Security Privacy and Ethical Issues in Information Systems


























- Slides: 40

Security, Privacy, and Ethical Issues in Information Systems and the Internet Chapter 14 MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 1

Principles and Learning Objectives • Policies and procedures must be established to avoid computer waste and mistakes. – Describe some examples of waste and mistakes in an IS environment, their causes, and possible solutions. – Identify policies and procedures useful in eliminating waste and mistakes. MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 2

Principles and Learning Objectives • Computer crime is a serious and rapidly growing area of concern requiring management attention. – Explain the types and effects of computer crime. – Identify specific measures to prevent computer crime. – Discuss the principles and limits of an individual’s right to privacy. MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 3

Principles and Learning Objectives • Jobs, equipment, and working conditions must be designed to avoid negative health effects. – List the important effects of computers on the work environment. – Identify specific actions that must be taken to ensure the health and safety of employees. – Outline criteria for the ethical use of information systems. MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 4

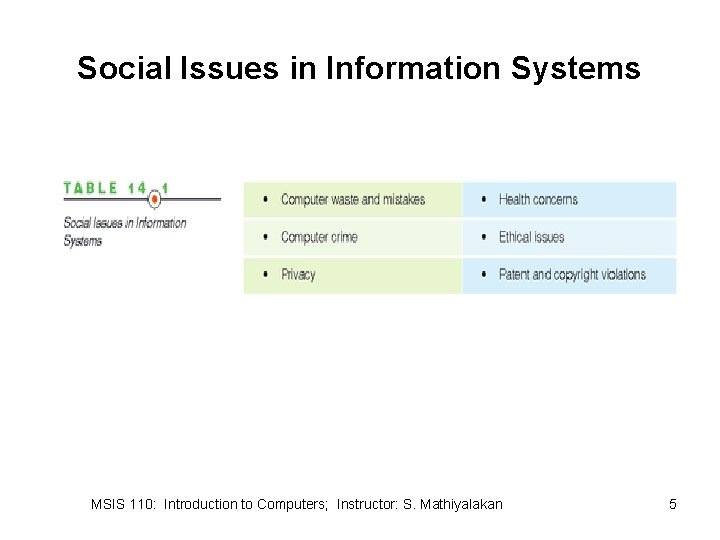
Social Issues in Information Systems MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 5

Computer Waste & Mistakes MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 6

Computer Waste • Discard technology • Unused systems • Personal use of corporate time and technology MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 7

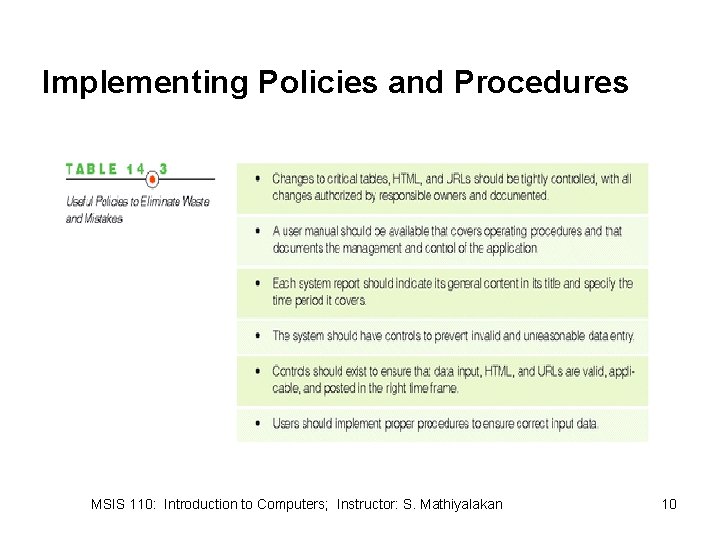
Preventing Computer Waste and Mistakes • • Establish Policies and Procedures Implement Policies and Procedures Monitor Policies and Procedures Review Policies and Procedures MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 8

Preventing Computer-Related Waste and Mistakes MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 9

Implementing Policies and Procedures MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 10

