Security Systems Lecture notes Dr Clifford Neuman University















- Slides: 45

Security Systems Lecture notes Dr. Clifford Neuman University of Southern California Information Sciences Institute Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 1

CSci 530: Security Systems Lecture 2 – September 3, 2004 Cryptography Dr. Clifford Neuman University of Southern California Information Sciences Institute Slides by Drs. Brian Tung and Clifford Neuman Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 2

Administration v Second TA is Paras Shah – Contact information on web site v Paper will likely be due last class period. – Proposal will be due in first half of October v Textbooks not available in Bookstore – Final choice of text was made late, which did not leave time for bookstore to have in stock by start of semester. – You can get the book cheaper through Amazon and similar sites anyway, including used versions. Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 3

Cryptography and Security v Cryptography underlies many fundamental security services – Confidentiality – Data integrity – Authentication v It is a basic foundation of much of security. Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 4

A Brief History v Steganography: “covered writing” – Demaratus (5 th century B. C. ) – German microdots (WWII) – Crucial flaw: Discovery yields knowledge u Confidentiality v Cryptography: through obscurity “secret writing” – TASOIINRNPSTO and TVCTUJUVUJPO Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 5

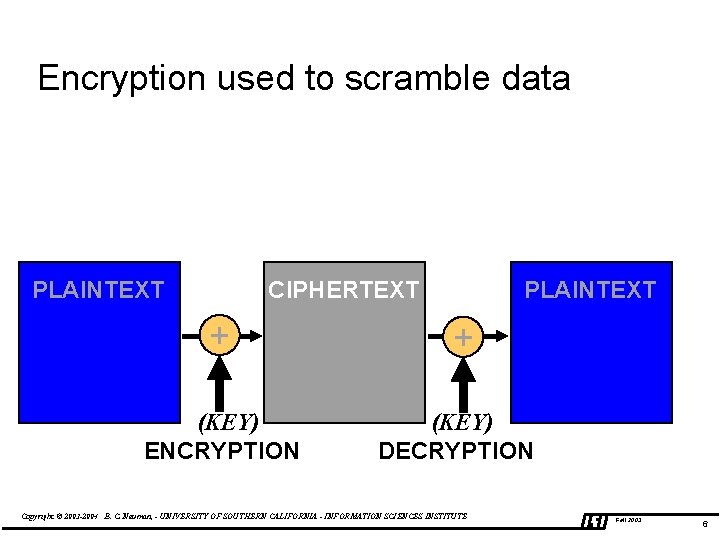
Encryption used to scramble data PLAINTEXT CIPHERTEXT PLAINTEXT + + (KEY) ENCRYPTION (KEY) DECRYPTION Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 6

A Brief History v Two basic types of cryptography – Transposition (TASOIINRNPSTO) u Message broken up into units u Units permuted in a seemingly random but reversible manner u Difficult to make it easily reversible only by intended receiver u Exhibits same first-order statistics Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 7

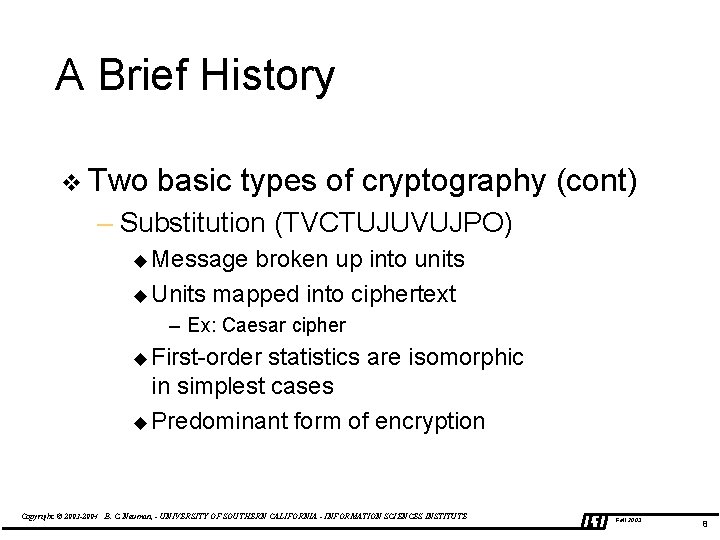
A Brief History v Two basic types of cryptography (cont) – Substitution (TVCTUJUVUJPO) u Message broken up into units u Units mapped into ciphertext – Ex: Caesar cipher u First-order statistics are isomorphic in simplest cases u Predominant form of encryption Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 8

