Security Testing Solutions for Software Applications July 3


- Slides: 15

Security Testing Solutions for Software Applications July 3 rd, 2010

Our Objective for today v Discuss on some of our common security concerns in any organization v Identify our priority area on Security Testing v What approach do we take to build Solutions around Security Testing v Discuss on key focus areas while building Solutions v A quick overview of Testing Approach under different Situations 2009© Symphony Services Corp. | Proprietary & Confidential

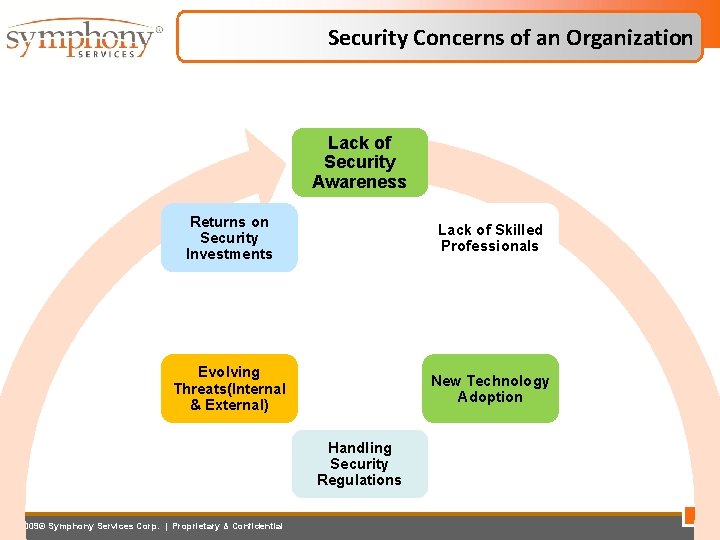
Security Concerns of an Organization Lack of Security Awareness Returns on Security Investments Lack of Skilled Professionals Evolving Threats(Internal & External) New Technology Adoption Handling Security Regulations 2009© Symphony Services Corp. | Proprietary & Confidential

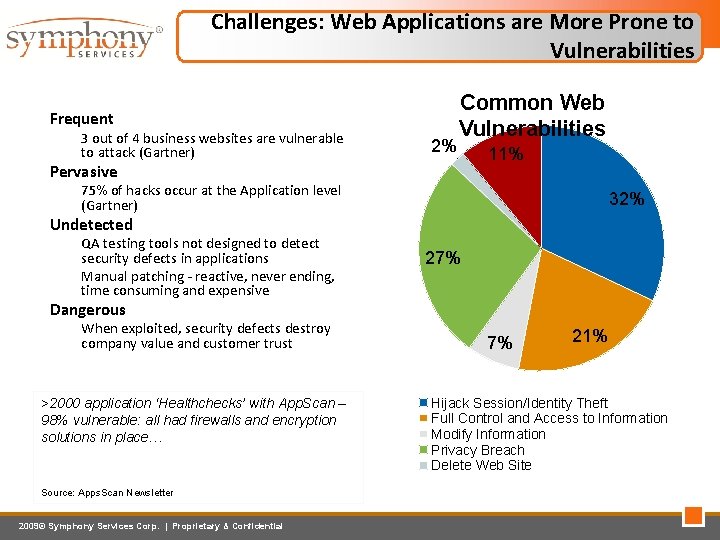
Challenges: Web Applications are More Prone to Vulnerabilities • • Frequent – 3 out of 4 business websites are vulnerable to attack (Gartner) 2% Common Web Vulnerabilities Pervasive 11% – 75% of hacks occur at the Application level (Gartner) 32% Undetected – QA testing tools not designed to detect security defects in applications – Manual patching - reactive, never ending, time consuming and expensive 27% Dangerous – When exploited, security defects destroy company value and customer trust >2000 application ‘Healthchecks’ with App. Scan – 98% vulnerable: all had firewalls and encryption solutions in place… Source: Apps. Scan Newsletter 2009© Symphony Services Corp. | Proprietary & Confidential 7% 21% Hijack Session/Identity Theft Full Control and Access to Information Modify Information Privacy Breach Delete Web Site

