Security Java ECommerce Martin Cooke 2003 This lecture





























- Slides: 55

Security Java E-Commerce © Martin Cooke, 2003

This lecture • Security requirements for e-commerce • Java language features • Java sandbox 10/17/2021 Java E-Commerce © Martin Cooke, 2003 2

Later lectures • Next: Authentication & authorisation • Cryptography – Cryptographic hash functions – Encryption/decrption: symmetric and public key systems • Applications – Message digests – digital signatures & certificates • SSL and SET • Java support for cryptography 10/17/2021 Java E-Commerce © Martin Cooke, 2003 3

Security requirements for ecommerce Java E-Commerce © Martin Cooke, 2003

Why security is a hot topic • Security threats have increased out of all recognition in the last 10 years, with virtually no aspect of life left untouched, leaving opportunities to snoop, sneal, clog up, impersonate, modify, delete, or simply make mistakes and wreak havoc …. – Financial transactions eg credit card details – Sensitive information eg exam papers – Downloaded programs, including applets 10/17/2021 Java E-Commerce © Martin Cooke, 2003 5

Aspects not covered here • • • Nature of threats Tools for attacks Firewalls Virtual private networks (VPNs) Auditing for post-mortems See Ince (2001), ch 11 10/17/2021 Java E-Commerce © Martin Cooke, 2003 6

The purpose of security • Security is not used simply to protect against direct threats … • … but is essential in establishing trust in transactions between unseen parties Security & trust are probably the most significant barriers to e-commerce 10/17/2021 Java E-Commerce © Martin Cooke, 2003 7

Four cornerstones of security & trust authorisation authentication integrity & confidentiality nonrepudiation 10/17/2021 Java E-Commerce © Martin Cooke, 2003 8

Authentication The identities of all parties involved in an operation should be verified (including code sources) 10/17/2021 authentication Java E-Commerce © Martin Cooke, 2003 9

Integrity authentication ensure information has not been tampered with 10/17/2021 integrity Java E-Commerce © Martin Cooke, 2003 10

Non-repudiation authentication cannot deny that you are the sender of the info, or that it has been received 10/17/2021 integrity & nonrepudiation Java E-Commerce © Martin Cooke, 2003 11

Confidentiality authentication integrity & confidentiality nonrepudiation 10/17/2021 Java E-Commerce © Martin Cooke, 2003 only intended recipient can make sense of message or stored information 12

Authorisation authentication Is the user or code allowed to carry out certain operations? integrity & confidentiality nonrepudiation 10/17/2021 Java E-Commerce © Martin Cooke, 2003 13

Security tradeoffs • With unlimited resources, most forms of security can be broken • Cost of breaking should outweigh reward • Have to consider end-to-end security • only as secure as weakest part – Eg: encryption with private key is all very well, but weakness is often storage of private key • Aim for simplicity – Don’t want to frighten away legitimate users – Easier to analyse and maintain 10/17/2021 Java E-Commerce © Martin Cooke, 2003 14

Common web scenarios and their security aspects Java E-Commerce © Martin Cooke, 2003

Scenario 1: online banking • Authentication: is this a valid user? • Authorisation: does this user have permission to access account information? • Confidentiality: is account information secure from attack? • … but must still be easy to use 10/17/2021 Java E-Commerce © Martin Cooke, 2003 16

Scenario 2: Downloading code • Authentication: does the code come from a trusted source? • Integrity: has the code been tampered with before or during downloading? • Authorisation: does the code have permission to carry out certain operations? 10/17/2021 Java E-Commerce © Martin Cooke, 2003 17

Scenario 3: online credit card transactions • Authentication: does the credit card belong to the customer? Is the merchant valid? Is the merchant bank valid? • Integrity: have any details been altered en route? • Non-repudiation: can any of the parties deny that any aspects of the transaction took place? • Confidentiality: should the merchant have access to credit card details? Should the bank have access to purchase details? 10/17/2021 Java E-Commerce © Martin Cooke, 2003 18

But isn’t Java secure? Java E-Commerce © Martin Cooke, 2003

Java 2 security features • Configurable security policy to protect you from Java programs (this lecture) • Authentication and authorisation framework to protect you against end users (next lecture) • Integrity checks for data • Digital signatures • Digital certificates • Key management • Encryption/decryption (from 1. 4) 10/17/2021 Java E-Commerce © Martin Cooke, 2003 20

