Security Guide to Network Security Fundamentals Fourth Edition






































- Slides: 54

Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 2 Malware and Social Engineering Attacks

Objectives • Describe the differences between a virus and a worm • List the types of malware that conceals its appearance • Identify different kinds of malware that is designed for profit • Describe the types of social engineering psychological attacks • Explain physical social engineering attacks Security+ Guide to Network Security Fundamentals, Fourth Edition 2

Attacks Using Malware • Malicious software (malware): is software that enters a computer system without the user’s knowledge or consent ﻣﻮﺍﻓﻘﺔ and then performs an unwanted and usually harmful action. • malware uses a threat vector to deliver a malicious “payload” that performs a harmful function once it is invoked. –Threat Vector is a path or a tool that a. Threat Actor uses to attack the target • However, malware is most often used as a general term that refers to a wide variety of damaging 3 software programs.

Attacks Using Malware • Primary objectives of malware – Infecting systems – Concealing ﺇﺧﻔﺎﺀ its purpose – Making profit Security+ Guide to Network Security Fundamentals, Fourth Edition 4

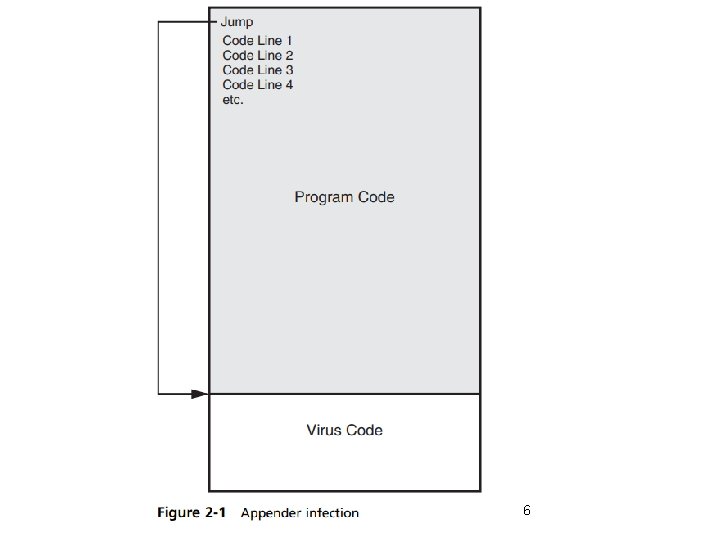
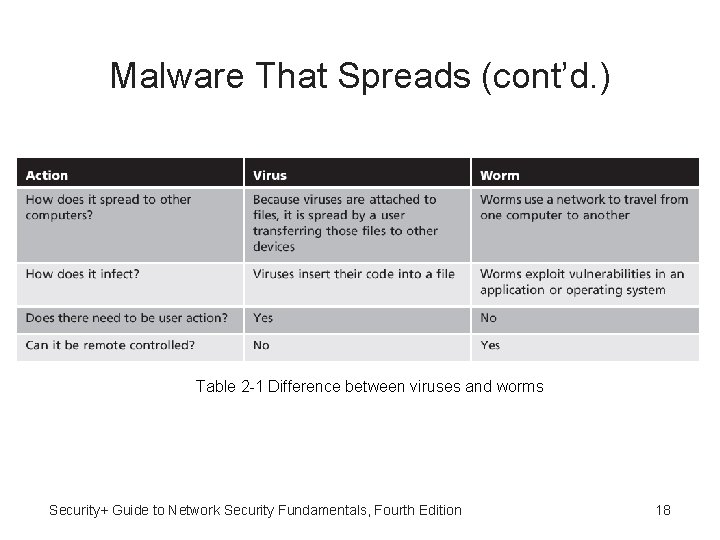
Malware That Spreads • Viruses – Malicious computer code that reproduces itself on the same computer without any human intervention. • Virus infection methods – Appender infection • Virus appends itself to end of a file • Moves first three bytes of original file to virus code • Replaces them with a jump instruction pointing to the virus code • When the program is launched, the jump instruction redirects control to the virus. Security+ Guide to Network Security Fundamentals, Fourth Edition 5

