Sept 2004 doc IEEE 802 15 04 0494



- Slides: 14

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Project: IEEE P 802. 15 Working Group for Wireless Personal Area Networks (WPANs) Submission Title: [New Protocol to Solve the Deadlock of IEEE 802. 15. 4 MAC] Date Submitted: [Sept. 2004] Source: [Liang Li, Xin Wang, Chenyang Yang, Zhijian Hu ] Company: [WXZJ Inc. ] Address: [Building D, No. 2, Shangdi Xin. Xi Lu, Beijing, China 100085 ] Voice: [], E-Mail: [liang_1@yahoo. com] Re: [ IEEE 802. 15. 4 b ] Abstract: [This contribution proposes an enhanced MAC for TG 4. ] Purpose: [Response to the call for proposal of IEEE 802. 15. 4 b, Doc Number: 15 -04 -0366 -00 -004 b] Notice: This document has been prepared to assist the IEEE P 802. 15. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) reserve(s) the right to add, amend or withdraw material contained herein. Release: The contributor acknowledges and accepts that this contribution becomes the property of IEEE and may be made publicly available by P 802. 15. Submission 1 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Proposal • Enhance the IEEE 802. 15. 4 CSMA/CA algorithm – Solving the deadlock problems – Achieving the High throughput – Keeping the High energy efficiency Submission 2 Liang Li, WXZJ Inc. /Helicomm

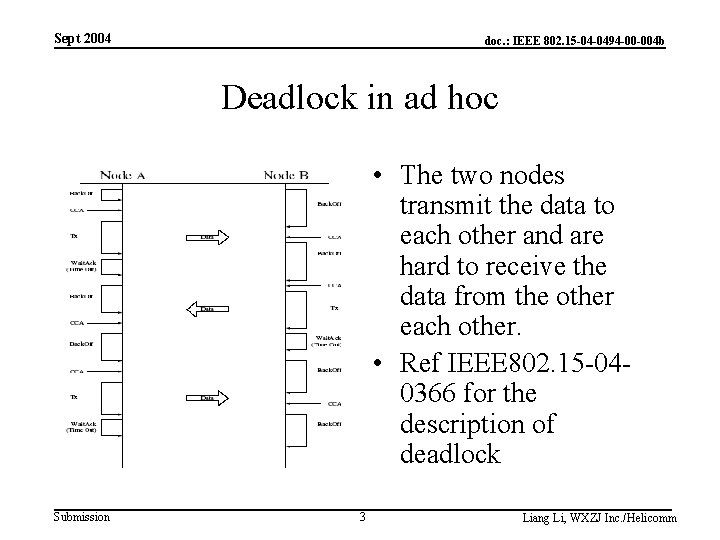
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Deadlock in ad hoc • The two nodes transmit the data to each other and are hard to receive the data from the other each other. • Ref IEEE 802. 15 -040366 for the description of deadlock Submission 3 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b State Chart with current CSMA/CA • Once one node enters this circle, it can not receive the data frames until it transmits the data successfully or abandons the transmission. Submission 4 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b The Deadlock in the States Viewpoint • When a node is in State 1, it can’t receive the data from the nodes within State 2, nor it sends the ack to nodes within State 3. • When a node is within State 2, it will make other nodes failed to contend the channel. • When a node is within State 3, it can’t receive the data from the nodes in State 2. Submission 5 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b New CSMA/CA: Monitoring the Channel and Adding the Backoff Counter • Set the node within State 1 and may monitor the channel and receive the data , then send the acknowledgement back. The backoff counter is introduced. • The deadlock circle may be broken in such way. Submission 6 Liang Li, WXZJ Inc. /Helicomm

