Security Technologies on Communication Networks and Their Applications










- Slides: 30

Security Technologies on Communication Networks and Their Applications to Electronic Business Chair Professor Chin-Chen Chang Feng Chia University National Chung Cheng University National Tsing Hua University http: //msn. iecs. fcu. edu. tw/~ccc MSN lab

Outline n n n n Mobile services Radio Frequency Identification (RFID) Roaming between cellular network and WLAN Watermarking Image authentication Visual cryptography Secret sharing Steganography MSN lab 2

Mobile services (1/4) MSN lab 3

Mobile services (2/4) MSN lab 4

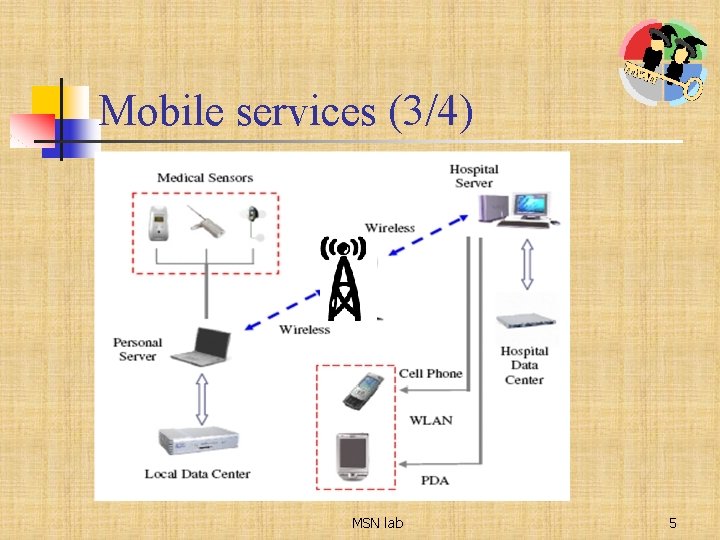
Mobile services (3/4) MSN lab 5

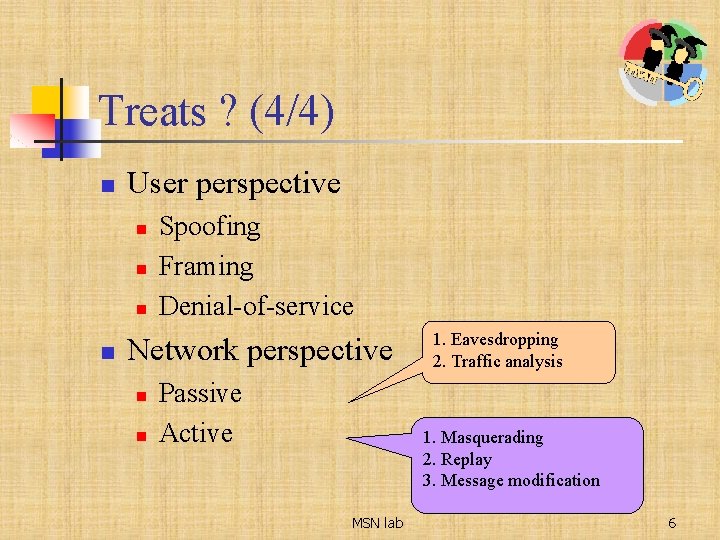
Treats ? (4/4) n User perspective n n Spoofing Framing Denial-of-service Network perspective n n Passive Active 1. Eavesdropping 2. Traffic analysis 1. Masquerading 2. Replay 3. Message modification MSN lab 6

