Security Service i Why do we need security











- Slides: 29

Security Service i Why do we need security in distributed system? 4 Examples: banking, e-commerce, personal info, classified info i Distributed systems are inherently insecure 4 network Security Service 1

Security Service i Security Requirements 4 Confidentiality 4 Integrity 4 Accountability 4 Availability i threats to Security 4 Gaining access directly 4 Obtaining authorized user info and access 4 Obtaining info through monitoring the comm. Channel 4 Modifying messages on the comm. Channel 4 Performing untraceable malicious actions 4 Denying participations Security Service 2

Security Service i Categories of threats 4 Leakage: unauthorized disclosure of information 4 Tempering: unauthorized modification of information 4 Resource stealing: unauthorized use of computing resources 4 Vandalism: destruction of information 4 Combined threats i Methods of Attack 4 Masquerading: obtain the identity of legitimate users 4 Eavesdropping: listen to and decode request message 4 Tampering : modify request messages 4 Replaying: repetition of request messages 4 Infiltration: h Attacks by legitimate users h Obtaining a legitimate user’s identity h Smuggling client or server objects, virus, worms Security Service 3

Security Service i Security Service Features 4 Identification and authentication 4 Authorization and access control 4 Auditing 4 Communications security 4 Non-repudiation 4 Administration of security policy i Encryption 4 Encryption uses an algorithm and a key to convert plain text into cypher text and vice versa 4 secret key 4 Public key Security Service 4

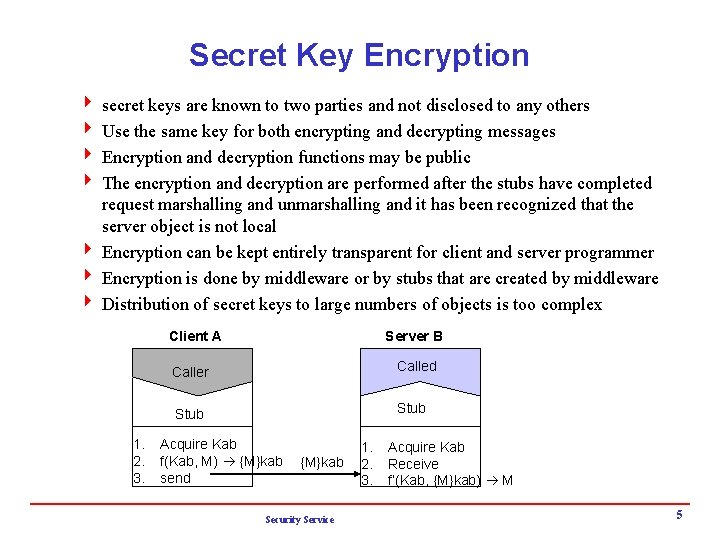
Secret Key Encryption 4 secret keys are known to two parties and not disclosed to any others 4 Use the same key for both encrypting and decrypting messages 4 Encryption and decryption functions may be public 4 The encryption and decryption are performed after the stubs have completed request marshalling and unmarshalling and it has been recognized that the server object is not local 4 Encryption can be kept entirely transparent for client and server programmer 4 Encryption is done by middleware or by stubs that are created by middleware 4 Distribution of secret keys to large numbers of objects is too complex Client A 1. 2. 3. Server B Caller Called Stub Acquire Kab f(Kab, M) {M}kab send {M}kab Security Service 1. 2. 3. Acquire Kab Receive f’(Kab, {M}kab) M 5

