Security in smart cards lti application smart cards














- Slides: 23

Security in smart cards lti application smart cards) Abolhassan Shamsaie 83203505 _shamsaie@yahoo. com amsaie@mehr. sharif. edu Smart cards 1

Content § § § Smart Cards History and Development Smart Cards in industry Applications of Smart Cards Smart Card Security – – – § § Physical Structure and Life Cycle Logical Structure and Access Controls Procedural Protection Attacks on Smart Card Multi application smart card – – – – Features Purpose of standard OS A java base Multi application smart card's architecture Protocol Most popular Memory Capacity Functionality A Secure channel protocol based on public key 2

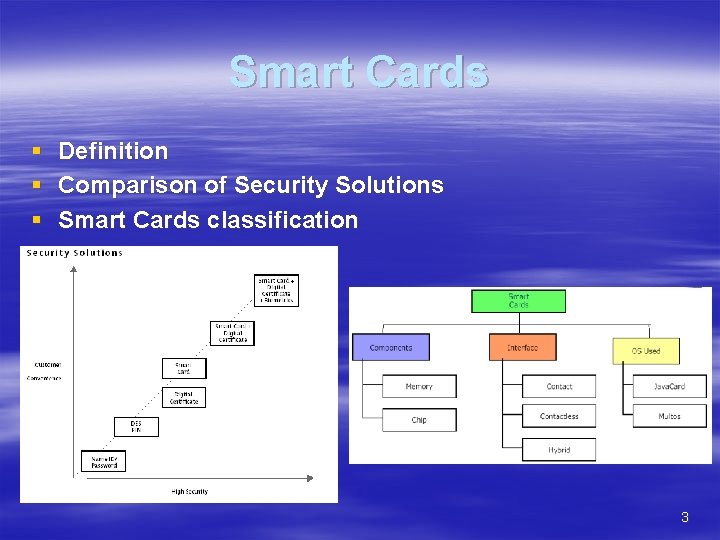
Smart Cards § Definition § Comparison of Security Solutions § Smart Cards classification 3

History and Development The Invention of the Smart Card Response from the Market Roland Moreno, in 1974. Innovatron company( Bull, Philips and Schlumberger ). public telephone payment system(1983) French standards(1984) GEC in the UK( contact less) market potential for the application security and user friendliness Development of the Technology highest performance smart card at the lowest cost As silicon technology develops so will the power of the smart card Laser cards 4

Smart Cards in industry § § § § Communications – Pay TV – Pre-paid Telephone Card Banking – Internet Commerce authentication device – Stored Value Pre-paid Payment Card Retail – Frequent shopper, frequent flyer, special events, etc – Loyalty and E purse applications. Health – Patient Identification Card – Prescription Card with drug dosage information Government – Social Security and ID – Immigration Access control – Physical access control to buildings – Logical access to computing systems and networks Transport – Cards for ticketing, – Driver's license containing biometric data 5

Applications of Smart Cards – – – – – Access Control System Time and attendance System Vehicle Identification Container tracking Tool or equipment ID Customer or loyalty cards Fare collection using 'Smart Label' tags Gas cylinder tracking Harsh/difficult environment usage Hazardous materials handling or id Inventory control( Raw materials or finished goods) Manufacturing processes Product identification PAY TV Cards Animal Tracking Cards Bank Pass Book Debit Cards, ATM Cards – – – – – Driving License Registration Certificate (RC Book) Health Cards Payment Collection Cards Vending Applications Service/Maintenance Card Royalty Cards Cash Cards - Stored Value Cards E-Purse Security Cards National ID Cards Railway Monthly Season Tickets Data Logging Cards Memory Cards Campus cards Airline IATA Cards Employee ID Cards Credit Cards 6

Smart Card Security § § § Physical Structure and Life Cycle Logical Structure and Access Controls Procedural Protection 7

