September 25 2000 HIPAA and Your Compliance Program

September 25, 2000 HIPAA and Your Compliance Program HCCA’s 2000 Compliance Institute New Orleans, Louisiana S IDLEY & A USTIN

Presentation Agenda • Introductions • Overview and Background • HIPAA Requirements and Provisions ° Technology with Q&A ° Privacy with Q&A ° Security with Q&A • Integration into Compliance Program S IDLEY & A USTIN 2

Overview and Background of HIPAA S IDLEY & A USTIN

General Provisions Group and Individual Insurance Reform • Limits on pre-existing exclusion provisions • Portability of coverage, guaranteed issue and renewal Fraud and Abuse • Medicare integrity, data collection, beneficiary incentive programs • Increased penalties, sanctions, and exclusions S IDLEY & A USTIN Tax-Related Health Provisions • MSAs, long-term care insurance, taxation of insurance benefits Administrative Simplification (AS) • Improve efficiency and effectiveness of the healthcare system • Define standards for electronic transmission - standard identifiers, transaction and code sets • Protect the privacy and security of health information 4
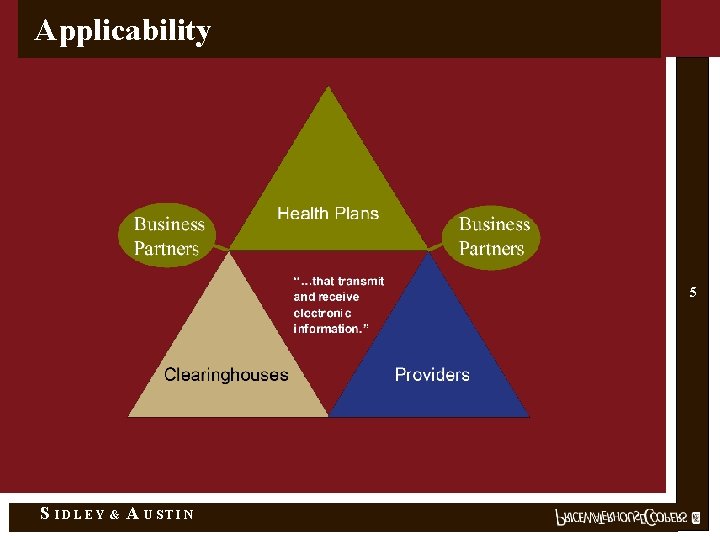
Applicability 5 S IDLEY & A USTIN

Penalties and Fines Non-Compliance with Requirements • $100 per violation to a maximum of $25, 000 per requirement per year • Considering the proposed security rules contain more than 25 specific requirements, the maximum penalty can exceed $625, 000 per year S IDLEY & A USTIN Wrongful Disclosure of Health Information • Simple disclosure – fines up to $50, 000 and/or one year in prison • Disclosure under false pretenses – fines up to $100, 000 and/or five years in prison • Disclosure with intent to sell or use – fines up to $250, 000 and/or 10 years in prison 6

