Security Strategies in Windows Platforms and Applications Lesson







- Slides: 23

Security Strategies in Windows Platforms and Applications Lesson 10 Microsoft Windows Security Administration © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective and Key Concepts Learning Objective § Develop a security administration framework to ensure your organization meets its security policy goals. Key Concepts § Security administration § Due diligence § End user security awareness training program Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

Operating System Administration Workstation Administration Server Administration Network Device Administration Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

Security Administration Process Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

C-I-A Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

Types of Security Administration Firewall Backup Operating system service pack Group Policy Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

Types of Security Administration DACL Encryption Anti-malware software Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

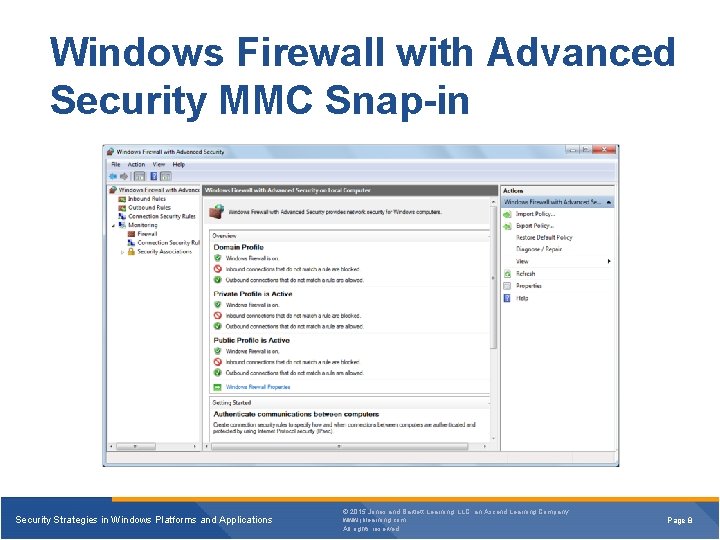
Windows Firewall with Advanced Security MMC Snap-in Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

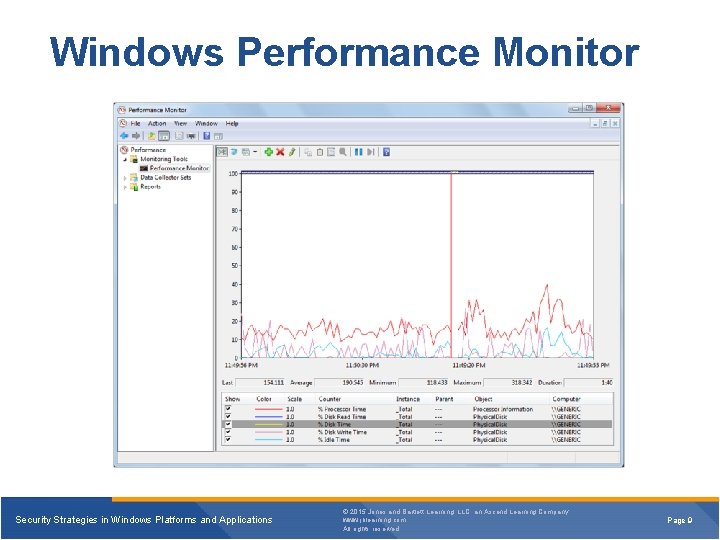
Windows Performance Monitor Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

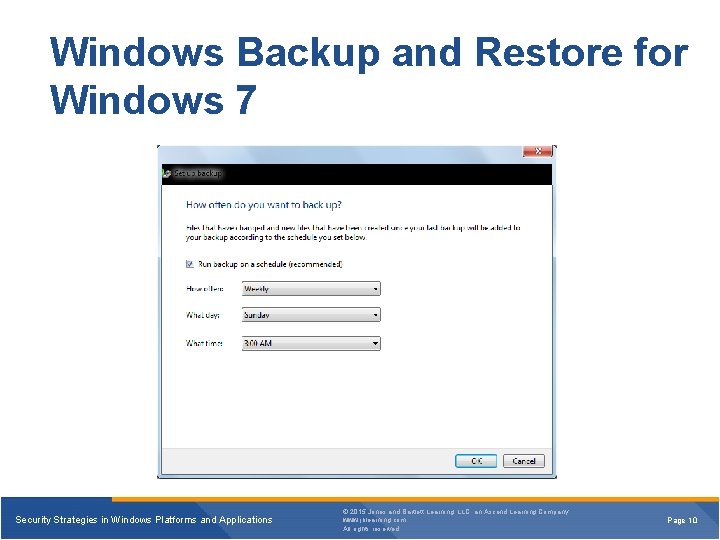
Windows Backup and Restore for Windows 7 Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

Windows Server 2008 Backup Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

MBSA GUI Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

Group Policy Management Console Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

Object Properties Security Page Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

DACL Advanced Security Settings Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