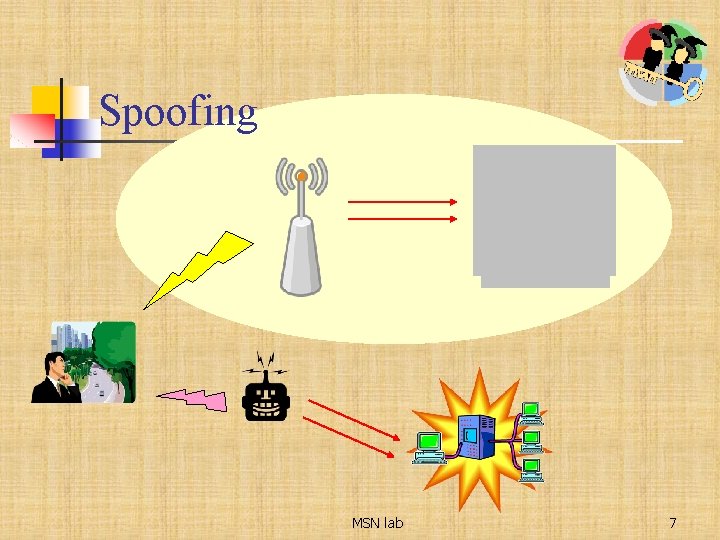
Spoofing MSN lab 7

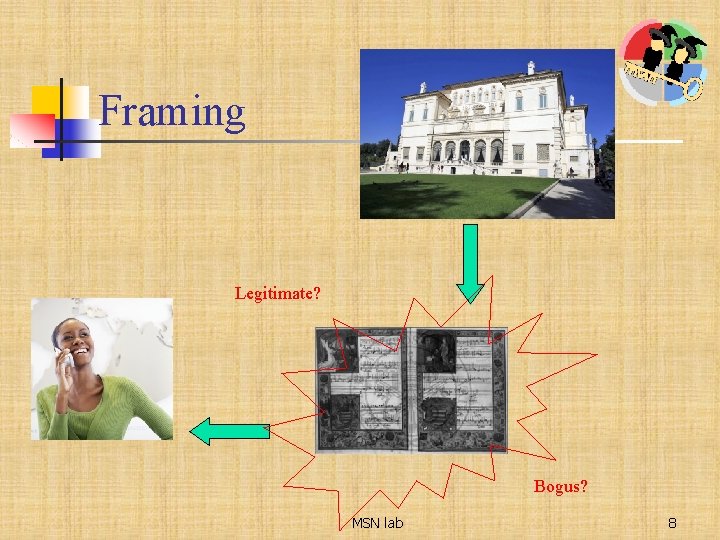
Framing Legitimate? Bogus? MSN lab 8

Denial-of-service MSN lab 9

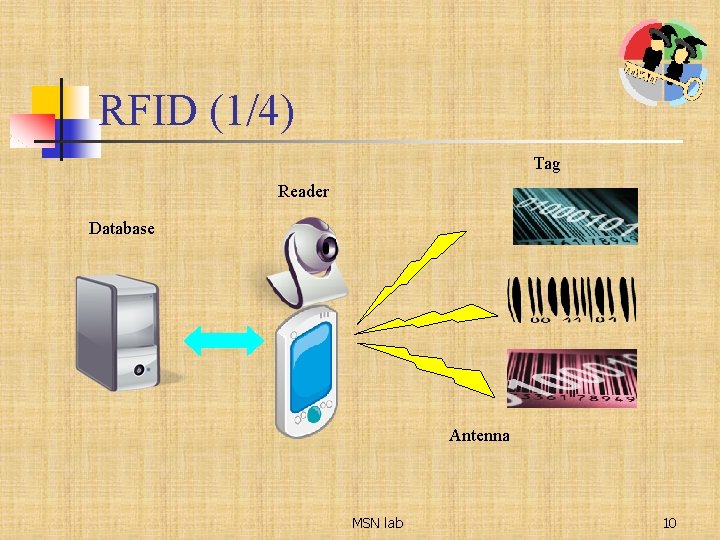
RFID (1/4) Tag Reader Database Antenna MSN lab 10

RFID (2/4) n n n Shopping Library Transportation Household appliance … MSN lab 11

Risk? (3/4) n n n Eavesdropping Traffic analysis Replay attack Position detection Physical attack MSN lab 12

Issue? (4/4) n n Anonymity -> Privacy Synchronization Authentication Efficiency MSN lab 13

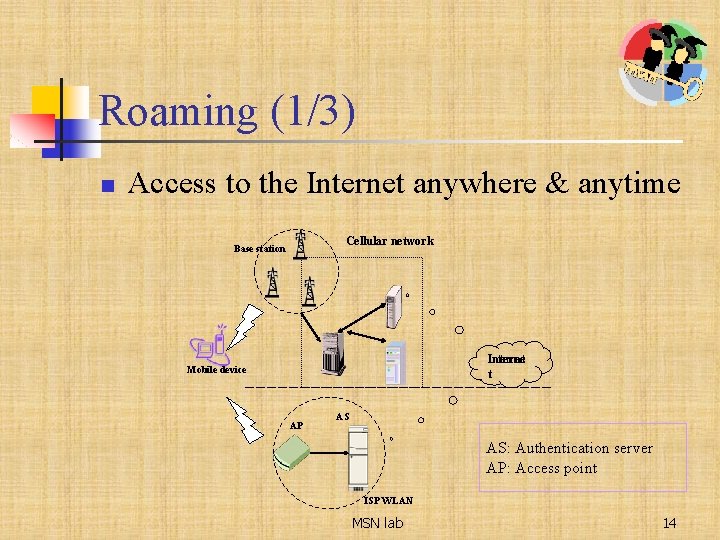
Roaming (1/3) n Access to the Internet anywhere & anytime Cellular network Base station Internet t Mobile device AP AS AS: Authentication server AP: Access point ISP WLAN MSN lab 14