Computer Crime MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 11

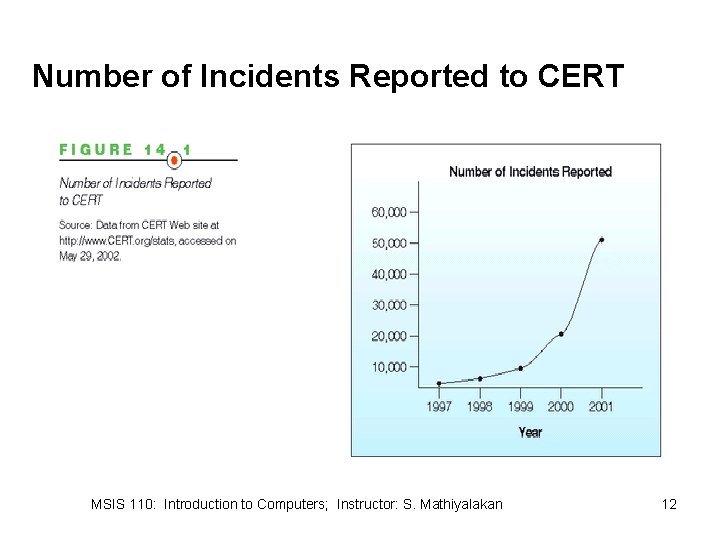
Number of Incidents Reported to CERT MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 12

Computer Crime and Security Survey MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 13

The Computer as a Tool to Commit Crime • • Social engineering Dumpster diving Identity theft Cyberterrorism MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 14

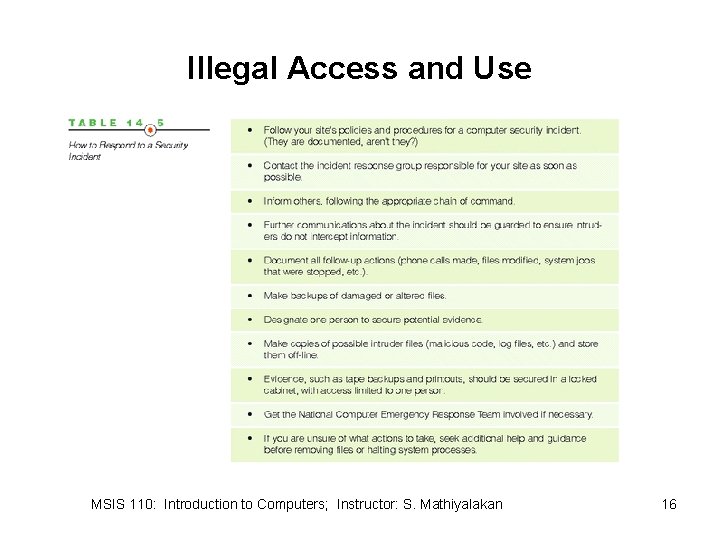
Computers as Objects of Crime • Illegal access and use – Hackers vs. crackers – Script bunnies – Insiders MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 15

Illegal Access and Use MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 16

Data Alteration and Destruction • Virus – Application virus – System virus – Macro virus • Worm • Logic bomb MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 17

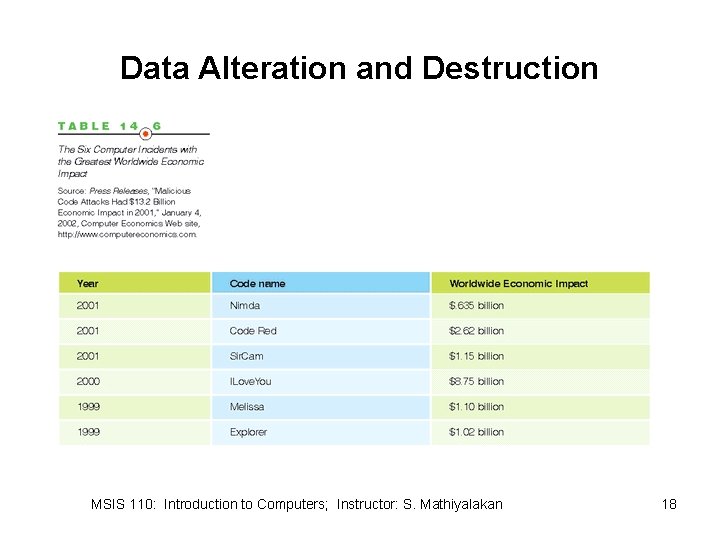
Data Alteration and Destruction MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 18

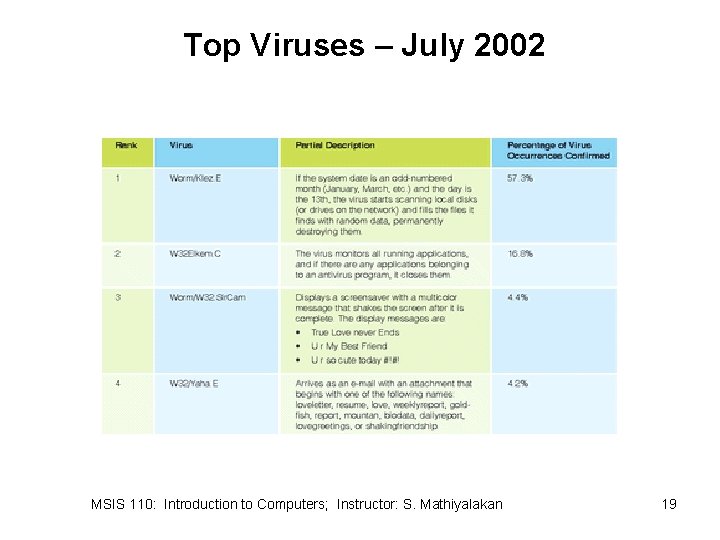
Top Viruses – July 2002 MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 19