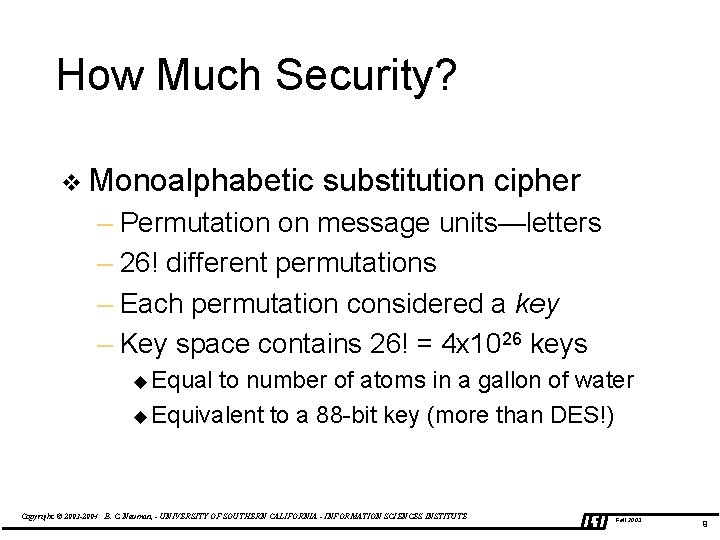
How Much Security? v Monoalphabetic substitution cipher – Permutation on message units—letters – 26! different permutations – Each permutation considered a key – Key space contains 26! = 4 x 1026 keys u Equal to number of atoms in a gallon of water u Equivalent to a 88 -bit key (more than DES!) Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 9

How Much Security? v So why not use substitution ciphers? – Hard to remember 26 -letter keys u But we can restrict ourselves to shorter keys u Ex: JULISCAERBDFGHKM, etc – Remember: first-order statistics are isomorphic u Vulnerable to simple cryptanalysis u Hard-to-read fonts for crypto? ! Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 10

Substitution Ciphers v Two basic types – Symmetric-key (conventional) u Single key used for both encryption and decryption u Keys are typically short, because key space is densely filled u Ex: DES, 3 DES, RC 4, Blowfish, IDEA, etc Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 11

Substitution Ciphers v Two basic types (cont) – Public-key (asymmetric) u Two keys: one for encryption, one for decryption u Keys are typically long, because key space is sparsely filled u Ex: RSA, El Gamal, DSA, etc Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 12

Conventional Cryptography v Block ciphers encrypt message in units called blocks – DES: 8 -byte key (56 key bits), 8 -byte block – Larger blocks make simple cryptanalysis useless (at least for short messages) u Not enough samples for valid statistics u “Octogram Statistics Needed” Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 13

Key and Block Size v Do larger keys make sense for an 8 byte block? – 3 DES: Key is 112 or 168 bits, but block is still 8 bytes long (64 bits) – Key space is larger than block space – But how large is permutation space? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 14

Anatomy of a Block Cipher v DES: Data Encryption Standard – Developed as Lucifer (one of a few) at IBM in 1970 s – Break message into 8 -byte (64 -bit) blocks u Each block broken into 32 -bit halves u Initial permutation u 16 rounds of scrambling u Final (reverse) permutation Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 15

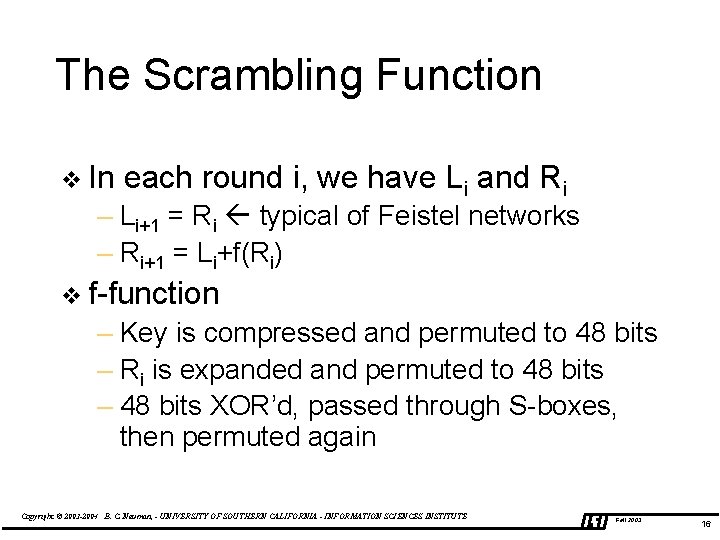
The Scrambling Function v In each round i, we have Li and Ri – Li+1 = Ri typical of Feistel networks – Ri+1 = Li+f(Ri) v f-function – Key is compressed and permuted to 48 bits – Ri is expanded and permuted to 48 bits – 48 bits XOR’d, passed through S-boxes, then permuted again Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 16

