Security on Grid User Interface Internals and APIs










![Certificate Information • To get cert information run grid-cert-info [scampana@grid 019: ~]$ grid-cert-info -subject Certificate Information • To get cert information run grid-cert-info [scampana@grid 019: ~]$ grid-cert-info -subject](https://slidetodoc.com/presentation_image_h2/b0edfcac407df5ec9574f5c6f0c6ed45/image-22.jpg)













- Slides: 46

Security on Grid: User Interface, Internals and APIs Simone Campana LCG Experiment Integration and Support CERN IT

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 2

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 3

Glossary • Principal • An entity: a user, a program, or a machine • Credentials • Some data providing a proof of identity • Authentication • Verify the identity of the principal • Authorization • Map an entity to some set of privileges • Confidentiality • Encrypt the message so that only the recipient can understand it • Integrity • Ensure that the message has not been altered in the transmission • Non-repudiation • Impossibility of denying the authenticity of a digital signature First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 4

Overview • Glosary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 5

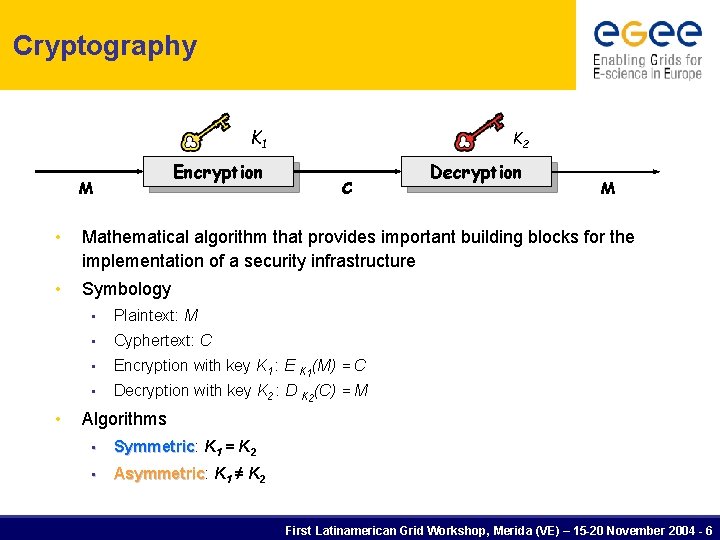
Cryptography K 1 Encryption M K 2 C Decryption M • Mathematical algorithm that provides important building blocks for the implementation of a security infrastructure • Symbology • • Plaintext: M • Cyphertext: C • Encryption with key K 1 : E K 1(M) = C • Decryption with key K 2 : D K 2(C) = M Algorithms • Symmetric: Symmetric K 1 = K 2 • Asymmetric: Asymmetric K 1 ≠ K 2 First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 6

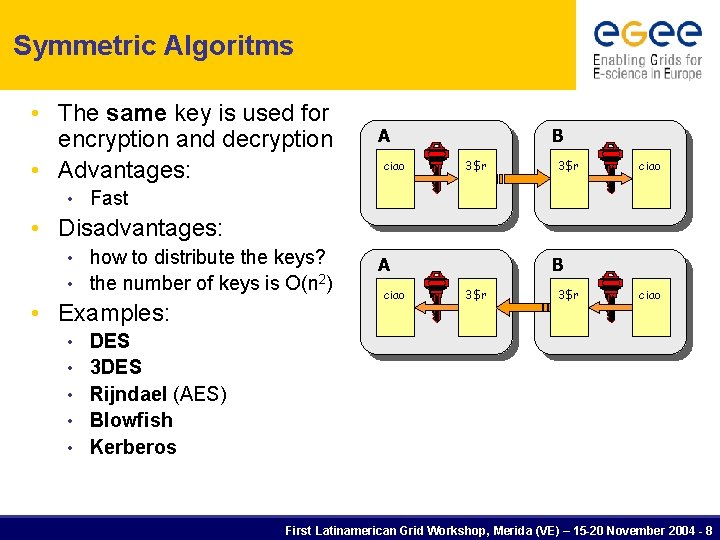
Symmetric Algoritms • The same key is used for encryption and decryption • Advantages: • A ciao B 3$r ciao Fast • Disadvantages: how to distribute the keys? • the number of keys is O(n 2) • • Examples: • • • A ciao B 3$r ciao DES 3 DES Rijndael (AES) Blowfish Kerberos First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 8

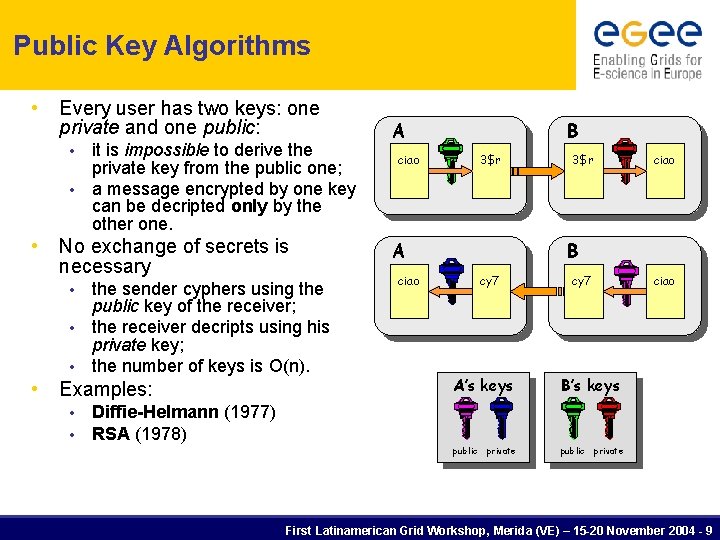
Public Key Algorithms • Every user has two keys: one private and one public: • • • No exchange of secrets is necessary • • it is impossible to derive the private key from the public one; a message encrypted by one key can be decripted only by the other one. the sender cyphers using the public key of the receiver; the receiver decripts using his private key; the number of keys is O(n). Examples: • • A ciao B 3$r A ciao 3$r ciao B cy 7 A’s keys B’s keys public private ciao Diffie-Helmann (1977) RSA (1978) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 9