Technology Requirements S IDLEY & A USTIN
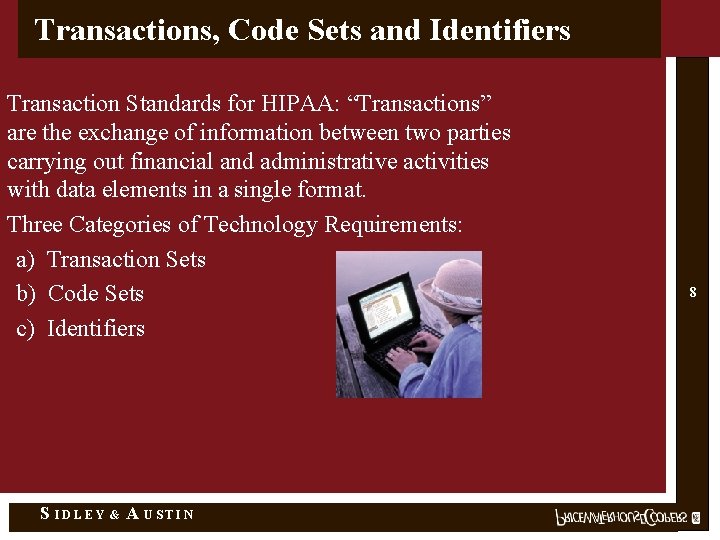
Transactions, Code Sets and Identifiers Transaction Standards for HIPAA: “Transactions” are the exchange of information between two parties carrying out financial and administrative activities with data elements in a single format. Three Categories of Technology Requirements: a) Transaction Sets b) Code Sets c) Identifiers S IDLEY & A USTIN 8
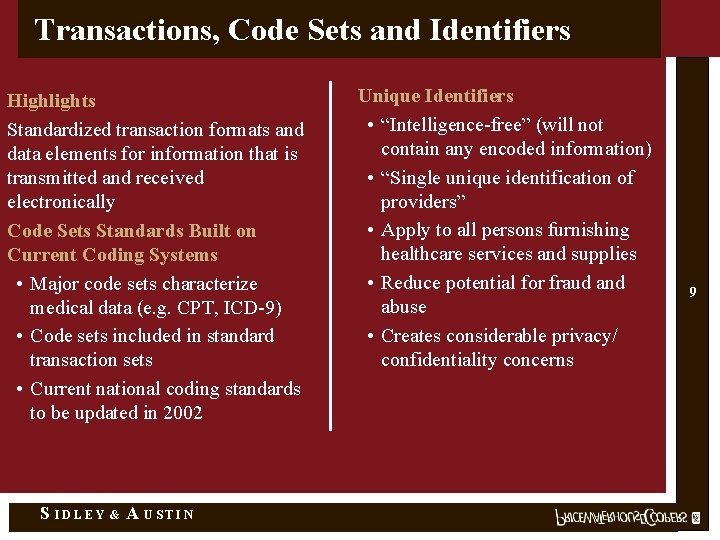
Transactions, Code Sets and Identifiers Highlights Standardized transaction formats and data elements for information that is transmitted and received electronically Code Sets Standards Built on Current Coding Systems • Major code sets characterize medical data (e. g. CPT, ICD-9) • Code sets included in standard transaction sets • Current national coding standards to be updated in 2002 S IDLEY & A USTIN Unique Identifiers • “Intelligence-free” (will not contain any encoded information) • “Single unique identification of providers” • Apply to all persons furnishing healthcare services and supplies • Reduce potential for fraud and abuse • Creates considerable privacy/ confidentiality concerns 9

Transactions, Code Sets and Identifiers Standard transaction sets are defined for the following: • • • Health claims or equivalent encounter (X 12 N 837) Enrollment and disenrollment in a health plan (X 12 834) Eligibility for health plan - inquiry/response (X 12 N 270 -271) Healthcare payment and remittance advice (X 12 N 835) Health plan premium payments (X 12 820) Health claim status - inquiry/response (X 12 N 276 -277) • • • Coordination of benefits (X 12 N 837) Referral certification (X 12 N 278) Referral authorization (X 12 N 278) First report of injury (open) Health claims attachments (open) Standard Transaction Record 10 Code Sets ICD-9 -CM (diagnosis and procedures) CPT-4 (physician procedures) HCPCS (ancillary services/procedures) CDT-2 (dental terminology) NDC (national drug codes) S IDLEY & A USTIN Identifiers Providers Employers Health plans (open) Individuals (open)

Key Business Considerations • Integration of new transactions into legacy systems • Investment in new systems/channels • Revision of Q/A testing and user acceptance processes • Integration of technology requirements in contracts, accreditation • Budget impact • Return on investment • Leverage investment in Y 2 K S IDLEY & A USTIN 11

Privacy Requirements S IDLEY & A USTIN
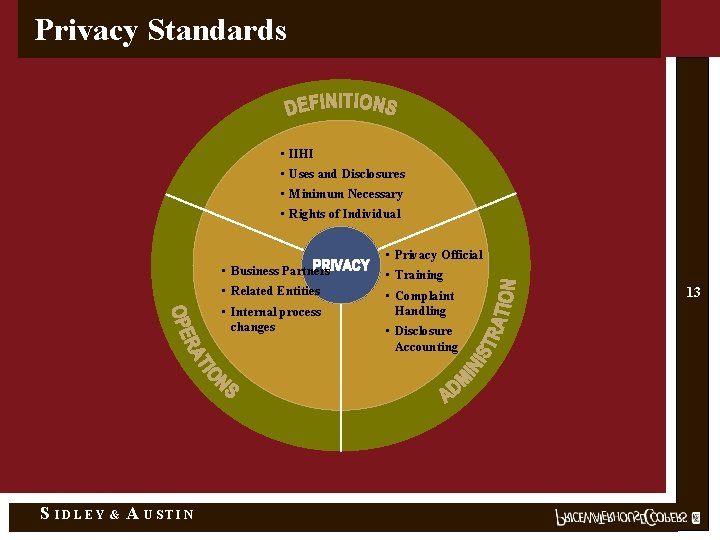
Privacy Standards • IIHI • Uses and Disclosures • Minimum Necessary • Rights of Individual • Privacy Official • Business Partners • Training • Related Entities • Complaint Handling • Internal process changes S IDLEY & A USTIN • Disclosure Accounting 13

