Security Strategies in Linux Platforms and Applications Chapter








- Slides: 17

Security Strategies in Linux Platforms and Applications Chapter 3 Basic Security: Facilities Through the Boot Process © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective § Lock down the Linux boot process. Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

Key Concepts § Physical server security § Challenges of the standard kernel and possible security issues § Secure boot loaders § Obscurity as a security enhancement Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

Physical Security-Server Room Locks/Biometric controls Pre-boot e. Xecution Environment (PXE) Physical ports Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

TPM and Trusted Computing § Trusted Platform Module (TPM) • Not open source • Password protection • Software license protection • Digital rights management (DRM) • Disk encryption • Chain of trust § TPM in a open source environment • trousers, package with the TCG software stack, tpm-tools Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

Boot Loader Security § Black-hat hacker use poorly configured boot systems and boot loaders to gain administrative access to systems Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

Locking Down Boot Loaders § Back up boot loader before making changes § If something goes wrong: • Use rescue mode on local distribution or a live CD to boot system • Access local drives • Restore the boot loader from backup • Use the appropriate command (grub-install or lilo) Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

Securing LILO Run apt-get install lilo command Accept LILO configuration Create /etc/lilo. configuration file; customize Run lilo -v command Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

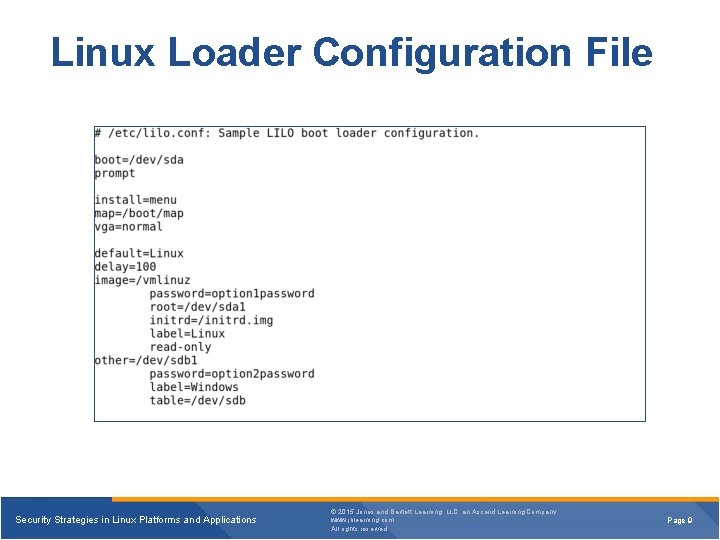
Linux Loader Configuration File Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

Securing GRUB Run apt-get install lilo command Accept LILO configuration Create /etc/lilo. configuration file; customize Run lilo -v command Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

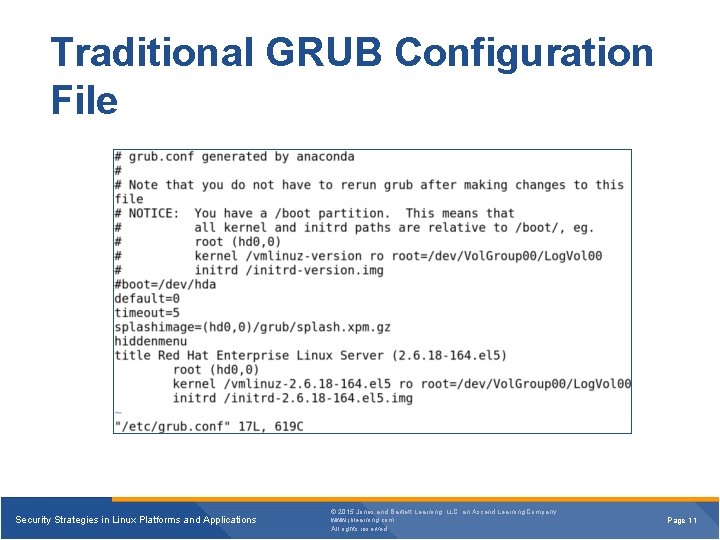
Traditional GRUB Configuration File Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

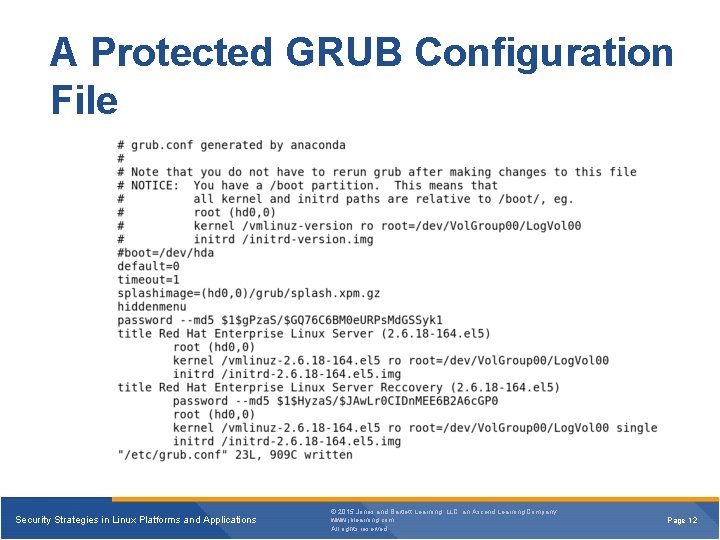
A Protected GRUB Configuration File Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

Challenges of Standard Kernel § Different kernels for different architectures § What kernels can be installed on your system? § What kernel is best for your needs? § When do you consider a different kernel? § You may need to customize a kernel or install a new kernel for more security. Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

Why Use Obscurity? Boot menus Boot loader Boot config files Services Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

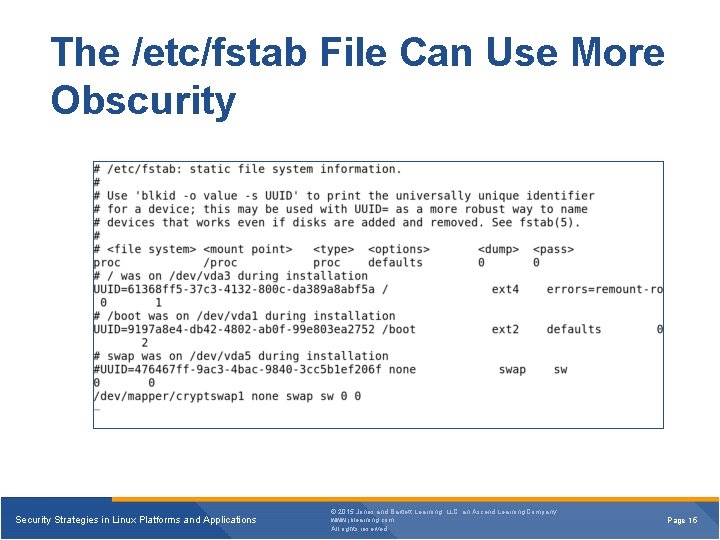
The /etc/fstab File Can Use More Obscurity Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

Five Process Controls Nonrepudiation Confidentiality Integrity Security Strategies in Linux Platforms and Applications Privacy Alarm © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

Summary § Physical server security § Challenges of the standard kernel and possible security issues § Secure boot loaders § Obscurity as a security enhancement Security Strategies in Linux Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17