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 10

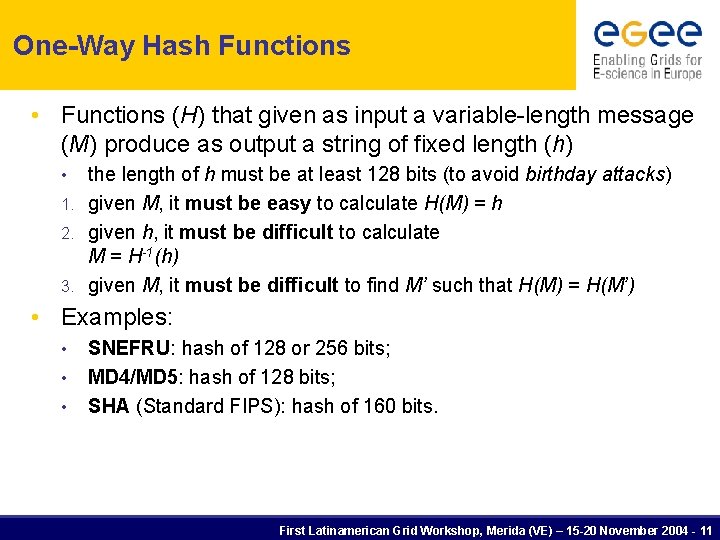
One-Way Hash Functions • Functions (H) that given as input a variable-length message (M) produce as output a string of fixed length (h) the length of h must be at least 128 bits (to avoid birthday attacks) 1. given M, it must be easy to calculate H(M) = h 2. given h, it must be difficult to calculate M = H-1(h) 3. given M, it must be difficult to find M’ such that H(M) = H(M’) • • Examples: • • • SNEFRU: hash of 128 or 256 bits; MD 4/MD 5: hash of 128 bits; SHA (Standard FIPS): hash of 160 bits. First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 11

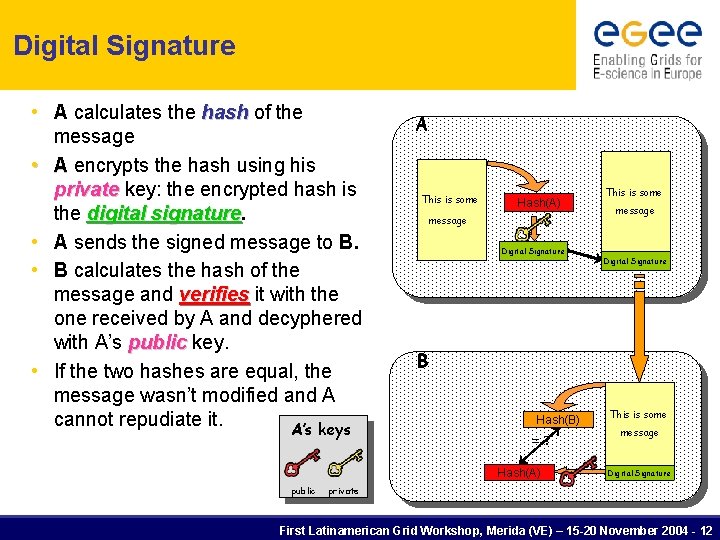
Digital Signature • A calculates the hash of the message • A encrypts the hash using his private key: the encrypted hash is the digital signature • A sends the signed message to B. • B calculates the hash of the message and verifies it with the one received by A and decyphered with A’s public key. • If the two hashes are equal, the message wasn’t modified and A cannot repudiate it. A’s keys A This is some Hash(A) message Digital Signature B Hash(B) =? Hash(A) public This is some message Digital Signature private First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 12

Digital Certificates • A’s digital signature is safe if: 1. 2. • A’s private key is not compromised B knows A’s public key How can B be sure that A’s public key is really A’s public key and not someone else’s? • • A third party guarantees the correspondence between public key and owner’s identity, by signing a document which contains the owner’s identity and his public key (Digital Certificate) Both A and B must trust this third party • Two models: • • X. 509: hierarchical organization; PGP: “web of trust”. First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 13

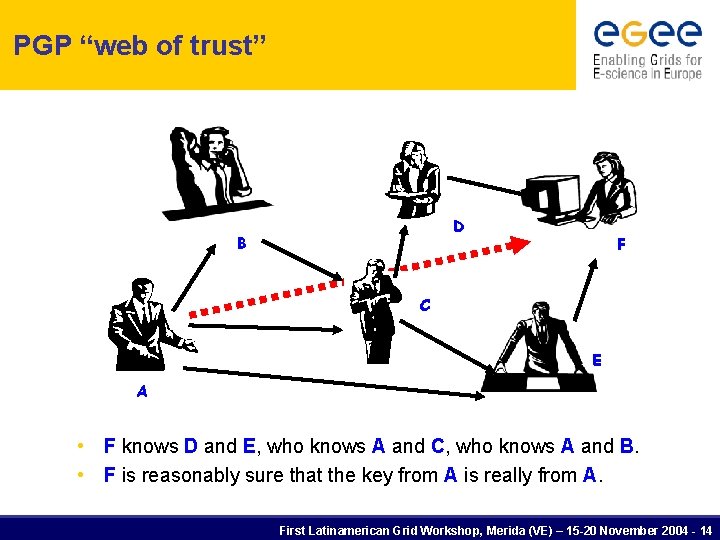
PGP “web of trust” D B F C E A • F knows D and E, who knows A and C, who knows A and B. • F is reasonably sure that the key from A is really from A. First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 14

