Security in internetwork PRAVIN SHETTY Security in layered























- Slides: 55

Security in (inter)network PRAVIN SHETTY.

Security in layered IP Security at the IP layer is related to the layer’s function of end-to-end datagram delivery. The security weakness are: Network snooping Message replay Message alteration Message delay and denial Authentication issues Routing attacks 2

Network Snooping Attacker observes network traffic without disturbing the transmission (passive) – commonly known as snooping or sniffing. Commonly snooped are user passwords. Sniffing software works by placing a system’s network interface into promiscuous mode. Systems like Unix require superuser or system -level privileges to access the network promiscuously. 3

Message Relaying the message to another host and it accepts as if it is trusted. Example: transfer of password files in a networked unix systems. 4

Message alteration Message means the payload of the IP datagram, the router performs routine modifications to the IP datagram header, and sometimes fragments a datagram into several smaller ones (when the length exceeds a limit allowed by the underlying data link layer). No need to suspect message alteration, but techniques such as check sum are not sufficient. 5

Message Delay and Denial By gaining authorised control of a router or routing host, then modifying executable code or routing and screening rules used by the code. need to apply proper authentication and access mechanisms to the routing systems. By overwhelming a routing device, or one of the communication end systems, with an inordinate amount of network traffic. easy to detect but difficult to prevent! 6

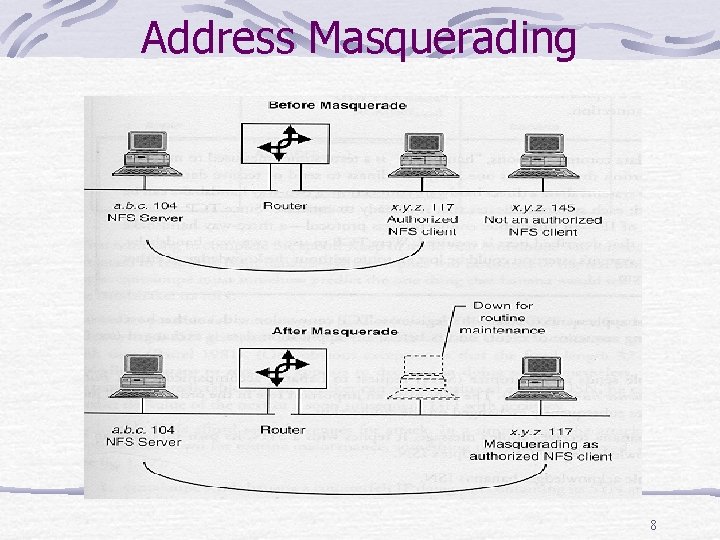
Authentication issues Authentication at the IP layer is concerned with the identify of computer systems. IP address are software configurable and the mere possession (or fraudulent use) of one enables communication with other systems. Two such techniques to do this are address masquerading address spoofing 7

Address Masquerading 8

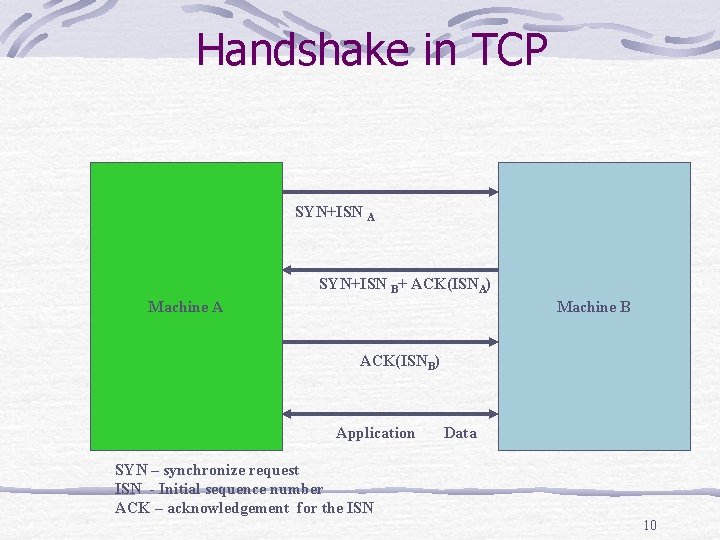
Address Spoofing Also known as TCP sequence number attack. First we need to understand how the threeway TCP handshake protocol works. handshake means- an assertion that indicates one party’s readiness to send or receive data. When two systems share a hardware connection, twoway handshake is enough. Since TCP rides on IP – an unreliable, connectionless protocol – a three-way handshake is required. 9

Handshake in TCP SYN+ISN A SYN+ISN B+ ACK(ISNA) Machine A Machine B ACK(ISNB) Application Data SYN – synchronize request ISN - Initial sequence number ACK – acknowledgement for the ISN 10

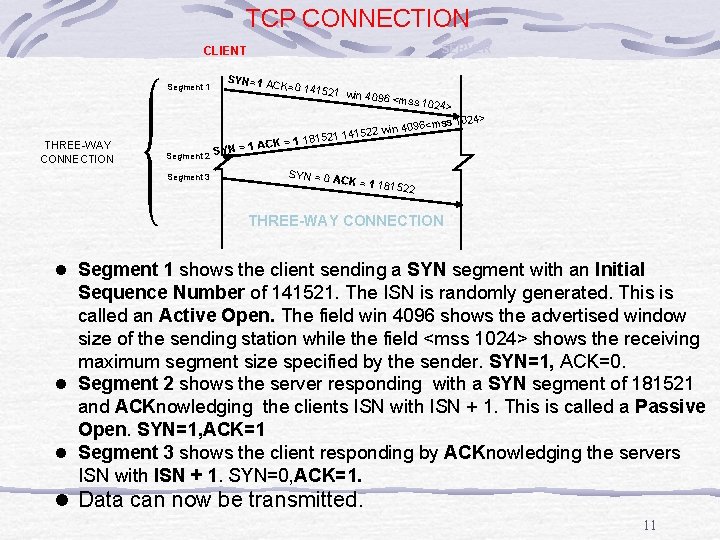
TCP CONNECTION SERVER CLIENT Segment 1 THREE-WAY CONNECTION SYN=1 A CK=0 141 15 CK = 1 18 YN = 1 A Segment 2 S Segment 3 521 win 4 096 <mss 102 4> 024> 96<mss 1 2 win 40 21 14152 SYN = 0 A CK = 1 18 1522 THREE-WAY CONNECTION l Segment 1 shows the client sending a SYN segment with an Initial Sequence Number of 141521. The ISN is randomly generated. This is called an Active Open. The field win 4096 shows the advertised window size of the sending station while the field <mss 1024> shows the receiving maximum segment size specified by the sender. SYN=1, ACK=0. l Segment 2 shows the server responding with a SYN segment of 181521 and ACKnowledging the clients ISN with ISN + 1. This is called a Passive Open. SYN=1, ACK=1 l Segment 3 shows the client responding by ACKnowledging the servers ISN with ISN + 1. SYN=0, ACK=1. l Data can now be transmitted. 11

How to get the ISN? ISN is a 32 bit clock that increases systematically with time. If the clock increment is predictable and an attacker can see the value of any one ISN, he can probably predict the value of the next or a soon subsequent ISN with accuracy. 12

Predictable ISN can lead to After knowing the ISN, wait for A to go down (say for maintenance) which is easy to detect (say by ping), then C sends B a counterfeit IP datagram containing its SYN and ISN; this B receives and believes to have originated from A. B replies with a SYN, its own ISN and an acknowledgement of C’s ISN (This reply is routed inconsequentially to A who is still unavailable to receive it. ) C mean while predicts and acknowledges B’s ISN. It follows with an rsh command that coxes B to give the attacker easier access from his true location. C successfully opened a TCP connection and executed a command on B, without ever having received a single byte in return from B. It simply acted as if it had, enabled by B’s predictable ISN. 13

