Security is always excessive until its not enough
















- Slides: 24

“Security is always excessive until it’s not enough. ” -- Robbie Sinclair, Head of Security, Country Energy (New South Wales, Australia)

ANTHONY TURNER Crypt. Inject https: //github. com/mzxgiant/Crypt. Inject ANTHTURN@MICROSOFT. CO M WWW. ANTHTURNER. COM

What Does it Help With? Implement cryptography in a secure manner Handle multiple security roles within documents and files Enhance existing applications with cryptography Utilize secure data storage when using other libraries

What is Crypt. Inject? A slim wrapper around developer-created classes that shifts data access calls into reading from and writing to encrypted memory Designed to be used for objects that need to leave the program’s process space and be stored/moved somewhere else Not for memory heap security

Crypt. Inject’s Three Major Goals Simplify integration of cryptography using concepts developers understand already Allow for extensibility with what algorithms and serializers can be used for encryption operations Maintain native object support to allow for usage of encryption-enabled objects outside of Crypt. Inject and user code (such as using these objects within entity models in Entity Framework or NHibernate)

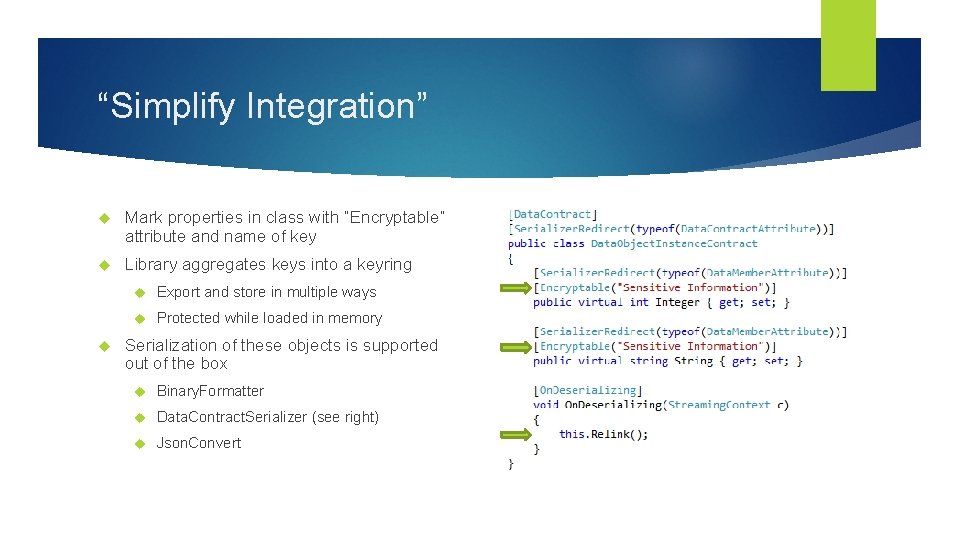
“Simplify Integration” Mark properties in class with “Encryptable” attribute and name of key Library aggregates keys into a keyring Export and store in multiple ways Protected while loaded in memory Serialization of these objects is supported out of the box Binary. Formatter Data. Contract. Serializer (see right) Json. Convert

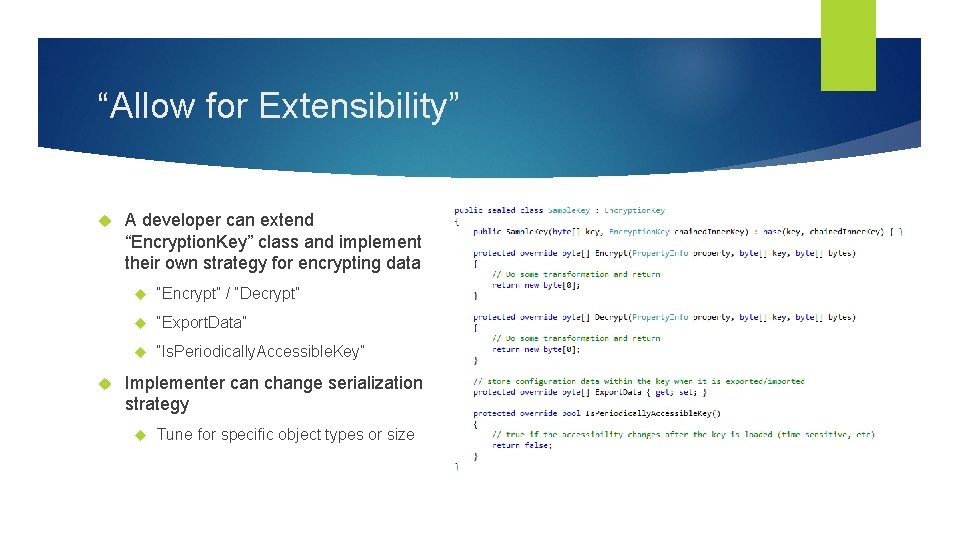
“Allow for Extensibility” A developer can extend “Encryption. Key” class and implement their own strategy for encrypting data “Encrypt” / “Decrypt” “Export. Data” “Is. Periodically. Accessible. Key” Implementer can change serialization strategy Tune for specific object types or size