Roaming (2/3) n n n Cellular networks : wide service areas and continuous pervasive access WLAN : high-speed pervasive communications How to integrate? MSN lab 15

Issues? (3/3) n n n Mutual authentication Anonymous service Charging MSN lab 16

Watermarking n Visible watermarking n n Easy to embed Clear to see watermark MSN lab 17

Watermarking (Cont. ) n Invisible watermarking n Requirements: n n Good visual quality of watermarked image Robustness Watermarking Original image Watermark MSN lab Watermarked image 18

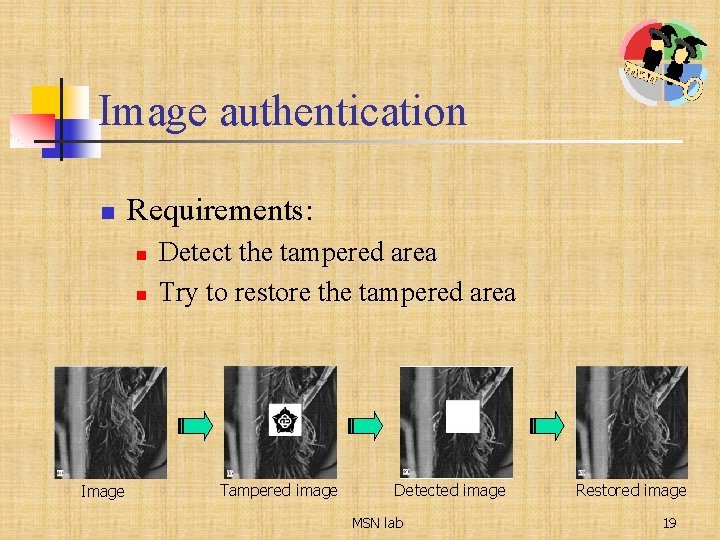
Image authentication n Requirements: n n Image Detect the tampered area Try to restore the tampered area Tampered image Detected image MSN lab Restored image 19

Secret sharing n Classification: n Meaningless shadows n Meaningful shadows MSN lab 20

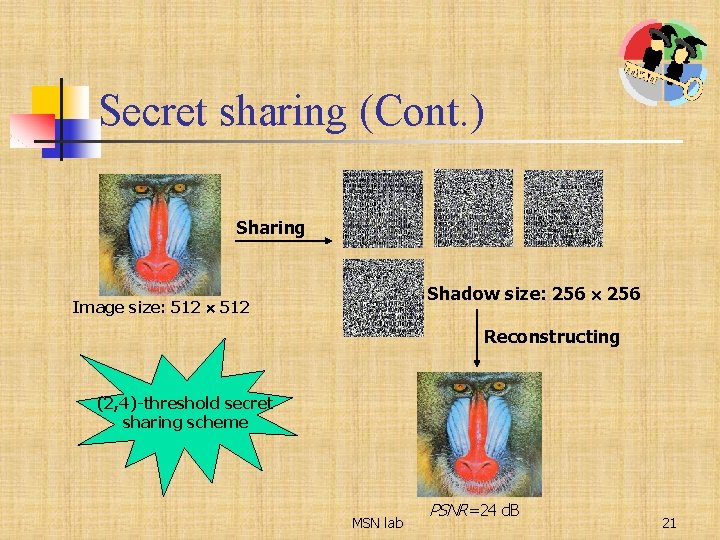
Secret sharing (Cont. ) Sharing Shadow size: 256 Image size: 512 Reconstructing (2, 4)-threshold secret sharing scheme MSN lab PSNR=24 d. B 21