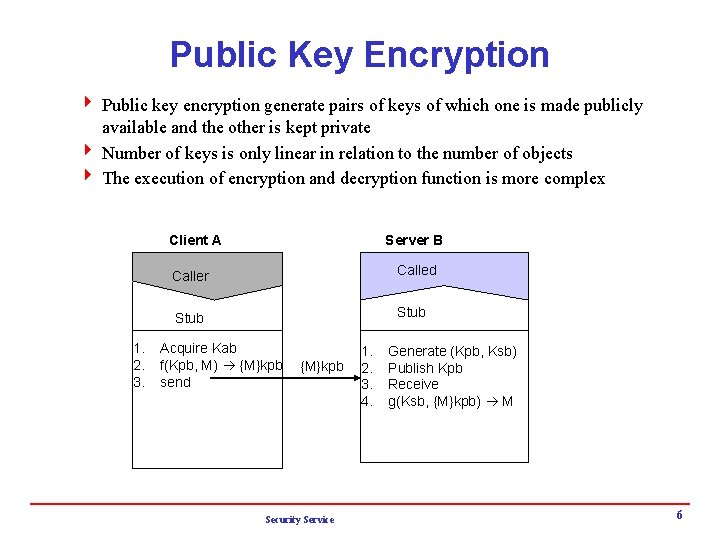
Public Key Encryption 4 Public key encryption generate pairs of keys of which one is made publicly available and the other is kept private 4 Number of keys is only linear in relation to the number of objects 4 The execution of encryption and decryption function is more complex Client A 1. 2. 3. Server B Caller Called Stub Acquire Kab f(Kpb, M) {M}kpb send {M}kpb Security Service 1. 2. 3. 4. Generate (Kpb, Ksb) Publish Kpb Receive g(Ksb, {M}kpb) M 6

Key Distribution i Secure key distribution mechanisms are needed for both secret and public key encryption i Key distribution service 4 Service has to be a trusted service 4 The registration of object with that service has to be trustworthy 4 Needham/Schroeder protocol Security Service 7

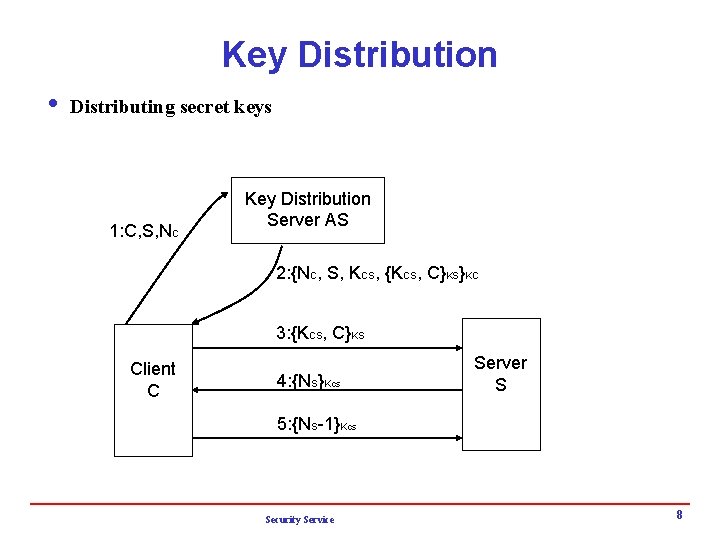
Key Distribution i Distributing secret keys 1: C, S, NC Key Distribution Server AS 2: {NC, S, KCS, {KCS, C}KS}KC 3: {KCS, C}KS Client C 4: {NS}Kcs Server S 5: {NS-1}Kcs Security Service 8

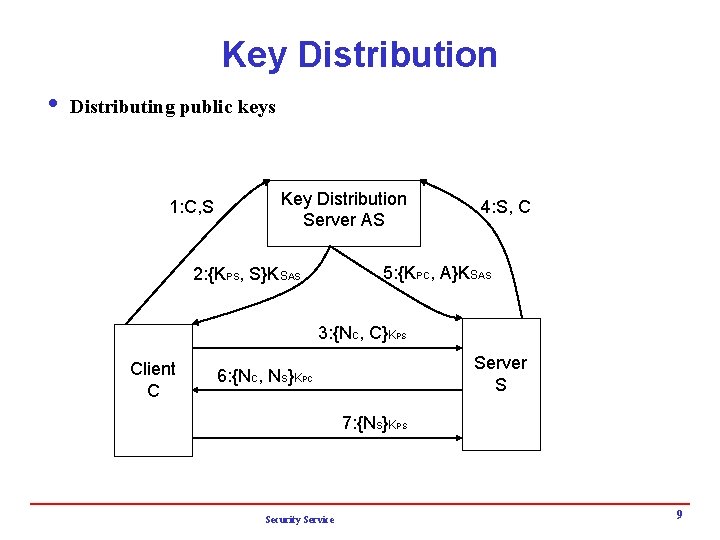
Key Distribution i Distributing public keys 1: C, S Key Distribution Server AS 4: S, C 5: {KPC, A}KSAS 2: {KPS, S}KSAS 3: {NC, C}KPS Client C Server S 6: {NC, NS}KPC 7: {NS}KPS Security Service 9