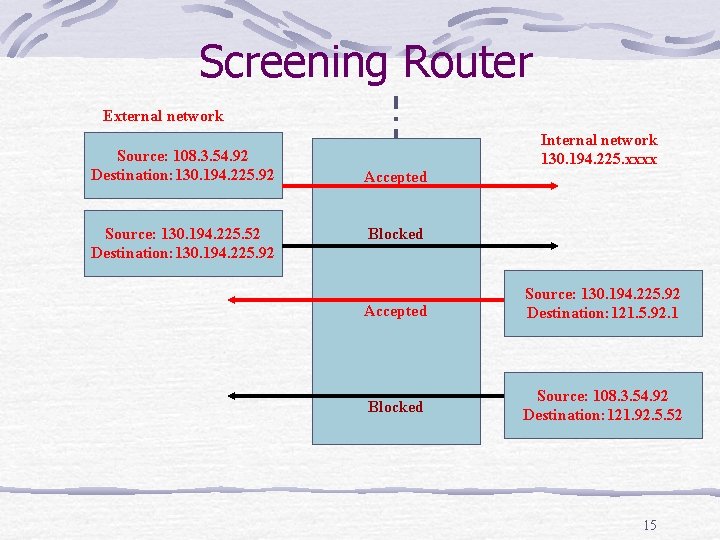
Method of defense Avoid reliance on address-based authentication and trust mechanisms (liked those used by rsh) Use a screening router, a device that can intelligently filter network packets based on configurable rules. Although this cannot prevent spoofing, but can prevent Inbound attacks that originate from external networks (by discarding incoming datagrams with source address belonging to the internal address) Outbound attacks that originate inside of your own network (discarding outgoing datagrams with a source address from an external network). 14

Screening Router External network Source: 108. 3. 54. 92 Destination: 130. 194. 225. 92 Source: 130. 194. 225. 52 Destination: 130. 194. 225. 92 Accepted Internal network 130. 194. 225. xxxx Blocked Accepted Source: 130. 194. 225. 92 Destination: 121. 5. 92. 1 Blocked Source: 108. 3. 54. 92 Destination: 121. 92. 5. 52 15

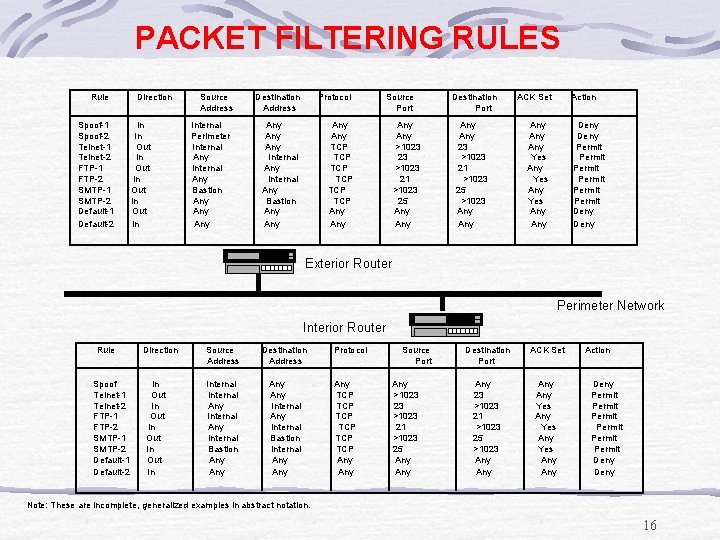
PACKET FILTERING RULES Rule Spoof-1 Spoof-2 Telnet-1 Telnet-2 FTP-1 FTP-2 SMTP-1 SMTP-2 Default-1 Default-2 Direction In In Out In Source Address Internal Perimeter Internal Any Bastion Any Any Destination Address Protocol Any Any Internal Any Bastion Any Any TCP TCP TCP Any Source Port Any >1023 23 >1023 21 >1023 25 Any Destination Port Any 23 >1023 21 >1023 25 >1023 Any ACK Set Action Any Any Yes Any Deny Permit Permit Deny Exterior Router Perimeter Network Interior Router Rule Spoof Telnet-1 Telnet-2 FTP-1 FTP-2 SMTP-1 SMTP-2 Default-1 Default-2 Direction In Out In Source Address Destination Address Internal Any Internal Bastion Any Any Internal Bastion Internal Any Protocol Any TCP TCP TCP Any Source Port Any >1023 23 >1023 21 >1023 25 Any Destination Port ACK Set Any 23 >1023 21 >1023 25 >1023 Any Any Yes Any Action Deny Permit Permit Deny Note: These are incomplete, generalized examples in abstract notation. 16

Firewalls Screening router (also called as packet filtering) is an example of a firewall. We will look at the firewalls in more detail later. 17

SYN Attack 18

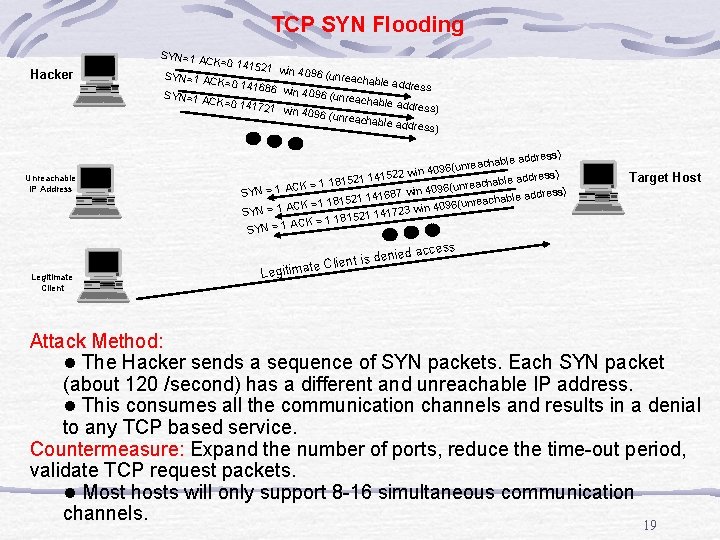
TCP SYN Flooding SYN=1 A Hacker Unreachable IP Address Legitimate Client CK=0 141 521 win 4 096 (unre SYN=1 A achable a CK=0 141 ddress 686 win 4 096 (unre SYN=1 A a c hable add CK=0 141 ress) 721 win 4 096 (unre achable a ddress) hable add c a re n (u 6 win 409 ress) 1 141522 2 5 1 8 1 hable add c 1 a = re n K C (u A 6 ss) SYN = 1 7 win 409 able addre 21 14168 h 5 c 1 a 8 re 1 n 1 (u = CK win 4096 SYN = 1 A 1 141723 2 5 1 8 1 1 CK = SYN = 1 A te Legitima denied Client is Target Host access Attack Method: l The Hacker sends a sequence of SYN packets. Each SYN packet (about 120 /second) has a different and unreachable IP address. l This consumes all the communication channels and results in a denial to any TCP based service. Countermeasure: Expand the number of ports, reduce the time-out period, validate TCP request packets. l Most hosts will only support 8 -16 simultaneous communication channels. 19

PING Attack 20

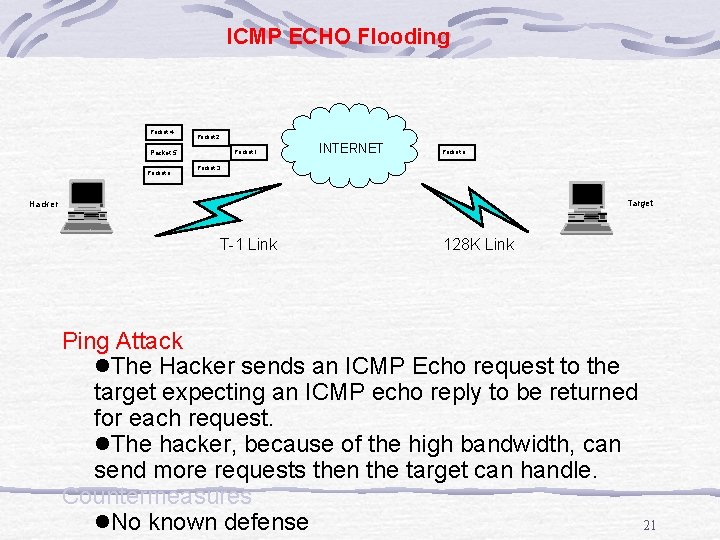
ICMP ECHO Flooding Packet 4 Packet 2 Packet 5 Packet n Packet 1 INTERNET Packet n Packet 3 Target Hacker T-1 Link 128 K Link Ping Attack l. The Hacker sends an ICMP Echo request to the target expecting an ICMP echo reply to be returned for each request. l. The hacker, because of the high bandwidth, can send more requests then the target can handle. Countermeasures l. No known defense 21