X. 509 The “third party” is called Certification Authority (CA). • Issue certificates for users, programs and machines • Check the identity and the personal data of the requestor • Registration Authorities (RAs) do the actual validation • CA’s periodically publish a list of compromised certificates • Certificate Revocation Lists (CRL) • They contain all the revoked certificates yet to expire • Online Certificate Status Protocol (OCSP). • CA certificates are self-signed First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 15

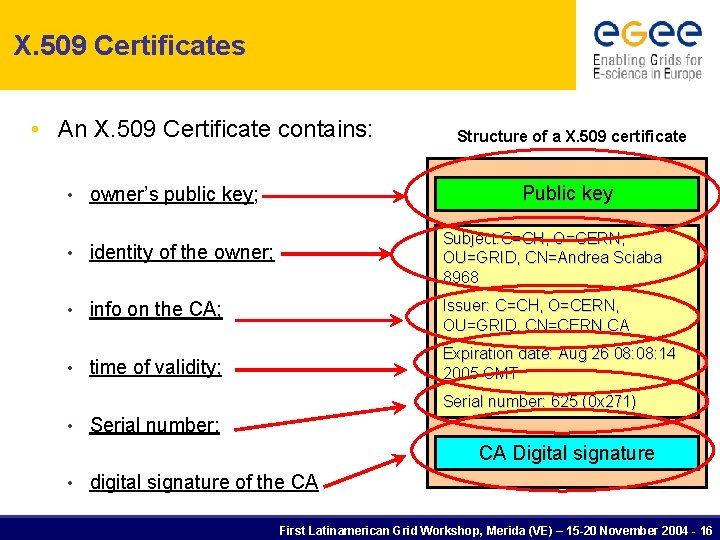
X. 509 Certificates • An X. 509 Certificate contains: Structure of a X. 509 certificate Public key • owner’s public key; • identity of the owner; Subject: C=CH, O=CERN, OU=GRID, CN=Andrea Sciaba 8968 • info on the CA; Issuer: C=CH, O=CERN, OU=GRID, CN=CERN CA time of validity; Expiration date: Aug 26 08: 14 2005 GMT • Serial number: 625 (0 x 271) • Serial number; CA Digital signature • digital signature of the CA First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 16

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 17

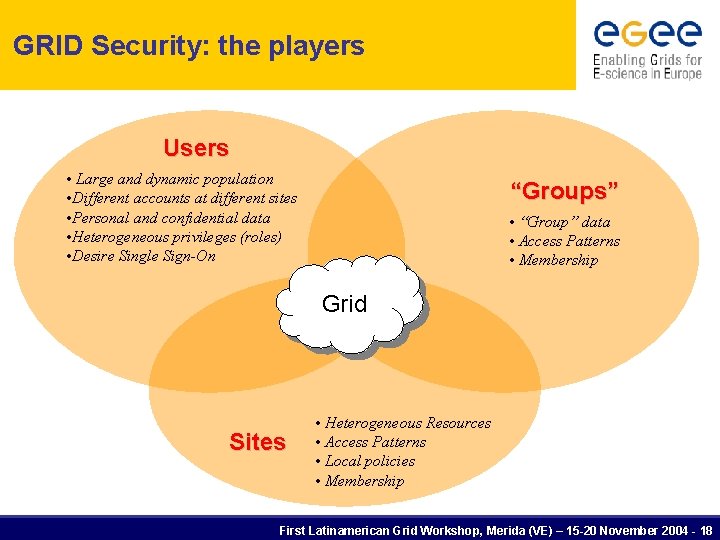
GRID Security: the players Users • Large and dynamic population • Different accounts at different sites • Personal and confidential data • Heterogeneous privileges (roles) • Desire Single Sign-On “Groups” • “Group” data • Access Patterns • Membership Grid Sites • Heterogeneous Resources • Access Patterns • Local policies • Membership First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 18

The Risks • Launch attacks to other sites • Large distributed farms of machines • Illegal or inappropriate data distribution and access sensitive information • Massive distributed storage capacity • Disruption by exploiting security holes • Complex, heterogeneous and dynamic environment • Damage caused by viruses, worms etc. • Highly connected and novel infrastructure First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 19

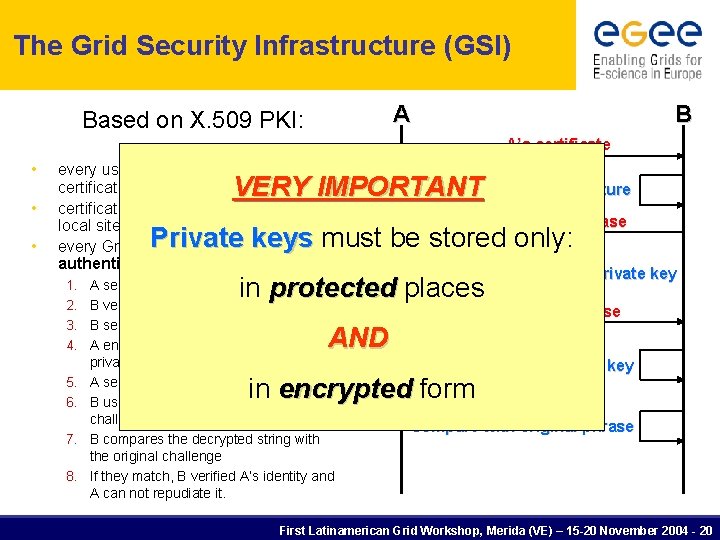
The Grid Security Infrastructure (GSI) B A Based on X. 509 PKI: A’s certificate • • • every user/host/service has an X. 509 certificate; certificates are signed by trusted (by the local sites) CA’s; every Grid transaction is mutually authenticated: VERY IMPORTANTVerify CA signature Random phrase Private keys must be stored only: 1. A sends his certificate; Encrypt with A’ s private key in protected places 2. B verifies signature in A’s certificate; 3. B sends to A a challenge string; Encrypted phrase AND 4. A encrypts the challenge string with his 5. 6. 7. 8. private key; A sends encrypted challenge to B B uses A’s public key to decrypt the challenge. B compares the decrypted string with the original challenge If they match, B verified A’s identity and A can not repudiate it. Decrypt with A’ s public key in encrypted form Compare with original phrase First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 20