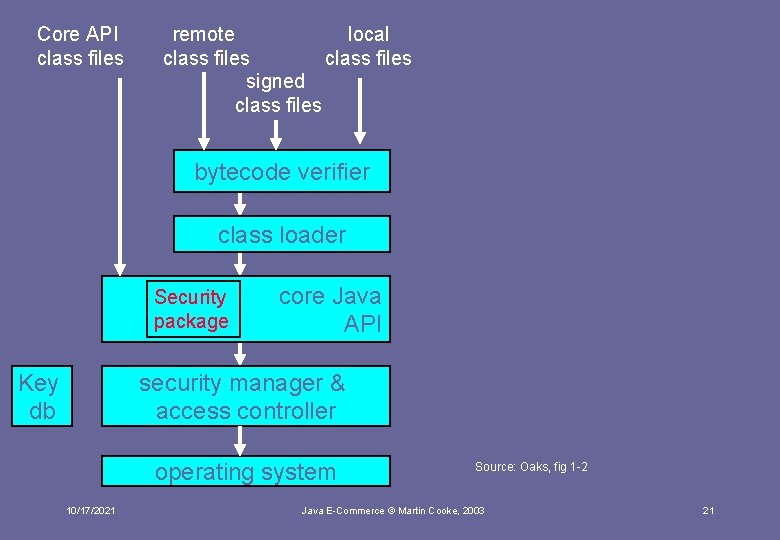
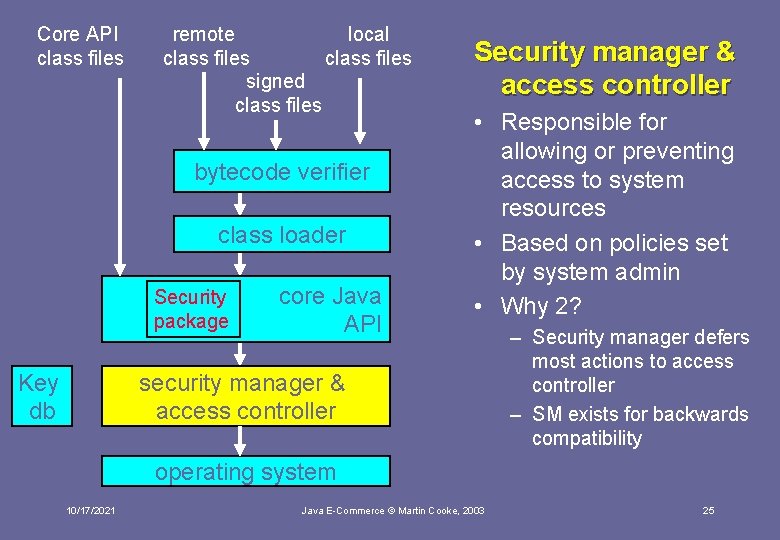
Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db core Java API security manager & access controller operating system 10/17/2021 Source: Oaks, fig 1 -2 Java E-Commerce © Martin Cooke, 2003 21

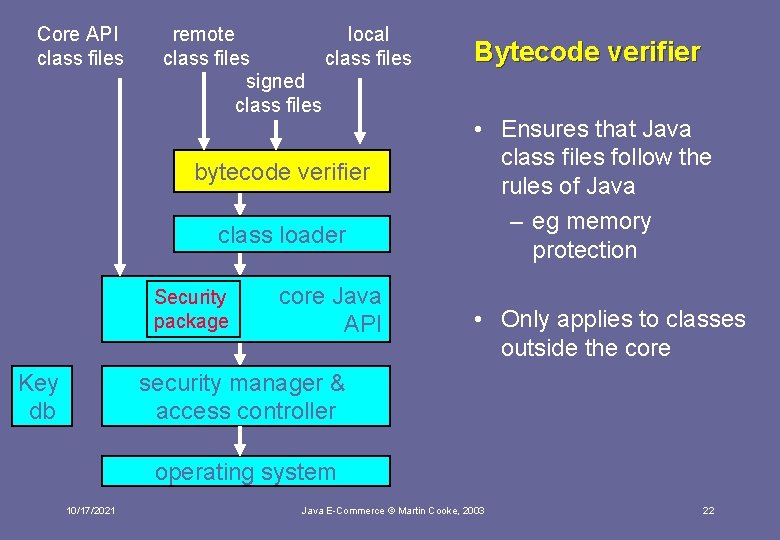
Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db core Java API Bytecode verifier • Ensures that Java class files follow the rules of Java – eg memory protection • Only applies to classes outside the core security manager & access controller operating system 10/17/2021 Java E-Commerce © Martin Cooke, 2003 22

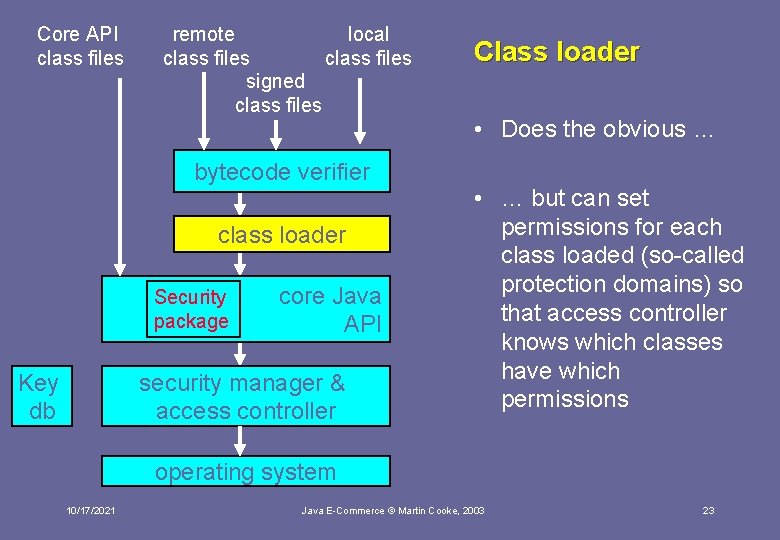
Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db core Java API security manager & access controller Class loader • Does the obvious … • … but can set permissions for each class loaded (so-called protection domains) so that access controller knows which classes have which permissions operating system 10/17/2021 Java E-Commerce © Martin Cooke, 2003 23