SMURF Attack 22

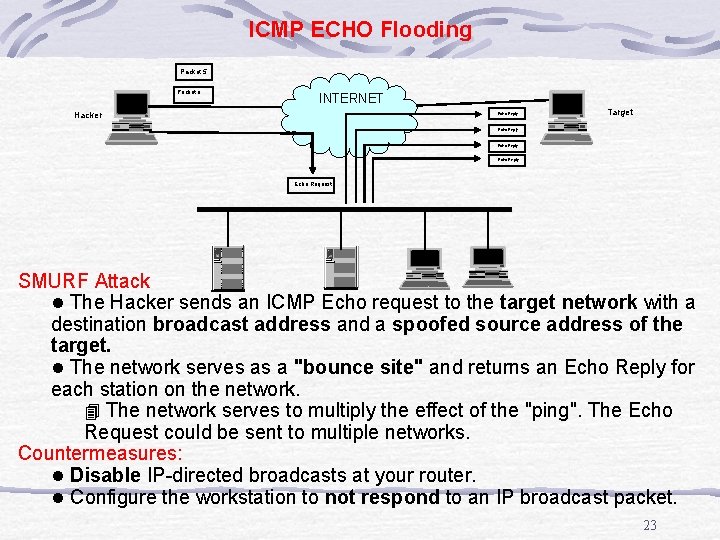
ICMP ECHO Flooding Packet 5 Packet n INTERNET Hacker Echo Reply Target Echo Reply Echo Request SMURF Attack l The Hacker sends an ICMP Echo request to the target network with a destination broadcast address and a spoofed source address of the target. l The network serves as a "bounce site" and returns an Echo Reply for each station on the network. 4 The network serves to multiply the effect of the "ping". The Echo Request could be sent to multiple networks. Countermeasures: l Disable IP-directed broadcasts at your router. l Configure the workstation to not respond to an IP broadcast packet. 23

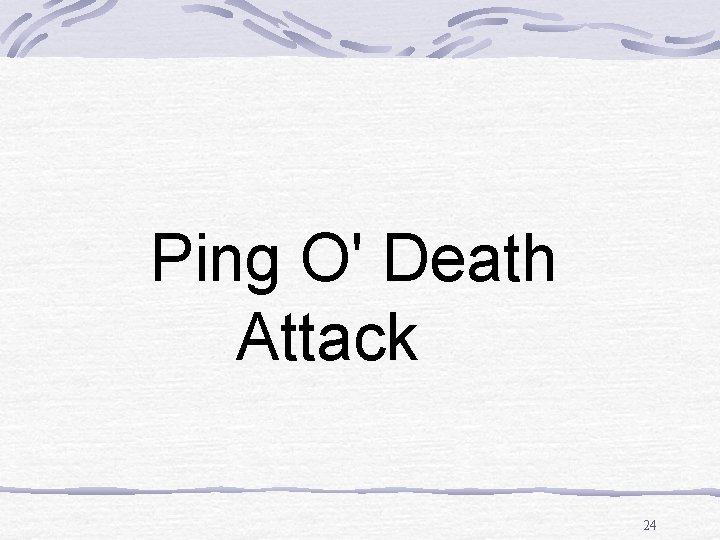
Ping O' Death Attack 24

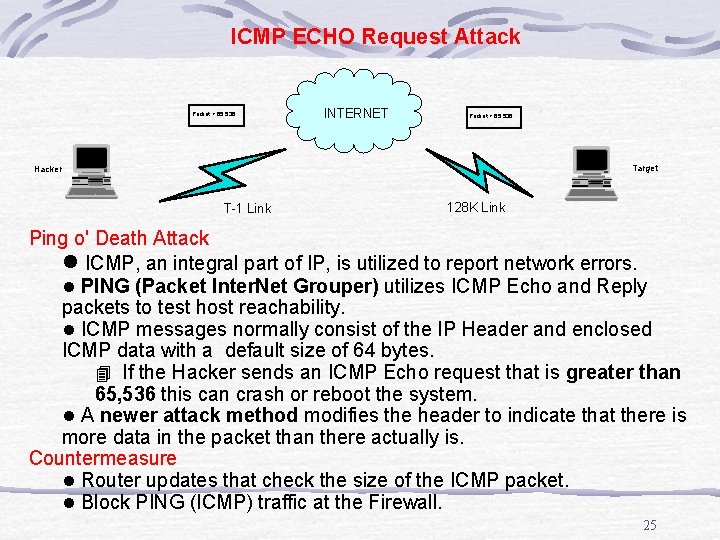
ICMP ECHO Request Attack Packet > 65, 536 INTERNET Packet > 65, 536 Target Hacker T-1 Link 128 K Link Ping o' Death Attack l ICMP, an integral part of IP, is utilized to report network errors. l PING (Packet Inter. Net Grouper) utilizes ICMP Echo and Reply packets to test host reachability. l ICMP messages normally consist of the IP Header and enclosed ICMP data with a default size of 64 bytes. 4 If the Hacker sends an ICMP Echo request that is greater than 65, 536 this can crash or reboot the system. l A newer attack method modifies the header to indicate that there is more data in the packet than there actually is. Countermeasure l Router updates that check the size of the ICMP packet. l Block PING (ICMP) traffic at the Firewall. 25

RST Attack 26

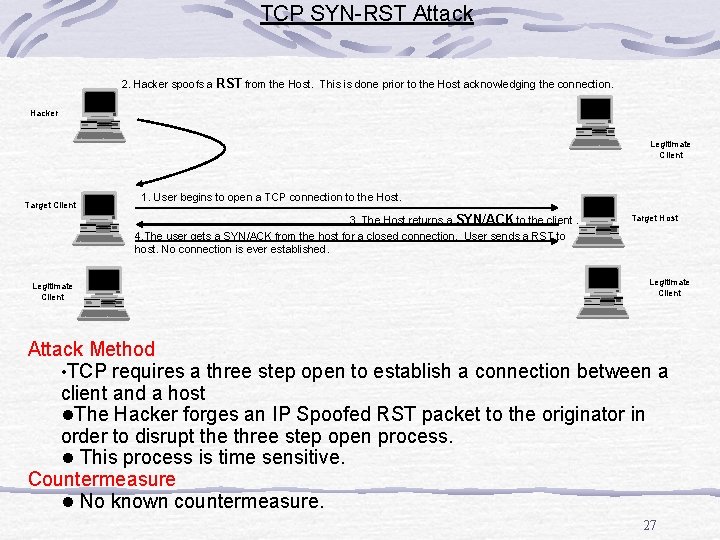
TCP SYN-RST Attack 2. Hacker spoofs a RST from the Host. This is done prior to the Host acknowledging the connection. Hacker Legitimate Client Target Client 1. User begins to open a TCP connection to the Host. 3. The Host returns a SYN/ACK to the client. 4. The user gets a SYN/ACK from the host for a closed connection. User sends a RST to host. No connection is ever established. Legitimate Client Target Host Legitimate Client Attack Method • TCP requires a three step open to establish a connection between a client and a host l. The Hacker forges an IP Spoofed RST packet to the originator in order to disrupt the three step open process. l This process is time sensitive. Countermeasure l No known countermeasure. 27

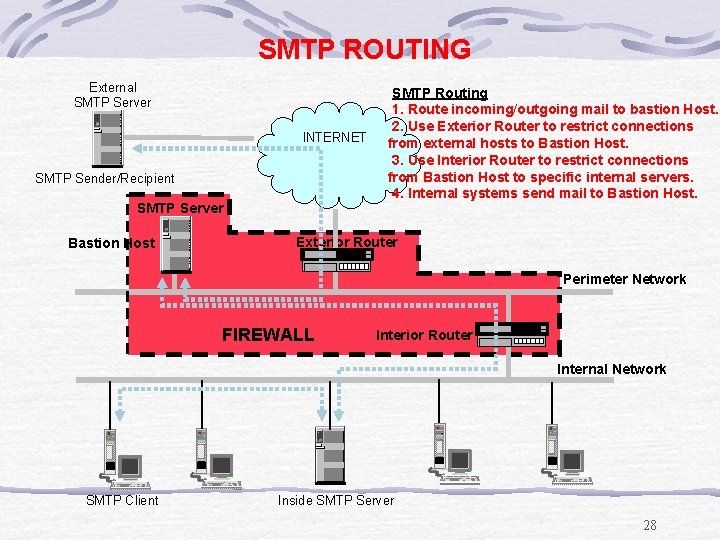
SMTP ROUTING External SMTP Server INTERNET SMTP Sender/Recipient SMTP Server Bastion Host SMTP Routing 1. Route incoming/outgoing mail to bastion Host. 2. Use Exterior Router to restrict connections from external hosts to Bastion Host. 3. Use Interior Router to restrict connections from Bastion Host to specific internal servers. 4. Internal systems send mail to Bastion Host. Exterior Router Perimeter Network FIREWALL Interior Router Internal Network SMTP Client Inside SMTP Server 28