Certificate request … more details • Egee/LCG recognizes a given set of CAs • https: //lcg-registrar. cern. ch/pki_certificates. html • How do you request a certificate depends on your CA • The certificate request is created together with the certificate private key (encrypted by a pass phrase) • For GILDA, have a look at the Demo Video: https: //gilda. ct. infn. it/video/Certification/Allproxy. html (Flash) • https: //gilda. ct. infn. it/video/Certification/All. Certproxy. ram (Real) • First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 21

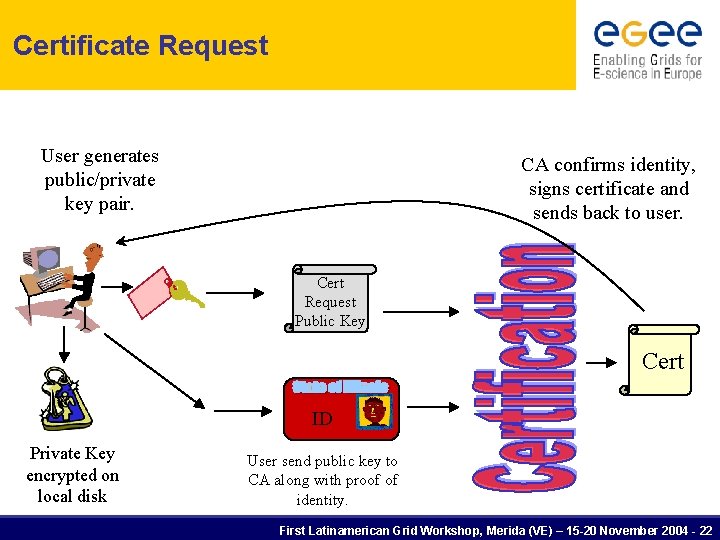
Certificate Request User generates public/private key pair. CA confirms identity, signs certificate and sends back to user. Cert Request Public Key Cert ID Private Key encrypted on local disk User send public key to CA along with proof of identity. First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 22
![Certificate Information To get cert information run gridcertinfo scampanagrid 019 gridcertinfo subject Certificate Information • To get cert information run grid-cert-info [scampana@grid 019: ~]$ grid-cert-info -subject](https://slidetodoc.com/presentation_image_h2/b0edfcac407df5ec9574f5c6f0c6ed45/image-22.jpg)
Certificate Information • To get cert information run grid-cert-info [scampana@grid 019: ~]$ grid-cert-info -subject /C=CH/O=CERN/OU=GRID/CN=Simone Campana 7461 • Options for printing cert information -all -subject -issuer -startdate -enddate -help First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 23

X. 509 Proxy Certificate • GSI extension to X. 509 Identity Certificates • • • Enables single sign-on Support some important features • • signed by the normal end entity cert (or by another proxy). Delegation Mutual authentication Has a limited lifetime (minimized risk of “compromised credentials”) It is created by the grid-proxy-init command: % grid-proxy-init Enter PEM pass phrase: ****** • Options for grid-proxy-init: • • • -hours <lifetime of credential> -bits <length of key> -help First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 24

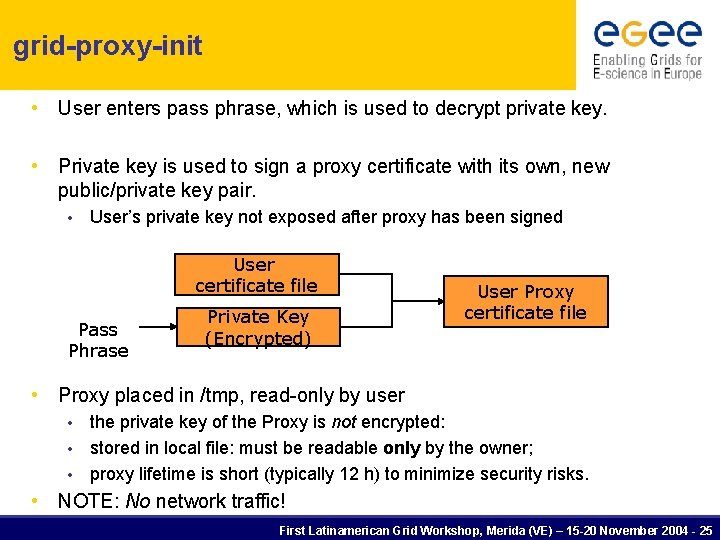
grid-proxy-init • User enters pass phrase, which is used to decrypt private key. • Private key is used to sign a proxy certificate with its own, new public/private key pair. • User’s private key not exposed after proxy has been signed User certificate file Pass Phrase Private Key (Encrypted) User Proxy certificate file • Proxy placed in /tmp, read-only by user the private key of the Proxy is not encrypted: • stored in local file: must be readable only by the owner; • proxy lifetime is short (typically 12 h) to minimize security risks. • • NOTE: No network traffic! First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 25

Proxy again … • grid-proxy-init ≡ “login to the Grid” • To “logout” you have to destroy your proxy: • grid-proxy-destroy This does NOT destroy any proxies that were delegated from this proxy. • You cannot revoke a remote proxy • Usually create proxies with short lifetimes • • To gather information about your proxy: • grid-proxy-info • Options for printing proxy information -subject -type -strength -issuer -timeleft -help First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 26