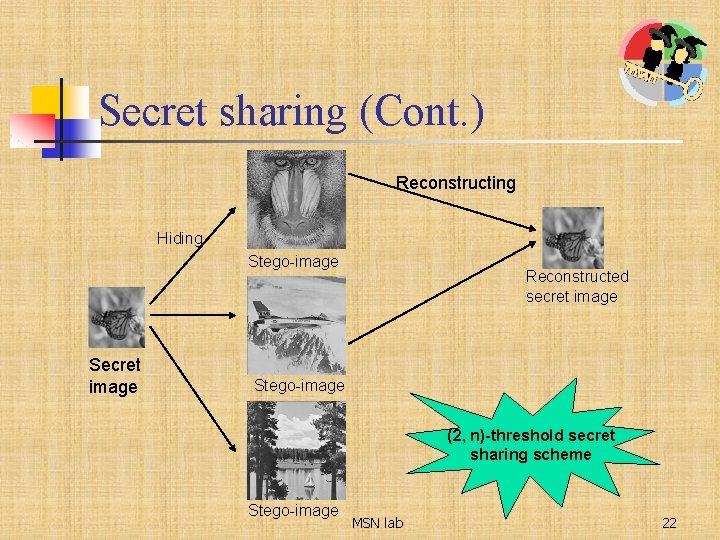
Secret sharing (Cont. ) Reconstructing Hiding Stego-image Secret image Reconstructed secret image Stego-image (2, n)-threshold secret sharing scheme Stego-image MSN lab 22

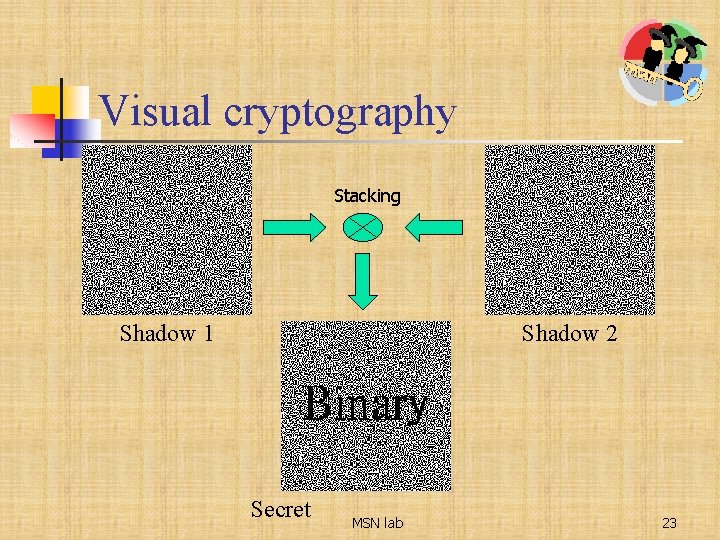
Visual cryptography Stacking Shadow 1 Shadow 2 Secret MSN lab 23

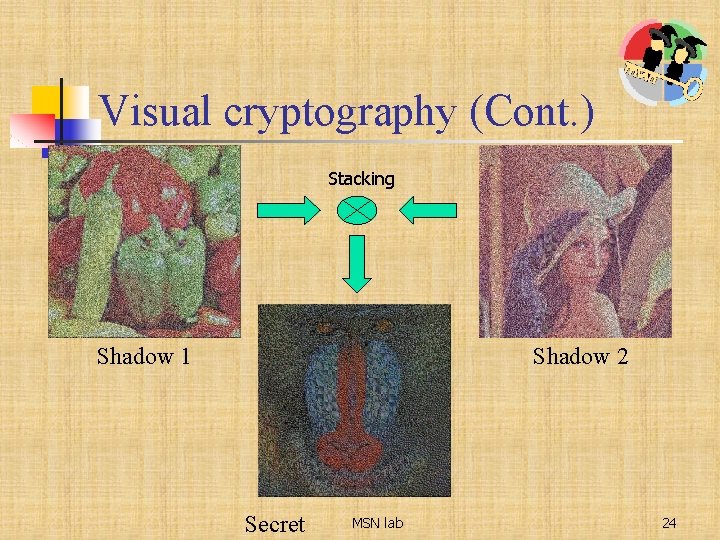
Visual cryptography (Cont. ) Stacking Shadow 1 Shadow 2 Secret MSN lab 24