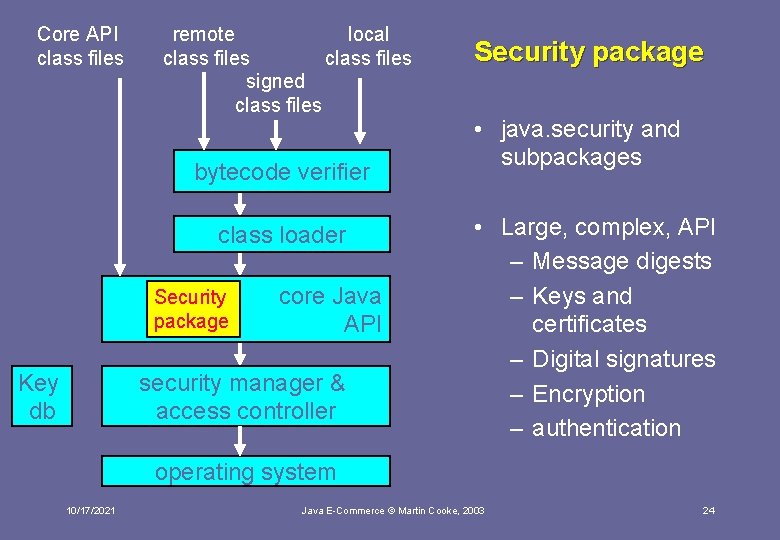
Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db core Java API security manager & access controller Security package • java. security and subpackages • Large, complex, API – Message digests – Keys and certificates – Digital signatures – Encryption – authentication operating system 10/17/2021 Java E-Commerce © Martin Cooke, 2003 24

Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db core Java API Security manager & access controller • Responsible for allowing or preventing access to system resources • Based on policies set by system admin • Why 2? security manager & access controller – Security manager defers most actions to access controller – SM exists for backwards compatibility operating system 10/17/2021 Java E-Commerce © Martin Cooke, 2003 25

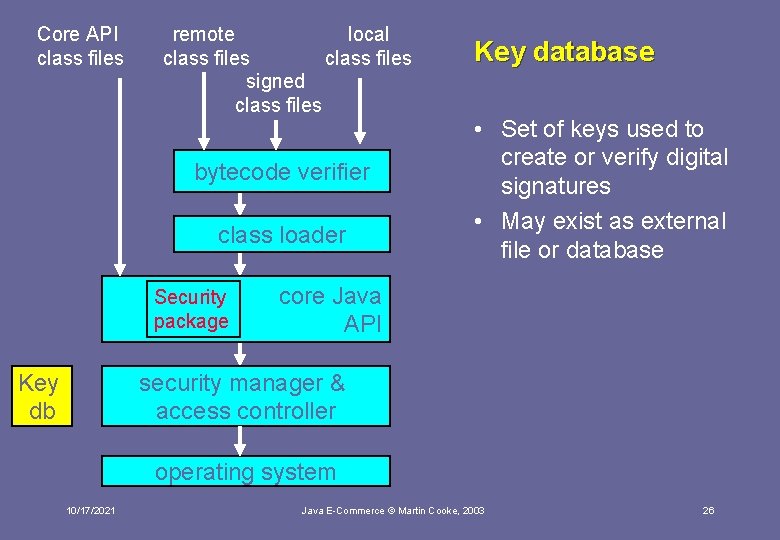
Core API class files remote local class files signed class files bytecode verifier class loader Security package Key db Key database • Set of keys used to create or verify digital signatures • May exist as external file or database core Java API security manager & access controller operating system 10/17/2021 Java E-Commerce © Martin Cooke, 2003 26

Security features in the language • Every object has an access level – Private, package, protected, public • Cannot access arbitrary memory locations • Immutable final objects • Variables must be initialised before use • Array-bound checking • No arbitrary object casting 10/17/2021 Java E-Commerce © Martin Cooke, 2003 27

Enforcement 1: compiler • Every object has an access level – Private, package, protected, public • Cannot access arbitrary memory locations • Immutable final objects • Variables must be initialised before use • Array-bound checking • No arbitrary object casting 10/17/2021 Java E-Commerce © Martin Cooke, 2003 28

Enforcement 2: byte-code verifier • Every object has an access level – Private, package, protected, public • Cannot access arbitrary memory locations • Immutable final objects • Variables must be initialised before use • Array-bound checking • No arbitrary object casting • Necessary since it is possible to compile classes which, together, represent non-conforming Java code • Internal part of JVM • Proves that a series of bytecodes is a legal sequence of Java instructions • • • Correct format for class No subclassing of finals Single superclass for each class No illegal primitive data conversion No illegal casting (*) No operand stack overflow/underflow (*) cannot test fully until runtime 10/17/2021 Java E-Commerce © Martin Cooke, 2003 29

Enforcement 3: runtime system • Every object has an access level – Private, package, protected, public • Cannot access arbitrary memory locations • Immutable final objects • Variables must be initialised before use • Array-bound checking • No arbitrary object casting 10/17/2021 Java E-Commerce © Martin Cooke, 2003 30

The Java Sandbox Java E-Commerce © Martin Cooke, 2003

The sandbox • Originally, applied only to applets and was very ‘tight’ • Since 1. 1, offered fine-grained security authorisation to code • Since 1. 2, can be applied to applications as well as applets (only difference is that it is default for applets) • Implemented by security manager 10/17/2021 Java E-Commerce © Martin Cooke, 2003 32