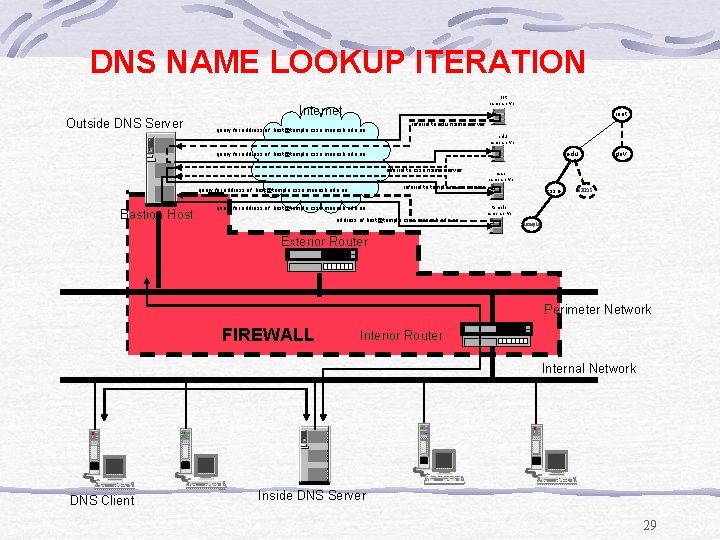
DNS NAME LOOKUP ITERATION Outside DNS Server root name server Internet root query for address of host@temple. csse. monash. edu. au referral to edu name server referral to csse name server Bastion Host csse name server referral to temple name server query for address of host@temple. csse. monash. edu. au gov edu query for address of host@temple. csse. monash. edu. au csse sims temple name server temple Exterior Router Perimeter Network FIREWALL Interior Router Internal Network DNS Client Inside DNS Server 29

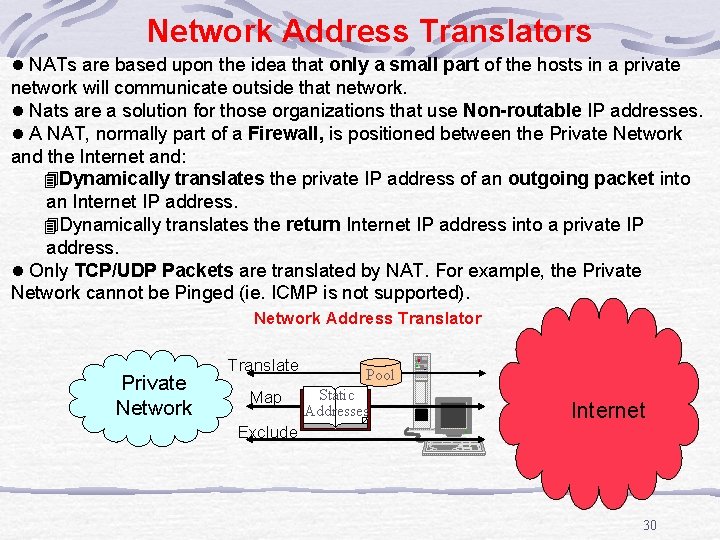
Network Address Translators l NATs are based upon the idea that only a small part of the hosts in a private network will communicate outside that network. l Nats are a solution for those organizations that use Non-routable IP addresses. l A NAT, normally part of a Firewall, is positioned between the Private Network and the Internet and: 4 Dynamically translates the private IP address of an outgoing packet into an Internet IP address. 4 Dynamically translates the return Internet IP address into a private IP address. l Only TCP/UDP Packets are translated by NAT. For example, the Private Network cannot be Pinged (ie. ICMP is not supported). Network Address Translator Private Network Translate Map Exclude Pool Static Addresses Internet 30

TCP/IP Security 31

Why Wrappers? These programs are born out of the need to modify the operating systems without access to the systems’ source code as well as security tools. the security logic is encapsulated into a single program, wrappers are simple and easy to validate. the wrapped program remains a separate entity, it can be upgraded without a need to re-certify the program that is wrapping it. wrappers call the wrapped program via the standard exec() system call, a single wrapper can be used to control access to a variety of wrapped programs. 32

Why Wrappers? Common use of wrappers is to limit the amount of information reaching a network-capable program. The above is an advantage because those programs are general in nature and are likely to be trusting and can accept too much information without validation. 33

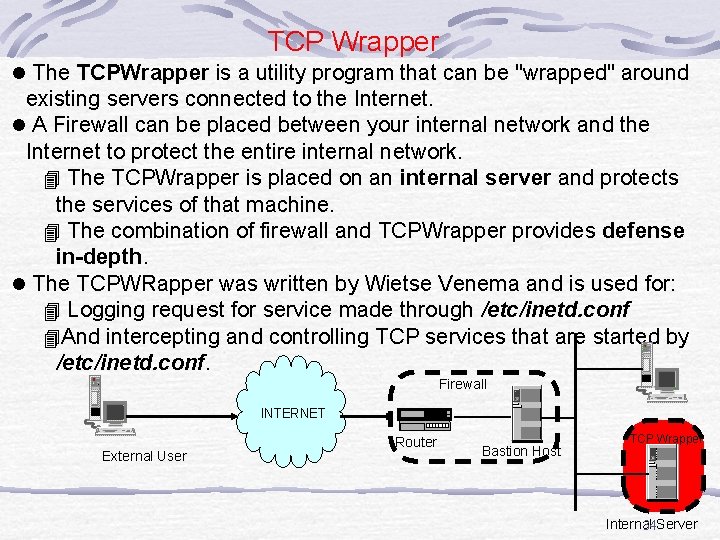
TCP Wrapper l The TCPWrapper is a utility program that can be "wrapped" around existing servers connected to the Internet. l A Firewall can be placed between your internal network and the Internet to protect the entire internal network. 4 The TCPWrapper is placed on an internal server and protects the services of that machine. 4 The combination of firewall and TCPWrapper provides defense in-depth. l The TCPWRapper was written by Wietse Venema and is used for: 4 Logging request for service made through /etc/inetd. conf 4 And intercepting and controlling TCP services that are started by /etc/inetd. conf. Firewall INTERNET External User Router Bastion Host TCP Wrapper Internal 34 Server

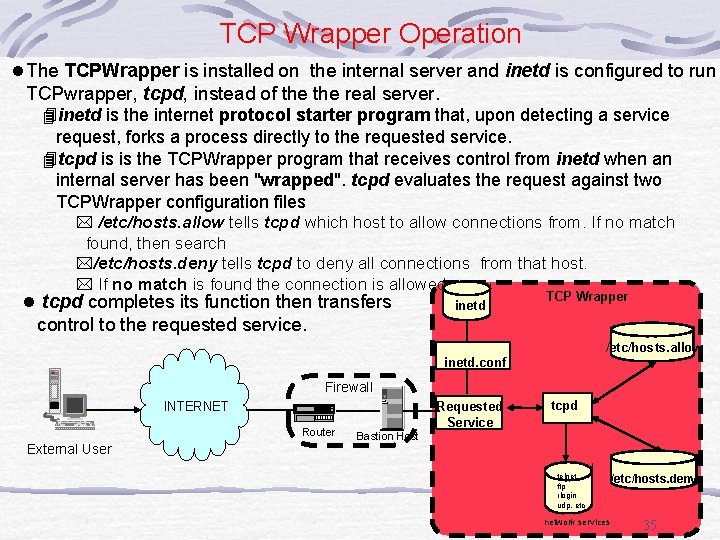
TCP Wrapper Operation l The TCPWrapper is installed on the internal server and inetd is configured to run TCPwrapper, tcpd, instead of the real server. 4 inetd is the internet protocol starter program that, upon detecting a service request, forks a process directly to the requested service. 4 tcpd is is the TCPWrapper program that receives control from inetd when an internal server has been "wrapped". tcpd evaluates the request against two TCPWrapper configuration files * /etc/hosts. allow tells tcpd which host to allow connections from. If no match found, then search */etc/hosts. deny tells tcpd to deny all connections from that host. * If no match is found the connection is allowed. l tcpd completes its function then transfers inetd TCP Wrapper control to the requested service. /etc/hosts. allow inetd. conf Firewall Requested Service INTERNET Router External User tcpd Bastion Host telnet ftp rlogin udp, etc network services /etc/hosts. deny 35