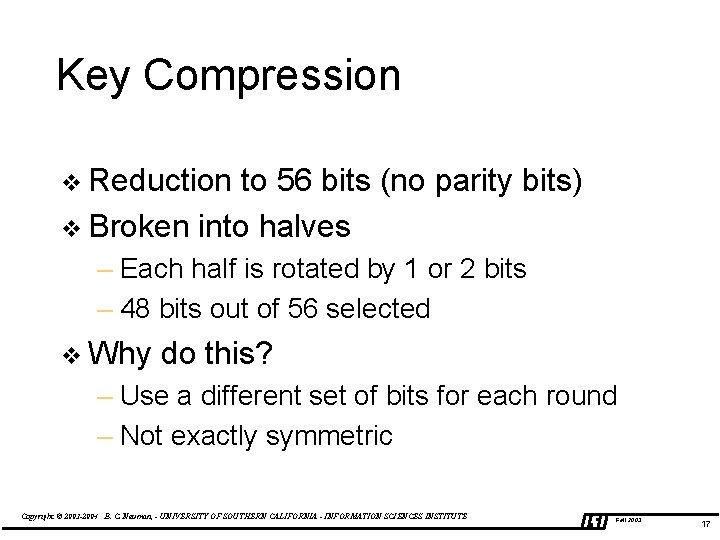
Key Compression v Reduction to 56 bits (no parity bits) v Broken into halves – Each half is rotated by 1 or 2 bits – 48 bits out of 56 selected v Why do this? – Use a different set of bits for each round – Not exactly symmetric Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 17

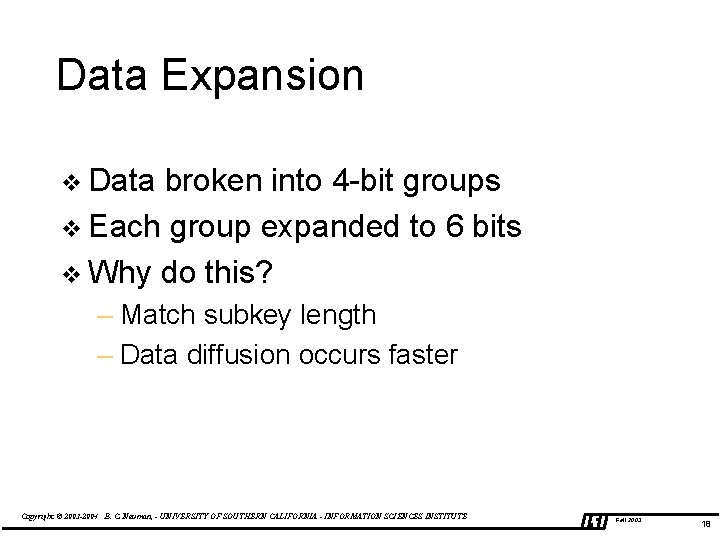
Data Expansion v Data broken into 4 -bit groups v Each group expanded to 6 bits v Why do this? – Match subkey length – Data diffusion occurs faster Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 18

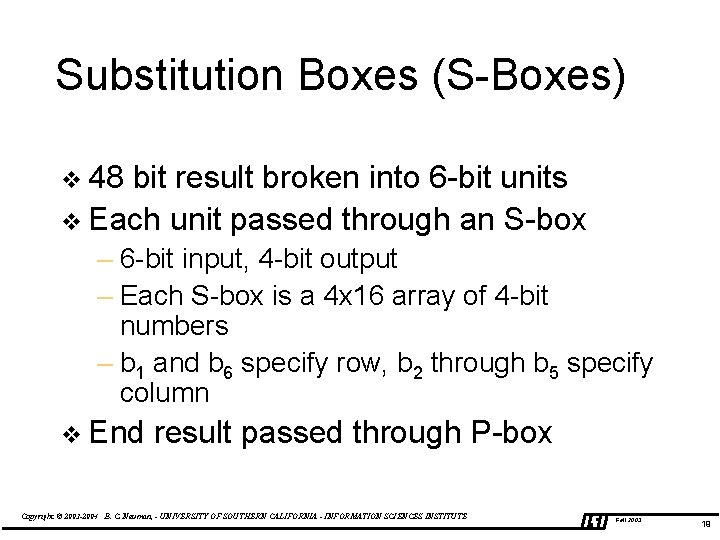
Substitution Boxes (S-Boxes) v 48 bit result broken into 6 -bit units v Each unit passed through an S-box – 6 -bit input, 4 -bit output – Each S-box is a 4 x 16 array of 4 -bit numbers – b 1 and b 6 specify row, b 2 through b 5 specify column v End result passed through P-box Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 19