6

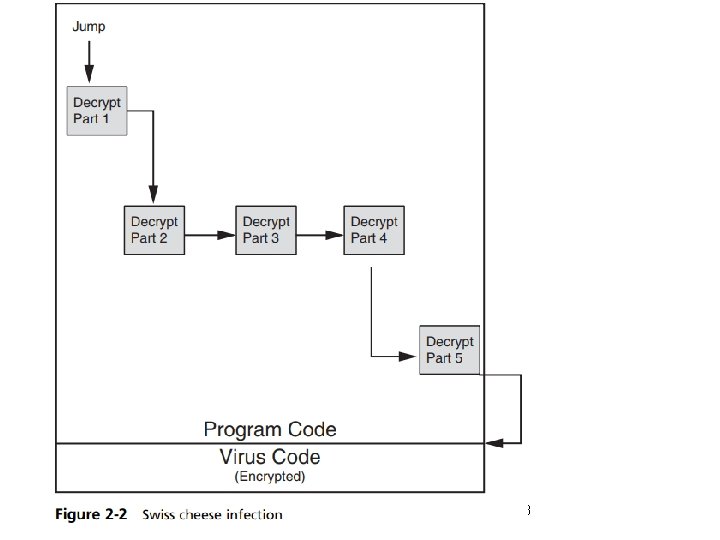
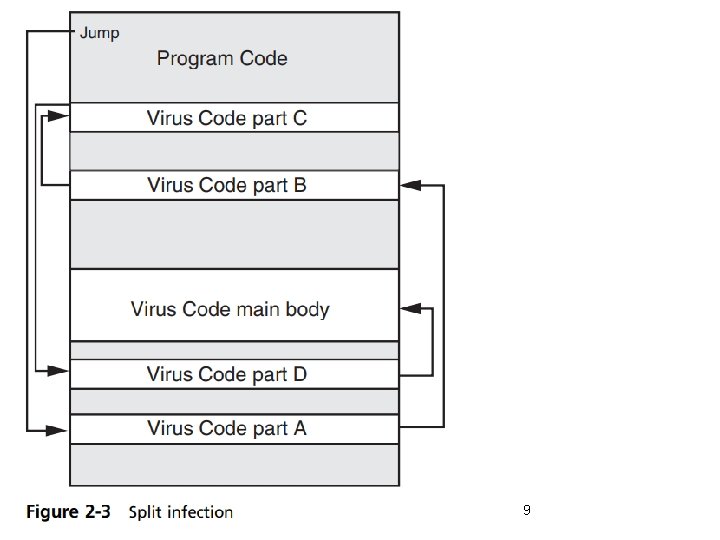
Malware That Spreads (cont’d. ) • Virus infection methods (cont’d. ) – Swiss cheese infection • First “scramble” (encrypt) the virus code to make it more difficult to detect. • Then divide the engine to “unscramble” (decrypt) the virus code into different pieces and inject these pieces throughout the infected program code. • When the program is launched the different pieces are then tied together and unscramble the virus code. – Split infection • • Virus splits into several parts Parts placed at random positions in host program Head of virus code starts at beginning of file Gives control to next piece of virus code Security+ Guide to Network Security Fundamentals, Fourth Edition 7

8

9

Malware That Spreads (cont’d. ) • When infected program is launched: – Virus replicates itself by spreading to another file on same computer. – Virus activates its malicious payload • Viruses may display an annoying message: – Or be much more harmful • Examples of virus actions – Cause a computer to repeatedly crash – Erase files from or reformat hard drive – Turn off computer’s security settings Security+ Guide to Network Security Fundamentals, Fourth Edition 10

Malware That Spreads (cont’d. ) Figure 2 -4 Annoying virus message © Cengage Learning 2012 Security+ Guide to Network Security Fundamentals, Fourth Edition 11

Malware That Spreads (cont’d. ) • A virus can only replicate itself on the host computer on which it is located; it cannot automatically spread to another computer by itself. – Relies on user action to spread • Viruses are attached to files • Viruses are spread by transferring infected files Security+ Guide to Network Security Fundamentals, Fourth Edition 12

Malware That Spreads (cont’d. ) • Types of computer viruses – Program viruses • A virus that infects an executable program file. • When the program is launched the virus is activated. – Macro viruses • Executes a script • One of the most common data file viruses. • Macros can be written by using a macro language, such as Visual Basic for Applications (VBA), and are stored within the user document. • Once the document is opened, the macro instructions then execute Security+ Guide to Network Security Fundamentals, Fourth Edition 13

14

Malware That Spreads (cont’d. ) • Types of computer viruses(cont’d. ) –Memory Resident • Loads into RAM when the computer boots up • Infects files opened by user or operating system –Boot virus • Infects the Master Boot Record of hard disk drive to harm the hard disk it selfe instead of programs and files. • MBR contains program necessary for the computer to start up and the hard drive partition table • Loads before the OS starts 15

Malware That Spreads (cont’d. ) • Types of computer viruses (cont’d. ) – Companion virus or Companion Trojan • Adds malicious copycat program to operating system which is copycat version to legitimate program. • Ex: a companion virus might add the malicious program Notepad. com as a companion to Notepad. exe and when user type in command prompt “Notepad” instead of “Notepad. exe” the malicious program Notepad. com will be executed. Security+ Guide to Network Security Fundamentals, Fourth Edition 16