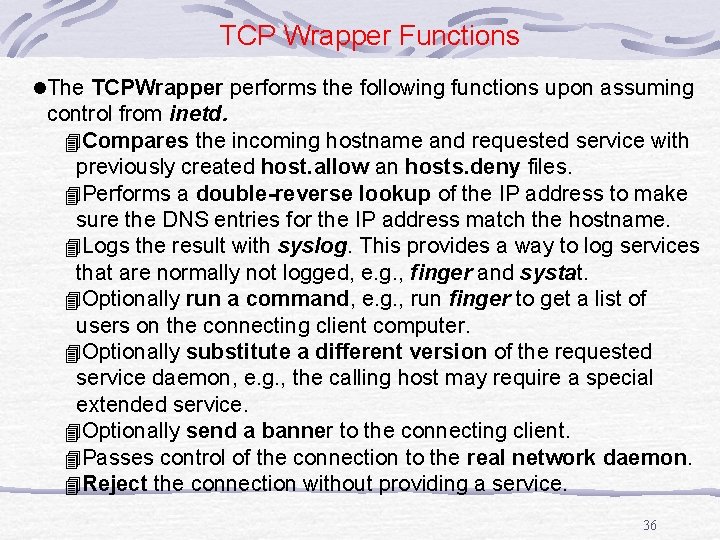
TCP Wrapper Functions l. The TCPWrapper performs the following functions upon assuming control from inetd. 4 Compares the incoming hostname and requested service with previously created host. allow an hosts. deny files. 4 Performs a double-reverse lookup of the IP address to make sure the DNS entries for the IP address match the hostname. 4 Logs the result with syslog. This provides a way to log services that are normally not logged, e. g. , finger and systat. 4 Optionally run a command, e. g. , run finger to get a list of users on the connecting client computer. 4 Optionally substitute a different version of the requested service daemon, e. g. , the calling host may require a special extended service. 4 Optionally send a banner to the connecting client. 4 Passes control of the connection to the real network daemon. 4 Reject the connection without providing a service. 36

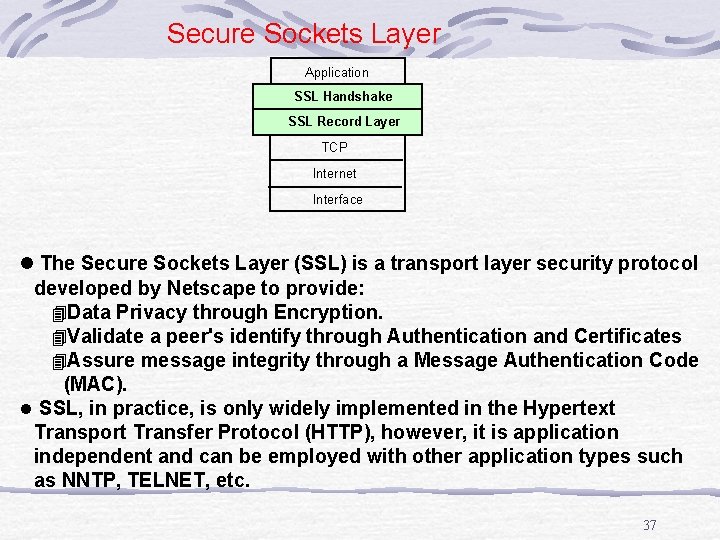
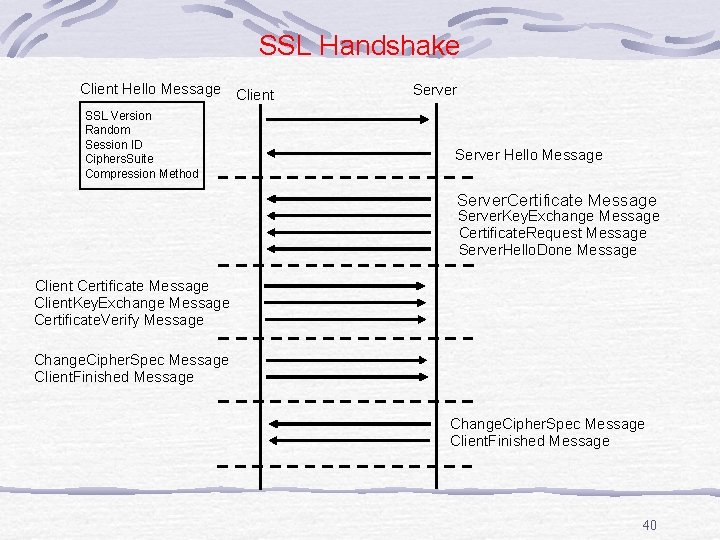
Secure Sockets Layer Application SSL Handshake SSL Record Layer TCP Internet Interface l The Secure Sockets Layer (SSL) is a transport layer security protocol developed by Netscape to provide: 4 Data Privacy through Encryption. 4 Validate a peer's identify through Authentication and Certificates 4 Assure message integrity through a Message Authentication Code (MAC). l SSL, in practice, is only widely implemented in the Hypertext Transport Transfer Protocol (HTTP), however, it is application independent and can be employed with other application types such as NNTP, TELNET, etc. 37

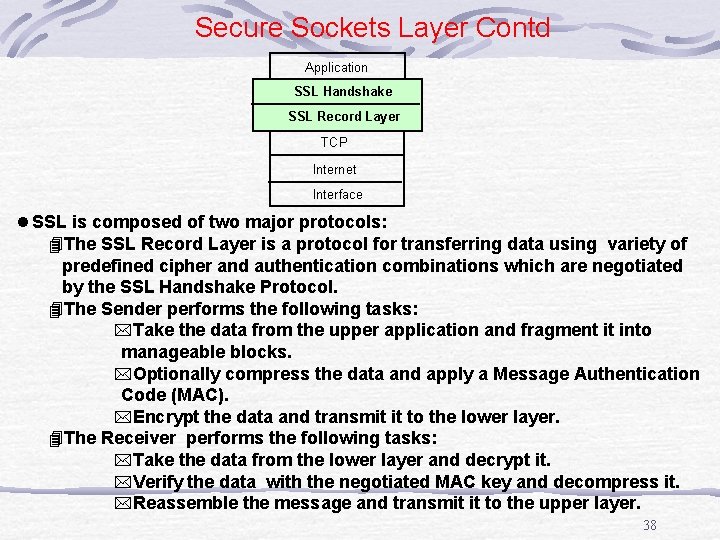
Secure Sockets Layer Contd Application SSL Handshake SSL Record Layer TCP Internet Interface l SSL is composed of two major protocols: 4 The SSL Record Layer is a protocol for transferring data using variety of predefined cipher and authentication combinations which are negotiated by the SSL Handshake Protocol. 4 The Sender performs the following tasks: *Take the data from the upper application and fragment it into manageable blocks. *Optionally compress the data and apply a Message Authentication Code (MAC). *Encrypt the data and transmit it to the lower layer. 4 The Receiver performs the following tasks: *Take the data from the lower layer and decrypt it. *Verify the data with the negotiated MAC key and decompress it. *Reassemble the message and transmit it to the upper layer. 38

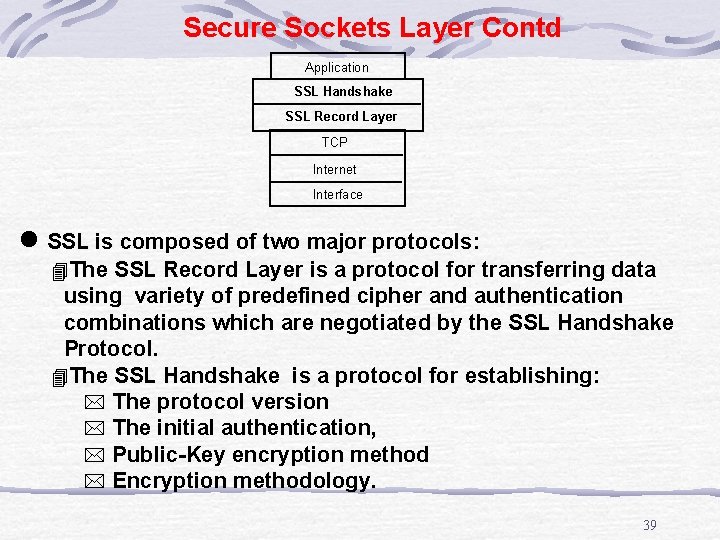
Secure Sockets Layer Contd Application SSL Handshake SSL Record Layer TCP Internet Interface l SSL is composed of two major protocols: 4 The SSL Record Layer is a protocol for transferring data using variety of predefined cipher and authentication combinations which are negotiated by the SSL Handshake Protocol. 4 The SSL Handshake is a protocol for establishing: * The protocol version * The initial authentication, * Public-Key encryption method * Encryption methodology. 39