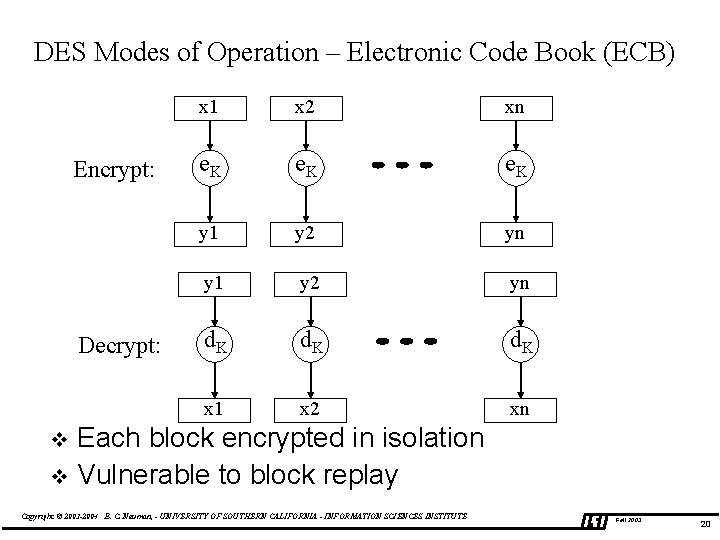
DES Modes of Operation – Electronic Code Book (ECB) Encrypt: Decrypt: x 1 xx 2 xxn e. K y 1 y 2 yn yy 1 y 2 yn d. K x 1 x 2 xn Each block encrypted in isolation v Vulnerable to block replay v Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 20

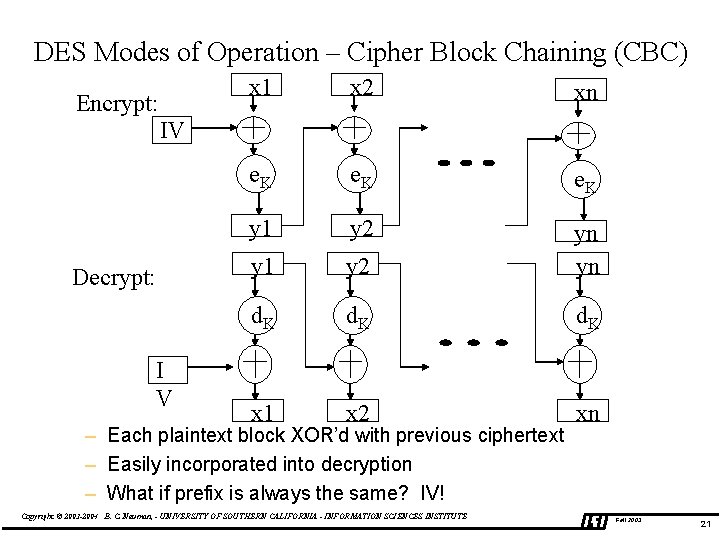
DES Modes of Operation – Cipher Block Chaining (CBC) Encrypt: x 1 x 2 xn e. K y 1 y 2 yn yn d. K x 1 x 2 xn IV Decrypt: I V – Each plaintext block XOR’d with previous ciphertext – Easily incorporated into decryption – What if prefix is always the same? IV! Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 21

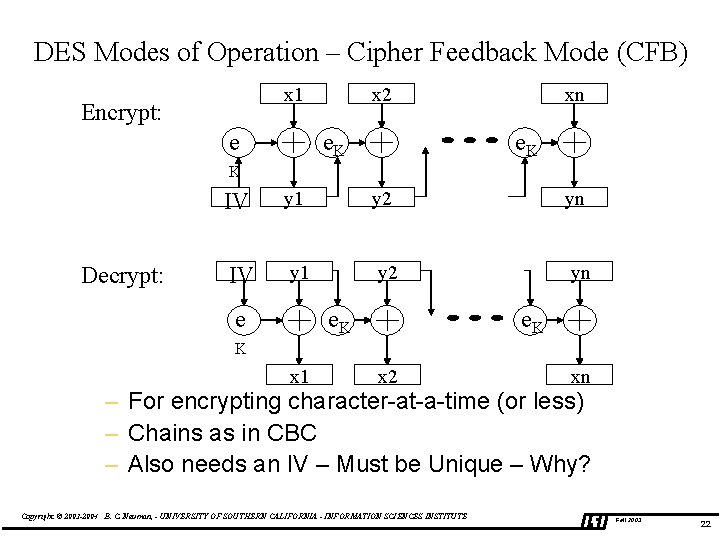
DES Modes of Operation – Cipher Feedback Mode (CFB) x 1 Encrypt: e xx 2 e. K xn x e. K K Decrypt: IV y 1 y 2 yn e. K e e. K K x 1 x 2 xn – For encrypting character-at-a-time (or less) – Chains as in CBC – Also needs an IV – Must be Unique – Why? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 22