Higher-Level Security Services i Security Service Features 4 Firewalls 4 Identification and authentication 4 Authorization and access control 4 Auditing 4 Non-repudiation 4 Communications security 4 Administration of security policy Security Service 10

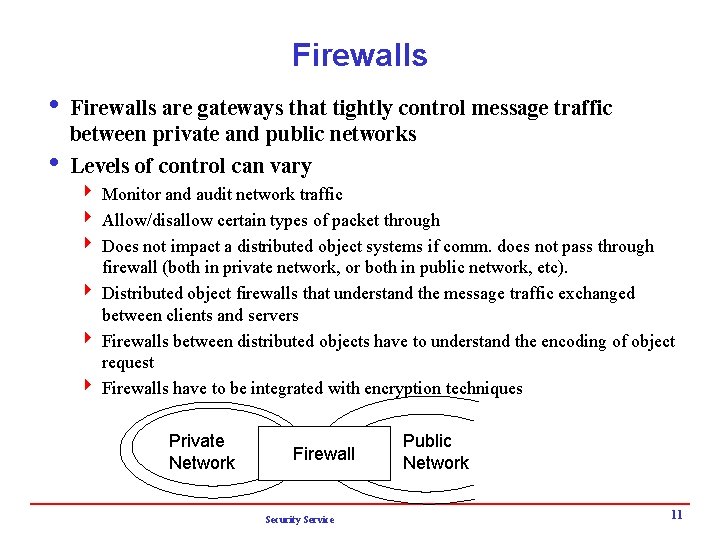
Firewalls i Firewalls are gateways that tightly control message traffic between private and public networks i Levels of control can vary 4 Monitor and audit network traffic 4 Allow/disallow certain types of packet through 4 Does not impact a distributed object systems if comm. does not pass through firewall (both in private network, or both in public network, etc). 4 Distributed object firewalls that understand the message traffic exchanged between clients and servers 4 Firewalls between distributed objects have to understand the encoding of object request 4 Firewalls have to be integrated with encryption techniques Private Network Firewall Security Service Public Network 11

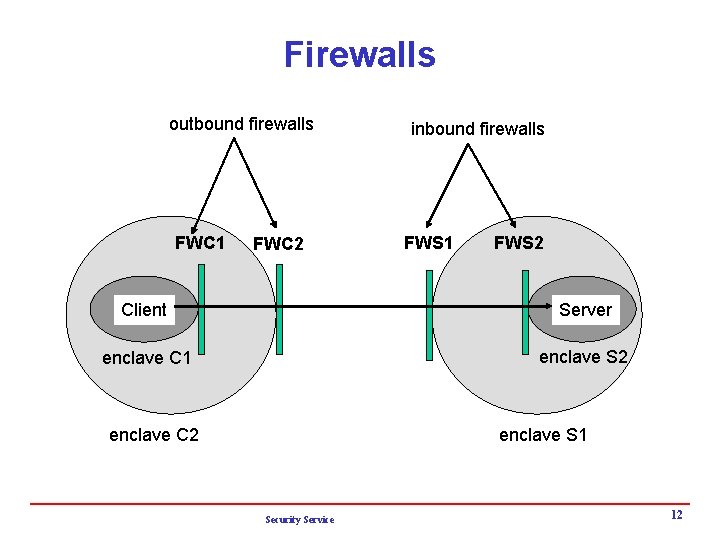
Firewalls outbound firewalls FWC 1 FWC 2 inbound firewalls FWS 1 FWS 2 Client Server enclave C 1 enclave S 2 enclave C 2 enclave S 1 Security Service 12