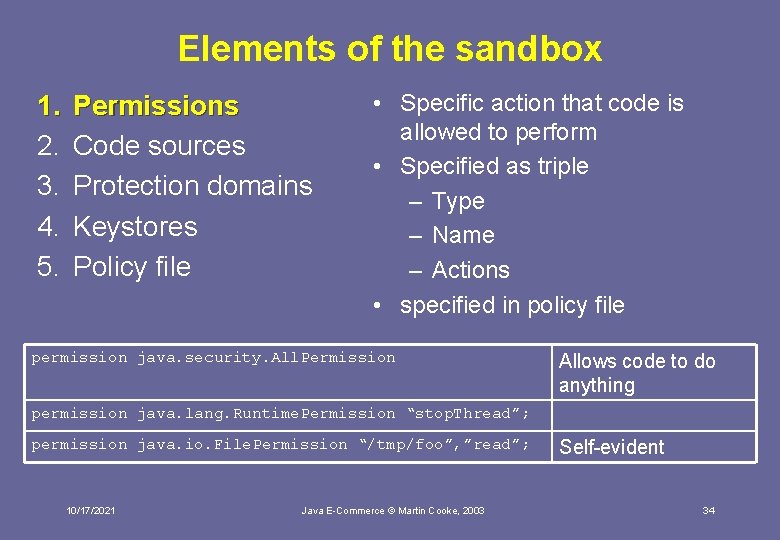
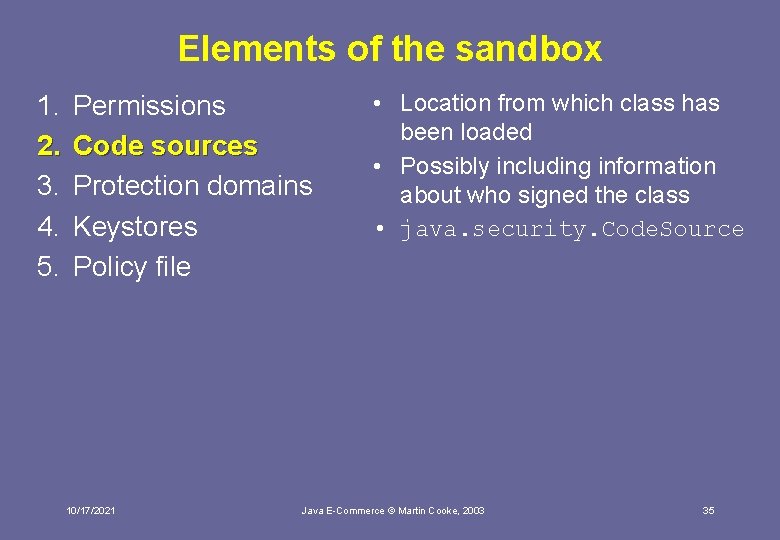
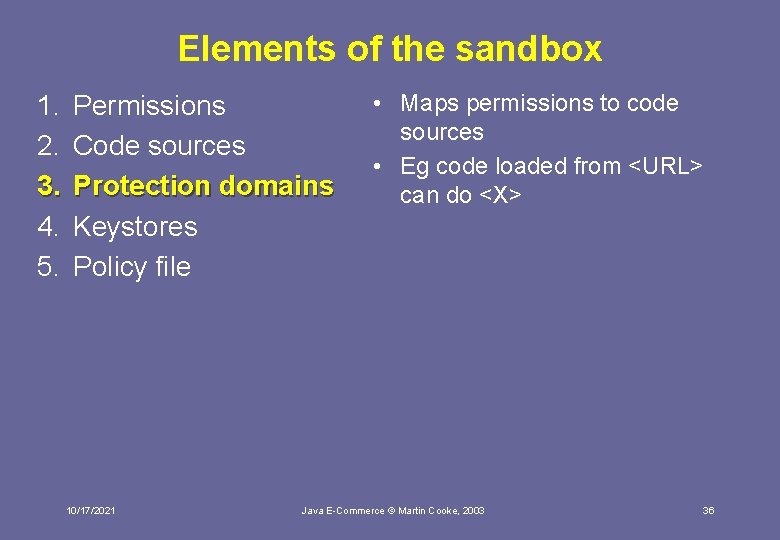
Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file 10/17/2021 Java E-Commerce © Martin Cooke, 2003 33

Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file • Specific action that code is allowed to perform • Specified as triple – Type – Name – Actions • specified in policy file permission java. security. All. Permission Allows code to do anything permission java. lang. Runtime. Permission “stop. Thread”; permission java. io. File. Permission “/tmp/foo”, ”read”; 10/17/2021 Java E-Commerce © Martin Cooke, 2003 Self-evident 34

Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file 10/17/2021 • Location from which class has been loaded • Possibly including information about who signed the class • java. security. Code. Source Java E-Commerce © Martin Cooke, 2003 35

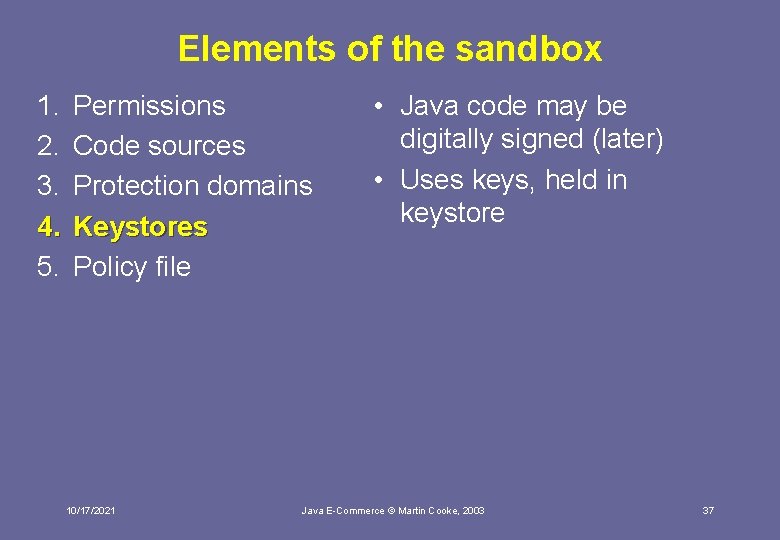
Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file 10/17/2021 • Maps permissions to code sources • Eg code loaded from <URL> can do <X> Java E-Commerce © Martin Cooke, 2003 36

Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file 10/17/2021 • Java code may be digitally signed (later) • Uses keys, held in keystore Java E-Commerce © Martin Cooke, 2003 37

Elements of the sandbox 1. 2. 3. 4. 5. Permissions Code sources Protection domains Keystores Policy file 10/17/2021 • Used to list permissions, identify keystore location, specify code sources and protection domains • Global policy file: lib/security/java. policy • Local policy file: . java. policy in home dir • Policies based on union of the two Java E-Commerce © Martin Cooke, 2003 38

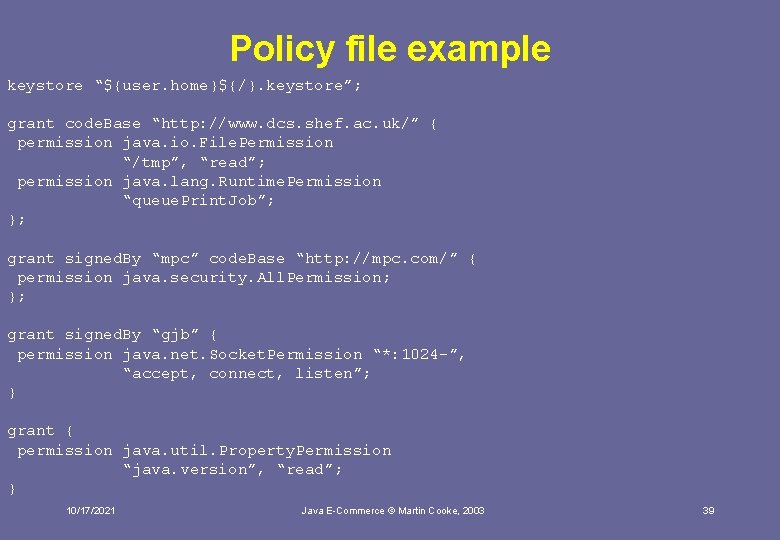
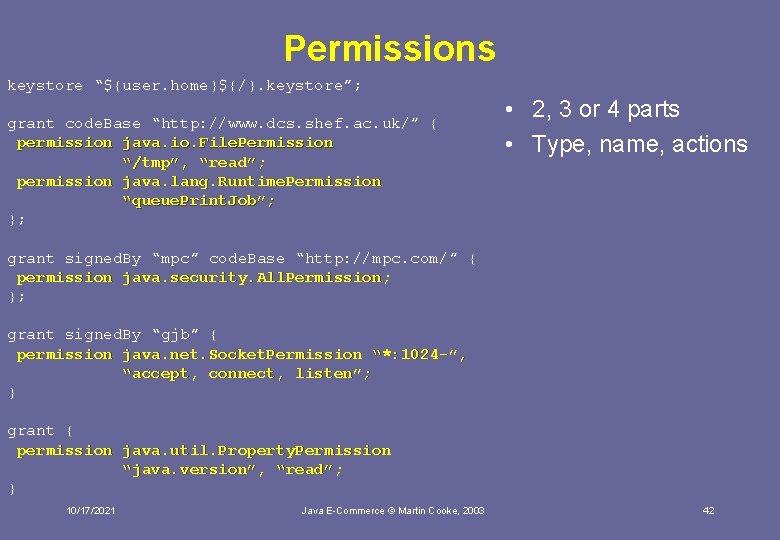
Policy file example keystore “${user. home}${/}. keystore”; grant code. Base “http: //www. dcs. shef. ac. uk/” { permission java. io. File. Permission “/tmp”, “read”; permission java. lang. Runtime. Permission “queue. Print. Job”; }; grant signed. By “mpc” code. Base “http: //mpc. com/” { permission java. security. All. Permission; }; grant signed. By “gjb” { permission java. net. Socket. Permission “*: 1024 -”, “accept, connect, listen”; } grant { permission java. util. Property. Permission “java. version”, “read”; } 10/17/2021 Java E-Commerce © Martin Cooke, 2003 39

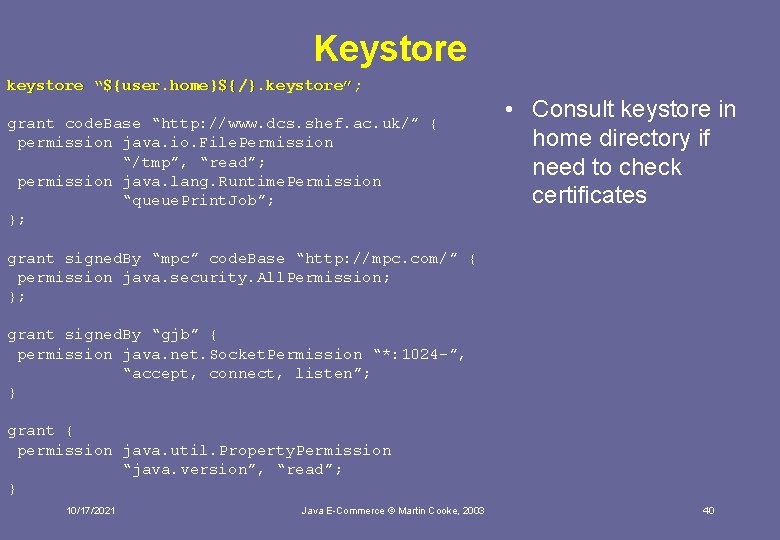
Keystore keystore “${user. home}${/}. keystore”; grant code. Base “http: //www. dcs. shef. ac. uk/” { permission java. io. File. Permission “/tmp”, “read”; permission java. lang. Runtime. Permission “queue. Print. Job”; }; • Consult keystore in home directory if need to check certificates grant signed. By “mpc” code. Base “http: //mpc. com/” { permission java. security. All. Permission; }; grant signed. By “gjb” { permission java. net. Socket. Permission “*: 1024 -”, “accept, connect, listen”; } grant { permission java. util. Property. Permission “java. version”, “read”; } 10/17/2021 Java E-Commerce © Martin Cooke, 2003 40