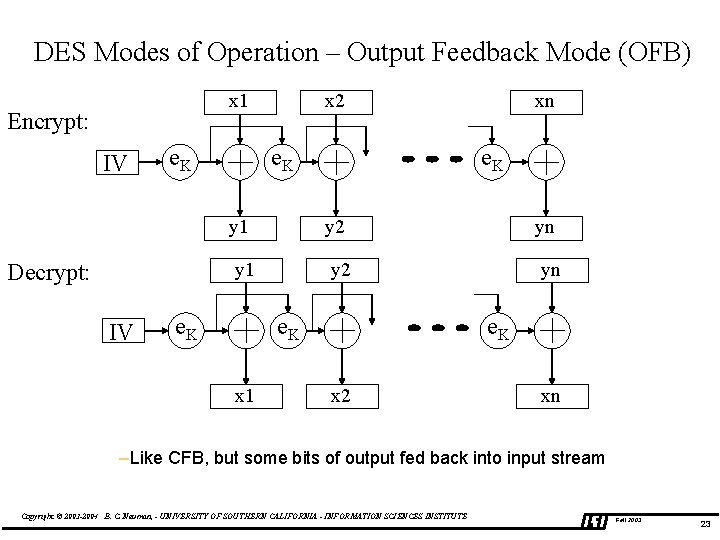
DES Modes of Operation – Output Feedback Mode (OFB) x x 2 x 1 Encrypt: IV e. K y 1 Decrypt: IV e. K y 2 yn e. K x 1 x xn e. K x 2 xn –Like CFB, but some bits of output fed back into input stream Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 23

Variants and Applications v 3 DES: Encrypt using DES 3 x – Two and three-key types – Inner and outer-CBC modes u Inner v Crypt: is more efficient, but less secure Unix hash function for passwords – Uses variable expansion permutations v DES with key-dependent S-boxes – Harder to analyze Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 24

Lucifer Goes Standard v Generally regarded in 1970 s as one of the strongest cryptosystems v Heading toward standardization as DES – NSA managed to get key size reduced to 56 bits (from 112), yielding 1017 keys – Also apparently changed S-boxes – Why (or why not) do this? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 25

Certification of DES v Had to be recertified every ~5 years – 1983: Recertified routinely – 1987: Recertified after NSA tried to promote secret replacement algorithms u Withdrawal would mean lack of protection u Lots of systems then using DES – 1993: Recertified after continued lack of alternative Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 26

Enter AES v 1998: NIST finally refuses to recertify DES – 1997: Call for candidates for Advanced Encryption Standard (AES) – Fifteen candidates whittled down to five – Criteria: Security, but also efficiency u Compare Rijndael with Serpent – 2000: Rijndael selected as AES Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 27

Structure of Rijndael v Unlike DES, operates on whole bytes for efficiency of software implementations v Key sizes: 128/192/256 bits v Variable rounds: 9/11/13 rounds v Rounds are not Feistel networks Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 28

Structure of Rijndael v Round structure – Run block through S-box – Permute result into 4 x 4/4 x 6/4 x 8 array of bytes – Multiply each byte by 1, 2, or 3 in GF(28) – Mix subkey into result Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 29

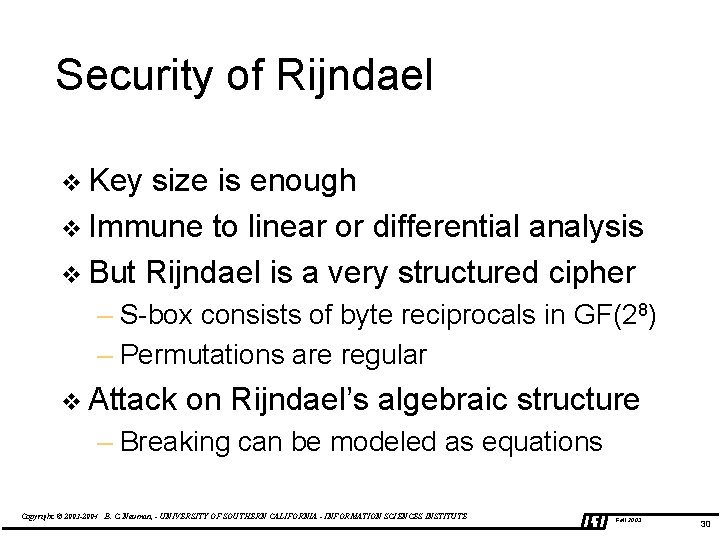
Security of Rijndael v Key size is enough v Immune to linear or differential analysis v But Rijndael is a very structured cipher – S-box consists of byte reciprocals in GF(28) – Permutations are regular v Attack on Rijndael’s algebraic structure – Breaking can be modeled as equations Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 30