Hacking attempts on our favourites Facebook Accounts Hacked Sold Facebook is not able to estimate how many more accounts may be compromised by other hackers. Twitter knocked offline by DDo. S attack. Popular micro blogging service Twitter was knocked offline for an extended period this morning by what appears to be a massive distributed denial-of-service attacks. My. Space, an even larger social networking site with an estimated 250 million users, has been subverted on multiple occasions by malware attackers during Hacking Amazon’s Cloud and Other Web 2. 0 Threats the last year. Amazon’s cloud can be hacked for Bit. Torrent use (and has), and social network sites are hotbeds for cyber crime (surprised? ). 2009© Symphony Services Corp. | Proprietary & Confidential 5

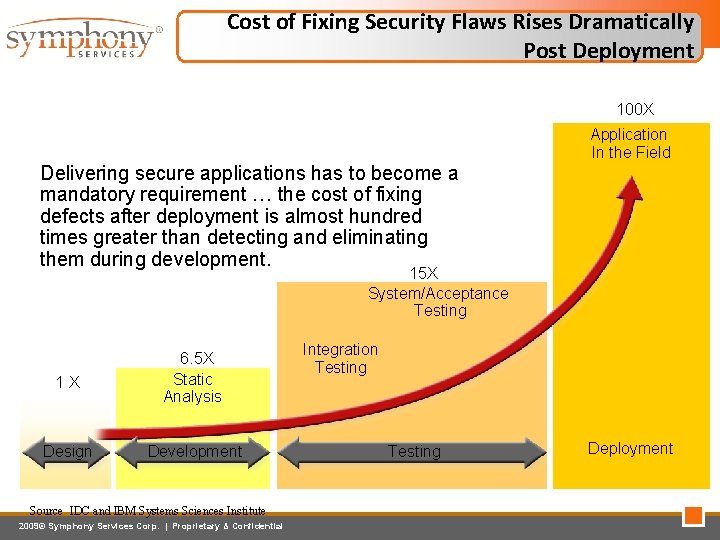
Cost of Fixing Security Flaws Rises Dramatically Post Deployment 100 X Application In the Field Delivering secure applications has to become a mandatory requirement … the cost of fixing defects after deployment is almost hundred times greater than detecting and eliminating them during development. 15 X System/Acceptance Testing 1 X 6. 5 X Static Analysis Design Development Source IDC and IBM Systems Sciences Institute 2009© Symphony Services Corp. | Proprietary & Confidential Integration Testing Deployment

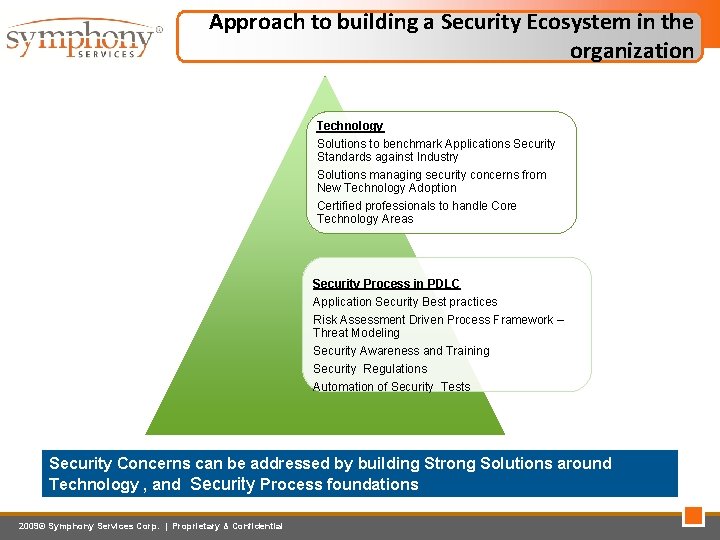
Approach to building a Security Ecosystem in the organization Technology Solutions to benchmark Applications Security Standards against Industry Solutions managing security concerns from New Technology Adoption Certified professionals to handle Core Technology Areas Security Process in PDLC Application Security Best practices Risk Assessment Driven Process Framework – Threat Modeling Security Awareness and Training Security Regulations Automation of Security Tests Security Concerns can be addressed by building Strong Solutions around Technology , and Security Process foundations 2009© Symphony Services Corp. | Proprietary & Confidential