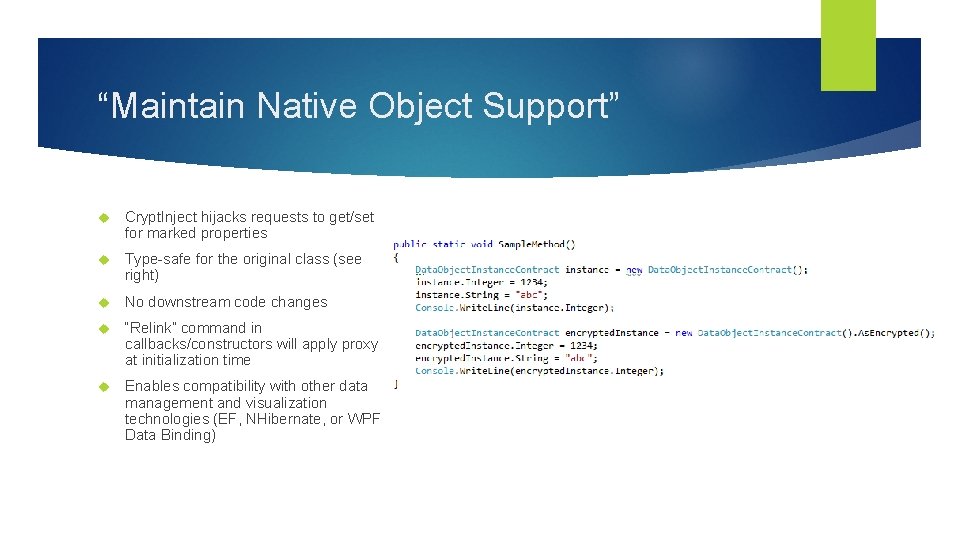
“Maintain Native Object Support” Crypt. Inject hijacks requests to get/set for marked properties Type-safe for the original class (see right) No downstream code changes “Relink” command in callbacks/constructors will apply proxy at initialization time Enables compatibility with other data management and visualization technologies (EF, NHibernate, or WPF Data Binding)

Demonstration BASIC DEMO WITH BUILT-IN SERIALIZERS

Technical Dive

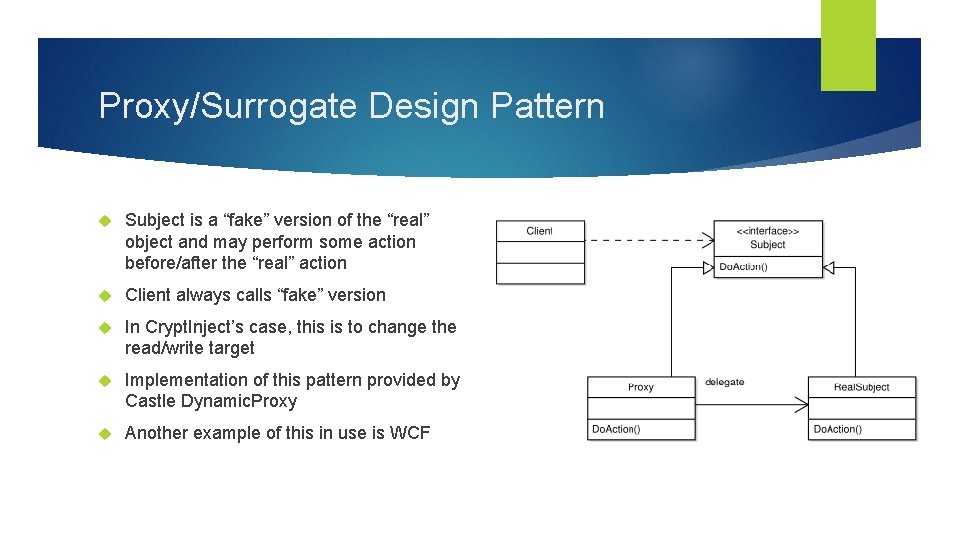
Proxy/Surrogate Design Pattern Subject is a “fake” version of the “real” object and may perform some action before/after the “real” action Client always calls “fake” version In Crypt. Inject’s case, this is to change the read/write target Implementation of this pattern provided by Castle Dynamic. Proxy Another example of this in use is WCF