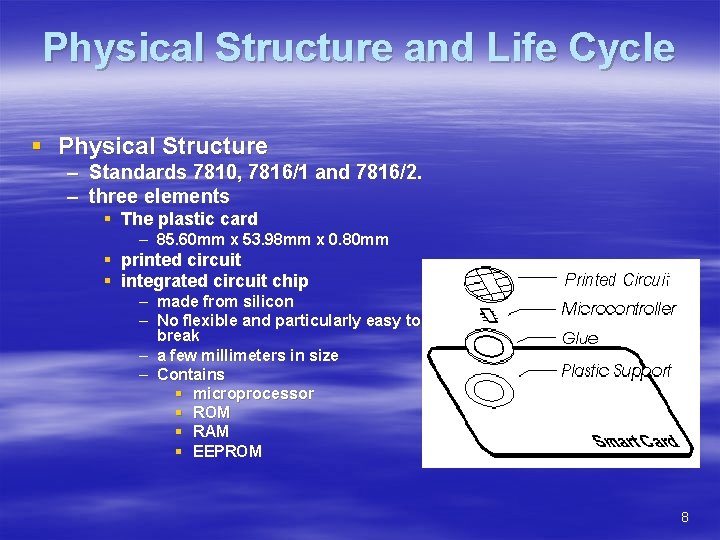
Physical Structure and Life Cycle § Physical Structure – Standards 7810, 7816/1 and 7816/2. – three elements § The plastic card – 85. 60 mm x 53. 98 mm x 0. 80 mm § printed circuit § integrated circuit chip – made from silicon – No flexible and particularly easy to break – a few millimeters in size – Contains § microprocessor § ROM § RAM § EEPROM 8

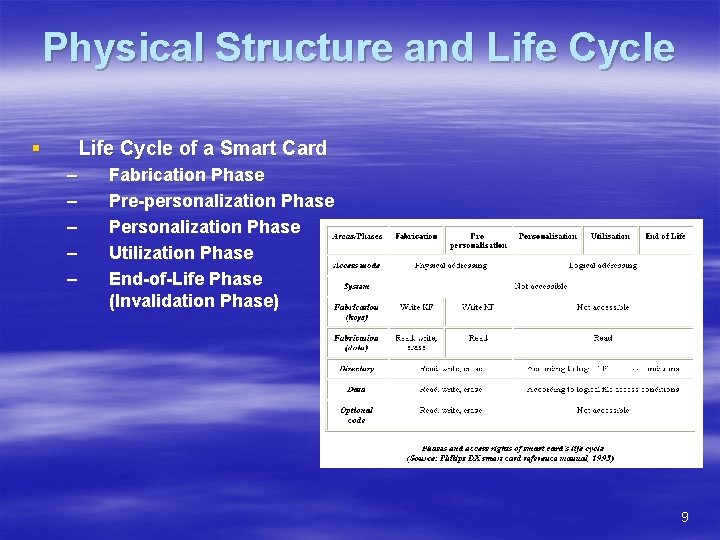
Physical Structure and Life Cycle § Life Cycle of a Smart Card – – – Fabrication Phase Pre-personalization Phase Personalization Phase Utilization Phase End-of-Life Phase (Invalidation Phase) 9

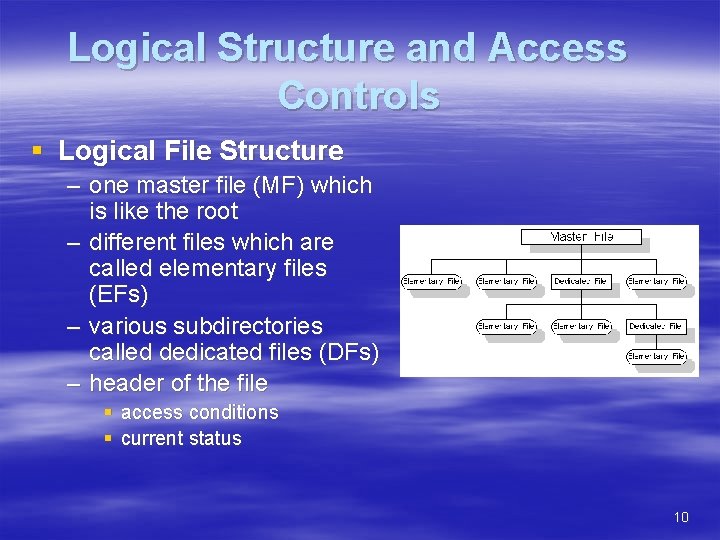
Logical Structure and Access Controls § Logical File Structure – one master file (MF) which is like the root – different files which are called elementary files (EFs) – various subdirectories called dedicated files (DFs) – header of the file § access conditions § current status 10