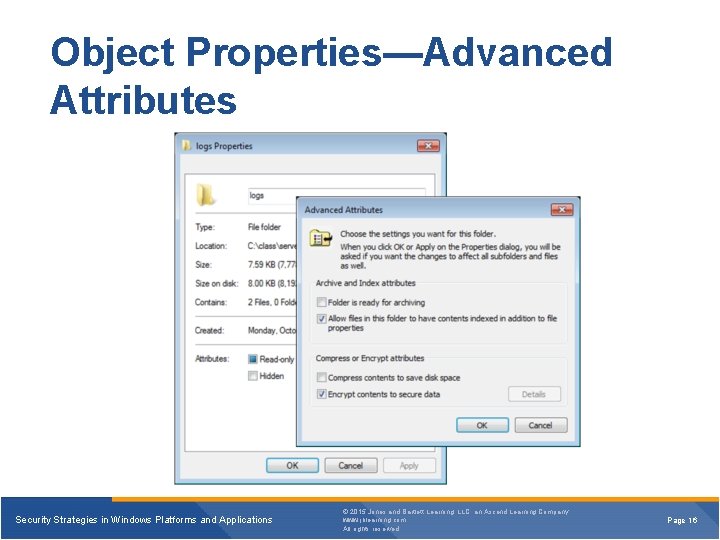
Object Properties—Advanced Attributes Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

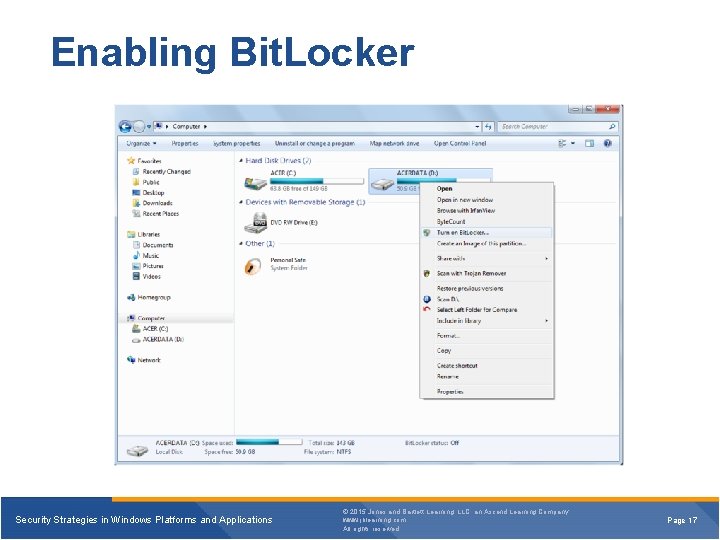
Enabling Bit. Locker Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17

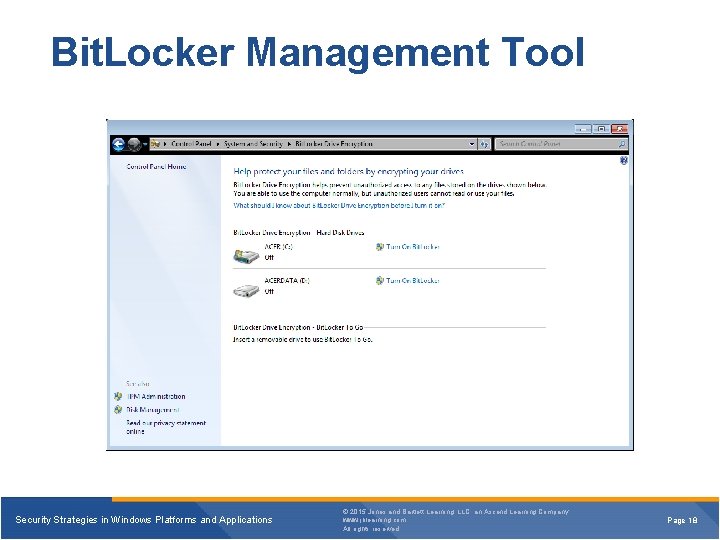
Bit. Locker Management Tool Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18

Compliance and Due Diligence Compliance Security Strategies in Windows Platforms and Applications Due Diligence © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 19

Security Policies, Standards, Procedures, and Guidelines Main Security Elements § Clearly stated security goals § Documented plans § Communication with stakeholders Security Strategies in Windows Platforms and Applications Guidance Documents § Security policy § Security standard § Security procedure § Security guidelines © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 20

Best Practices § Clearly state security goals § Include all compliance requirements § Use the PDCA method § Communicate with all stakeholders § Strive for simplicity § Search for controls that have little impact on users § Coordinate AUPs with technical controls § Automate § Use AD GPOs Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 21

Best Practices (Cont. ) § Coordinate physical and technical controls § Use anti-malware controls § Develop a plan to monitor system and network performance § Use up to date software § Examine log files § Stay current on emerging attacks § Test your recovery plans § Define DACLs Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 22

Summary § Methods of Windows security administration § Process of security administration § Key roles involved in security administration § Recent security breaches Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 23