Security Strategies in Windows Platforms and Applications Lesson








- Slides: 18

Security Strategies in Windows Platforms and Applications Lesson 2 Security in the Microsoft Windows Operating System © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective and Key Concepts Learning Objective § Explain security features of the Microsoft Windows operating system. Key Concepts § Anatomy of Microsoft Windows systems and their application vulnerabilities § Purpose of access control, authentication, and creating users and groups § Security features of directory services Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

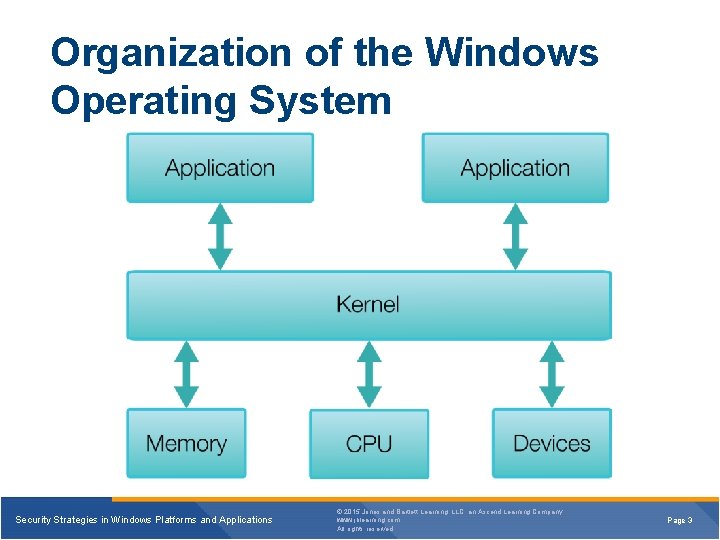
Organization of the Windows Operating System Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

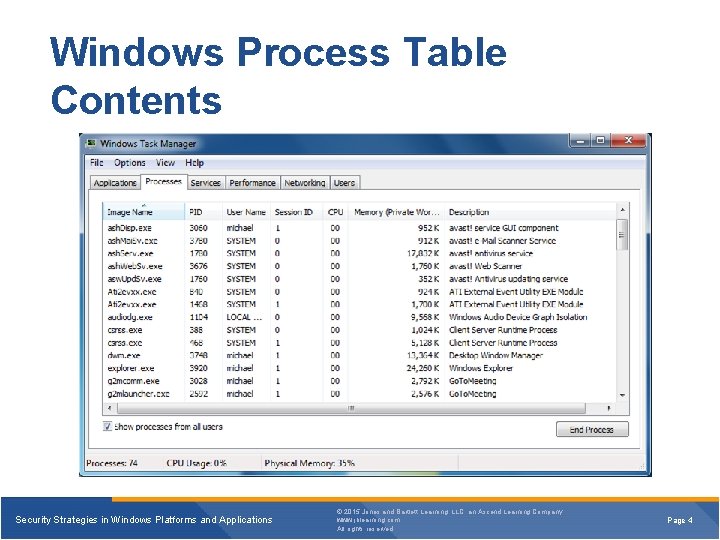
Windows Process Table Contents Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

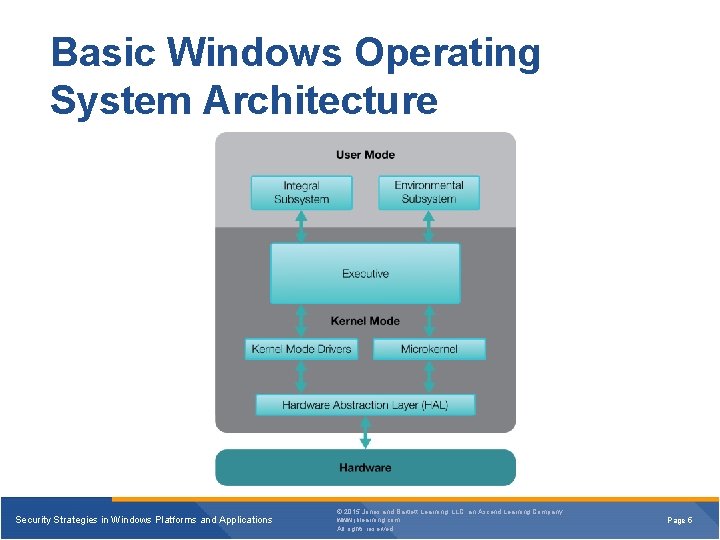
Basic Windows Operating System Architecture Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