Encryptable Attribute Specifies that a property should be stored encrypted Developer specifies the key by name [Encryptable(“Human Resources”)] Property must be an auto-property and marked virtual

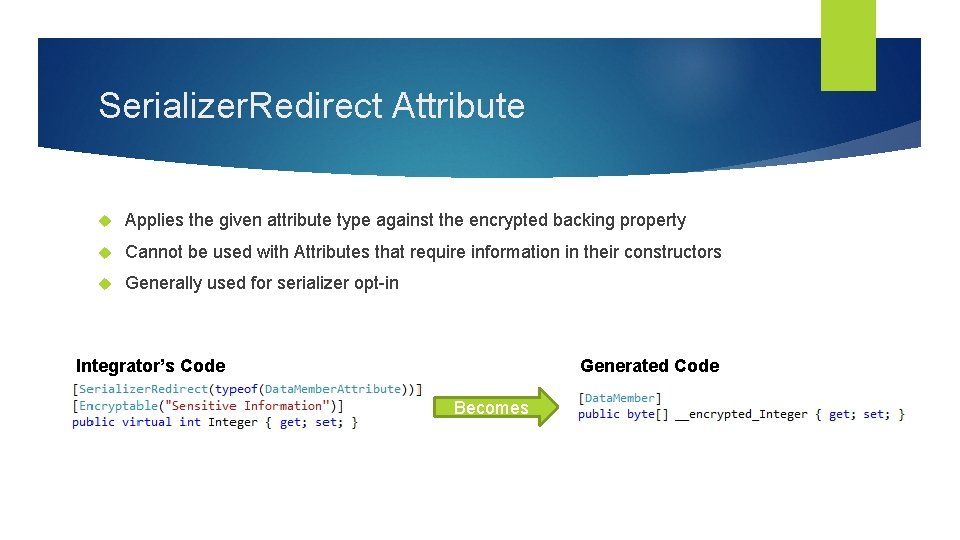
Serializer. Redirect Attribute Applies the given attribute type against the encrypted backing property Cannot be used with Attributes that require information in their constructors Generally used for serializer opt-in Integrator’s Code Generated Code Becomes

How Is The Object Set Up? When. As. Encrypted is run, a new type is cloned from the original All properties in object marked with “Encryptable” attribute have additional members generated A cache property matching the type of the original property An encrypted backing property, as a byte array Clones any attributes from corresponding Serializer. Redirect attributes Additional members are “mixed in” to cloned type with Castle Dynamic. Proxy Gets/Sets of marked properties redirected to Crypt. Inject interceptor

Demonstration ENTITY FRAMEWORK/NHIBERNATE

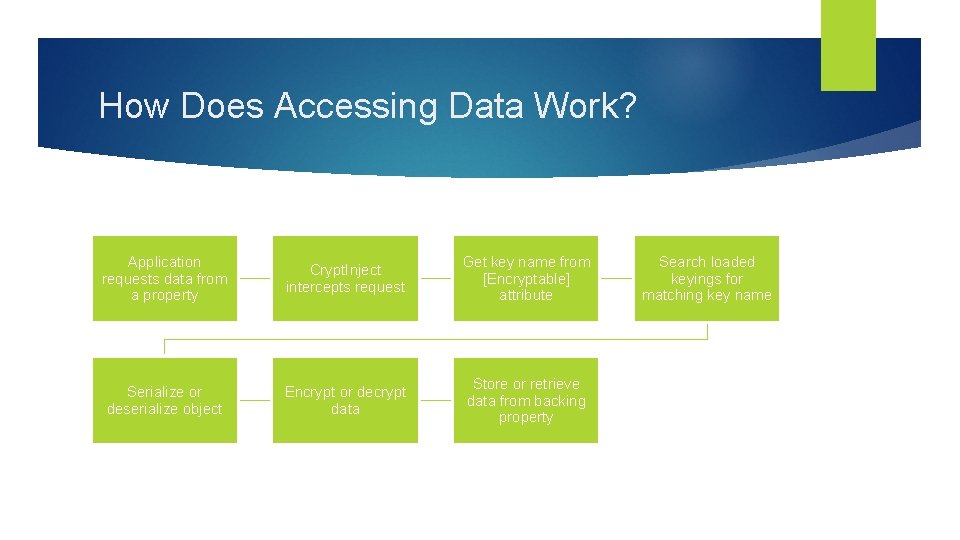
How Does Accessing Data Work? Application requests data from a property Crypt. Inject intercepts request Get key name from [Encryptable] attribute Serialize or deserialize object Encrypt or decrypt data Store or retrieve data from backing property Search loaded keyings for matching key name