Types of Firewalls i Packet Filtering 4 Allow all kinds of packets, but only to this IP address and this port 4 Allow incoming traffic only from the specified IP subnets i Application-level gateways (Figure 12. 4) i CORBA and Firewalls 4 HTTP Tunneling: an IIOP request is enclosed in an HTTP envelope and sent via the HTTP protocol (Figure 12. 5) 4 GIOP Proxies: callbacks i Security Socket Layer 4 A protocol on top of TCP/IP that adds security capabilities 4 SSL API is an extension to the TCP/IP socket API 4 Encryption of messages 4 Authentication of the server based on digital certificates and signatures 4 Optional authentication of the cleint Security Service 13

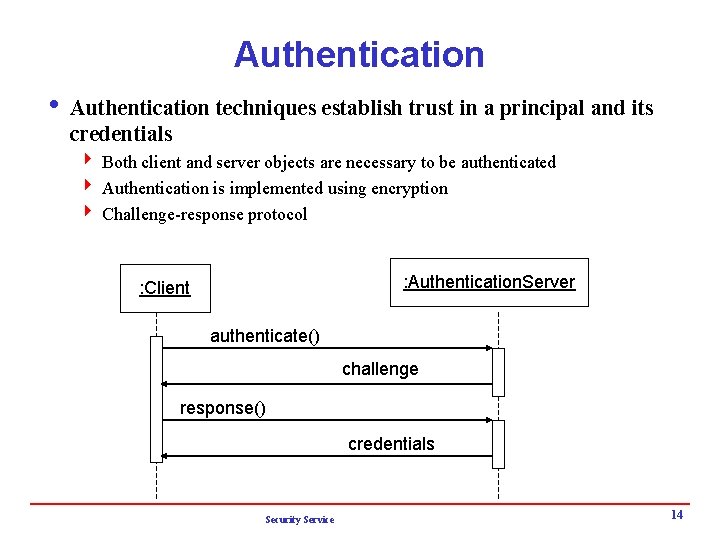
Authentication i Authentication techniques establish trust in a principal and its credentials 4 Both client and server objects are necessary to be authenticated 4 Authentication is implemented using encryption 4 Challenge-response protocol : Authentication. Server : Client authenticate() challenge response() credentials Security Service 14

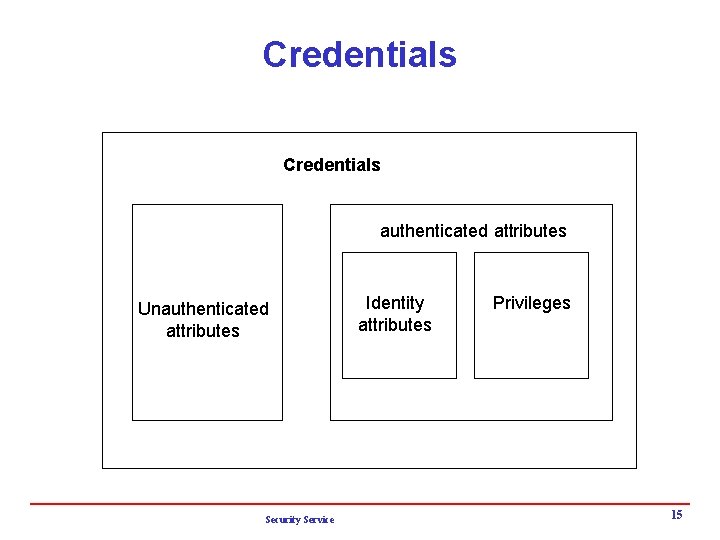
Credentials authenticated attributes Unauthenticated attributes Security Service Identity attributes Privileges 15

Access Control i Access control mechanisms decide whether or not an object request can be granted to a client object 4 A principal is a human user or a system entity that is registered in and authenticated to a system 4 Credentials contain the security attributes of a principal 4 Object invocation access policies determine whether a particular principal is allowed to perform an object request 4 Two forms of access policies: h Object invocation access policies are implemented by the object-oriented middleware h Application object access policies are enforced at an application level and implemented by the application developer Security Service 16