Identification and Authentication § Identification—a claim to be someone § Authentication—evidence to prove you are who you claim to be • Type I–What you know (password) • Type II–What you have (token) • Type III–What you are (biometrics) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

Access Control Methods • Discretionary access control (DAC) • Mandatory access control (MAC) • Role-based access control (RBAC) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

Tokens, Rights, and Permissions § Security access token (SAT) § User rights: Actions a user can carry out § Permissions: What a user can do to a specific object Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

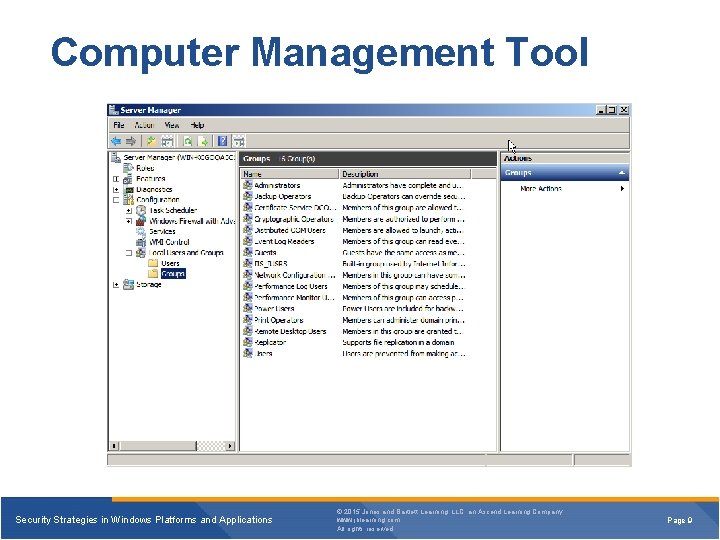
Computer Management Tool Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

Windows Users and Groups § User account as primary identification is used by Windows § Group allows a logical collection of user accounts § SAT allows local rights to be written Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

Active Directory § Directory services implemented through centralized shared database, user and group definitions, and shared access controls § Domains and organizational units (OUs) group computers § Shared data stored on a domain controller Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

Active Directory (Continued) § Central user definitions simplify security administration § User have the same security identifier (SID) anywhere in the domain § Workgroup users have different SIDs for each computer Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

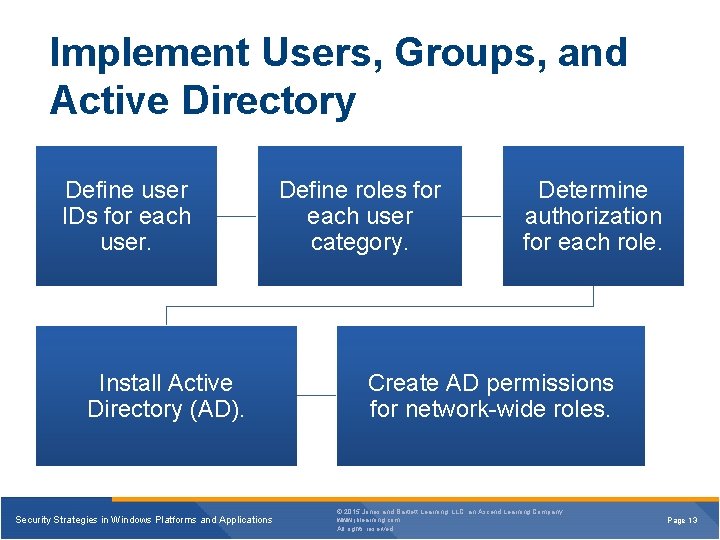
Implement Users, Groups, and Active Directory Define user IDs for each user. Install Active Directory (AD). Security Strategies in Windows Platforms and Applications Define roles for each user category. Determine authorization for each role. Create AD permissions for network-wide roles. © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

