Select and Implement an Intrusion Detection and Prevention


- Slides: 9

Select and Implement an Intrusion Detection and Prevention System Reduce risks to critical systems and data with IDPS-enabled visibility and responsiveness. Info-Tech Research Group, Inc. is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with ready-to-use tools and templates that cover the full spectrum of IT concerns. © 1997 -2015 Info-Tech Research Group Inc. Info-Tech Research Group 1

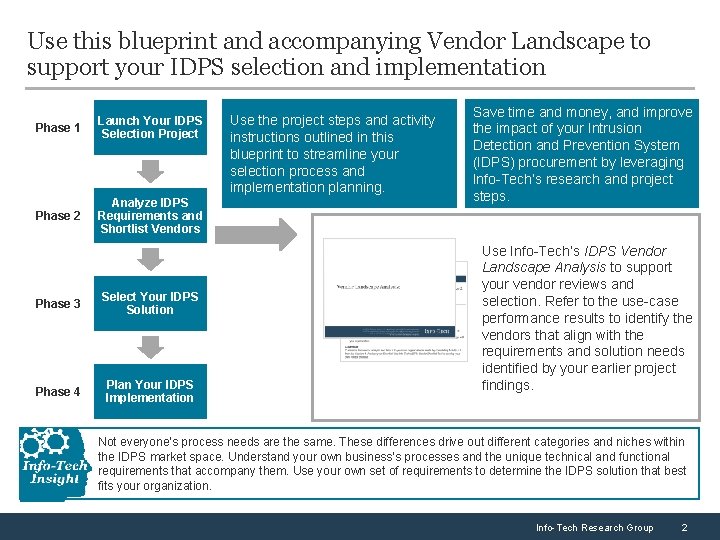
Use this blueprint and accompanying Vendor Landscape to support your IDPS selection and implementation Phase 1 Launch Your IDPS Selection Project Phase 2 Analyze IDPS Requirements and Shortlist Vendors Phase 3 Select Your IDPS Solution Phase 4 Plan Your IDPS Implementation Use the project steps and activity instructions outlined in this blueprint to streamline your selection process and implementation planning. Save time and money, and improve the impact of your Intrusion Detection and Prevention System (IDPS) procurement by leveraging Info-Tech’s research and project steps. Use Info-Tech’s IDPS Vendor Landscape Analysis to support your vendor reviews and selection. Refer to the use-case performance results to identify the vendors that align with the requirements and solution needs identified by your earlier project findings. Not everyone’s process needs are the same. These differences drive out different categories and niches within the IDPS market space. Understand your own business’s processes and the unique technical and functional requirements that accompany them. Use your own set of requirements to determine the IDPS solution that best fits your organization. Info-Tech Research Group 2

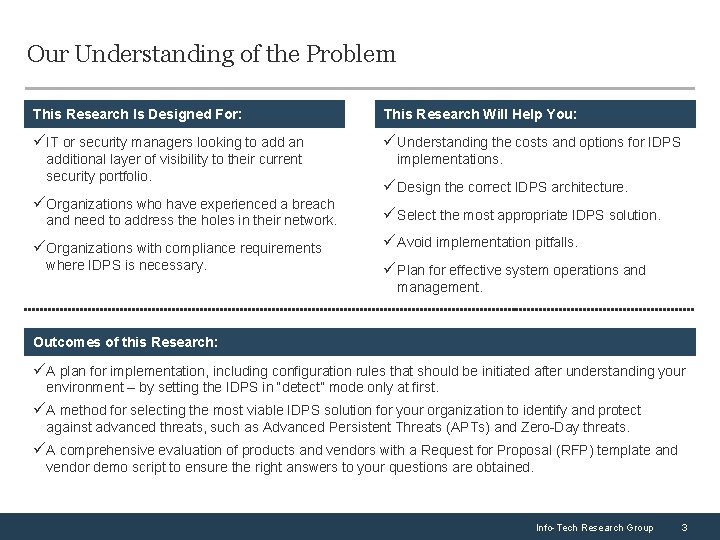
Our Understanding of the Problem This Research Is Designed For: This Research Will Help You: üIT or security managers looking to add an üUnderstanding the costs and options for IDPS additional layer of visibility to their current security portfolio. üOrganizations who have experienced a breach and need to address the holes in their network. üOrganizations with compliance requirements where IDPS is necessary. implementations. üDesign the correct IDPS architecture. üSelect the most appropriate IDPS solution. üAvoid implementation pitfalls. üPlan for effective system operations and management. Outcomes of this Research: üA plan for implementation, including configuration rules that should be initiated after understanding your environment – by setting the IDPS in “detect” mode only at first. üA method for selecting the most viable IDPS solution for your organization to identify and protect against advanced threats, such as Advanced Persistent Threats (APTs) and Zero-Day threats. üA comprehensive evaluation of products and vendors with a Request for Proposal (RFP) template and vendor demo script to ensure the right answers to your questions are obtained. Info-Tech Research Group 3