Codebases keystore “${user. home}${/}. keystore”; grant code. Base “http: //www. dcs. shef. ac. uk/” { permission java. io. File. Permission “/tmp”, “read”; permission java. lang. Runtime. Permission “queue. Print. Job”; }; • combination of signed. By and code. Base elements grant signed. By “mpc” code. Base “http: //mpc. com/” { permission java. security. All. Permission; }; grant signed. By “gjb” { permission java. net. Socket. Permission “*: 1024 -”, “accept, connect, listen”; } grant { permission java. util. Property. Permission “java. version”, “read”; } 10/17/2021 Java E-Commerce © Martin Cooke, 2003 41

Permissions keystore “${user. home}${/}. keystore”; grant code. Base “http: //www. dcs. shef. ac. uk/” { permission java. io. File. Permission “/tmp”, “read”; permission java. lang. Runtime. Permission “queue. Print. Job”; }; • 2, 3 or 4 parts • Type, name, actions grant signed. By “mpc” code. Base “http: //mpc. com/” { permission java. security. All. Permission; }; grant signed. By “gjb” { permission java. net. Socket. Permission “*: 1024 -”, “accept, connect, listen”; } grant { permission java. util. Property. Permission “java. version”, “read”; } 10/17/2021 Java E-Commerce © Martin Cooke, 2003 42

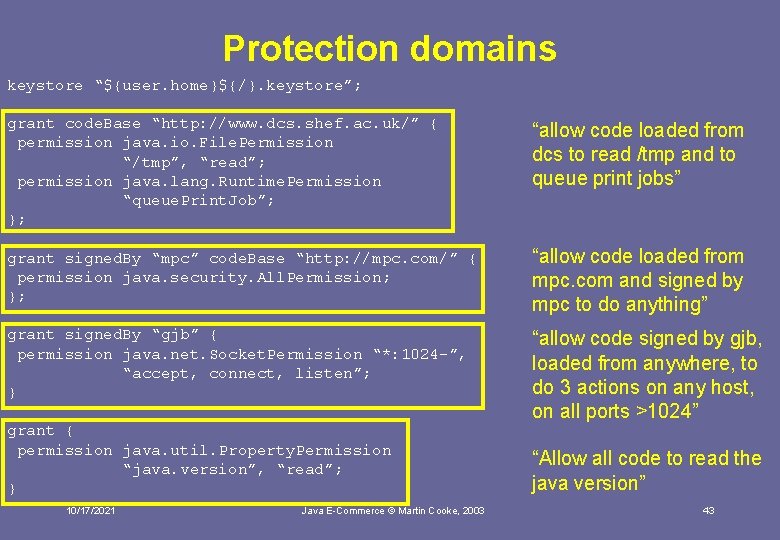
Protection domains keystore “${user. home}${/}. keystore”; grant code. Base “http: //www. dcs. shef. ac. uk/” { permission java. io. File. Permission “/tmp”, “read”; permission java. lang. Runtime. Permission “queue. Print. Job”; }; “allow code loaded from dcs to read /tmp and to queue print jobs” grant signed. By “mpc” code. Base “http: //mpc. com/” { permission java. security. All. Permission; }; “allow code loaded from mpc. com and signed by mpc to do anything” grant signed. By “gjb” { permission java. net. Socket. Permission “*: 1024 -”, “accept, connect, listen”; } “allow code signed by gjb, loaded from anywhere, to do 3 actions on any host, on all ports >1024” grant { permission java. util. Property. Permission “java. version”, “read”; } 10/17/2021 Java E-Commerce © Martin Cooke, 2003 “Allow all code to read the java version” 43

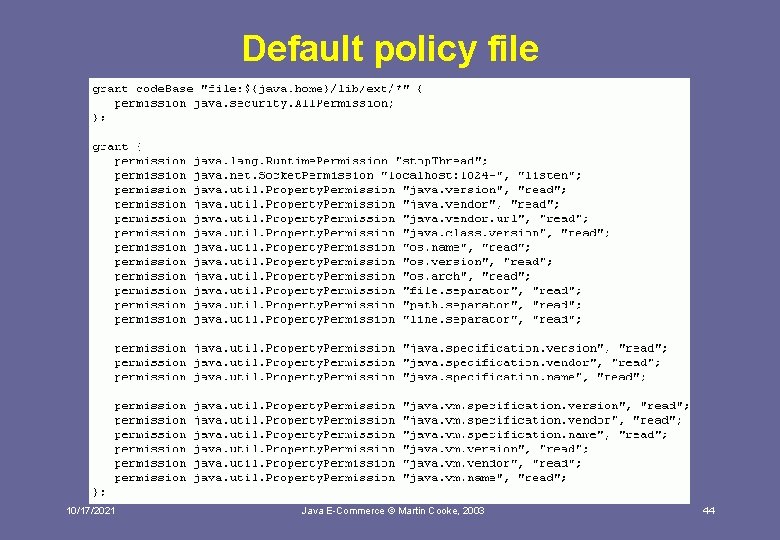
Default policy file 10/17/2021 Java E-Commerce © Martin Cooke, 2003 44