Logical Structure and Access Controls § Access Control – Levels of Access Conditions § § § – – Always (ALW) Card holder verification 1 (CHV 1) Card holder verification 2 (CHV 2) Administrative (ADM) Never (NEV) PIN Presentations PIN Management (three states ) § § § PIN has been presented PIN has not been presented or was presented incorrectly PIN is blocked 11

Procedural Protection & Attacks on Smart Card § Procedural Protection – – – verifications mutual authentication trusted applications § Attacks on Smart Card – Logical Attacks § unusual voltages § Temperatures – Physical Attacks § § Direct attack (nitric acid [>98% HNO 3] and acetone ) erasing the security lock bit by focusing UV light on the EPROM probing the operation of the circuit by using micro probing needles laser cutter microscopes to explore the chip 12

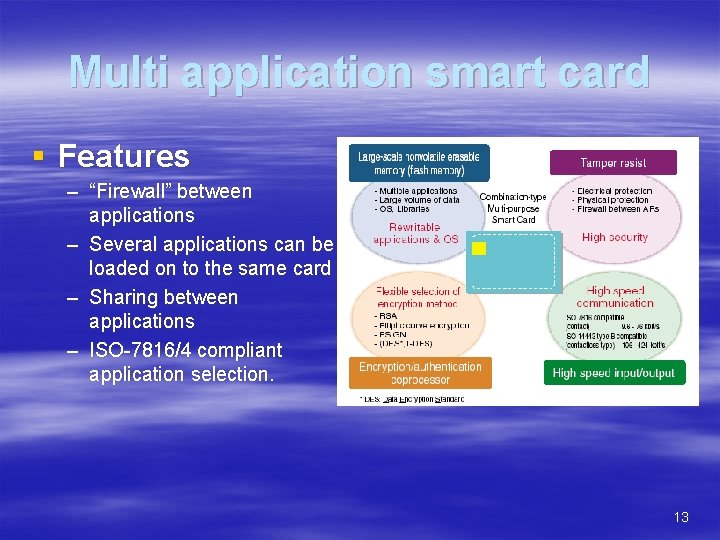
Multi application smart card § Features – “Firewall” between applications – Several applications can be loaded on to the same card – Sharing between applications – ISO-7816/4 compliant application selection. 13

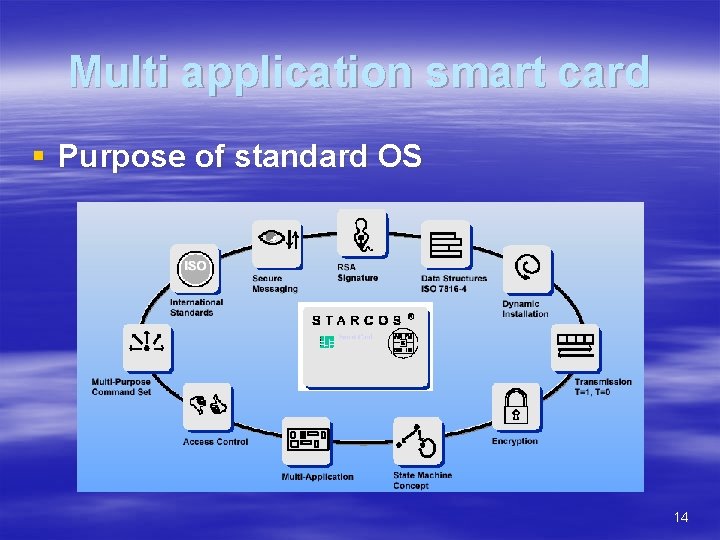
Multi application smart card § Purpose of standard OS 14

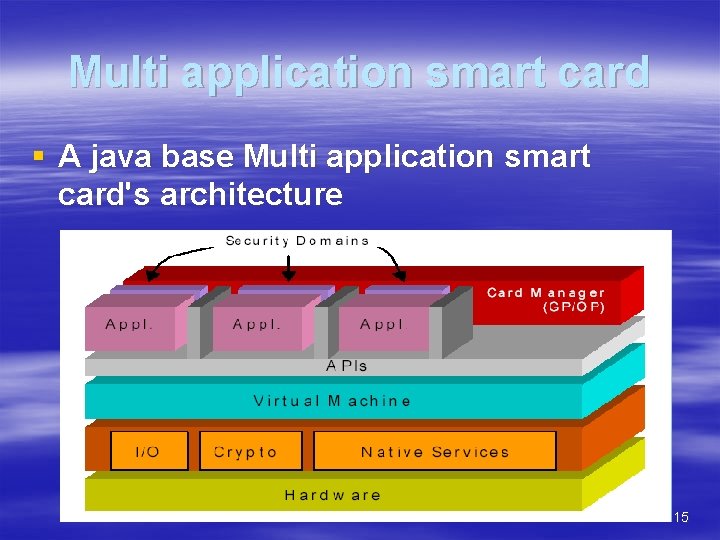
Multi application smart card § A java base Multi application smart card's architecture 15