Impact of Attacks on Rijndael v Currently of theoretical interest only – Reduces complexity of attack to about 2100 – Also applicable to Serpent v Still, uncomfortably close to feasibility – DES is already insecure against brute force – Schneier (somewhat arbitrarily) sets limit at 280 v Certainly usable pending further results Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 31

Public Key Cryptography v aka asymmetric cryptography v Based on some NP-complete problem – Unique factorization – Discrete logarithms u For any b, n, y: Find x such that bx mod n = y v Modular arithmetic produces folding Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 32

A Short Note on Primes v Why are public keys (and private keys) so large? v What is the probability that some large number p is prime? – About 1 in 1/ln(p) – When p ~ 2512, equals about 1 in 355 u About 1 in 3552 numbers ~ 21024 is product of two primes (and therefore valid RSA modulo) Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 33

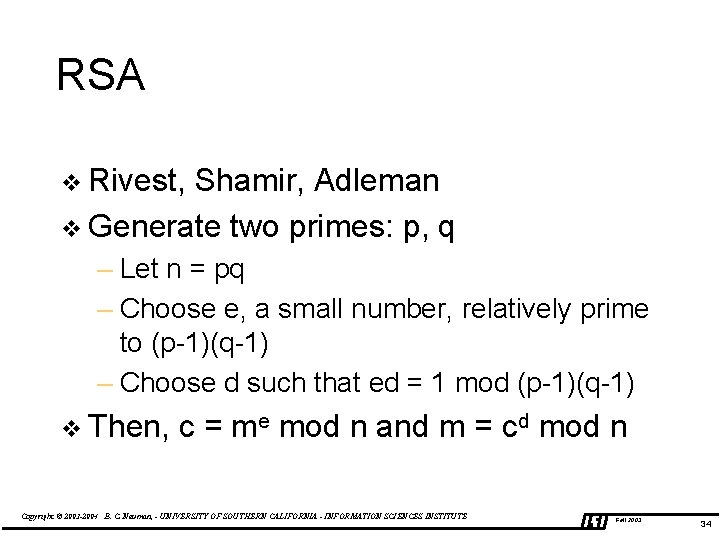
RSA v Rivest, Shamir, Adleman v Generate two primes: p, q – Let n = pq – Choose e, a small number, relatively prime to (p-1)(q-1) – Choose d such that ed = 1 mod (p-1)(q-1) v Then, c = me mod n and m = cd mod n Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 34

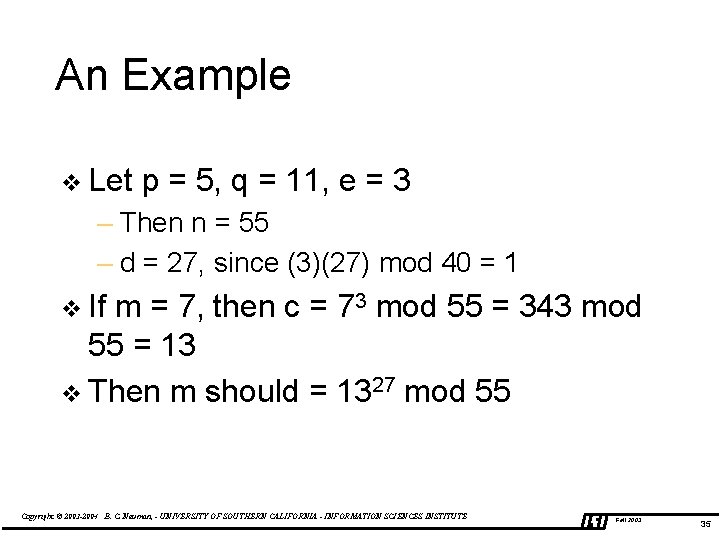
An Example v Let p = 5, q = 11, e = 3 – Then n = 55 – d = 27, since (3)(27) mod 40 = 1 v If m = 7, then c = 73 mod 55 = 343 mod 55 = 13 v Then m should = 1327 mod 55 Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 35

