Security Update Server Registration Active scanning and Windows












- Slides: 17

Security Update Server Registration, Active scanning and Windows patching

Bastion Host Policy • Ensure that critical servers are managed with appropriate levels of security • Define the overheads: management, operation and security • Identify all network servers and establish purpose, security requirements, user base and support staff • Limit exposure of network servers to those apps that are critical for their primary purpose • Establish network ACLs for specific IP applications. ACLs will restrict access to specific apps to those servers that have been registered to provide them

Bastion Host • A network system that may be exposed to attack from other internal or external network systems • Deployed, configured, operated and managed in a manner that mitigates this exposure • Fulfills a specific role • All unnecessary services, protocols, applications disabled or removed • Avoids trust relationships with other systems to guard against 'key to the castle' attacks • Apply bastion host principles to all University servers

Role • Purpose - services and applications • User community • Sensitivity • Legal / regulatory requirements • Security Considerations • Availability requirements

Location • Physical security • Environmental – Air conditioning – Emergency power source – Fire prevention • Dedicated network ports • Not in staff offices

Management, Support and Operation • Identify personnel responsible – – System administrators System operators Application support specialists Maintenance contractors • At least 2 individuals identified with at least one being the system administrator

Management, Support and Operation 2 • Asset register detailing hardware and software components, including licensed software • System configuration details inc security measures and details of admin/root accounts • System change procedures – including reversion procedures • Contractors callout procedures • Disaster recovery plans

Sys Admin Guidelines

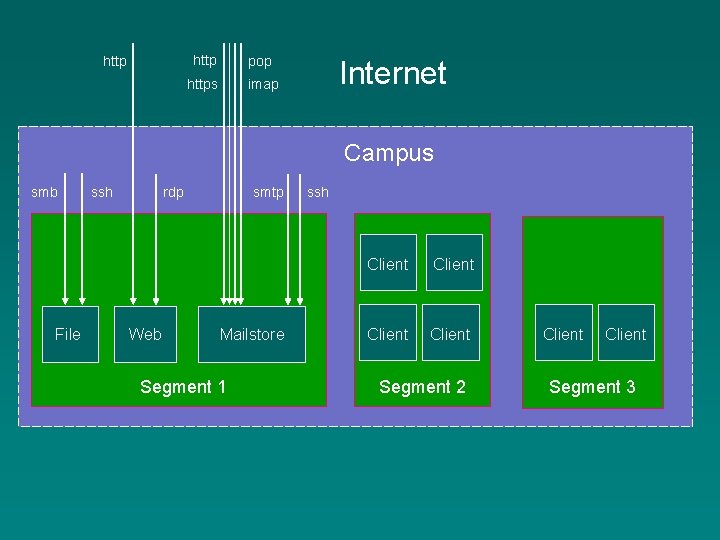
Protection via the Network • Filtering policies – Default allow – Default deny • Default deny – Inbound – Outbound ? • Protect – Servers – Clients

http pop https imap Internet Campus smb File ssh rdp Web smtp Mailstore Segment 1 ssh Client Segment 2 Client Segment 3

Server Registration Database • Demo

Friendly Probing • Identify remotely exploitable systems – new machines missing critical patches – old machines brought out of the cupboard • Locate holes before the enemy do • Automatic notification for IT staff • Initially, testing the most critical Microsoft holes – Then including other OSes • Scanner host: friendly-probe 1. cent. gla. ac. uk ( currently 130. 209. 16. 157 )

Windows Patching • TRG working group investigated options for automated patching of Microsoft systems • Recommended WSUS • Evolution: – SUS – WSUS • Available at: www. gla. ac. uk/cert/wsus/

Patch Classes • Updates Installed – Security Updates – Critical Updates – Definition Updates (Windows Defender) – Service Packs – Update Roll Ups – Tools – Updates (non-critical fixes) • Not Installed – Drivers – Feature packs

Does not help with: • Weak passwords • Lack of configuration hardening – Removing unneeded services better than patching • Executing untrustworthy code • Social Engineering

Thanks: Andrew Cooper Steve Mc. Intosh - WSUS Service Derek Higgins - Server Registration System

That’s all folks! Questions…