Malware That Spreads (cont’d. ) • Worm – Malicious program – Exploits application or operating system vulnerability in order to enter computer. – Sends copies of itself to other network devices • Worms may: – Slow down a network by spreading quickly (by replicating it selfe so quickly) to Consume all network resources or – Leave behind a payload to harm infected systems • Examples of worm actions – Deleting computer files – Allowing remote control of a computer by an attacker Security+ Guide to Network Security Fundamentals, Fourth Edition 17

Malware That Spreads (cont’d. ) Table 2 -1 Difference between viruses and worms Security+ Guide to Network Security Fundamentals, Fourth Edition 18

Malware That Conceals ﻳﺨﻔﻲ ﻭﺟﻮﺩﻩ • Malware that hiding their presence from the user includes Trojans, Rootkits, Logic bomb and Backdoor • Trojans – Program that does something other than advertised – Typically executable programs • Contain hidden code that launches an attack – Sometimes made to appear as data file – Example • User downloads “free calendar program” • Program scans system for credit card numbers and passwords • Transmits information to attacker through network Security+ Guide to Network Security Fundamentals, Fourth Edition 19

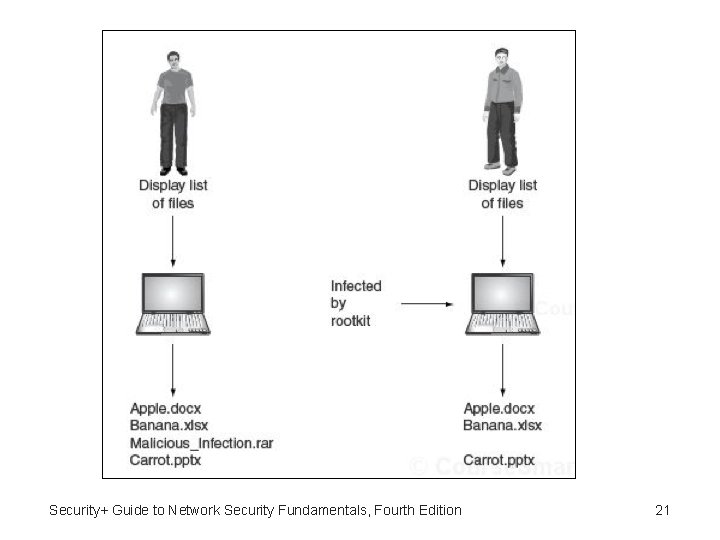
Malware That Conceals (cont’d. ) • Rootkits – Software tools used by an attacker to hide actions or presence of other types of malicious software such as trojans, viruses or worms. – Do that by Hide or remove traces of log-in records, log entries – May alter or replace operating system files with modified versions: • Specifically designed to ignore malicious activity for example for an anti-malware to scan specific directory it will receives file list of that directory from OS, rootkits will replaces this list with modified one that hide malicious files. Security+ Guide to Network Security Fundamentals, Fourth Edition 20

Security+ Guide to Network Security Fundamentals, Fourth Edition 21

Malware That Conceals (cont’d. ) • Rootkits can be detected using programs that compare file contents with original files this may require that detection program to run from clean media like CD or USB drive instead of hard drive. • Rootkits that operate at operating system’s lower levels: – May be difficult to detect • Removal of a rootkit can be difficult – Rootkit must be erased – Original operating system files must be restored – Reformat hard drive and reinstall operating system Security+ Guide to Network Security Fundamentals, Fourth Edition 22

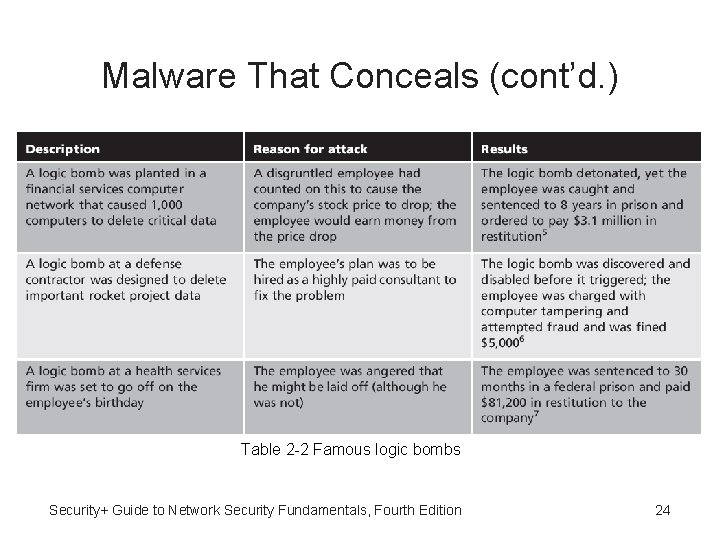
Malware That Conceals (cont’d. ) • Logic bomb – Computer code that lies dormant until it's Triggered by a specific logical event Then performs malicious activities – Difficult to detect before it is triggered because it embedded in larg program. • Attacker can easily insert 3 or 4 lines of code into large program and the inserted code is very hard to detect. • Backdoor – Software code that gives access to a computer, program, or service that circumvents ﺍﻻﻟﺘﻔﺎﻑ any normal security protections. – Backdoors that are installed on a computer allow the attacker to return at a later time and bypass security settings. – Common practice by developers is to remove backdoors in 23 final application.