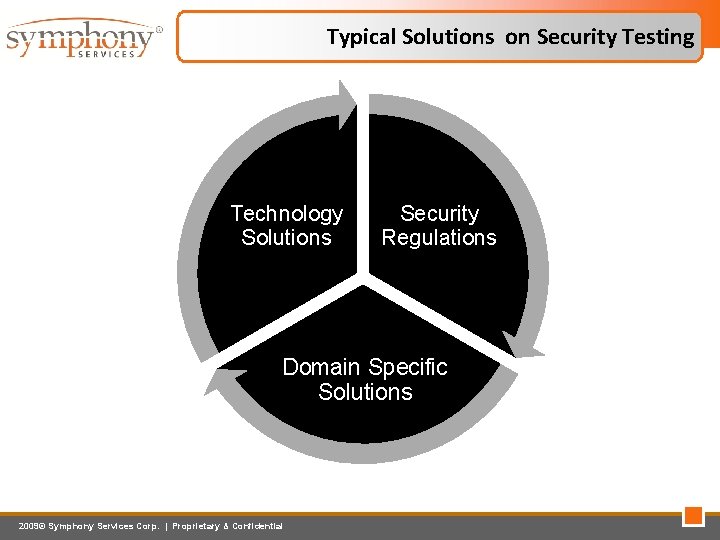
Typical Solutions on Security Testing Technology Solutions Security Regulations Domain Specific Solutions 2009© Symphony Services Corp. | Proprietary & Confidential

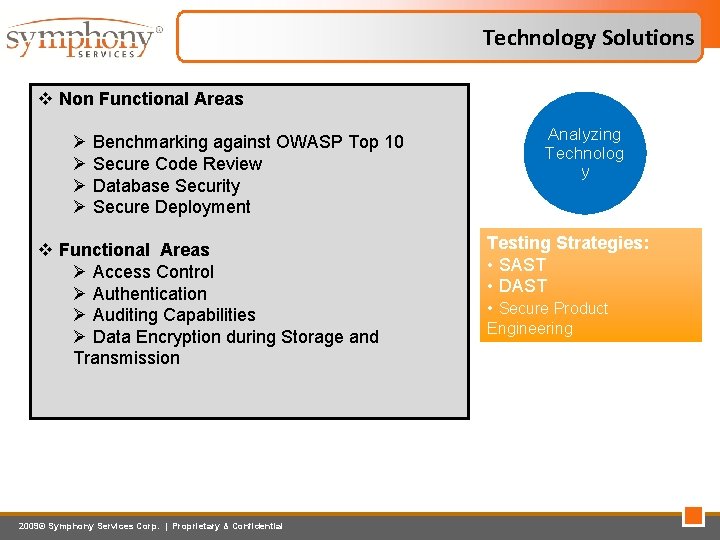
Technology Solutions v Non Functional Areas Ø Benchmarking against OWASP Top 10 Ø Secure Code Review Ø Database Security Ø Secure Deployment v Functional Areas Ø Access Control Ø Authentication Ø Auditing Capabilities Ø Data Encryption during Storage and Transmission 2009© Symphony Services Corp. | Proprietary & Confidential Analyzing Technolog y Testing Strategies: • SAST • DAST • Secure Product Engineering

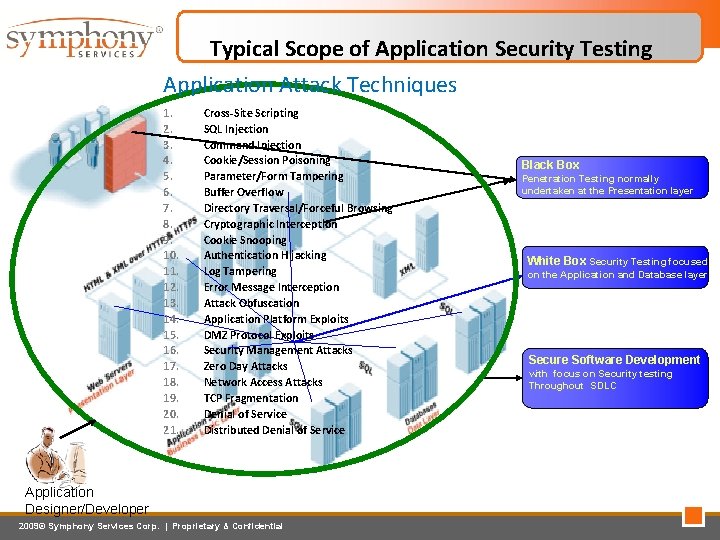
Typical Scope of Application Security Testing Application Attack Techniques 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 19. 20. 21. Cross-Site Scripting SQL Injection Command Injection Cookie/Session Poisoning Parameter/Form Tampering Buffer Overflow Directory Traversal/Forceful Browsing Cryptographic Interception Cookie Snooping Authentication Hijacking Log Tampering Error Message Interception Attack Obfuscation Application Platform Exploits DMZ Protocol Exploits Security Management Attacks Zero Day Attacks Network Access Attacks TCP Fragmentation Denial of Service Distributed Denial of Service Application Designer/Developer 2009© Symphony Services Corp. | Proprietary & Confidential Black Box Penetration Testing normally undertaken at the Presentation layer White Box Security Testing focused on the Application and Database layer Secure Software Development with focus on Security testing Throughout SDLC