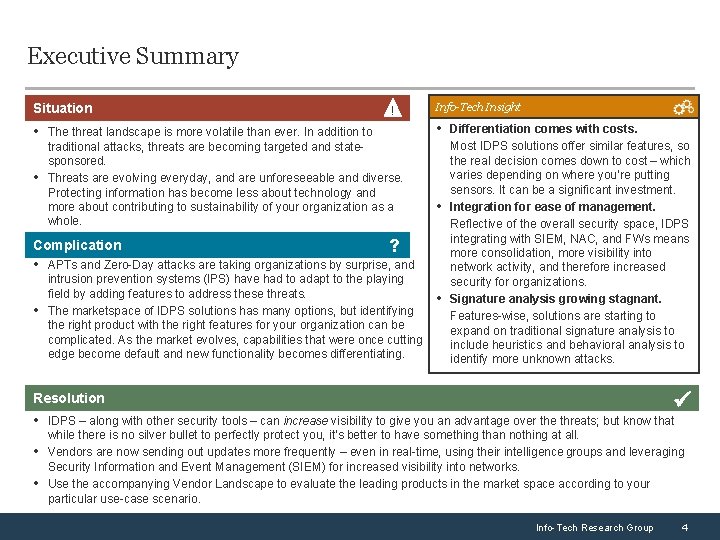
Executive Summary Situation ! • Differentiation comes with costs. • The threat landscape is more volatile than ever. In addition to • traditional attacks, threats are becoming targeted and statesponsored. Threats are evolving everyday, and are unforeseeable and diverse. Protecting information has become less about technology and more about contributing to sustainability of your organization as a whole. Complication Info-Tech Insight • ? • APTs and Zero-Day attacks are taking organizations by surprise, and • intrusion prevention systems (IPS) have had to adapt to the playing field by adding features to address these threats. The marketspace of IDPS solutions has many options, but identifying the right product with the right features for your organization can be complicated. As the market evolves, capabilities that were once cutting edge become default and new functionality becomes differentiating. • Most IDPS solutions offer similar features, so the real decision comes down to cost – which varies depending on where you’re putting sensors. It can be a significant investment. Integration for ease of management. Reflective of the overall security space, IDPS integrating with SIEM, NAC, and FWs means more consolidation, more visibility into network activity, and therefore increased security for organizations. Signature analysis growing stagnant. Features-wise, solutions are starting to expand on traditional signature analysis to include heuristics and behavioral analysis to identify more unknown attacks. Resolution • IDPS – along with other security tools – can increase visibility to give you an advantage over the threats; but know that • • while there is no silver bullet to perfectly protect you, it’s better to have something than nothing at all. Vendors are now sending out updates more frequently – even in real-time, using their intelligence groups and leveraging Security Information and Event Management (SIEM) for increased visibility into networks. Use the accompanying Vendor Landscape to evaluate the leading products in the market space according to your particular use-case scenario. Info-Tech Research Group 4