WCF SERVICE/CLIENT Demonstration (COMMUNICATING CROSSPROCESS)

Cryptographic Keys Provided AES Gold standard for encryption, best CNG implementation in C# 3 DES Silver standard for encryption, succeeded by AES Meant to re-use DES implementations (which are breakable) by chaining 3 DES instances with different keys Designed for performance in hardware, C# implements in software (slower)

Data Signing Keys Provided HMAC (Hashed Message Authentication Code) Uses a cryptographic hash function (MD 5, SHA 1, etc) to verify data integrity and authentication Shared secret must be known by signer and application X 509 Signing (RSA) Uses public/private RSA keys to sign messages Certificates can be portable and installed directly into end user systems

Programmatic Keys Provided These keys are to keep honest people honest Time. Window. Key Allows the user to access the inner key data only within a given time window Virtual. Machine. Prohibited. Key Future versions will allow signing of keyrings to make these security measures somewhat more secure Allows the user to only access the inner key data if the application is not being run inside a virtualized environment Anti. Print. Screen. Key Disables some methods of screen capture for a list of application-specified windows

Demonstration WPF DATA BINDING

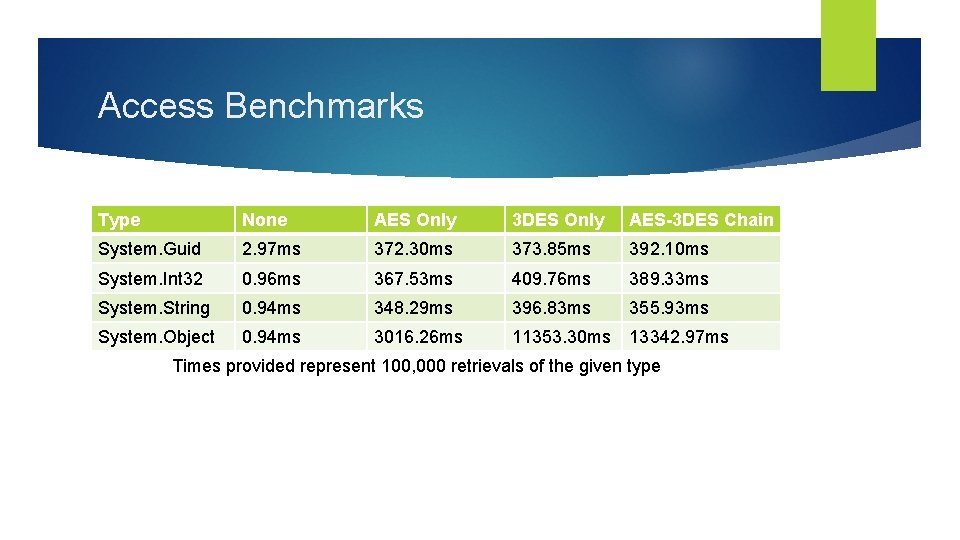
Access Benchmarks Type None AES Only 3 DES Only AES-3 DES Chain System. Guid 2. 97 ms 372. 30 ms 373. 85 ms 392. 10 ms System. Int 32 0. 96 ms 367. 53 ms 409. 76 ms 389. 33 ms System. String 0. 94 ms 348. 29 ms 396. 83 ms 355. 93 ms System. Object 0. 94 ms 3016. 26 ms 11353. 30 ms 13342. 97 ms Times provided represent 100, 000 retrievals of the given type

What’s Next? Keyring Generator Application Ability to digitally sign keyrings to make them tamper-proof Ability to expire entire keyrings (force periodic re-issue of keyrings) Ability to passphrase-protect keyrings In-Memory Protection Improvements String interning protection Forced object disposal Additional key types (Serpent, Blowfish, Twofish) Mobile support (portable keyrings) Depending on adoption and other developer participation

ANTHONY TURNER Crypt. Inject https: //github. com/mzxgiant/Crypt. Inject ANTHTURN@MICROSOFT. CO M WWW. ANTHTURNER. COM