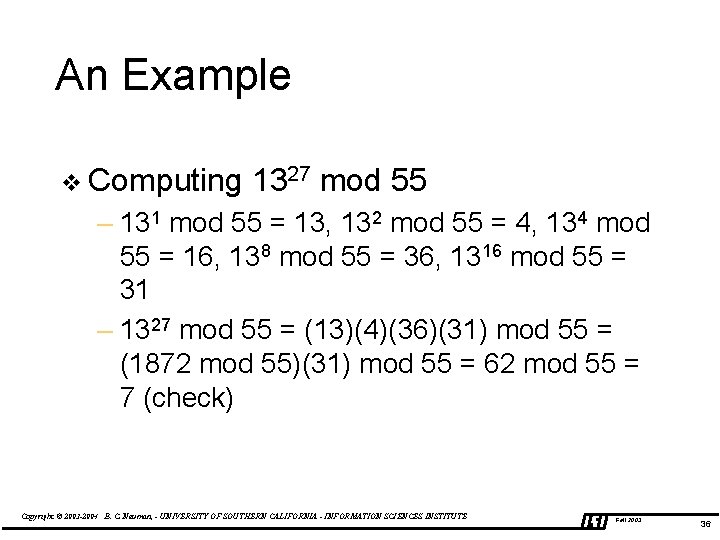
An Example v Computing 1327 mod 55 – 131 mod 55 = 13, 132 mod 55 = 4, 134 mod 55 = 16, 138 mod 55 = 36, 1316 mod 55 = 31 – 1327 mod 55 = (13)(4)(36)(31) mod 55 = (1872 mod 55)(31) mod 55 = 62 mod 55 = 7 (check) Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 36

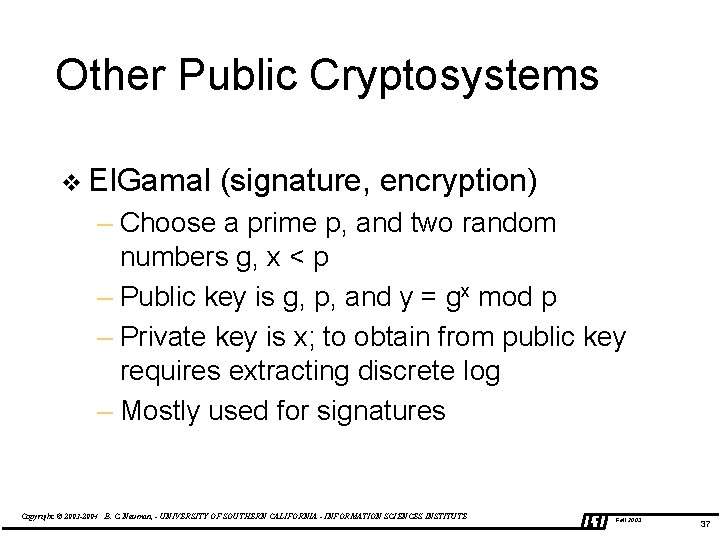
Other Public Cryptosystems v El. Gamal (signature, encryption) – Choose a prime p, and two random numbers g, x < p – Public key is g, p, and y = gx mod p – Private key is x; to obtain from public key requires extracting discrete log – Mostly used for signatures Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 37

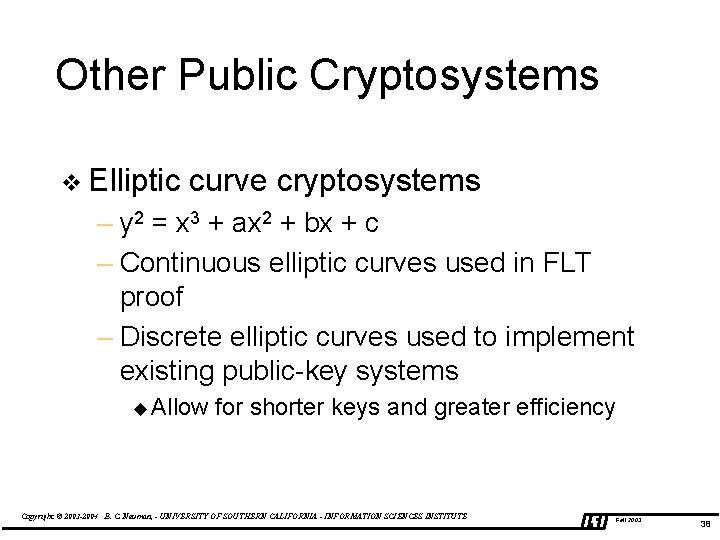
Other Public Cryptosystems v Elliptic curve cryptosystems – y 2 = x 3 + ax 2 + bx + c – Continuous elliptic curves used in FLT proof – Discrete elliptic curves used to implement existing public-key systems u Allow for shorter keys and greater efficiency Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 38

Digital Signatures v Provides data integrity – Can it be done with symmetric systems? Verification requires shared key u Doesn’t provide non-repudiation u v Need proof of provenance – Hash the data, encrypt with private key – Verification uses public key to decrypt hash – Provides “non-repudiation” u But what does non-repudiation really mean? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 39