Protected Health Information Permitted Uses and Disclosures Authorization not required for: Authorization required for: • Uses or disclosures relating to • Disclosures on request of treatment, payment or health care individual, entity or third party operations • Marketing, fund-raising purposes • Public health agency activities • Disclosure to non-health related • Health oversight and regulatory affiliates (e. g. , life insurance) agencies • Underwriting or risk rating • Judicial proceedings and law • Employment determinations enforcement investigations • Sale, rental or barter • Health care fraud • Disclosure of psychotherapy notes • Research purposes (under rigorous or research information criteria) • Disclosure of “de-identified” health information S IDLEY & A USTIN 14

Minimum Necessary Disclosure • Reasonable efforts not to use or disclose more than the minimum amount of information needed to accomplish an intended purpose • Entity designates staff to determine minimum necessary information • Determination made on individual basis within limits of technology • Pervasive throughout organization ° Applies to both internal and external uses ° “Minimum necessary” varies by function and department ° Implications for information systems S IDLEY & A USTIN 15

Administrative Requirements • Designate privacy official • Conduct privacy training program • Verification procedures • Maintain policies and procedures for PHI • Notice of privacy practices S IDLEY & A USTIN 16

Business Partners • Contractors providing services to covered entities - that utilize or share IIHI • Business partner contracts must contain specific privacy provisions ° Appropriate safeguards of records ° Report any unauthorized disclosures to entity ° Books and records available for inspection ° Material breach by partner grounds for termination, constitutes violation by entity ° Member/patient is third party beneficiary • Extension of liability S IDLEY & A USTIN 17

Rights of Individuals • With the exception of treatment, payment or health care operations, most uses and disclosures are permitted only with authorization • Individuals may revoke their authorization(s) • May request restriction of uses and disclosures by providers 18 • Access to health information • Amendment and correction of health information • Accounting for disclosures of health information S IDLEY & A USTIN
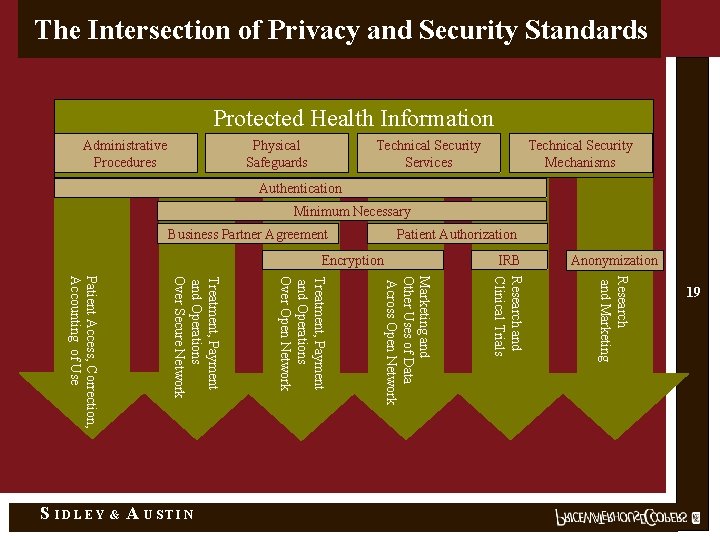
The Intersection of Privacy and Security Standards Protected Health Information Administrative Procedures Physical Safeguards Technical Security Services Technical Security Mechanisms Authentication Minimum Necessary Business Partner Agreement Patient Authorization Anonymization Research and Marketing A USTIN Marketing and Other Uses of Data Across Open Network & Treatment, Payment and Operations Over Open Network Treatment, Payment and Operations Over Secure Network Patient Access, Correction, Accounting of Use S IDLEY IRB Research and Clinical Trials Encryption 19