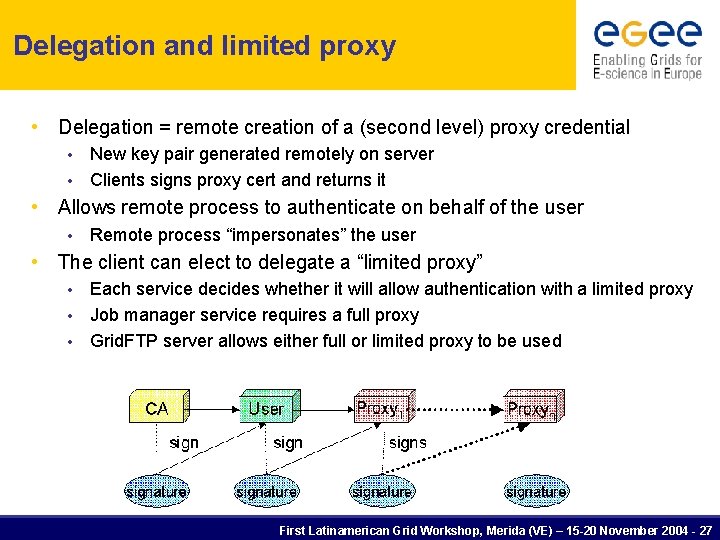
Delegation and limited proxy • Delegation = remote creation of a (second level) proxy credential New key pair generated remotely on server • Clients signs proxy cert and returns it • • Allows remote process to authenticate on behalf of the user • Remote process “impersonates” the user • The client can elect to delegate a “limited proxy” Each service decides whether it will allow authentication with a limited proxy • Job manager service requires a full proxy • Grid. FTP server allows either full or limited proxy to be used • First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 27

Long term proxy • Proxy has limited lifetime (default is 12 h) • Bad idea to have longer proxy • However, a grid task might need to use a proxy for a much longer time • Grid jobs in HEP Data Challenges on LCG last up to 2 days • myproxy server: Allows to create and store a long term proxy certificate: • myproxy-init -s <host_name> -d -n • • -s: <host_name> specifies the hostname of the myproxy server • -d: server to use the subject of the certificate as the default username • -n: avoids the use of a passphrase to access to the long-term proxy – so the WMS can perform the renewals automatically. • myproxy-get-delegation -s <host_name> • Get a new proxy from the My. Proxy server • myproxy-destroy • A dedicated service on the RB can renews automatically the proxy • contacts the myproxy server First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 28

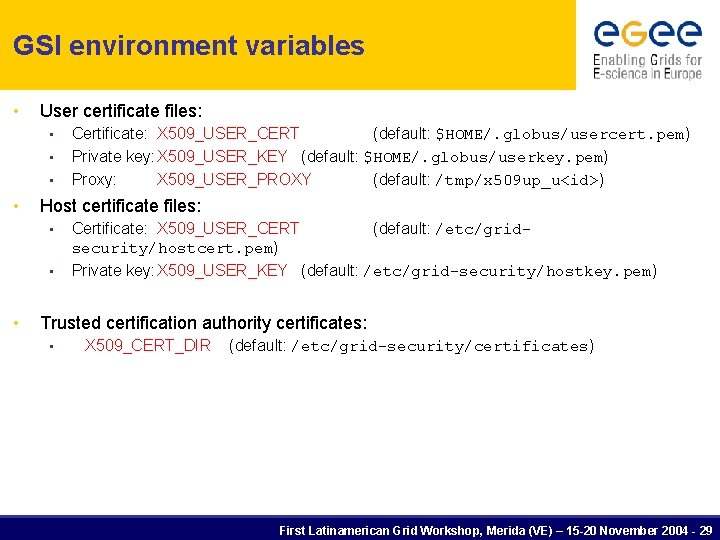
GSI environment variables • User certificate files: • • Host certificate files: • • • Certificate: X 509_USER_CERT (default: $HOME/. globus/usercert. pem) Private key: X 509_USER_KEY (default: $HOME/. globus/userkey. pem) Proxy: X 509_USER_PROXY (default: /tmp/x 509 up_u<id>) Certificate: X 509_USER_CERT (default: /etc/gridsecurity/hostcert. pem) Private key: X 509_USER_KEY (default: /etc/grid-security/hostkey. pem) Trusted certification authority certificates: • X 509_CERT_DIR (default: /etc/grid-security/certificates) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 29

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 30

Virtual Organizations and authorization • Grid users MUST belong to Virtual Organizations What we previously called “Groups” • Sets of users belonging to a collaboration • List of supported VOs: • • https: //lcg-registrar. cern. ch/virtual_organization. html • VOs maintain a list of their members • The list is downloaded by Grid machines to map user certificate subjects to local “pool” accounts. . . "/C=CH/O=CERN/OU=GRID/CN=Simone Campana 7461". dteam "/C=CH/O=CERN/OU=GRID/CN=Andrea Sciaba 8968". cms "/C=CH/O=CERN/OU=GRID/CN=Patricia Mendez Lorenzo-ALICE". alice. . . • Sites decide which VOs to accept /etc/grid-security/grid-mapfile First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 31

On the side: user Registration in a VO • Import your certificate in your browser If you received a. pem certificate you need to convert it to PKCS 12 • Use openssl command line (available in each egee/LCG UI) • • openssl pkcs 12 –export –in usercert. pem –inkey userkey. pem –out my_cert. p 12 –name ’My Name’ • Sign the usage guidelines for the VO • You will be registered in the VO-LDAP server (wait for notification) • Gilda (and other VO): You receive already a PKCS 12 certificate (can import it directly into web browser) • For future use, you will need usercert. pem and userkey. pem in a directory ~/. globus on your UI • Export the PKCS 12 cert to a local dir on UI and use again openssl: • • openssl pkcs 12 -nocerts -in my_cert. p 12 -out userkey. pem • openssl pkcs 12 -clcerts -nokeys -in my_cert. p 12 -out usercert. pem First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 32

