Security Strategies in Windows Platforms and Applications Lesson





















- Slides: 24

Security Strategies in Windows Platforms and Applications Lesson 13 Microsoft Windows Incident Handling and Management © 2021 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Cover image © Sharpshot/Dreamstime. com

Learning Objective(s) § Perform incident handling by using appropriate methods. Security Strategies in Windows Platforms and Applications © 2021 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

Key Concepts § § Windows incidents Windows incident handling tools Acquiring and managing evidence Incident response plan Security Strategies in Windows Platforms and Applications © 2021 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

Handling Security Incidents Involving Microsoft Windows OS and Applications § Event • Any observable occurrence within a computer or network § Incident • Any event that: - Violates security policy - Poses an imminent threat to security policy Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

Handling Security Incidents Involving Microsoft Windows OS and Applications § Examples of incidents • Virus or Internet worm activity • Internet protocol (IP) spoofing • Intruder activity • Network attack or denial of service (Do. S) condition The first step in responding to an incident is to recognize that an incident has occurred. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

Handling Security Incidents Involving Microsoft Windows OS and Applications § To minimize number and impact of incidents: • Develop, maintain, and enforce a clear security policy that management supports and promotes. • Conduct routine vulnerability assessments to discover vulnerabilities that could lead to incidents. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

Handling Security Incidents Involving Microsoft Windows OS and Applications § To minimize number and impact of incidents: • Ensure all computers and network devices have the latest available patches installed. • Train all computer system users on acceptable and unacceptable behavior. • Establish frequent and visible security awareness reminders. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

Handling Security Incidents Involving Microsoft Windows OS and Applications § To minimize number and impact of incidents: • Enforce strong passwords throughout your environment. • Frequently monitor network traffic, system performance, and all available log files to identify any incidents or unusual events. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

Handling Security Incidents Involving Microsoft Windows OS and Applications § To minimize number and impact of incidents: • Ensure you have a solid business continuity plan (BCP) and disaster recovery plan (DRP) that you test at least annually. • Create a computer security incident response team (CSIRT). Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

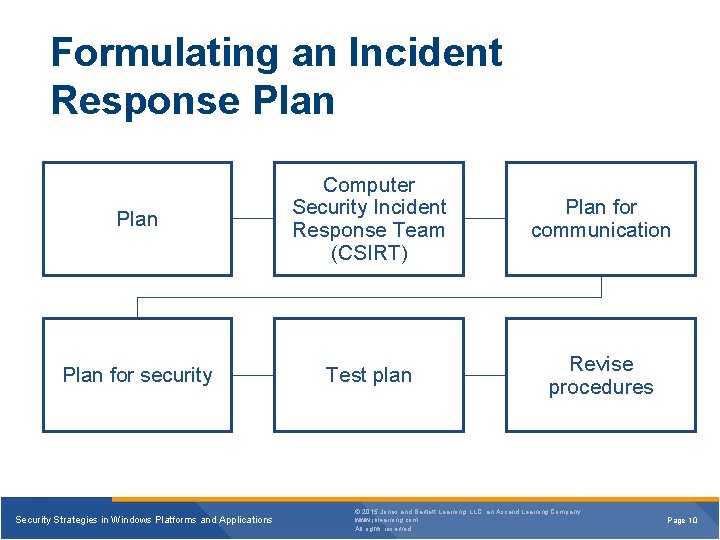
Formulating an Incident Response Plan Computer Security Incident Response Team (CSIRT) Plan for communication Plan for security Test plan Revise procedures Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

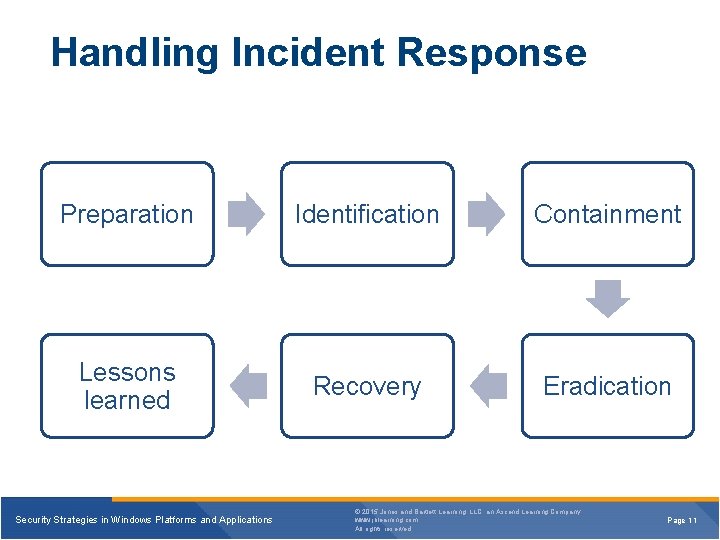
Handling Incident Response Preparation Identification Containment Lessons learned Recovery Eradication Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