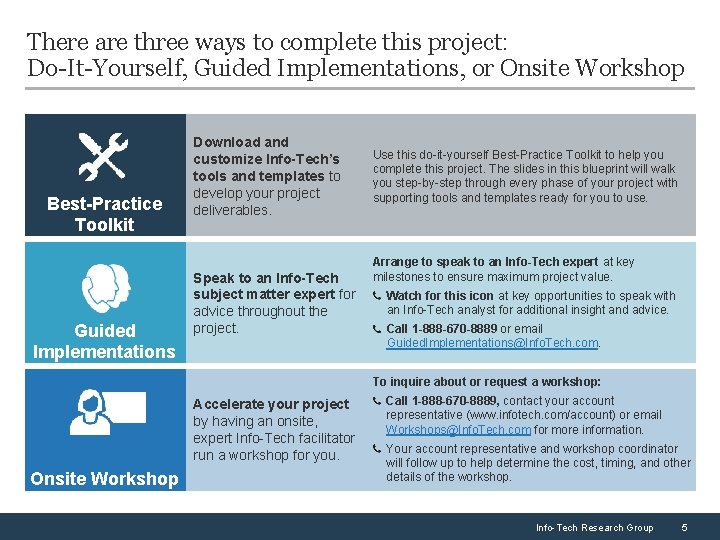
There are three ways to complete this project: Do-It-Yourself, Guided Implementations, or Onsite Workshop Best-Practice Toolkit Guided Implementations Download and customize Info-Tech’s tools and templates to develop your project deliverables. Speak to an Info-Tech subject matter expert for advice throughout the project. Use this do-it-yourself Best-Practice Toolkit to help you complete this project. The slides in this blueprint will walk you step-by-step through every phase of your project with supporting tools and templates ready for you to use. Arrange to speak to an Info-Tech expert at key milestones to ensure maximum project value. Watch for this icon at key opportunities to speak with an Info-Tech analyst for additional insight and advice. Call 1 -888 -670 -8889 or email Guided. Implementations@Info. Tech. com. To inquire about or request a workshop: Accelerate your project by having an onsite, expert Info-Tech facilitator run a workshop for you. Onsite Workshop Call 1 -888 -670 -8889, contact your account representative (www. infotech. com/account) or email Workshops@Info. Tech. com for more information. Your account representative and workshop coordinator will follow up to help determine the cost, timing, and other details of the workshop. Info-Tech Research Group 5

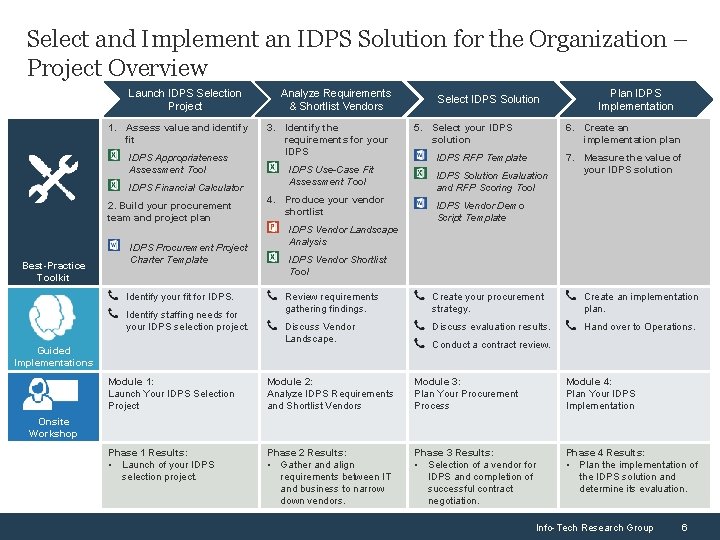
Select and Implement an IDPS Solution for the Organization – Project Overview Launch IDPS Selection Project 1. Assess value and identify fit IDPS Appropriateness Assessment Tool IDPS Financial Calculator 2. Build your procurement team and project plan Best-Practice Toolkit IDPS Procurement Project Charter Template Identify your fit for IDPS. Identify staffing needs for your IDPS selection project. Analyze Requirements & Shortlist Vendors 3. Identify the requirements for your IDPS Use-Case Fit Assessment Tool 4. Produce your vendor shortlist Select IDPS Solution 5. Select your IDPS solution Plan IDPS Implementation 6. Create an implementation plan IDPS RFP Template IDPS Solution Evaluation and RFP Scoring Tool 7. Measure the value of your IDPS solution IDPS Vendor Demo Script Template IDPS Vendor Landscape Analysis IDPS Vendor Shortlist Tool Review requirements gathering findings. Create your procurement strategy. Create an implementation plan. Discuss Vendor Landscape. Discuss evaluation results. Hand over to Operations. Guided Implementations Conduct a contract review. Module 1: Launch Your IDPS Selection Project Module 2: Analyze IDPS Requirements and Shortlist Vendors Module 3: Plan Your Procurement Process Module 4: Plan Your IDPS Implementation Phase 1 Results: • Launch of your IDPS selection project. Phase 2 Results: • Gather and align requirements between IT and business to narrow down vendors. Phase 3 Results: • Selection of a vendor for IDPS and completion of successful contract negotiation. Phase 4 Results: • Plan the implementation of the IDPS solution and determine its evaluation. Onsite Workshop Info-Tech Research Group 6