Top Viruses – July 2002 MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 20

Computers as Objects of Crime • • Information and equipment theft Software and Internet piracy Computer-related scams International computer crime MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 21

Preventing Computer-Related Crime • Crime prevention by state and federal agencies • Crime prevention by corporations – Public Key Infrastructure (PKI) – Biometrics • Antivirus programs MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 22

Preventing Computer-Related Crime • Intrusion Detection Software • Managed Security Service Providers (MSSPs) • Internet Laws for Libel and Protection of Decency MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 23

Preventing Crime on the Internet • Develop effective Internet and security policies • Use a stand-alone firewall with network monitoring capabilities • Monitor managers and employees • Use Internet security specialists to perform audits MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 24

Common Methods Used to Commit Computer Crimes MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 25

How to Protect Your Corporate Data from Hackers MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 26

Privacy MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 27

Privacy Issues • • Privacy and the Federal Government Privacy at work E-mail privacy Privacy and the Internet MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 28

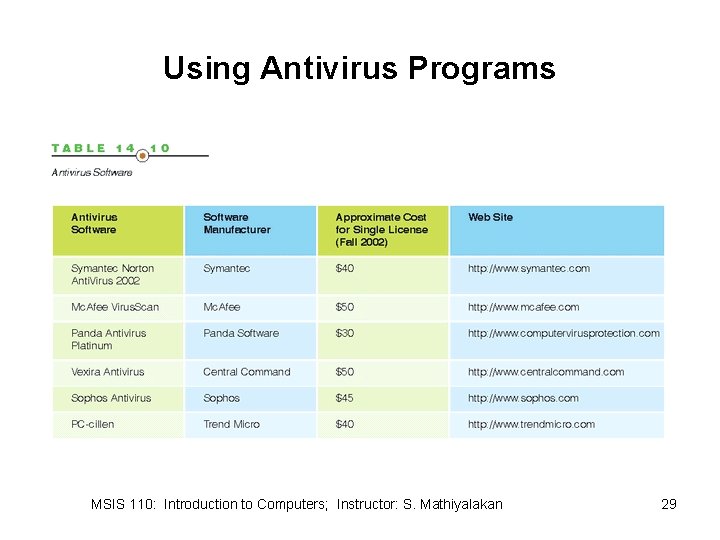
Using Antivirus Programs MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 29

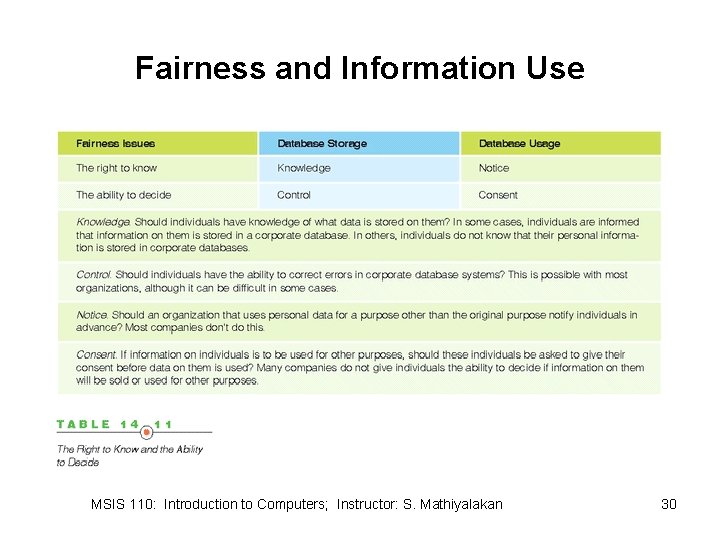
Fairness and Information Use MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 30