SSL Handshake Client Hello Message Client SSL Version Random Session ID Ciphers. Suite Compression Method Server Hello Message Server. Certificate Message Server. Key. Exchange Message Certificate. Request Message Server. Hello. Done Message Client Certificate Message Client. Key. Exchange Message Certificate. Verify Message Change. Cipher. Spec Message Client. Finished Message 40

Internet Protocol Security - IPSec - 41

IP SECURITY l. SECURITY ISSUES 4 Authentication: Allows the receiver to validate the identity of a user, client process or server process. 4 Integrity: Provides assurance to the receiver that the transmitted data has not been changed. 4 Confidentiality: Preventing the unwanted disclosure of information during transit. l. SECURITY STRATEGY 4 Message Digest 5(MD 5): Used to satisfy Authentication and Data Integrity. 4 Cipher Block Chaining/Data Encryption Standard (CBC -DES): Used to satisfy confidentiality. 42

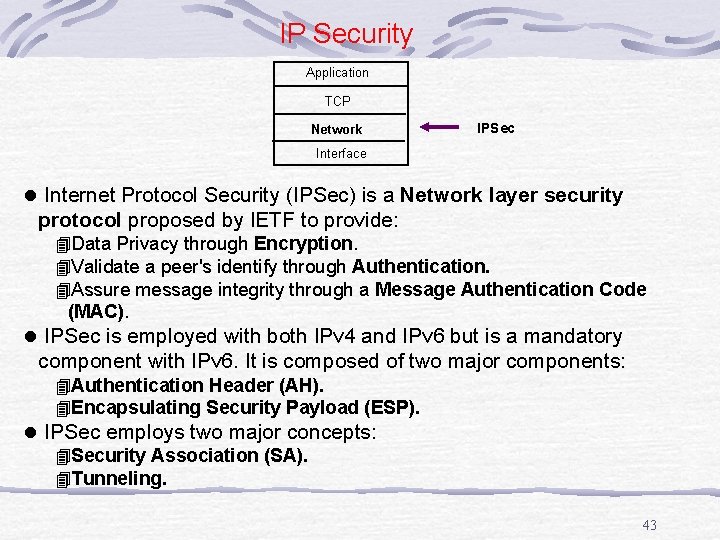
IP Security Application TCP Network IPSec Interface l Internet Protocol Security (IPSec) is a Network layer security protocol proposed by IETF to provide: 4 Data Privacy through Encryption. 4 Validate a peer's identify through Authentication. 4 Assure message integrity through a Message Authentication Code (MAC). l IPSec is employed with both IPv 4 and IPv 6 but is a mandatory component with IPv 6. It is composed of two major components: 4 Authentication Header (AH). 4 Encapsulating Security Payload (ESP). l IPSec employs two major concepts: 4 Security Association (SA). 4 Tunneling. 43

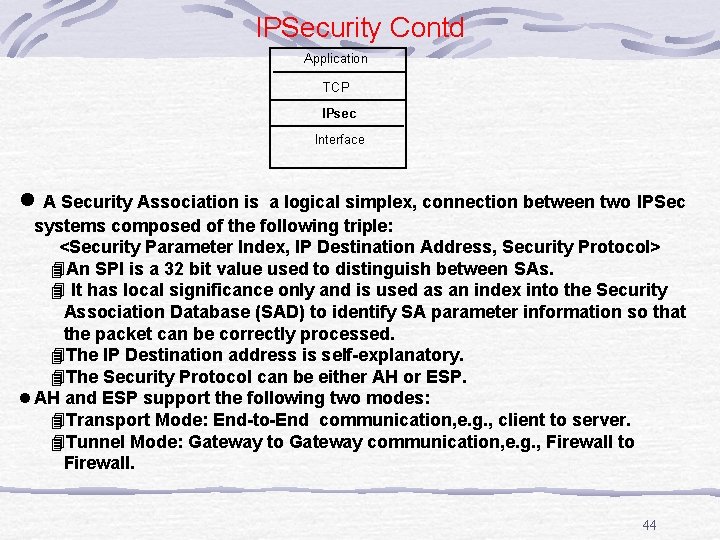
IPSecurity Contd Application TCP IPsec Interface l A Security Association is a logical simplex, connection between two IPSec systems composed of the following triple: <Security Parameter Index, IP Destination Address, Security Protocol> 4 An SPI is a 32 bit value used to distinguish between SAs. 4 It has local significance only and is used as an index into the Security Association Database (SAD) to identify SA parameter information so that the packet can be correctly processed. 4 The IP Destination address is self-explanatory. 4 The Security Protocol can be either AH or ESP. l AH and ESP support the following two modes: 4 Transport Mode: End-to-End communication, e. g. , client to server. 4 Tunnel Mode: Gateway to Gateway communication, e. g. , Firewall to Firewall. 44

Authentication 45

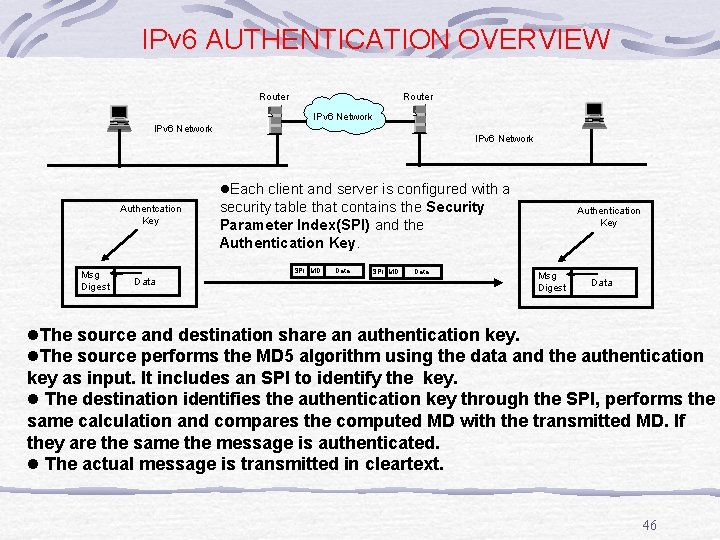
IPv 6 AUTHENTICATION OVERVIEW Router IPv 6 Network l. Each client and server is configured with a Authentcation Key Msg Digest security table that contains the Security Parameter Index(SPI) and the Authentication Key. SPI MD Data Authentication Key Msg Digest Data l. The source and destination share an authentication key. l. The source performs the MD 5 algorithm using the data and the authentication key as input. It includes an SPI to identify the key. l The destination identifies the authentication key through the SPI, performs the same calculation and compares the computed MD with the transmitted MD. If they are the same the message is authenticated. l The actual message is transmitted in cleartext. 46

