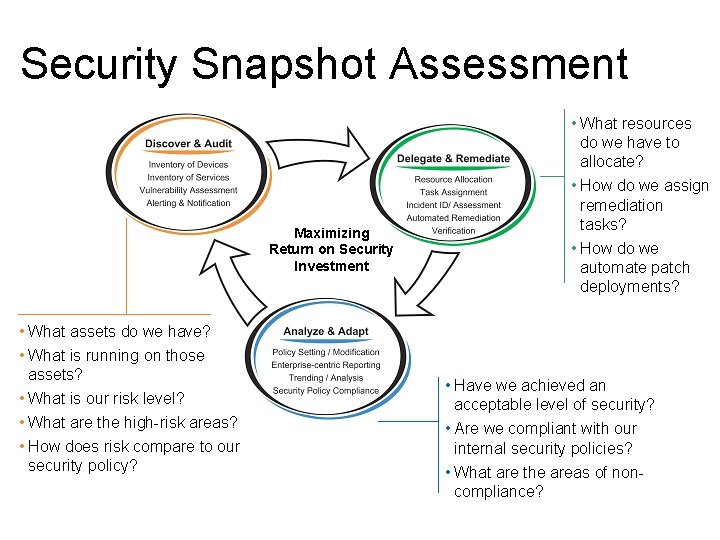
Security Snapshot Assessment Maximizing Return on Security Investment

- Slides: 5

Security Snapshot Assessment Maximizing Return on Security Investment • What assets do we have? • What is running on those assets? • What is our risk level? • What are the high-risk areas? • How does risk compare to our security policy? • What resources do we have to allocate? • How do we assign remediation tasks? • How do we automate patch deployments? • Have we achieved an acceptable level of security? • Are we compliant with our internal security policies? • What are the areas of noncompliance?

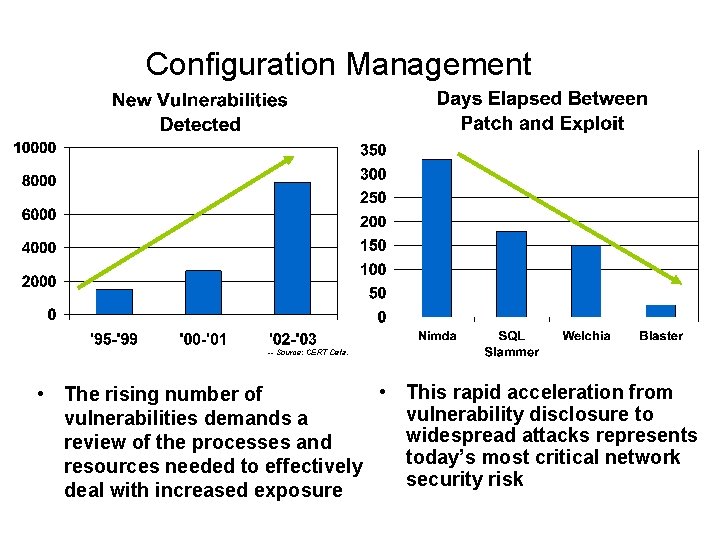
Configuration Management -- Source: CERT Data. • This rapid acceleration from • The rising number of vulnerability disclosure to vulnerabilities demands a widespread attacks represents review of the processes and today’s most critical network resources needed to effectively security risk deal with increased exposure

Business Continuity • The integration of enterprise applications (ERP, SFA, Financials, Call Center, Help Desk, etc. ) are creating complex business processes that require 24 x 7 availability • These business processes rely on network devices within an infrastructure – Servers, routers, switches, etc. • An attack on one network device can have ripple affects on a business process, shutting down services across a network, and crippling business continuity

Regulatory Compliance • Many companies now face board-level inquiries into their security practices • Scope of compliance is now a business and technology issue – Security programs must be developed, implemented and maintained – Identify and assess the risks threatening customer data – Generate timely, accurate and actionable information about their exposures • Internal policies must be created, implemented and enforced – Identify which technologies, methods and people are most vulnerable – Have a consistent baseline of questions around standards, practices, configurations and vulnerabilities GLB 4

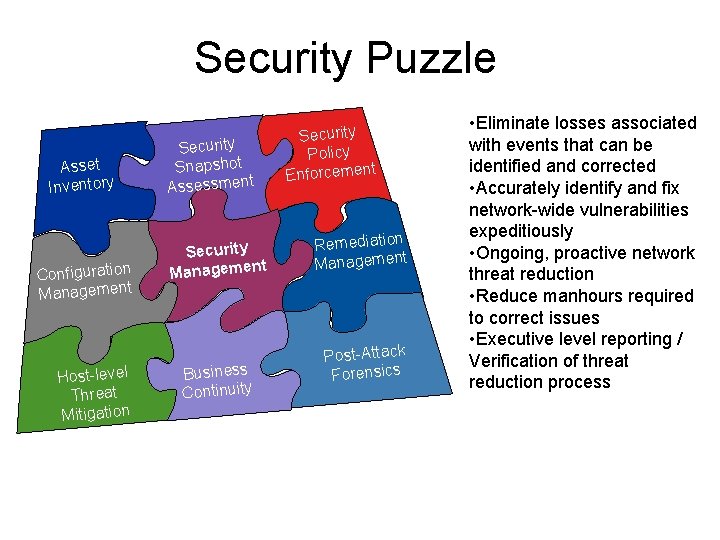
Security Puzzle Asset Inventory Configuration Management Host-level Threat Mitigation Security Snapshot Assessment Security t Managemen Business Continuity Security Policy Enforcement Remediation Management Post-Attack Forensics • Eliminate losses associated with events that can be identified and corrected • Accurately identify and fix network-wide vulnerabilities expeditiously • Ongoing, proactive network threat reduction • Reduce manhours required to correct issues • Executive level reporting / Verification of threat reduction process