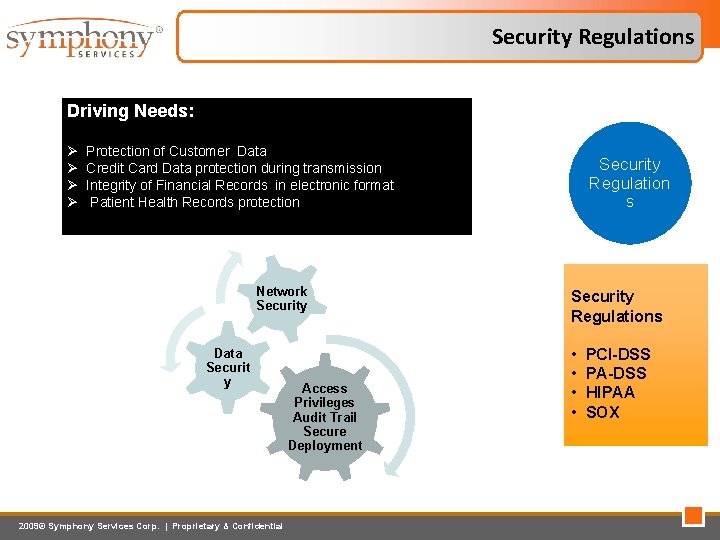
Security Regulations Driving Needs: Ø Ø Protection of Customer Data Credit Card Data protection during transmission Integrity of Financial Records in electronic format Patient Health Records protection Network Security Data Securit y 2009© Symphony Services Corp. | Proprietary & Confidential Access Privileges Audit Trail Secure Deployment Security Regulation s Security Regulations • • PCI-DSS PA-DSS HIPAA SOX

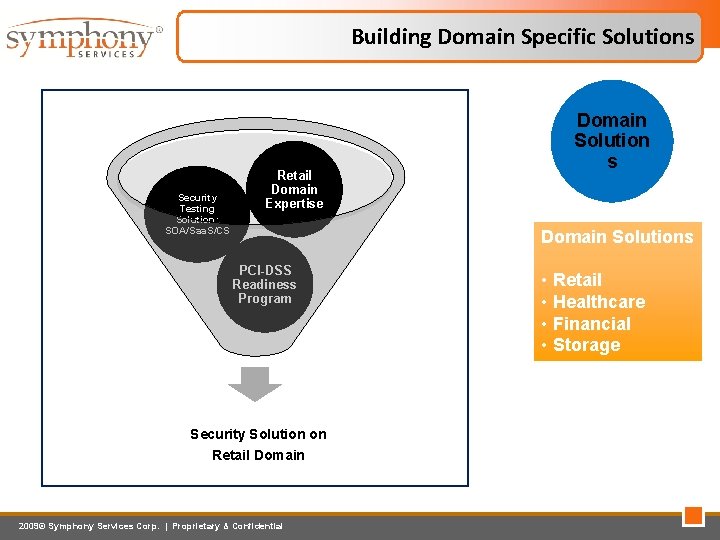
Building Domain Specific Solutions Security Testing Solution: SOA/Saa. S/CS Retail Domain Expertise Domain Solution s Domain Solutions PCI-DSS Readiness Program Security Solution on Retail Domain 2009© Symphony Services Corp. | Proprietary & Confidential • Retail • Healthcare • Financial • Storage