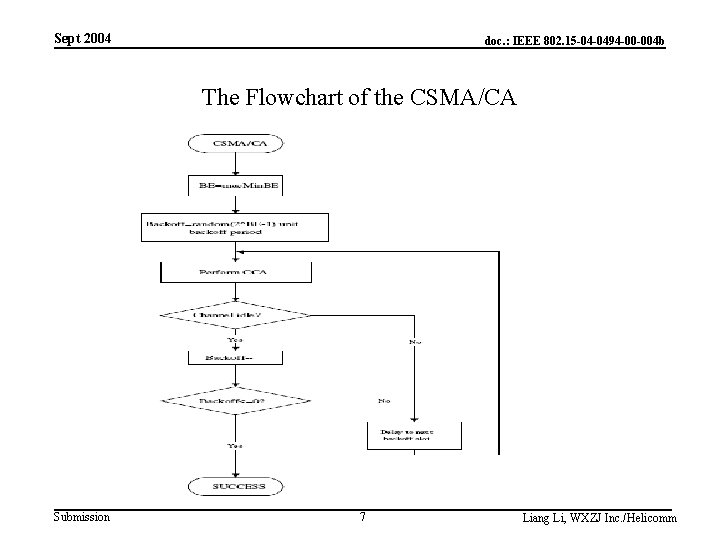
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b The Flowchart of the CSMA/CA Submission 7 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b The Simple Explanation to the New CSMA/CA Algorithm • The node should decrease the backoff counter if the channel is idle, otherwise it should pause the decreasing of the backoff counter. • When there is packet transmitting in the channel, the node who is in backoff state will detect a busy channel. The backoff counter of this node will not decrease in this period. When the packet has been received, the node will process the packet first and send back the ACK if necessary. Then the backoff counter will continue to decease since the channel is idle. Submission 8 Liang Li, WXZJ Inc. /Helicomm

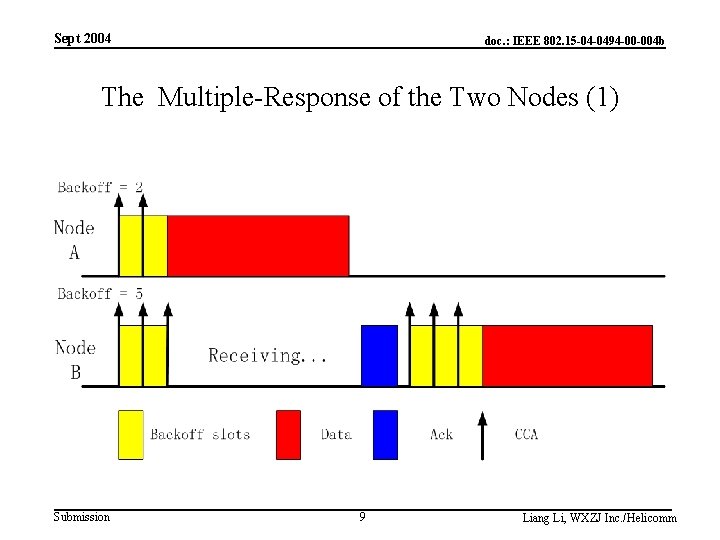
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b The Multiple-Response of the Two Nodes (1) Submission 9 Liang Li, WXZJ Inc. /Helicomm

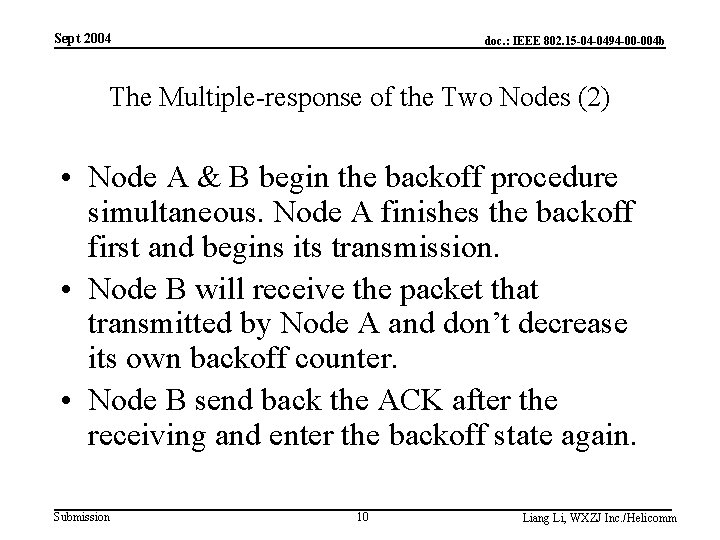
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b The Multiple-response of the Two Nodes (2) • Node A & B begin the backoff procedure simultaneous. Node A finishes the backoff first and begins its transmission. • Node B will receive the packet that transmitted by Node A and don’t decrease its own backoff counter. • Node B send back the ACK after the receiving and enter the backoff state again. Submission 10 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Simulation with new MAC Protocol (1) • We test our new mac protocol in a linear ad hoc networks. • The throughput and energy-efficiency have been tested. • The throughput is defined as the end-to-end throughput when packets are transmitted in multihop. Submission 11 Liang Li, WXZJ Inc. /Helicomm