Workshop Overview Contact your account representative or email Workshops@Info. Tech. com for more information. This workshop can be deployed as either a four- or five-day engagement depending on the client’s level of completed preparation prior to the facilitator’s arrival onsite. Day 1 Preparation Workshop Preparation • Review current network security technologies. • Conduct interviews. Day 2 Workshop Day 3 Workshop Day 4 Workshop Day 5 Working Session Morning Itinerary Workshop Debrief • Identify the drivers behind the IDPS procurement. • Complete the IDPS Appropriateness Assessment Tool. • Discuss cost-benefits; complete IDPS Financial Calculator. • Create a project plan for IDPS selection. • Determine metrics to evaluate selection process and IDPS performance. • Select the pilot. • Create & prioritize solution requirements. • Create an RFP to submit to vendors. • Evaluate RFPs received. • Review documents. Afternoon Itinerary • Identify the scope and purpose. • Select the staff resourcing. • Identify stakeholders. Afternoon Itinerary • Determine your use-case scenario; complete the IDPS Use-Case Fit Assessment Tool. • Analyze relevant Vendor Landscape use-case results. • Customize vendor analysis, compete IDPS Vendor Shortlist Tool. • Create a demo script. • Discuss the IDPS implementation plan. Next Steps • Analyst calls to provide guidance during the selection and implementation processes. The light blue slides at the end of each section highlight the key activities and exercises that will be completed during the engagement with our analyst team. Info-Tech Research Group 7

Use these icons to help direct you as you navigate this research Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities. This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project. This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization. This icon denotes a slide that pertains directly to the Info-Tech Vendor Landscape on IDPS. Use these slides to support and guide your evaluation of the IDPS vendors included in the research. Info-Tech Research Group 8

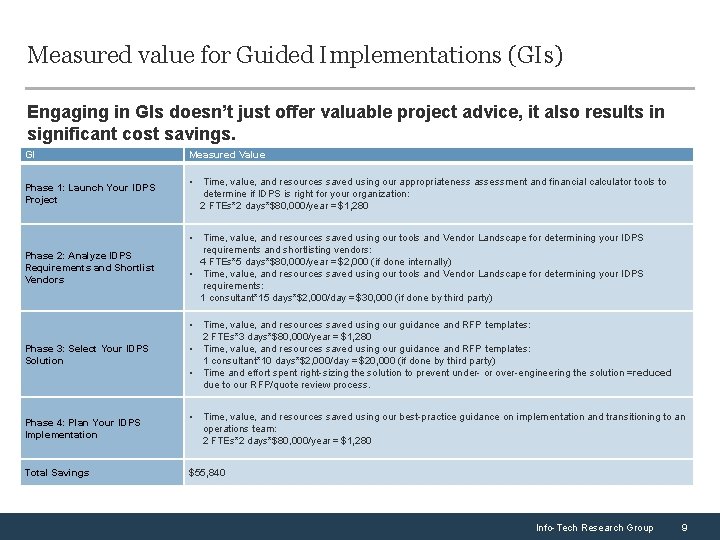
Measured value for Guided Implementations (GIs) Engaging in GIs doesn’t just offer valuable project advice, it also results in significant cost savings. GI Measured Value Phase 1: Launch Your IDPS Project • Time, value, and resources saved using our appropriateness assessment and financial calculator tools to determine if IDPS is right for your organization: 2 FTEs*2 days*$80, 000/year = $1, 280 Phase 2: Analyze IDPS Requirements and Shortlist Vendors • Time, value, and resources saved using our tools and Vendor Landscape for determining your IDPS requirements and shortlisting vendors: 4 FTEs*5 days*$80, 000/year = $2, 000 (if done internally) • Time, value, and resources saved using our tools and Vendor Landscape for determining your IDPS requirements: 1 consultant*15 days*$2, 000/day = $30, 000 (if done by third party) Phase 3: Select Your IDPS Solution • Time, value, and resources saved using our guidance and RFP templates: 2 FTEs*3 days*$80, 000/year = $1, 280 • Time, value, and resources saved using our guidance and RFP templates: 1 consultant*10 days*$2, 000/day = $20, 000 (if done by third party) • Time and effort spent right-sizing the solution to prevent under- or over-engineering the solution = reduced due to our RFP/quote review process. Phase 4: Plan Your IDPS Implementation • Time, value, and resources saved using our best-practice guidance on implementation and transitioning to an operations team: 2 FTEs*2 days*$80, 000/year = $1, 280 Total Savings $55, 840 Info-Tech Research Group 9