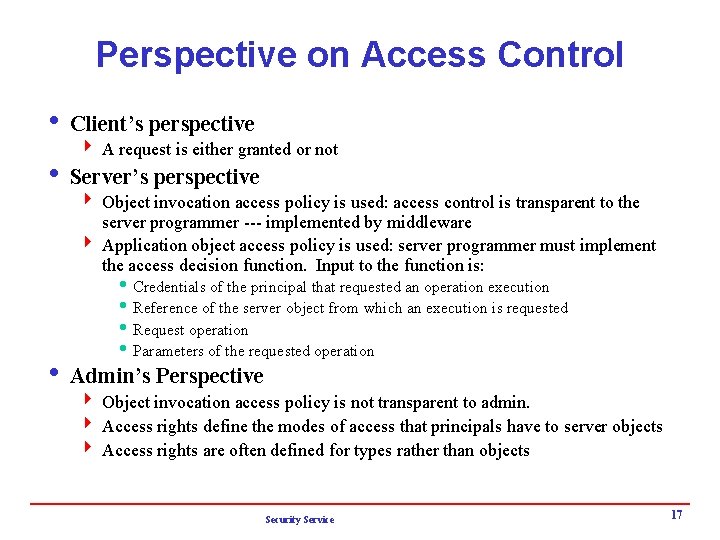
Perspective on Access Control i Client’s perspective 4 A request is either granted or not i Server’s perspective 4 Object invocation access policy is used: access control is transparent to the server programmer --- implemented by middleware 4 Application object access policy is used: server programmer must implement the access decision function. Input to the function is: h Credentials of the principal that requested an operation execution h Reference of the server object from which an execution is requested h Request operation h Parameters of the requested operation i Admin’s Perspective 4 Object invocation access policy is not transparent to admin. 4 Access rights define the modes of access that principals have to server objects 4 Access rights are often defined for types rather than objects Security Service 17

Security Service i Privileges and Privilege Delegation Scheme 4 Own privilege 4 Caller’s privilege 4 Combined privilege h Use both h Combine and generate new credentials Security Service 18

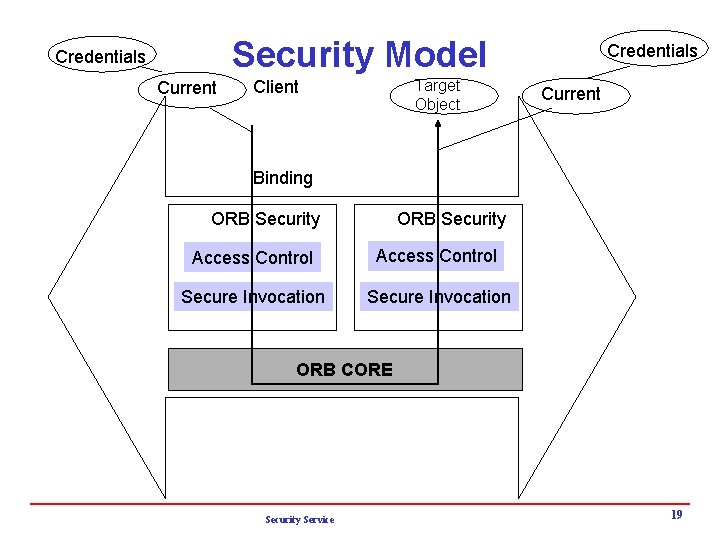
Security Model Credentials Current Target Object Client Credentials Current Binding ORB Security Access Control Secure Invocation ORB CORE Security Service 19

Security Service i Security Model 4 Clients, target objects, operation invocations 4 Building request transmitting the request executing an operation sending a reply 4 Figure 12. 8 Security Service is closely tied with ORB and is not an independent object service, but an ORB service 4 Security-aware applications vs Security-unaware applications i Principles and Security Attributes (Figure 12. 9) 4 Establish a security association: h usually, client trust, server authenticate h Binding between client and target h Security service provide current execution context (current) 4 Target object or Security Service decides operation permissions based on the current. (Access control …) 4 Auditing through auditing channel if required. Security Service 20