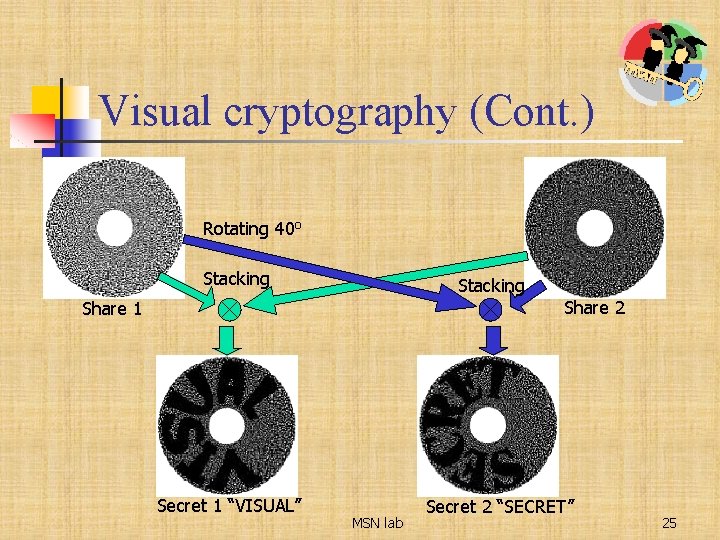
Visual cryptography (Cont. ) Rotating 40 o Stacking Share 2 Share 1 Secret 1 “VISUAL” MSN lab Secret 2 “SECRET” 25

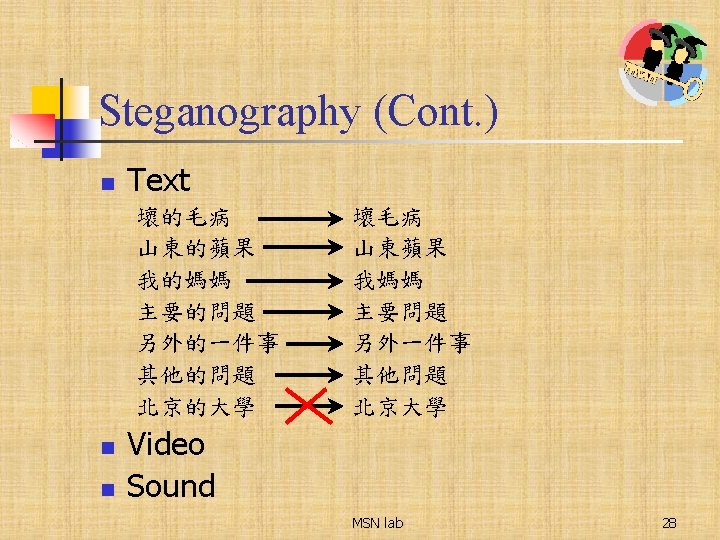
Steganography n The targets n n n Frequency domain (e. g. DCT, DWT, DFT) Spatial domain (e. g. pixel values) Compression domain (e. g. VQ) Text Restoration n n Irreversible Reversible MSN lab 26

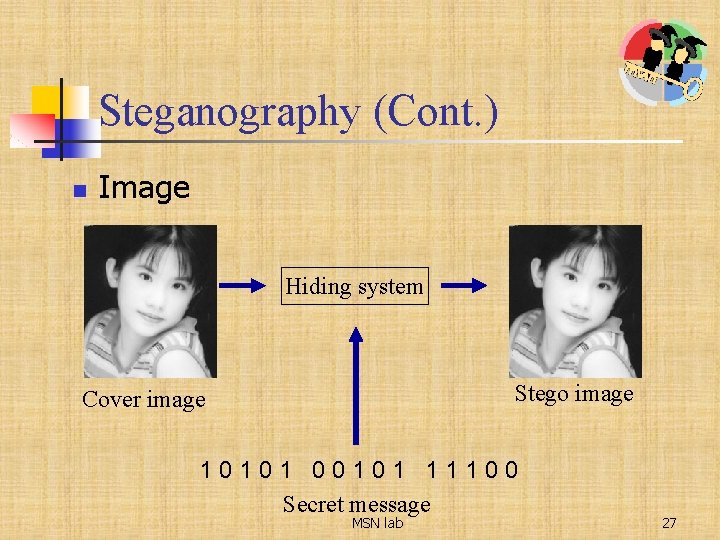
Steganography (Cont. ) n Image Hiding system Stego image Cover image 10101 00101 11100 Secret message MSN lab 27


Conclusions n n The biggest risk: eavesdropping & copy The limitation: n n Power Computing capability Robustness Image quality MSN lab 29

Security Technologies on Communication Networks and Their Applications to Electronic Business MSN lab 30