Multi application smart card § Protocol – T=0: Byte transfer. Developed by the French – T=1: Block transfer. Developed by the Germans – USB: Based on existing USB v. 1. 1 16

Multi application smart card § Most popular Memory Capacity – – 16 KB 32 KB (most popular) 64 KB 128 KB § Functionality – – RSA 1024/2048 bit algorithms Triple-DES, SHA-1 On-card key-pair generation On-card Biometrics matching engine 17

A Secure channel protocol for multi application smart card based on public key § Phases – – – Secure Channel Initiation Secure Channel Operation Secure Channel Termination § Requirement to fulfill – – – Cheap to operate. Fast Efficient Flexible Secure 18

A Secure channel protocol for multi application smart card based on public key § Operational Characteristics – – – – C represents the smart card H is a host defined as an off-card entity Each card has a Diffie-Hellman key agreement key pair The host (H) has an RSA public encryption key The card and the host share a symmetric cryptosystem and a key generation function (e. g. a one -way function) f 1 (Z). The card is capable of generating random numbers. Each card (e. g. through a security domain) has a trusted copy of its Owner’s (e. g. certification authority, issuer or application provider) public certification key 19

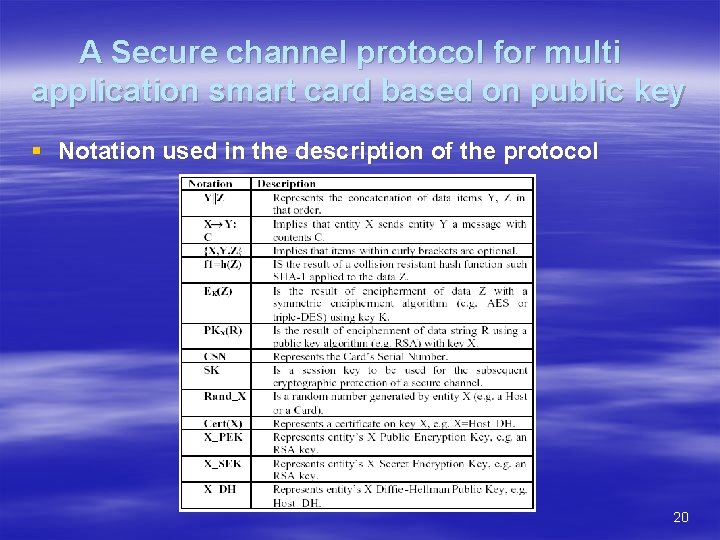
A Secure channel protocol for multi application smart card based on public key § Notation used in the description of the protocol 20

A Secure channel protocol for multi application smart card based on public key § The Protocol – H C: Cert (Host_DH) || Rand_H || {Host_ID ||Request_Cert (Card_DH) || Request_Cert (Card_PEK) ||Cert (Host_PEK)} – C H EK (Rand_H || Rand_C) {PKHost. PEK ((Cert (Card_DH) || CSN) || Rand_H)} – H C EK (Rand_C, {SK}, Rand_HB ) – C H ESK (Rand_HB, {optional parameters}) 21

References § CHAN, Siu-cheung, An Overview of Smart Card Security , Internet WWW page at URL: http: //home. hkstar. com/~alanchan/papers/smart. Card. Security § Andrew J Clark(1990), SMART CARDS, Principal Consultant Secure Systems Group Logica Aerospace & Defence Limited § Cyber. Ads Studio(2003), Smart Cards § Konstantinos Markantonakis, A SECURE CHANNEL PROTOCOL FOR MULTIAPPLICATION SMART CARDS BASED ON PUBLIC KEY CRYPTOGRAPHY, Keith Mayes Information Security Group Smart Card Centre, Royal Holloway, University of London, Egham, Surrey, TW 20 0 EX, United Kingdom § Won J. Jun (2003), Smart Card Technology Capabilities, Giesecke & Devrient 22

Questions 23