Sample Incident Reporting Form Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

Incident Handling and Management Tools for Microsoft Windows and Applications § Two basic types: • Tools that help manage the CSIRT’s activities and gather information about the incident response process • Tools that collect information about the incident itself Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

CSIRT Responsibilities Tracking incidents Reporting on incidents Archiving incident reports Communicating incident information Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

Investigating Microsoft Windows and Applications Incidents § Collect technical information to support incident investigation and resolution § Collect evidence of incident activity to discover what happened, why it happened, how to stop it from happening again § Discover traces of past activity in memory, stored on disks, or in log files § Find evidence of incident activity Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

Questions to Ask During an Investigation § What happened? § Who did it? § When did it happen? § Where did the incident originate and where was its target? § Why did the attacker attack this system? § How did it happen? Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

Acquiring and Managing Incident Evidence § Treat investigation as if it will end up in court § Investigation should produce evidence of an incident and possibly support action against an attacker § Evidence may be pictures, executable files, log files, other Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17

Types of Evidence § Most common types of evidence in computer incidents: • Real evidence–physical object • Documentary evidence–written evidence or file contents § Required to prove accusation Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18

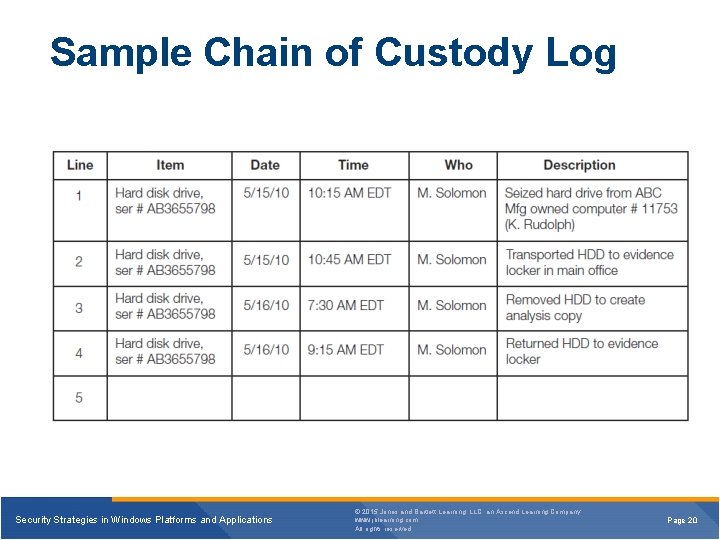
Chain of Custody § Only original evidence is useful • Evidence that has not changed since the incident • Collection methods can change evidence • Handling methods can change evidence Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 19

Sample Chain of Custody Log Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 20

Evidence Collection Rules § Each state and local jurisdiction may impose slightly different rules • Familiarize yourself with local laws and policies § Different rules govern different types of evidence § Contact local law enforcement to learn how they approach investigations § Contact your organization’s legal representatives, beginning with your CSIRT team legal representative Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 21

Best Practices for Handling Incidents § Harden operating systems and software to avoid incidents. § Assess computers periodically to expose vulnerabilities. § Validate BCPs and DRPs. § Get full management support for a CSIRT. § Create a CSIRT. § Conduct a risk assessment to identify potential incidents that require attention first. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 22

Best Practices for Handling Incidents (Cont. ) § Develop an incident response plan around the six steps to handling incidents. § Create an incident reporting form and procedures. § Distribute and publicize the incident reporting form and procedures. § Test the incident response plan before attackers do. § Identify and acquire incident management software. § Identify and acquire incident investigation software. § Train key CSIRT members on proper evidence collection and handling. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 23

Summary § Windows incidents § Windows incident handling tools § Acquiring and managing evidence § Incident response plan Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 24