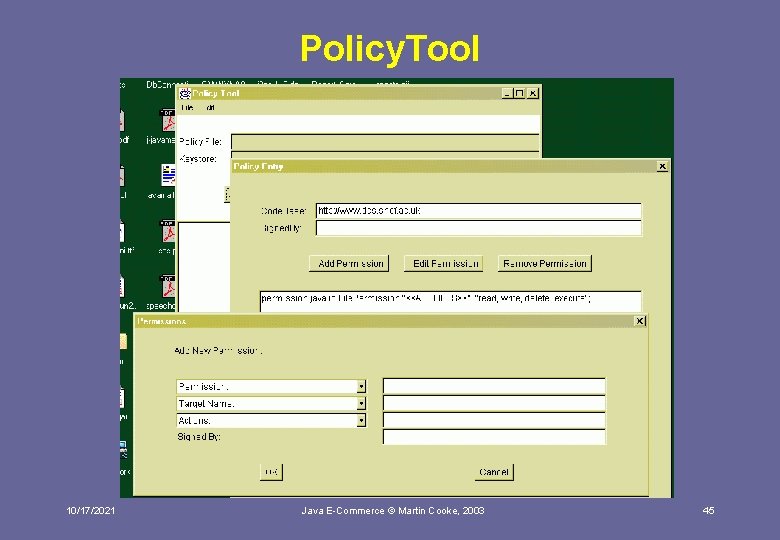
Policy. Tool 10/17/2021 Java E-Commerce © Martin Cooke, 2003 45

Launching the sandbox for applications java -Djava. security. manager <app> java -Djava. security. manager -Djava. security. policy=<URL> <app> 10/17/2021 Java E-Commerce © Martin Cooke, 2003 46

Programming perspective: The access controller • Main mechanism used by Java API to implement the sandbox • Simple to use 10/17/2021 Java E-Commerce © Martin Cooke, 2003 47

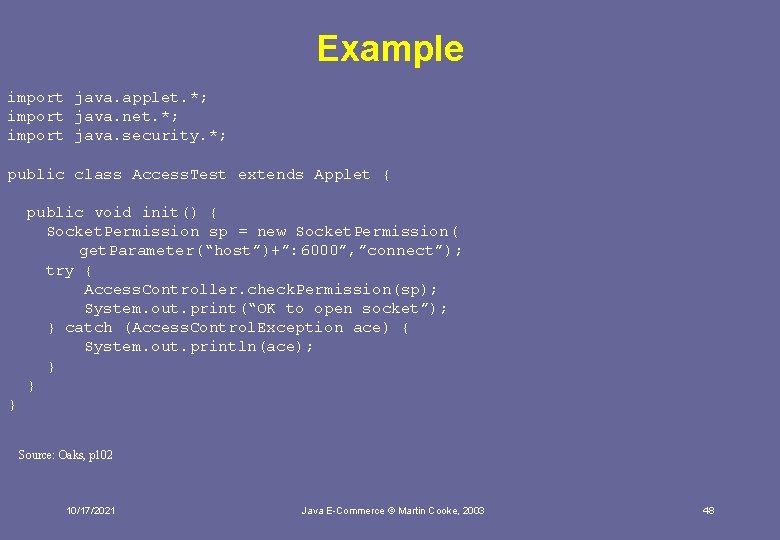
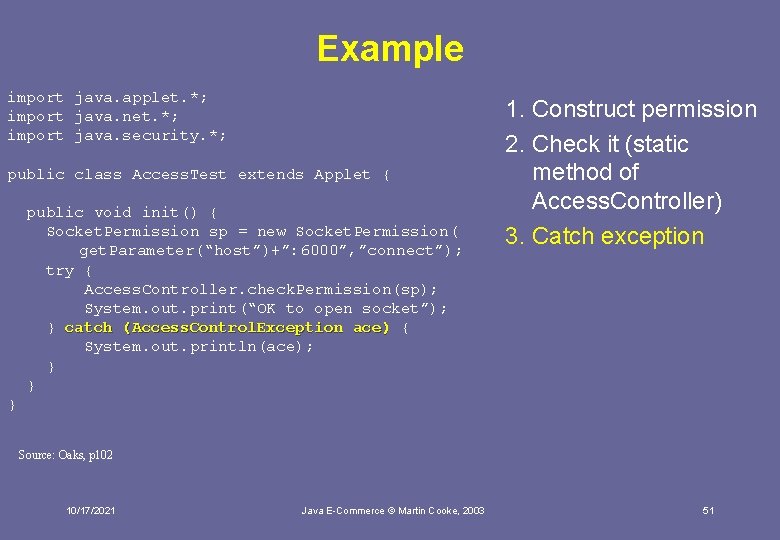
Example import java. applet. *; import java. net. *; import java. security. *; public class Access. Test extends Applet { public void init() { Socket. Permission sp = new Socket. Permission( get. Parameter(“host”)+”: 6000”, ”connect”); try { Access. Controller. check. Permission(sp); System. out. print(“OK to open socket”); } catch (Access. Control. Exception ace) { System. out. println(ace); } } } Source: Oaks, p 102 10/17/2021 Java E-Commerce © Martin Cooke, 2003 48