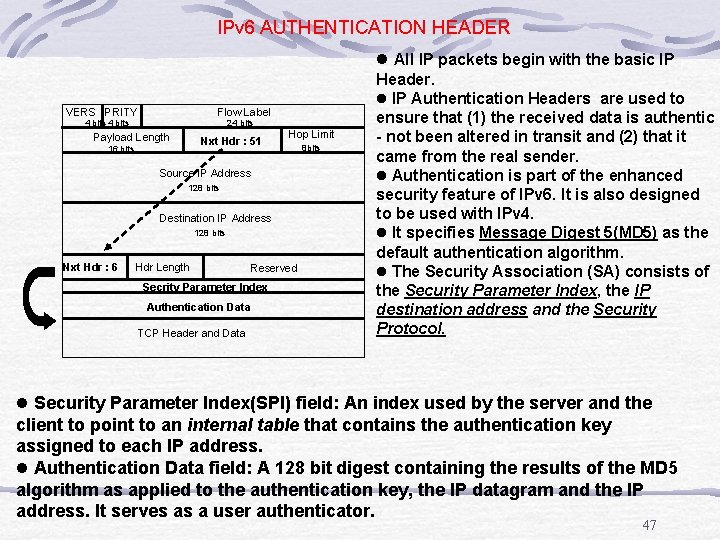
IPv 6 AUTHENTICATION HEADER VERS PRITY Flow Label 4 bits 24 bits Payload Length Nxt Hdr : 51 16 bits Hop Limit Source IP Address 128 bits Destination IP Address 128 bits Nxt Hdr : 6 Hdr Length Reserved Secrity Parameter Index Authentication Data TCP Header and Data 8 bits l All IP packets begin with the basic IP Header. l IP Authentication Headers are used to ensure that (1) the received data is authentic - not been altered in transit and (2) that it came from the real sender. l Authentication is part of the enhanced security feature of IPv 6. It is also designed to be used with IPv 4. l It specifies Message Digest 5(MD 5) as the default authentication algorithm. l The Security Association (SA) consists of the Security Parameter Index, the IP destination address and the Security Protocol. l Security Parameter Index(SPI) field: An index used by the server and the client to point to an internal table that contains the authentication key assigned to each IP address. l Authentication Data field: A 128 bit digest containing the results of the MD 5 algorithm as applied to the authentication key, the IP datagram and the IP address. It serves as a user authenticator. 47

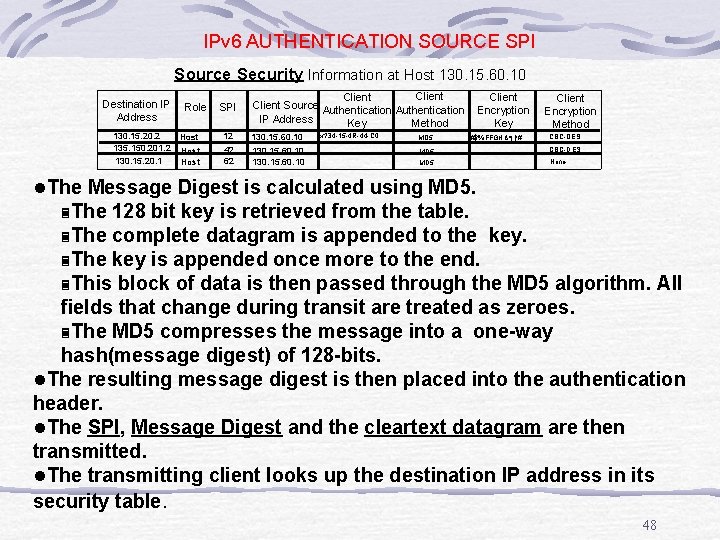
IPv 6 AUTHENTICATION SOURCE SPI Source Security Information at Host 130. 15. 60. 10 Destination IP Address Role 130. 15. 20. 2 Host 135. 150. 201. 2 Host 130. 15. 20. 1 Host SPI 12 42 62 Client Source Authentication IP Address Method Key 130. 15. 60. 10 x? 34 -15 -4 R-44 -C 0. . . MD 5 Client Encryption Key #$%FFGH&*()!#. . . MD 5 . . . . Client Encryption Method CBC-DES None l. The Message Digest is calculated using MD 5. 3 The 128 bit key is retrieved from the table. 3 The complete datagram is appended to the key. 3 The key is appended once more to the end. 3 This block of data is then passed through the MD 5 algorithm. All fields that change during transit are treated as zeroes. 3 The MD 5 compresses the message into a one-way hash(message digest) of 128 -bits. l. The resulting message digest is then placed into the authentication header. l. The SPI, Message Digest and the cleartext datagram are then transmitted. l. The transmitting client looks up the destination IP address in its security table. 48

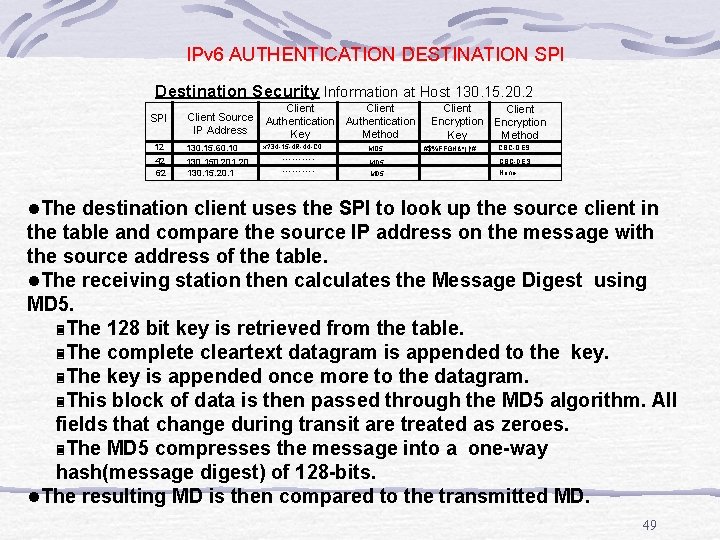
IPv 6 AUTHENTICATION DESTINATION SPI Destination Security Information at Host 130. 15. 20. 2 SPI Client Source IP Address 12 130. 15. 60. 10 42 62 130. 150. 201. 20 130. 15. 20. 1 Client Authentication Method Key x? 34 -15 -4 R-44 -C 0. . . MD 5 Client Encryption Key Method #$%FFGH&*()!#. . . . . CBC-DES None l. The destination client uses the SPI to look up the source client in the table and compare the source IP address on the message with the source address of the table. l. The receiving station then calculates the Message Digest using MD 5. 3 The 128 bit key is retrieved from the table. 3 The complete cleartext datagram is appended to the key. 3 The key is appended once more to the datagram. 3 This block of data is then passed through the MD 5 algorithm. All fields that change during transit are treated as zeroes. 3 The MD 5 compresses the message into a one-way hash(message digest) of 128 -bits. l. The resulting MD is then compared to the transmitted MD. 49

Encryption 50

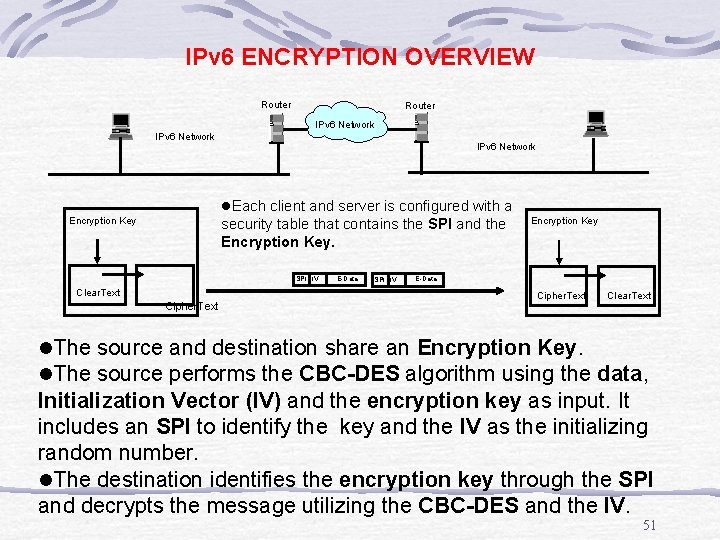
IPv 6 ENCRYPTION OVERVIEW Router IPv 6 Network l. Each client and server is configured with a Encryption Key security table that contains the SPI and the Encryption Key. SPI IV Clear. Text Cipher. Text E-Data SPI IV Encryption Key E-Data Cipher. Text Clear. Text l. The source and destination share an Encryption Key. l. The source performs the CBC-DES algorithm using the data, Initialization Vector (IV) and the encryption key as input. It includes an SPI to identify the key and the IV as the initializing random number. l. The destination identifies the encryption key through the SPI and decrypts the message utilizing the CBC-DES and the IV. 51