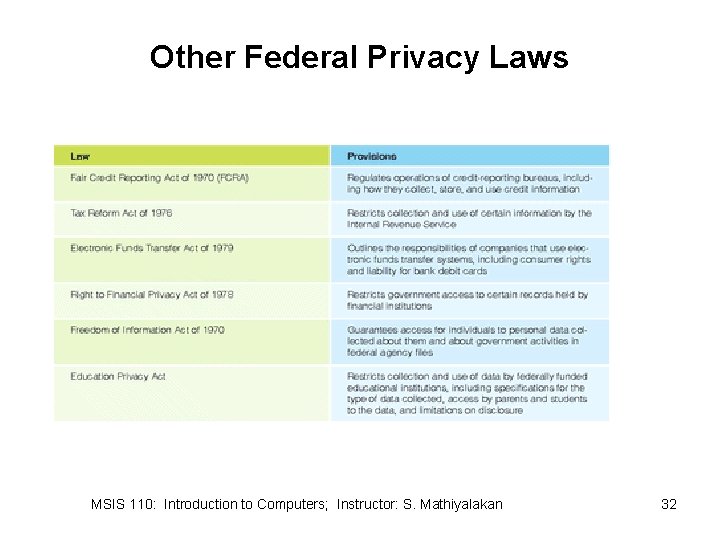
Federal Privacy Laws and Regulations • The Privacy Act of 1979 • Gramm-Leach-Bliley Act • USA Patriot Act MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 31

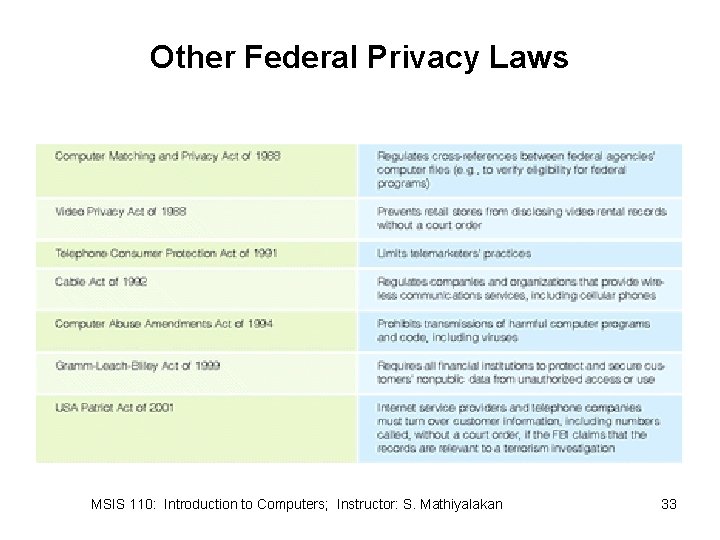
Other Federal Privacy Laws MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 32

Other Federal Privacy Laws MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 33

The Work Environment MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 34

Health Concerns • Repetitive stress injury (RSI) • Carpal tunnel syndrome (CTS) • Ergonomics MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 35

Avoiding Health and Environment Problems • • Maintain good posture and positioning. Don’t ignore pain or discomfort. Use stretching and strengthening exercises. Find a good physician who is familiar with RSI and how to treat it. MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 36

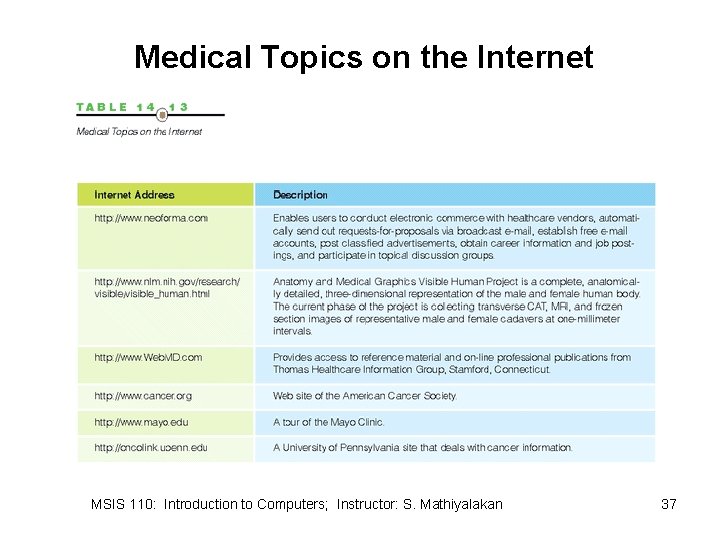
Medical Topics on the Internet MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 37

Ethical Issues in Information Systems • The AITP Code of Ethics – Obligation to management – Obligation to fellow AITP members – Obligation to society • The ACM Code of Professional Conduct – Acquire and maintain professional competence MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 38

AITP Code of Ethics MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 39

Summary • Computer waste - the inappropriate use of computer technology and resources in both the public and private sectors • Software and Internet piracy - represent the most common computer crime • Ethics - determine generally accepted and discouraged activities within a company MSIS 110: Introduction to Computers; Instructor: S. Mathiyalakan 40