Where Active Directory is Most Valuable § Enterprise applications § Networks with shared resources § Centralized administration § Administrators that manage multiple computers § Users that connect from different computers Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

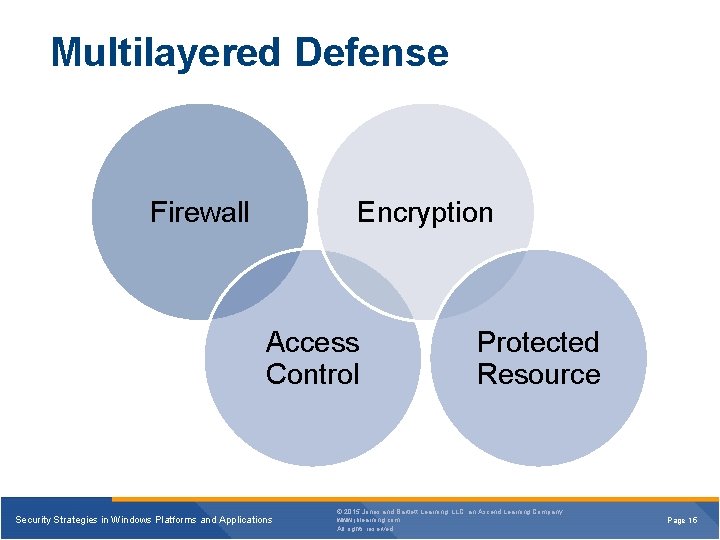
Multilayered Defense Firewall Encryption Access Control Security Strategies in Windows Platforms and Applications Protected Resource © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

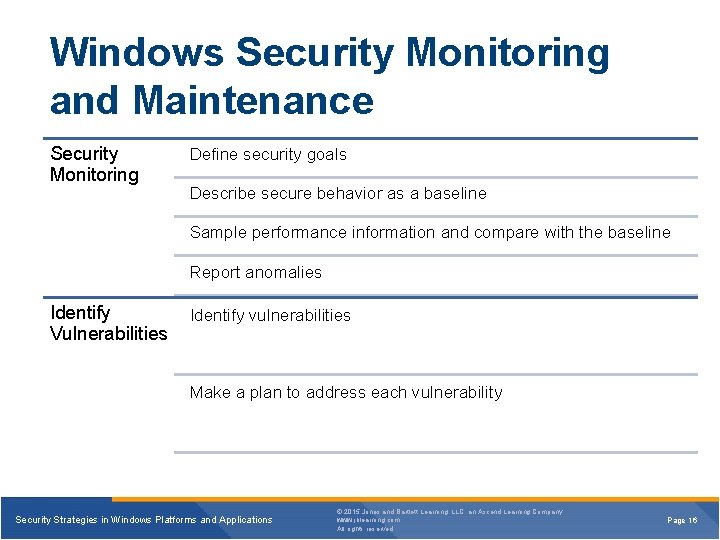
Windows Security Monitoring and Maintenance Security Monitoring Define security goals Describe secure behavior as a baseline Sample performance information and compare with the baseline Report anomalies Identify Vulnerabilities Identify vulnerabilities Make a plan to address each vulnerability Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

Summary § Anatomy of Microsoft Windows systems and their application vulnerabilities § Purpose of access control, authentication, and creating users and groups § Security features of directory services Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17

Virtual Lab § Implementing Access Controls with Windows Active Directory Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18