eq 80 access-group acl_out in interface outside The access-list command statement is bound to the outside interface by the access-group command statement.

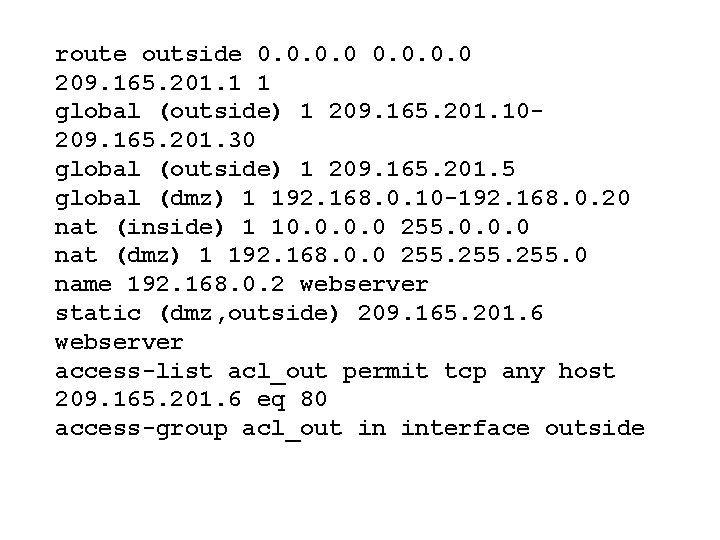
Example 4: Three Interfaces with NAT nameif ethernet 0 outside security 0 nameif ethernet 1 inside security 100 nameif ethernet 2 dmz security 50 interface ethernet 0 10 full interface ethernet 1 10 full interface ethernet 2 10 full ip address outside 209. 165. 201. 4 255. 224 ip address inside 10. 0. 0. 3 255. 0. 0. 0 ip address dmz 192. 168. 0. 1 255. 0 hostname pixfirewall

route outside 0. 0 209. 165. 201. 1 1 global (outside) 1 209. 165. 201. 10209. 165. 201. 30 global (outside) 1 209. 165. 201. 5 global (dmz) 1 192. 168. 0. 10 -192. 168. 0. 20 nat (inside) 1 10. 0 255. 0. 0. 0 nat (dmz) 1 192. 168. 0. 0 255. 0 name 192. 168. 0. 2 webserver static (dmz, outside) 209. 165. 201. 6 webserver access-list acl_out permit tcp any host 209. 165. 201. 6 eq 80 access-group acl_out in interface outside


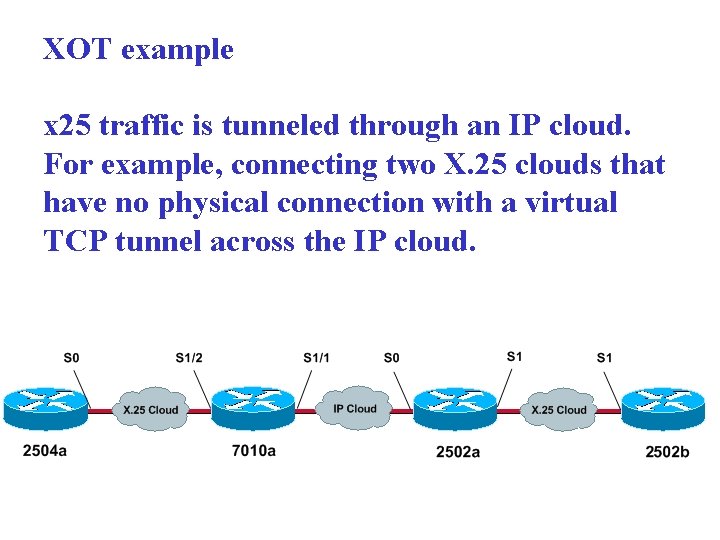
XOT is X 25 Over TCP, Request For Comments (RFC) 1613. This allows X. 25 packets to be sent over a Transmission Control Protocol/Internet Protocol (TCP/IP) network … instead of a Link Access Procedure, Balanced (LAPB) link.

Intérêt (économiques): - pérennité des applications X 25 - coûts télécom abaissés: mutualisation des liens avec les applications TCP

XOT example x 25 traffic is tunneled through an IP cloud. For example, connecting two X. 25 clouds that have no physical connection with a virtual TCP tunnel across the IP cloud.