Security Requirements S IDLEY & A USTIN
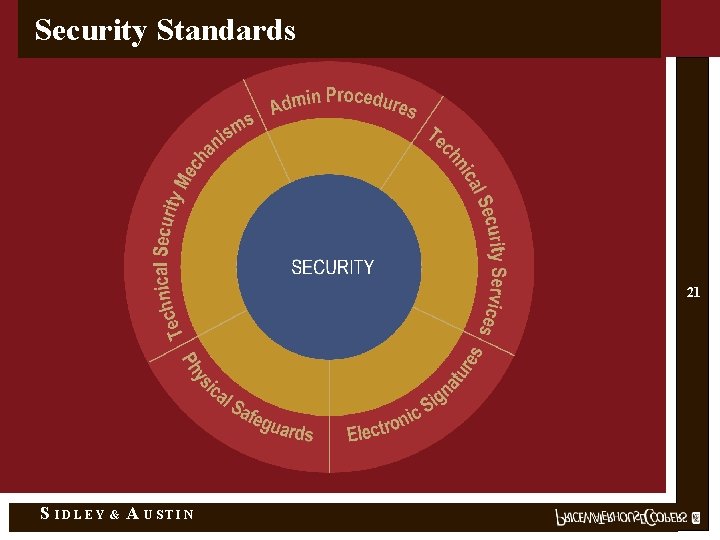
Security Standards 21 S IDLEY & A USTIN
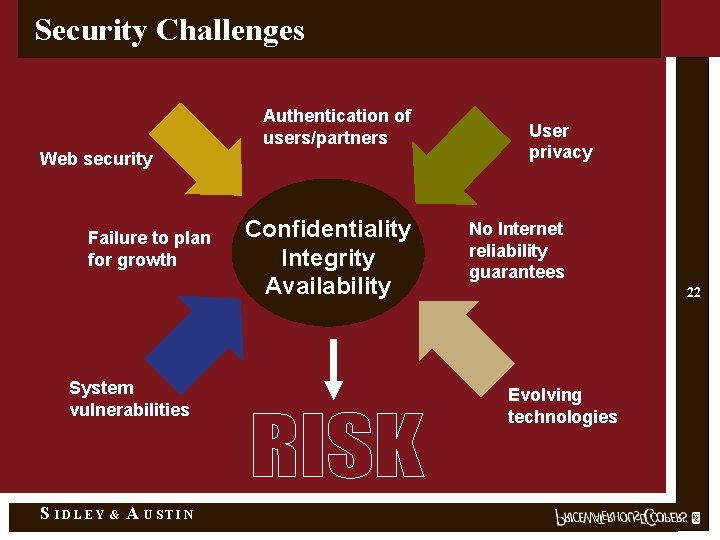
Security Challenges Authentication of users/partners Web security Failure to plan for growth System vulnerabilities S IDLEY & A USTIN Confidentiality Integrity Availability User privacy No Internet reliability guarantees 22 Evolving technologies

Administrative Procedures • • • Certification Chain of Trust Partner Agreement Contingency Plan Formal Mechanism for Processing Records Information Access Control Internal Audit Personnel Security Configuration Management Security Incident Procedures Security Management Process Termination Procedures Training S IDLEY & A USTIN 23

Physical Safeguards • Assigned Security Responsibility • Media Controls • Physical Access Controls • Policy/Guideline on Workstation Use • Secure Work Station Use • Security Awareness Training S IDLEY & A USTIN 24

Technical Security Services • Access Control • Audit Controls • Authorization Control • Data Authentication • Entity Authentication S IDLEY & A USTIN 25
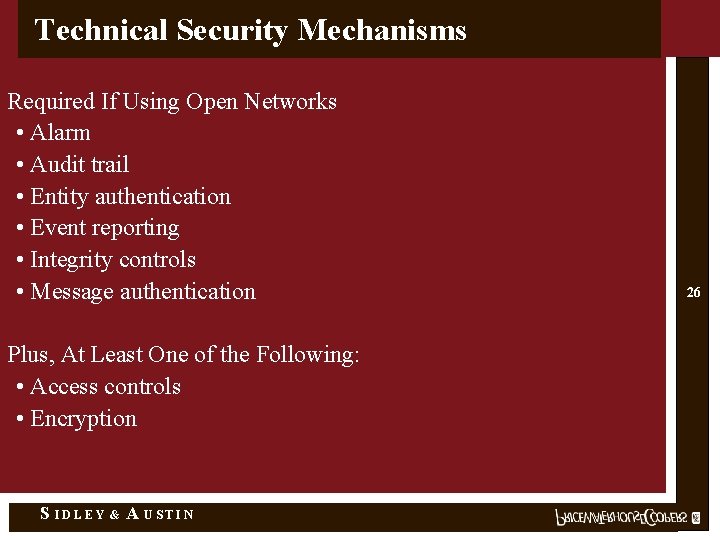
Technical Security Mechanisms Required If Using Open Networks • Alarm • Audit trail • Entity authentication • Event reporting • Integrity controls • Message authentication Plus, At Least One of the Following: • Access controls • Encryption S IDLEY & A USTIN 26