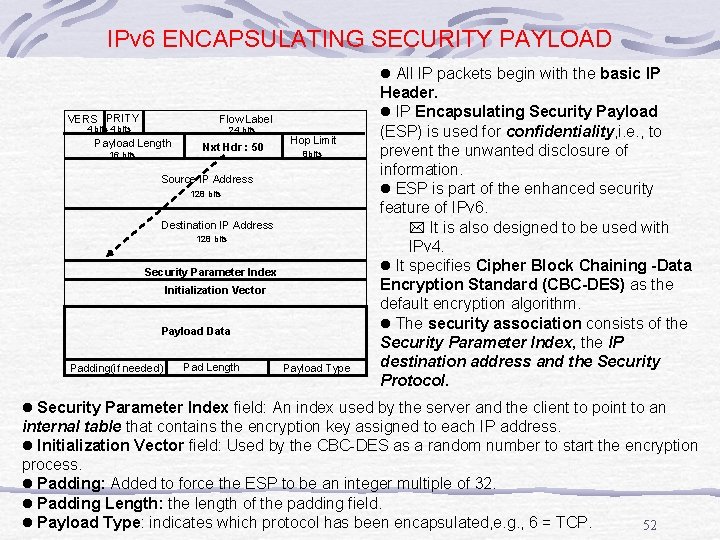
IPv 6 ENCAPSULATING SECURITY PAYLOAD l All IP packets begin with the basic IP VERS PRITY Flow Label 4 bits 24 bits Payload Length 16 bits Nxt Hdr : 50 Hop Limit 8 bits Source IP Address 128 bits Destination IP Address 128 bits Security Parameter Index Initialization Vector Payload Data Padding(if needed) Pad Length Payload Type Header. l IP Encapsulating Security Payload (ESP) is used for confidentiality, i. e. , to prevent the unwanted disclosure of information. l ESP is part of the enhanced security feature of IPv 6. * It is also designed to be used with IPv 4. l It specifies Cipher Block Chaining -Data Encryption Standard (CBC-DES) as the default encryption algorithm. l The security association consists of the Security Parameter Index, the IP destination address and the Security Protocol. l Security Parameter Index field: An index used by the server and the client to point to an internal table that contains the encryption key assigned to each IP address. l Initialization Vector field: Used by the CBC-DES as a random number to start the encryption process. l Padding: Added to force the ESP to be an integer multiple of 32. l Padding Length: the length of the padding field. l Payload Type: indicates which protocol has been encapsulated, e. g. , 6 = TCP. 52

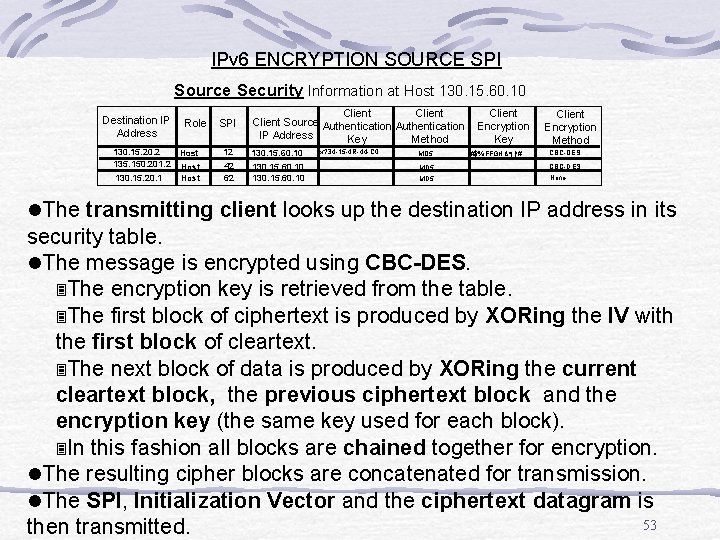
IPv 6 ENCRYPTION SOURCE SPI Source Security Information at Host 130. 15. 60. 10 Destination IP Address Role 130. 15. 20. 2 Host 135. 150. 201. 2 Host 130. 15. 20. 1 Host SPI 12 42 62 Client Source Authentication IP Address Method Key 130. 15. 60. 10 x? 34 -15 -4 R-44 -C 0. . . MD 5 Client Encryption Key #$%FFGH&*()!#. . . . . Client Encryption Method CBC-DES None l. The transmitting client looks up the destination IP address in its security table. l. The message is encrypted using CBC-DES. 3 The encryption key is retrieved from the table. 3 The first block of ciphertext is produced by XORing the IV with the first block of cleartext. 3 The next block of data is produced by XORing the current cleartext block, the previous ciphertext block and the encryption key (the same key used for each block). 3 In this fashion all blocks are chained together for encryption. l. The resulting cipher blocks are concatenated for transmission. l. The SPI, Initialization Vector and the ciphertext datagram is 53 then transmitted.

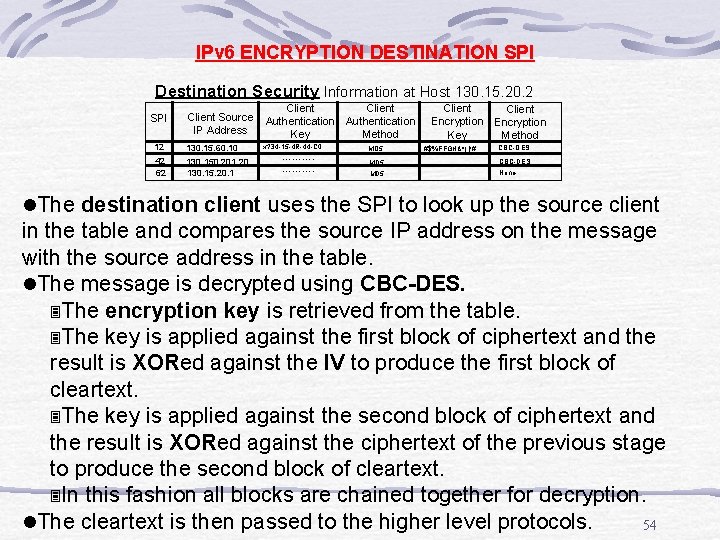
IPv 6 ENCRYPTION DESTINATION SPI Destination Security Information at Host 130. 15. 20. 2 SPI Client Source IP Address 12 130. 15. 60. 10 42 62 130. 150. 201. 20 130. 15. 20. 1 Client Authentication Method Key x? 34 -15 -4 R-44 -C 0. . . MD 5 Client Encryption Key Method #$%FFGH&*()!#. . . . . CBC-DES None l. The destination client uses the SPI to look up the source client in the table and compares the source IP address on the message with the source address in the table. l. The message is decrypted using CBC-DES. 3 The encryption key is retrieved from the table. 3 The key is applied against the first block of ciphertext and the result is XORed against the IV to produce the first block of cleartext. 3 The key is applied against the second block of ciphertext and the result is XORed against the ciphertext of the previous stage to produce the second block of cleartext. 3 In this fashion all blocks are chained together for decryption. l. The cleartext is then passed to the higher level protocols. 54

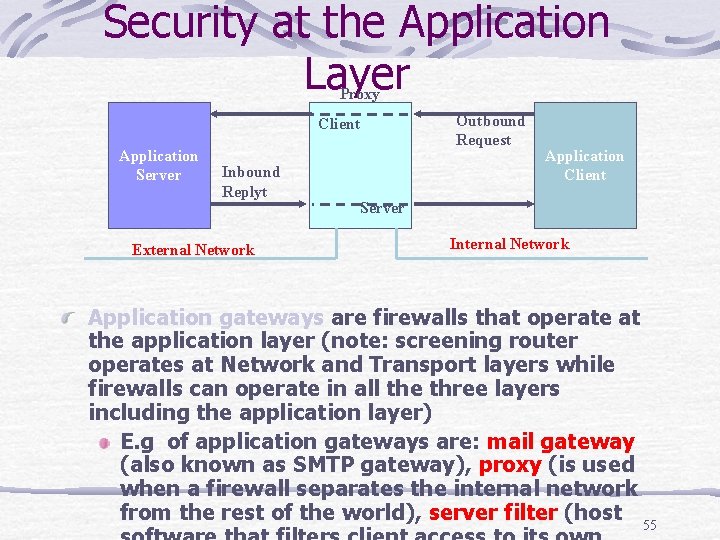
Security at the Application Layer Proxy Outbound Request Client Application Server Inbound Replyt External Network Application Client Server Internal Network Application gateways are firewalls that operate at the application layer (note: screening router operates at Network and Transport layers while firewalls can operate in all the three layers including the application layer) E. g of application gateways are: mail gateway (also known as SMTP gateway), proxy (is used when a firewall separates the internal network from the rest of the world), server filter (host 55