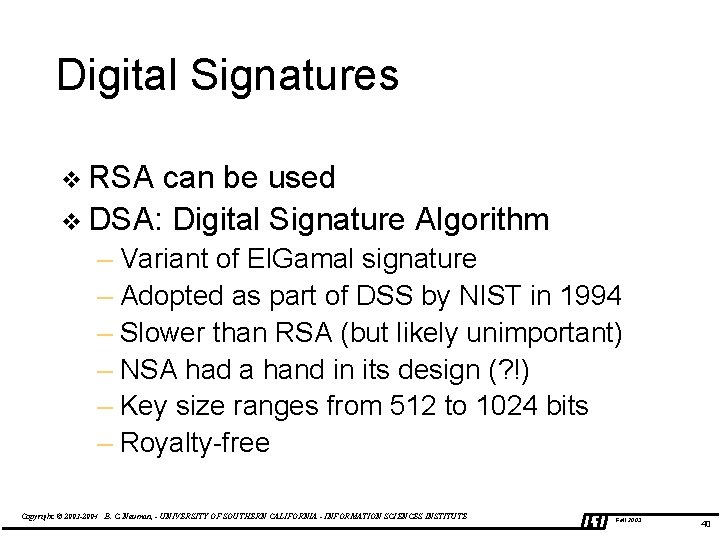
Digital Signatures v RSA can be used v DSA: Digital Signature Algorithm – Variant of El. Gamal signature – Adopted as part of DSS by NIST in 1994 – Slower than RSA (but likely unimportant) – NSA had a hand in its design (? !) – Key size ranges from 512 to 1024 bits – Royalty-free Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 40

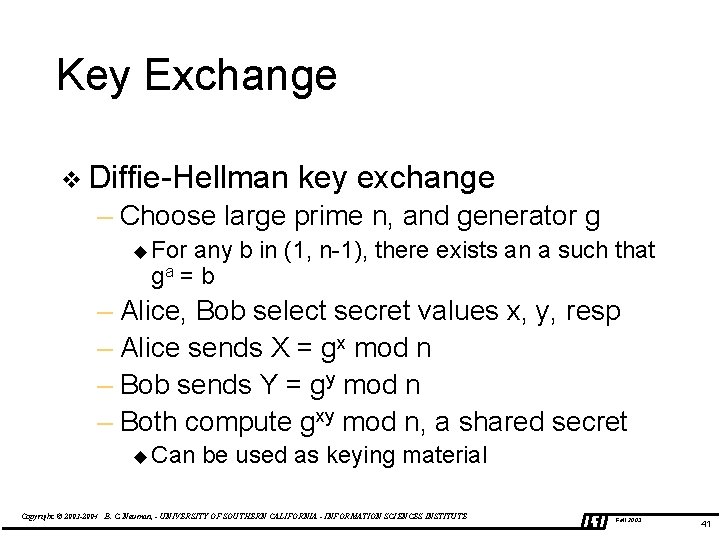
Key Exchange v Diffie-Hellman key exchange – Choose large prime n, and generator g u For any ga = b b in (1, n-1), there exists an a such that – Alice, Bob select secret values x, y, resp – Alice sends X = gx mod n – Bob sends Y = gy mod n – Both compute gxy mod n, a shared secret u Can be used as keying material Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 41

Hash Functions v Given m, compute H(m) v Should be… – Efficient: H() easy to compute – One-way: Given H(m), hard to find m’ such that H(m’) = H(m) – Collision-resistant: Hard to find m and m’ such that H(m’) = H(m) Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 42

Use of Hashes in Signatures v Reduce input to fixed data size – MD 5 produces 128 bits – SHA 1 produces 160 bits v Encrypt the output using private key v Why do we need collision-resistance? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 43

Signing Using Only Hashes v Generate random n 1, n 2, n 3, … v Distribute H(n 1), H(n 2), H(n 3), … v To authenticate message mi, release ni v Problems – Seem to need 2128 or 2160 hashes to sign – Need to bootstrap signature v Resolvable? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 44

Current event Technology Review – Online Edition – September 1, 2004 Is Encryption Doomed? Our entire information society rests on a fragile foundation that mathematicians are racing to dismantle. By Simson Garfinkel The Net Effect September 1, 2004 It's not often that results from conferences on mathematics make the news, but that's precisely what happened last month at the annual Crypto conference in Santa Barbara, CA when researchers from France, Israel, and China all showed that they had discovered flaws in a widely used algorithm called MD 5—an algorithm that I wrote about in some detail last month. The "when life gives you lemons, make lemonade" message that came out of the conference was that this process of breaking codes and developing even stronger ones is all part of the cryptographer’s game. But what if a fundamental breakthrough in mathematics rendered useless all of the fancy encryption that the world now depends upon? Copyright © 2003 -2004 B. C. Neuman, - UNIVERSITY OF SOUTHERN CALIFORNIA - INFORMATION SCIENCES INSTITUTE Fall 2003 45