HIPAA Compliance Framework S IDLEY & A USTIN
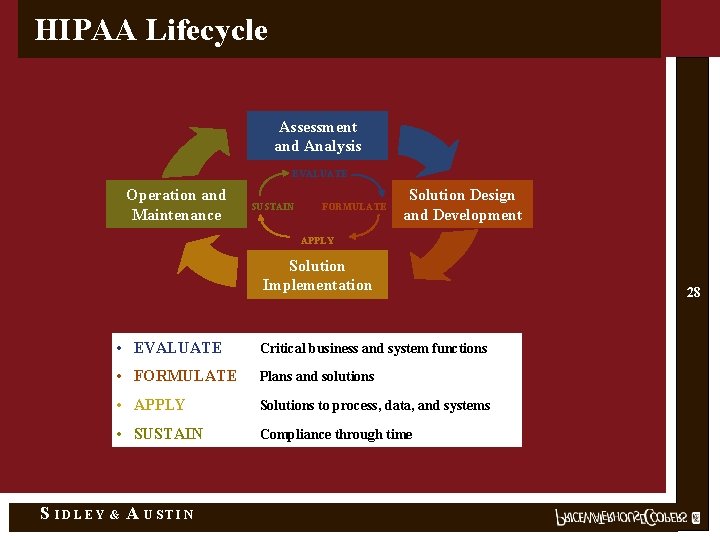
HIPAA Lifecycle Assessment and Analysis EVALUATE Operation and Maintenance SUSTAIN FORMULATE Solution Design and Development APPLY Solution Implementation S IDLEY • EVALUATE Critical business and system functions • FORMULATE Plans and solutions • APPLY Solutions to process, data, and systems • SUSTAIN Compliance through time & A USTIN 28
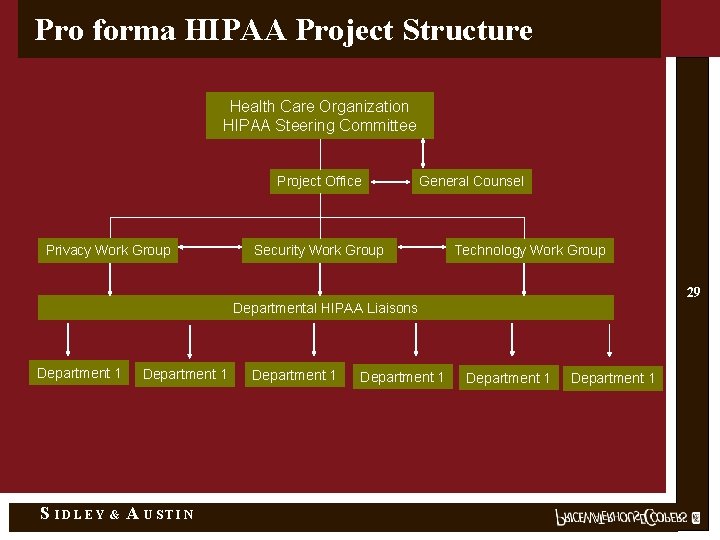
Pro forma HIPAA Project Structure Health Care Organization HIPAA Steering Committee Project Office Privacy Work Group General Counsel Security Work Group Technology Work Group 29 Departmental HIPAA Liaisons Department 1 S IDLEY & Department 1 A USTIN Department 1
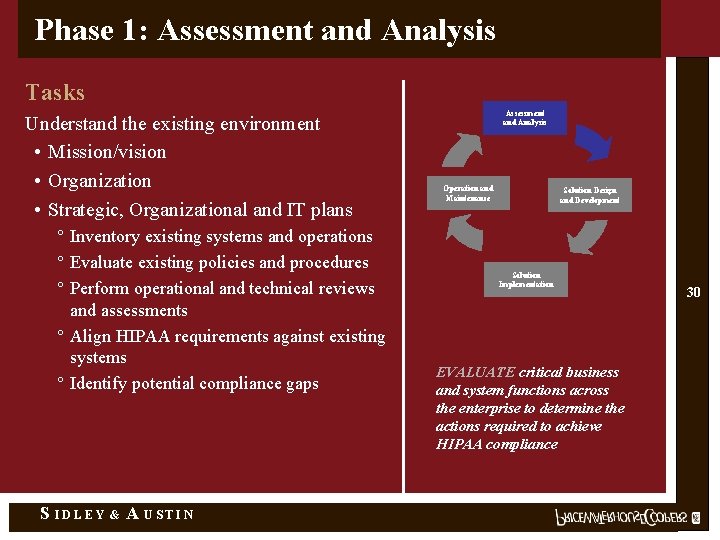
Phase 1: Assessment and Analysis Tasks Understand the existing environment • Mission/vision • Organization • Strategic, Organizational and IT plans ° Inventory existing systems and operations ° Evaluate existing policies and procedures ° Perform operational and technical reviews and assessments ° Align HIPAA requirements against existing systems ° Identify potential compliance gaps S IDLEY & A USTIN Assessment and Analysis Operation and Maintenance Solution Design and Development Solution Implementation EVALUATE critical business and system functions across the enterprise to determine the actions required to achieve HIPAA compliance 30
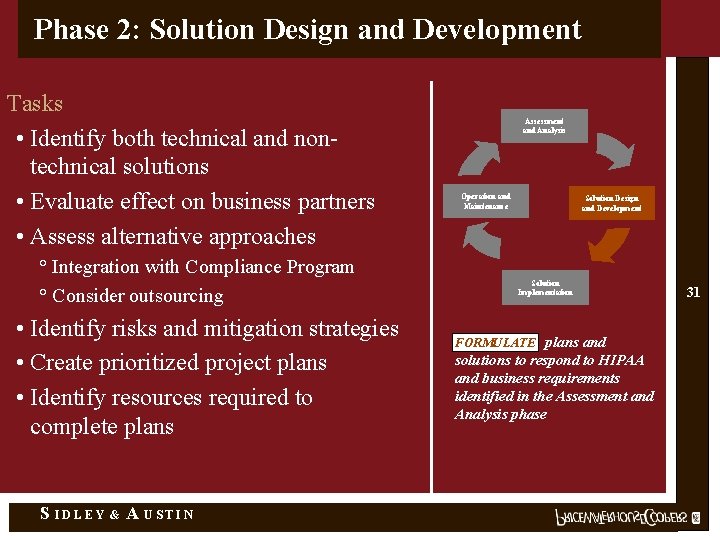
Phase 2: Solution Design and Development Tasks • Identify both technical and nontechnical solutions • Evaluate effect on business partners • Assess alternative approaches ° Integration with Compliance Program ° Consider outsourcing • Identify risks and mitigation strategies • Create prioritized project plans • Identify resources required to complete plans S IDLEY & A USTIN Assessment and Analysis Operation and Maintenance Solution Design and Development Solution Implementation FORMULATE plans and solutions to respond to HIPAA and business requirements identified in the Assessment and Analysis phase 31
