Security Training and Certification A look at why





- Slides: 9


Security Training and Certification A look at why security should become a part of your DNA

A little about me Jedi Hammond Certification Strategy Lead Dell EMC Proven Professional Program Over 20 years in IT Some Career Roles Include: IT management, IT administration, product development, technical and professional skills training, and certification program management.

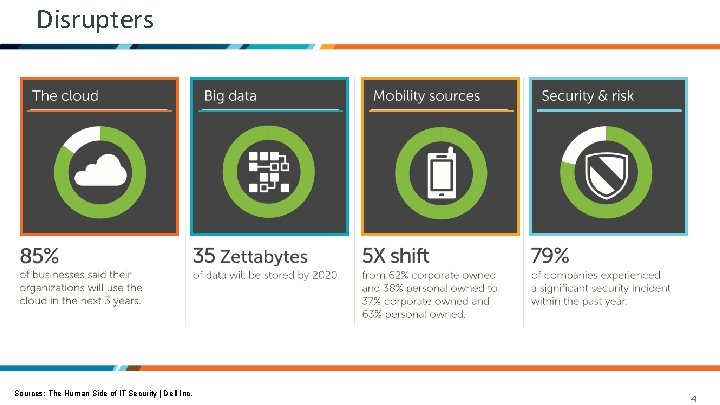
Disrupters Sources: The Human Side of IT Security | Dell Inc. 4

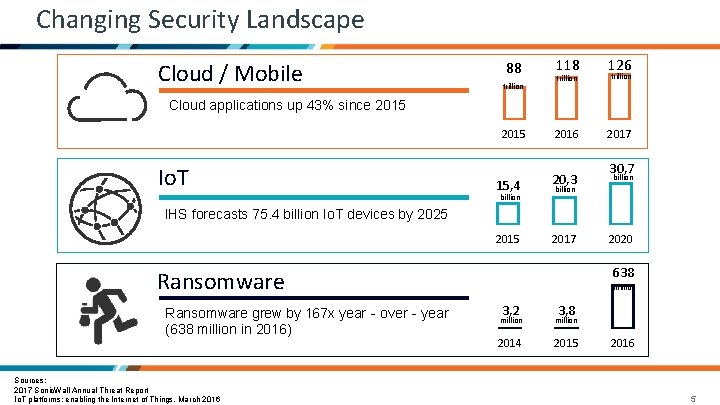
Changing Security Landscape Cloud / Mobile 88 trillion 118 126 2017 20, 3 30, 7 billion 2017 2020 trillion Cloud applications up 43% since 2015 Io. T 15, 4 billion IHS forecasts 75. 4 billion Io. T devices by 2025 2015 638 Ransomware grew by 167 x year‐over‐year (638 million in 2016) Sources: 2017 Sonic. Wall Annual Threat Report Io. T platforms: enabling the Internet of Things, March 2016 million 3, 2 3, 8 million 2014 2015 2016 5

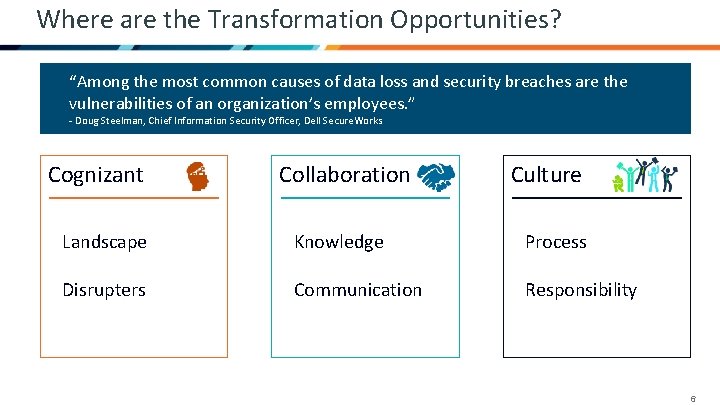
Where are the Transformation Opportunities? “Among the most common causes of data loss and security breaches are the vulnerabilities of an organization’s employees. ” - Doug Steelman, Chief Information Security Officer, Dell Secure. Works Cognizant Collaboration Culture Landscape Knowledge Process Disrupters Communication Responsibility 6

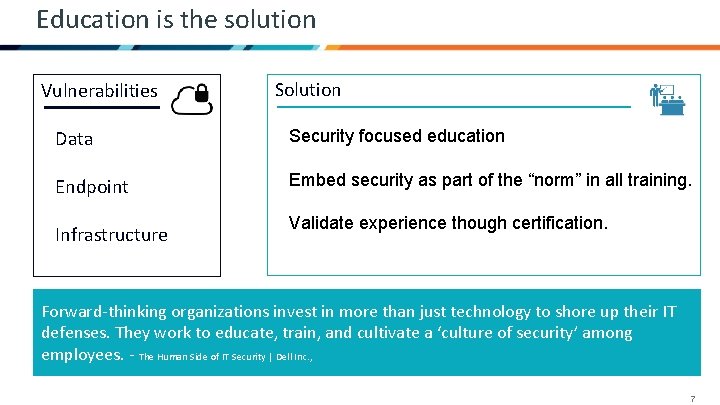
Education is the solution Vulnerabilities Solution Data Security focused education Endpoint Embed security as part of the “norm” in all training. Infrastructure Validate experience though certification. Forward-thinking organizations invest in more than just technology to shore up their IT defenses. They work to educate, train, and cultivate a ‘culture of security’ among employees. - The Human Side of IT Security | Dell Inc. , 7

Final Take away One of the greatest vulnerabilities in today’s security are people with a knowledge gap. The solution is fully educated people. 8