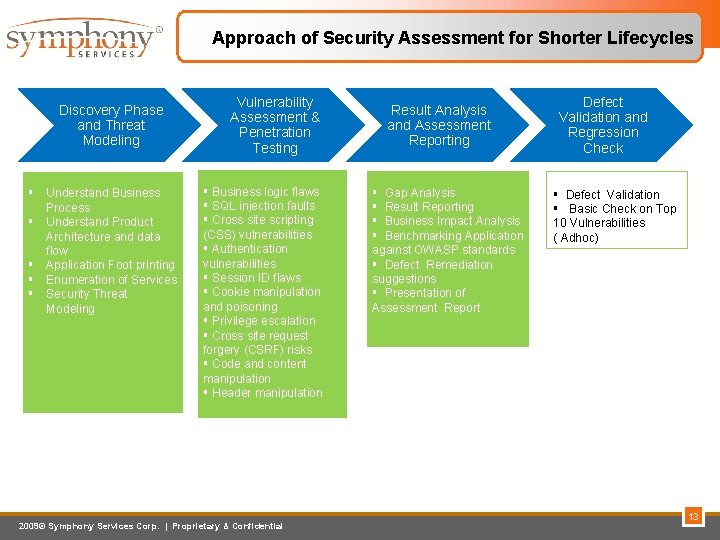
Approach of Security Assessment for Shorter Lifecycles Discovery Phase and Threat Modeling § Understand Business Process § Understand Product Architecture and data flow § Application Foot printing § Enumeration of Services § Security Threat Modeling Vulnerability Assessment & Penetration Testing § Business logic flaws § SQL injection faults § Cross site scripting (CSS) vulnerabilities § Authentication vulnerabilities § Session ID flaws § Cookie manipulation and poisoning § Privilege escalation § Cross site request forgery (CSRF) risks § Code and content manipulation § Header manipulation 2009© Symphony Services Corp. | Proprietary & Confidential Result Analysis and Assessment Reporting § Gap Analysis § Result Reporting § Business Impact Analysis § Benchmarking Application against OWASP standards § Defect Remediation suggestions § Presentation of Assessment Report Defect Validation and Regression Check § Defect Validation § Basic Check on Top 10 Vulnerabilities ( Adhoc) 13

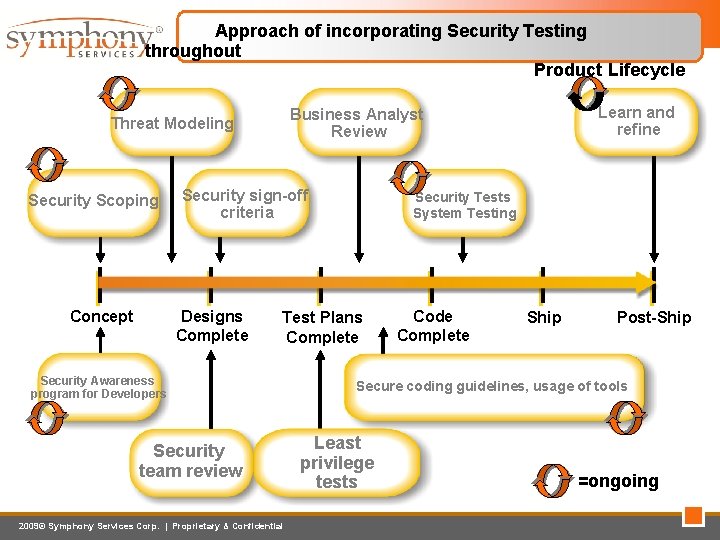
Approach of incorporating Security Testing throughout Product Lifecycle Security Scoping Concept Security sign-off criteria Designs Complete Learn and refine Business Analyst Review Threat Modeling Security Tests System Testing Test Plans Complete Security Awareness program for Developers Security team review 2009© Symphony Services Corp. | Proprietary & Confidential Code Complete Ship Post-Ship Secure coding guidelines, usage of tools Least privilege tests =ongoing

Thank You !!! Joyabrata. Burman@symphonysv. com 2009© Symphony Services Corp. | Proprietary & Confidential