Phase 3: Solution Implementation Tasks • Implement communication strategy • Execute project plans • Perform testing and quality assurance • Provide end user training Assessment and Analysis Operation and Maintenance Solution Design and Development Solution Implementation APPLY solutions developed to those business and system functions necessary to ensure compliance with HIPAA regulations S IDLEY & A USTIN 32
Phase 4: Operation and Maintenance Tasks • Keep documentation current as changes occur ° New systems and technology ° Organizational (i. e. , mergers and acquisitions) • Periodically test system vulnerabilities • Institutionalize ongoing HIPAA compliance S IDLEY & A USTIN Assessment and Analysis Operation and Maintenance Solution Design and Development Solution Implementation SUSTAIN a compliant environment through ongoing initiatives 33

Critical Success Factors • Enterprise-wide planning • Align HIPAA initiatives with corporate strategy(s) and integrate into operations • Secure management support and awareness • Leverage historic and on-going initiatives and accumulated knowledge (Y 2 K, E-Business, Business Transformation, etc. . ) • Build HIPAA into existing change initiatives (do it once) • Integrate with current Compliance Program activities S IDLEY & A USTIN • Establish clear governance structure to manage complexities and interdependencies among business units and the technology, security and privacy requirements of HIPAA • Ensure on-going communication channels for HIPAA specific initiatives • Raise corporate awareness of HIPAA and its potential impacts on the origination and its stakeholders • Incorporate HIPAA into existing compliance program 34
- Slides: 34