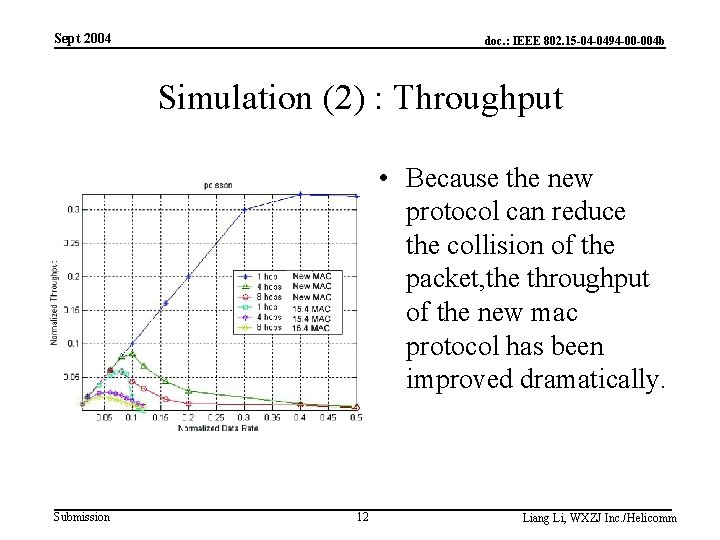
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Simulation (2) : Throughput • Because the new protocol can reduce the collision of the packet, the throughput of the new mac protocol has been improved dramatically. Submission 12 Liang Li, WXZJ Inc. /Helicomm

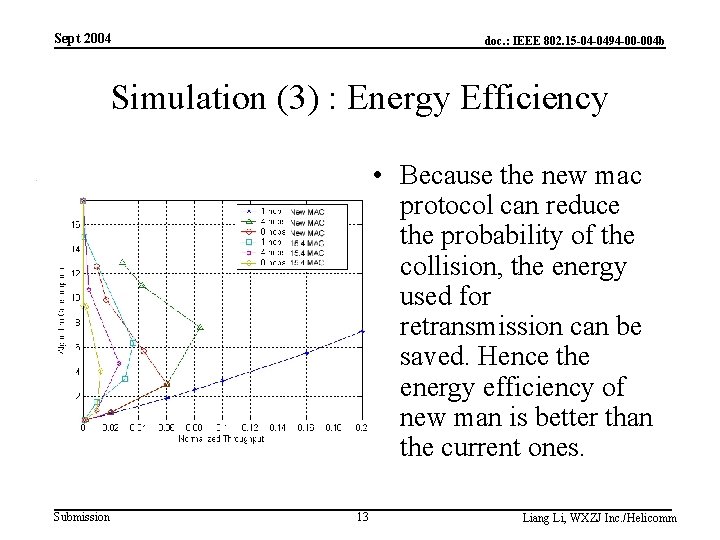
Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Simulation (3) : Energy Efficiency • Because the new mac protocol can reduce the probability of the collision, the energy used for retransmission can be saved. Hence the energy efficiency of new man is better than the current ones. Submission 13 Liang Li, WXZJ Inc. /Helicomm

Sept 2004 doc. : IEEE 802. 15 -04 -0494 -00 -004 b Conclusion • The backoff counter is introduced to break the deadlock circle. Each node needs to monitor the coming data. • This modification can improve throughput of the network and achieve the better energy efficiency. Submission 14 Liang Li, WXZJ Inc. /Helicomm