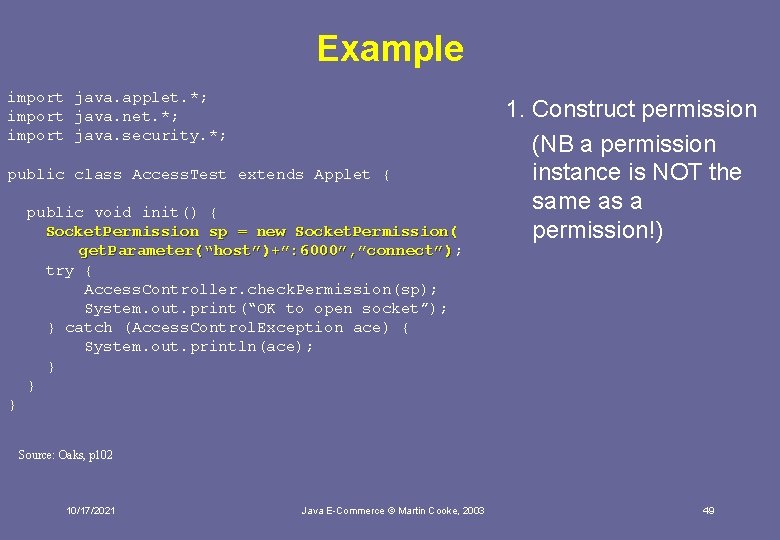
Example import java. applet. *; import java. net. *; import java. security. *; public class Access. Test extends Applet { public void init() { Socket. Permission sp = new Socket. Permission( get. Parameter(“host”)+”: 6000”, ”connect”); get. Parameter(“host”)+”: 6000”, ”connect”) try { Access. Controller. check. Permission(sp); System. out. print(“OK to open socket”); } catch (Access. Control. Exception ace) { System. out. println(ace); } } 1. Construct permission (NB a permission instance is NOT the same as a permission!) } Source: Oaks, p 102 10/17/2021 Java E-Commerce © Martin Cooke, 2003 49

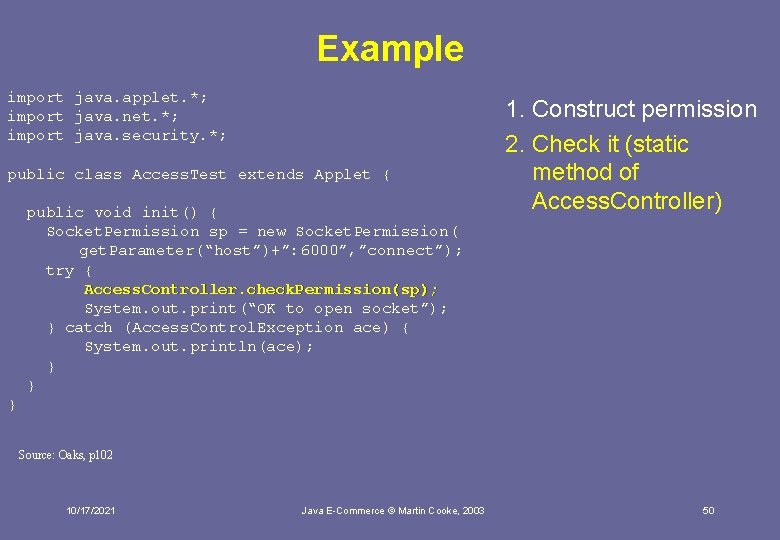
Example import java. applet. *; import java. net. *; import java. security. *; public class Access. Test extends Applet { public void init() { Socket. Permission sp = new Socket. Permission( get. Parameter(“host”)+”: 6000”, ”connect”); try { Access. Controller. check. Permission(sp); System. out. print(“OK to open socket”); } catch (Access. Control. Exception ace) { System. out. println(ace); } } 1. Construct permission 2. Check it (static method of Access. Controller) } Source: Oaks, p 102 10/17/2021 Java E-Commerce © Martin Cooke, 2003 50

Example import java. applet. *; import java. net. *; import java. security. *; public class Access. Test extends Applet { public void init() { Socket. Permission sp = new Socket. Permission( get. Parameter(“host”)+”: 6000”, ”connect”); try { Access. Controller. check. Permission(sp); System. out. print(“OK to open socket”); } catch (Access. Control. Exception ace) { System. out. println(ace); } } 1. Construct permission 2. Check it (static method of Access. Controller) 3. Catch exception } Source: Oaks, p 102 10/17/2021 Java E-Commerce © Martin Cooke, 2003 51

Constructing your own permissions • Think of this as similar to constructing own exceptions • Powerful and flexible way to implement arbitrary, applicationspecific, security policies, which can be administered from a policy file • Eg read, modify rows with particular fields from database • Extend java. security. Permission • Easier to extend java. security. Basic. Permission 10/17/2021 Java E-Commerce © Martin Cooke, 2003 52

Interim summary • The Java language contains many features which make it difficult to subvert • The sandbox concept applies to applets (always) and applications, using -Djava. security. manager • A policy file specifies which permissions can be granted to code coming from specific locations and/or specific signers • This adds up to protecting system resources from untrusted code But what about unstrusted users? 10/17/2021 Java E-Commerce © Martin Cooke, 2003 53

Summary • Authentication, authorisation, integrity and confidentiality are the cornerstones of security • Java supports security in many ways, from language features to APIs, but is only as secure as the programmer makes it 10/17/2021 Java E-Commerce © Martin Cooke, 2003 54

Resources Books • Oaks (2001) Java Security (2 nd edition) O’Reilly, 0 -596 -00157 -6 • Ince, ch 11 • Norris & West (2001) e. Business Essentials, Wiley, 0 -471 -52183 -3, chs 4 and 5 10/17/2021 Java E-Commerce © Martin Cooke, 2003 55