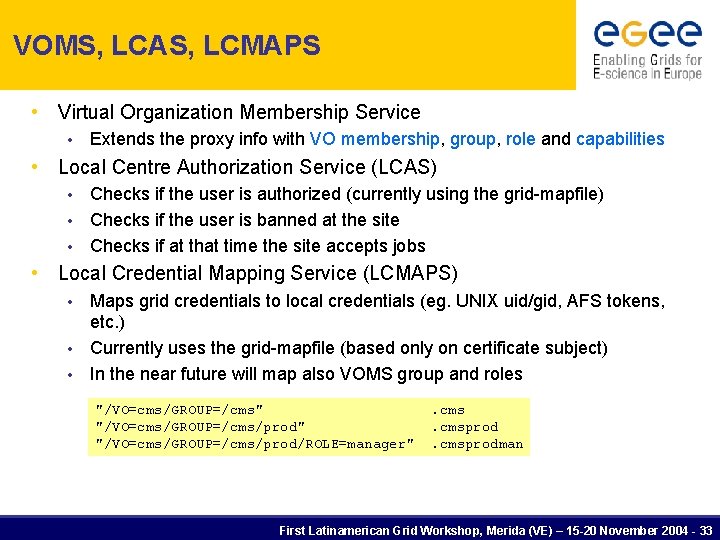
VOMS, LCAS, LCMAPS • Virtual Organization Membership Service • Extends the proxy info with VO membership, group, role and capabilities • Local Centre Authorization Service (LCAS) Checks if the user is authorized (currently using the grid-mapfile) • Checks if the user is banned at the site • Checks if at that time the site accepts jobs • • Local Credential Mapping Service (LCMAPS) Maps grid credentials to local credentials (eg. UNIX uid/gid, AFS tokens, etc. ) • Currently uses the grid-mapfile (based only on certificate subject) • In the near future will map also VOMS group and roles • "/VO=cms/GROUP=/cms" "/VO=cms/GROUP=/cms/prod/ROLE=manager" . cmsprodman First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 33

Overview • Glossary • Encryption • • Symmetric algorithms Asymmetric algorithms: PKI • Certificates • • Digital Signatures X 509 certificates • Grid Security • • Basic concepts Grid Security Infrastructure Proxy certificates Command line interfaces • Virtual Organisation • • Concept of VO and authorization VOMS, LCAS, LCMAPS • C/C++ interfaces (GSS-API, GSS Assist) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 34

Security APIs in egee/LCG • Currently, there are no API developed specifically by egee/LCG • The existing API come from other projects • Authentication • Globus GSS-API, GSS Assist, COG Kits • Authorization • LCAS plugins • LCMAPS plugins • VOMS API • The documentation is generally poor • Some development is on the way. Check CHEP 2004: • http: //indico. cern. ch/contribution. Display. py? contrib. Id=78&session. Id= 23&conf. Id=0 First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 35

API: GSS-API and GSS Assist • GSS-API (Generic Security Services Application Programming Interface) is a generic API for client-server authentication (RFC-2743, 2744) Traditionally, interfaces to Kerberos • Globus interfaced it to GSI • Communication is kept separate • Unfortunately, rather complicated to use • • GSS-API as user interface to GSI C API • Java API • • The Globus GSS Assist routines are designed to simplify the use of the GSSAPI First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 36

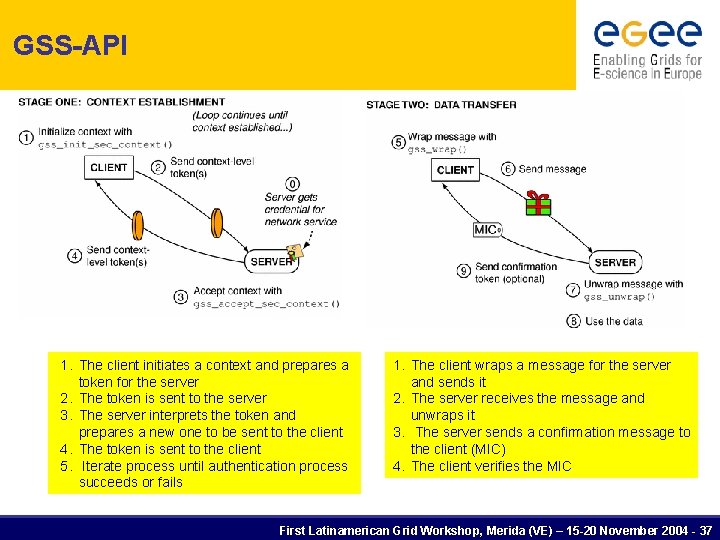
GSS-API 1. The client initiates a context and prepares a token for the server 2. The token is sent to the server 3. The server interprets the token and prepares a new one to be sent to the client 4. The token is sent to the client 5. Iterate process until authentication process succeeds or fails 1. The client wraps a message for the server and sends it 2. The server receives the message and unwraps it 3. The server sends a confirmation message to the client (MIC) 4. The client verifies the MIC First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 37