Security Conformance Levels i Security Conformance Levels 4 Level allows ORB security to be applied to applications that are not securityaware: authentication; security policies; provision of message integrity and confidentiality; access control policy 4 Level 2 = level 1 + enhanced integrity + trust + auditing Security Service 21

Security Service i Higher-Level Security Services 4 Firewalls: gateways that tightly control message traffic between private and public network 4 Authentication: establish trust in a principal and its credentials 4 Access control: decide whether or not an object request can be granted to a client object h Client: request is either granted or not h Server: – Performed by middleware (invocation policy define on object) – Server application make access control decisions based on the data: Request credentials References to server objects Requested operations Parameters to the requested operations h Admin: – Define the modes of access that principals have to server objects – Access rights are defined for types rather than objects Security Service 22

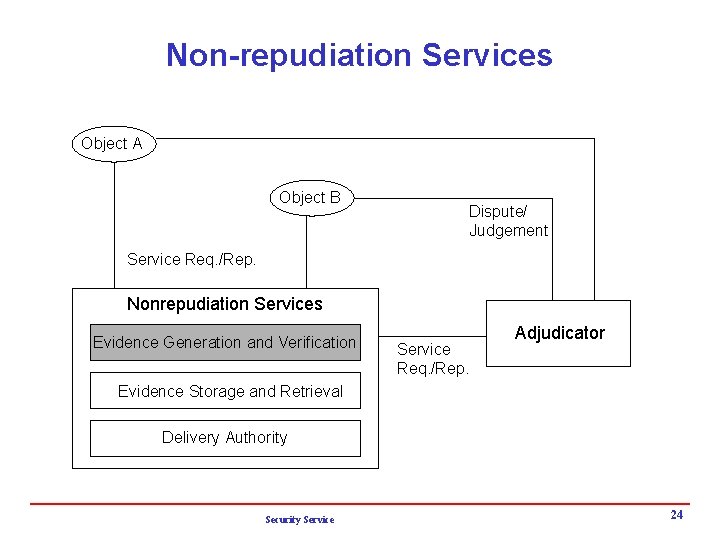
Security Service i Non-repudiation Services 4 Evidence Generation and Verification 4 Evidence Storage and Retrieval 4 Delivery Authority Security Service 23

Non-repudiation Services Object A Object B Dispute/ Judgement Service Req. /Rep. Nonrepudiation Services Evidence Generation and Verification Service Req. /Rep. Adjudicator Evidence Storage and Retrieval Delivery Authority Security Service 24

Security Service i Security Domains 4 Security Policies: h Hierarchy h Overlap h Conflict i Finding the Security Features of an ORB Get_service_information() i Authentication of a User Principal i Selecting Privileges Credentials: get_credentials(); set_privileges() i Making a Security Invocation Access_Decision object, access_allowed(); Audit. Decision object, audit_needed(); audit_channel() Security Service 25

Security Service i Non-repudiation 4 Generate_token(): generate an unforgeable token to be used in the evidence 4 Verify_evidence(): check if evidence is valid 4 Form_complete_evidence(): use original token to generate further evidence, Security Service 26

Security Service i Application Security Interfaces 4 Common Security Types 4 Security Level 1 (for security-unaware applications) Interface Current: CORBA: Current{//PIDL Security: : Attribute. List get_attributes(in Security: : Attribute. Type. List attributes); }; For level 1, only allow the client to know what attributes are available 4 Security Level 2 (for security-aware applications) Current interface inherits the one form Security. Level 1, extends functionality with references to the following objects: Required. Rights, Access. Decision, Audit. Decision, and Principal. Authenticator, and Credentials objects. Security Service 27

Security Service i Required. Rights 4 Get_required_rights() 4 Set_required_rights() i Principal. Authenticator 4 Get_supported_authen_methods(); 4 Authenticate(); 4 Continue_authentication(); i Credentials 4 Copy() 4 Destroy() 4 Get_security_feature() 4 Get_attributes() 4 Set_privileges(); 4 Is_valid(); 4 Refresh(); Security Service 28

Security Service i Object 4 Get_policy() 4 Get_domain_managers() 4 Set_policy_overrides() Security Service 29