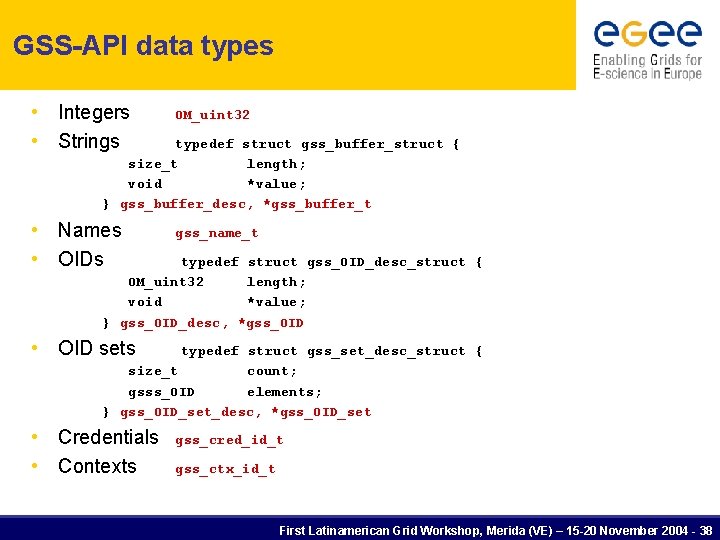
GSS-API data types • Integers • Strings OM_uint 32 • Names • OIDs gss_name_t typedef struct gss_buffer_struct { size_t length; void *value; } gss_buffer_desc, *gss_buffer_t typedef struct gss_OID_desc_struct { OM_uint 32 length; void *value; } gss_OID_desc, *gss_OID • OID sets typedef struct gss_set_desc_struct { size_t count; gsss_OID elements; } gss_OID_set_desc, *gss_OID_set • Credentials • Contexts gss_cred_id_t gss_ctx_id_t First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 38

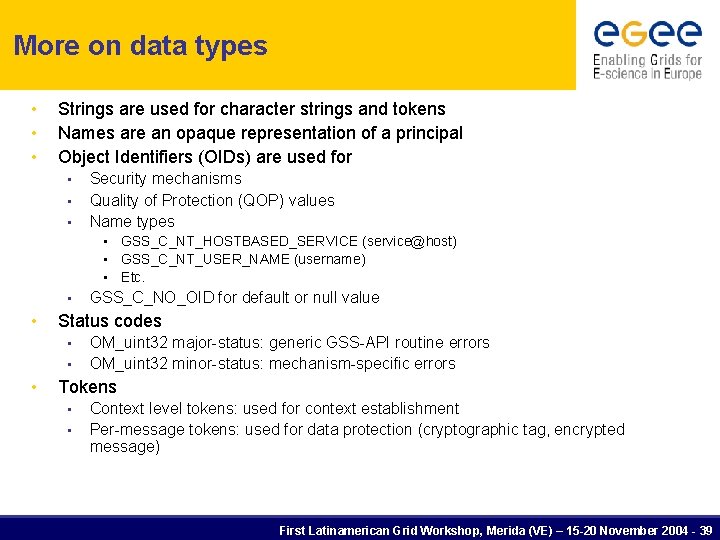
More on data types • • • Strings are used for character strings and tokens Names are an opaque representation of a principal Object Identifiers (OIDs) are used for • • • Security mechanisms Quality of Protection (QOP) values Name types • GSS_C_NT_HOSTBASED_SERVICE (service@host) • GSS_C_NT_USER_NAME (username) • Etc. • • Status codes • • • GSS_C_NO_OID for default or null value OM_uint 32 major-status: generic GSS-API routine errors OM_uint 32 minor-status: mechanism-specific errors Tokens • • Context level tokens: used for context establishment Per-message tokens: used for data protection (cryptographic tag, encrypted message) First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 39

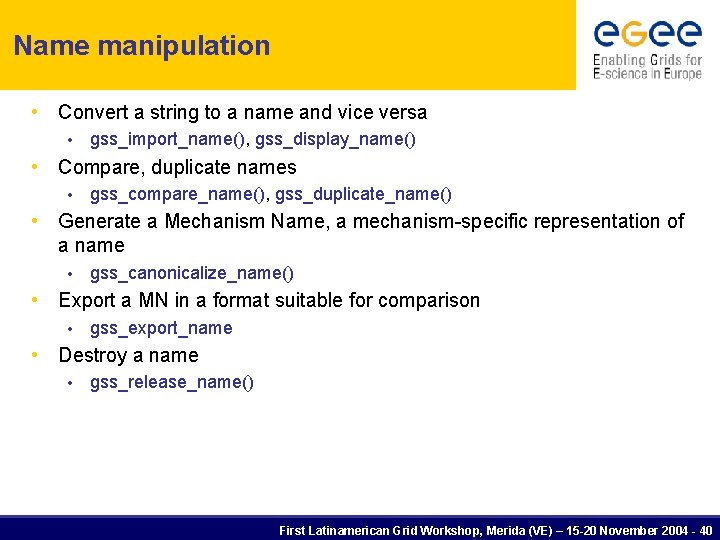
Name manipulation • Convert a string to a name and vice versa • gss_import_name(), gss_display_name() • Compare, duplicate names • gss_compare_name(), gss_duplicate_name() • Generate a Mechanism Name, a mechanism-specific representation of a name • gss_canonicalize_name() • Export a MN in a format suitable for comparison • gss_export_name • Destroy a name • gss_release_name() First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 40

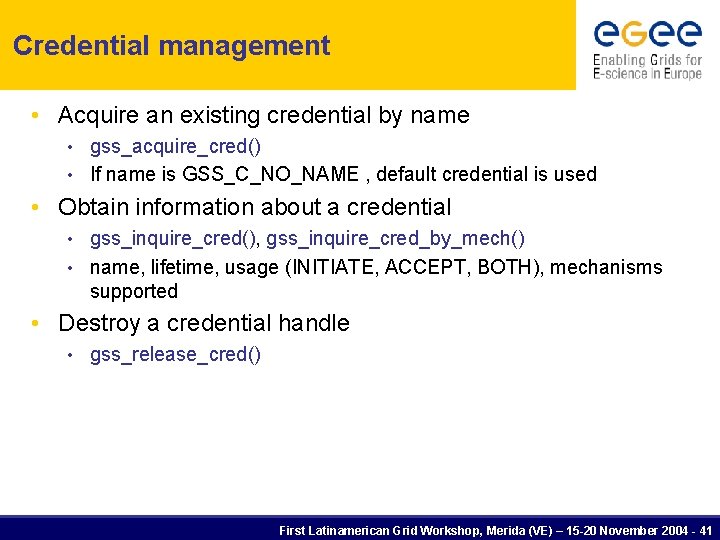
Credential management • Acquire an existing credential by name gss_acquire_cred() • If name is GSS_C_NO_NAME , default credential is used • • Obtain information about a credential gss_inquire_cred(), gss_inquire_cred_by_mech() • name, lifetime, usage (INITIATE, ACCEPT, BOTH), mechanisms supported • • Destroy a credential handle • gss_release_cred() First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 41

Context management • Establish a secure context • gss_init_sec_context(), gss_accept_sec_context() • Retrieve residual duration or other info about context • gss_context_time(), gss_inquire_context() • Export a context from a process to another by means of an interprocess token • gss_export_sec_context(), gss_import_sec_context() • Destroy a secure context • gss_delete_sec_context First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 42

Confidentiality and integrity • Generate a cryptographic message integrity code (MIC) for a message to transfer to the peer application • gss_get_mic() • Verify the received message against the received MIC • gss_verify_mic() • Embed the MIC in the (possibly encrypted) message • gss_wrap() • (possibly decrypt and) verify the embedded MIC • gss_unwrap() First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 43

Globus extensions • Credential import and export To pass credentials from a process to another or storing them • Export to 1) an opaque buffer, or 2) a file in GSI native format • gss_import_cred(), gss_export_cred() • • Delegation at any time • A lot more flexible than standard GSS-API delegation • Delegation at times other than context establishment • Possible to delegate credentials different than those used for context establishment: even for different mechanisms! – Ex. : delegate a Kerberos credential over a context established with GSI • gss_init_delegation(), gss_accept_delegation() First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 44

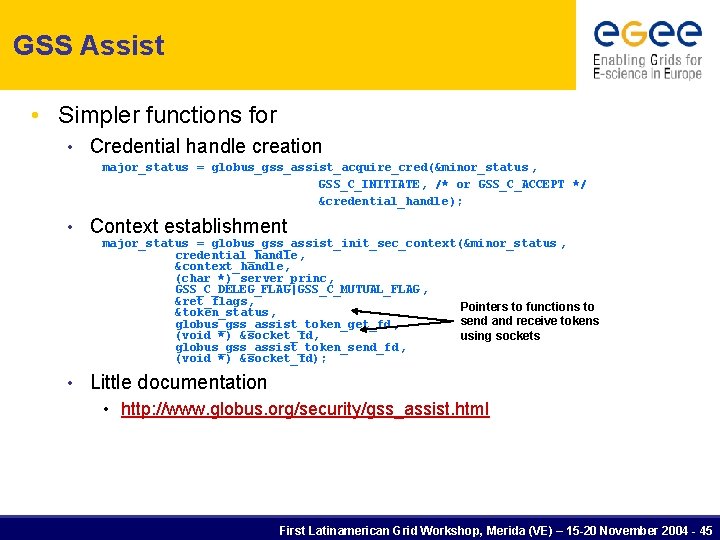
GSS Assist • Simpler functions for • Credential handle creation major_status = globus_gss_assist_acquire_cred(&minor_status , GSS_C_INITIATE, /* or GSS_C_ACCEPT */ &credential_handle); • Context establishment major_status = globus_gss_assist_init_sec_context(&minor_status , credential_handle, &context_handle, (char *) server_princ, GSS_C_DELEG_FLAG|GSS_C_MUTUAL_FLAG , &ret_flags, Pointers to functions to &token_status, send and receive tokens globus_gss_assist_token_get_fd , (void *) &socket_fd, using sockets globus_gss_assist_token_send_fd , (void *) &socket_fd); • Little documentation • http: //www. globus. org/security/gss_assist. html First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 45

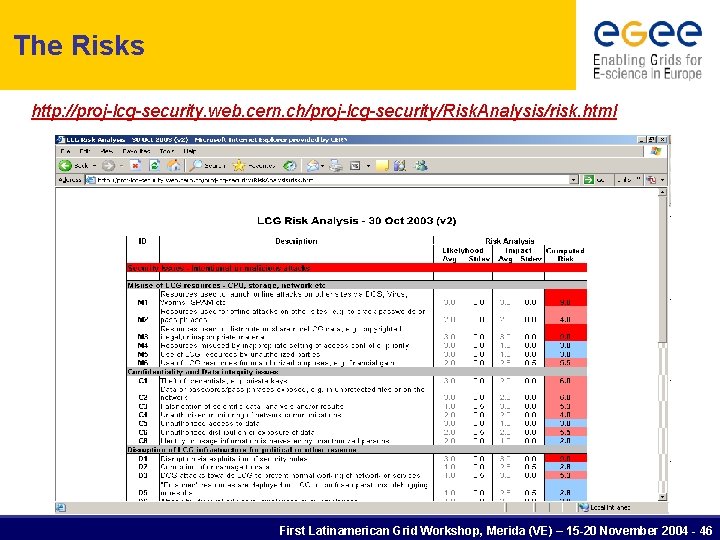
The Risks http: //proj-lcg-security. web. cern. ch/proj-lcg-security/Risk. Analysis/risk. html First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 46

Further Information Grid • LCG Security: http: //proj-lcg-security. web. cern. ch/proj-lcg-security/ • LCG Registration: http: //lcg-registrar. cern. ch/ • Globus Security: http: //www. globus. org/security/ Background • GGF Security: http: //www. gridforum. org/security/ • GSS-API: http: //www. faqs. org/faqs/kerberos-faq/general/section-84. html • GSS-API: http: //docsun. cites. uiuc. edu/sun_docs/C/solaris_9/SUNWdev/GSS • IETF PKIX charter: http: //www. ietf. org/html. charters/pkix-charter. html • PKCS: http: //www. rsasecurity. com/rsalabs/pkcs/index. html First Latinamerican Grid Workshop, Merida (VE) – 15 -20 November 2004 - 47