Malware That Conceals (cont’d. ) Table 2 -2 Famous logic bombs Security+ Guide to Network Security Fundamentals, Fourth Edition 24

Malware That Profits • Types of malware designed to profit attackers – – Botnets Spyware Adware Keyloggers Security+ Guide to Network Security Fundamentals, Fourth Edition 25

Malware That Profits (cont’d. ) • Botnets – Computer is infected with program that allows it to be remotely controlled by attacker • Often payload of (carried by) Trojans, worms, and viruses – Infected computer called a zombie – Groups of zombie computers together called botnet • Early botnet attackers used Internet Relay Chat (IRC) to remotely control zombies – IRC is an open communications protocol used for real -time chatting. Security+ Guide to Network Security Fundamentals, Fourth Edition 26

Malware That Profits (cont’d. ) • HTTP is often used today instead of IRC which makes it more difficult to detect and block. – For example, a zombie can receive its instructions by automatically signing in to a website that the bot herder operates or to a third-party website on which information has been placed that the zombie knows how to interpret as commands 27

Malware That Profits (cont’d. ) • Botnets’ advantages for attackers – Operate in the background: • Often with no visible evidence of existence – Provide means for concealing actions of attacker – Can remain active for years – Large percentage of zombies are accessible at a given time • Due to growth of always-on Internet services Security+ Guide to Network Security Fundamentals, Fourth Edition 28

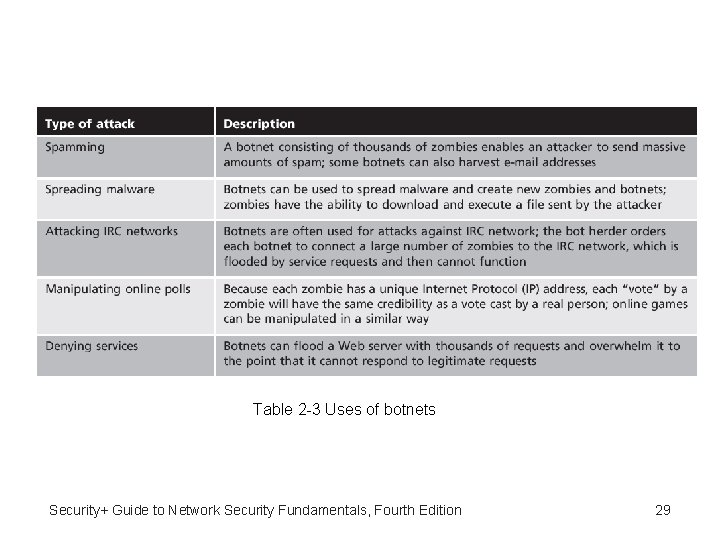
Table 2 -3 Uses of botnets Security+ Guide to Network Security Fundamentals, Fourth Edition 29

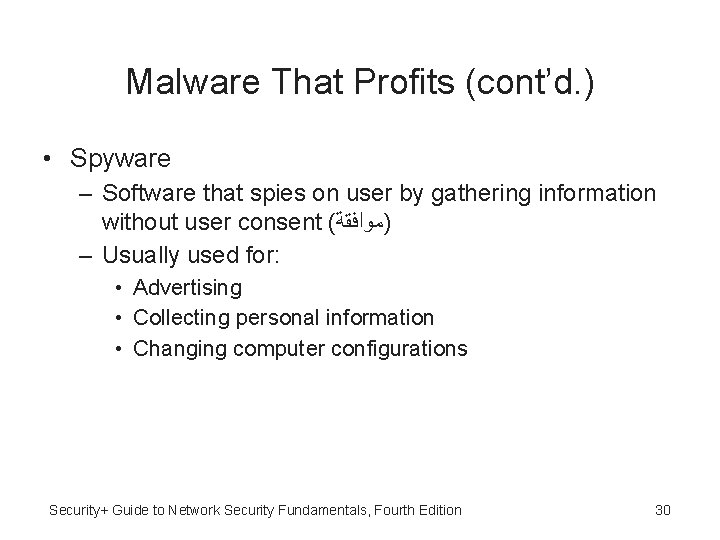
Malware That Profits (cont’d. ) • Spyware – Software that spies on user by gathering information without user consent ( )ﻣﻮﺍﻓﻘﺔ – Usually used for: • Advertising • Collecting personal information • Changing computer configurations Security+ Guide to Network Security Fundamentals, Fourth Edition 30

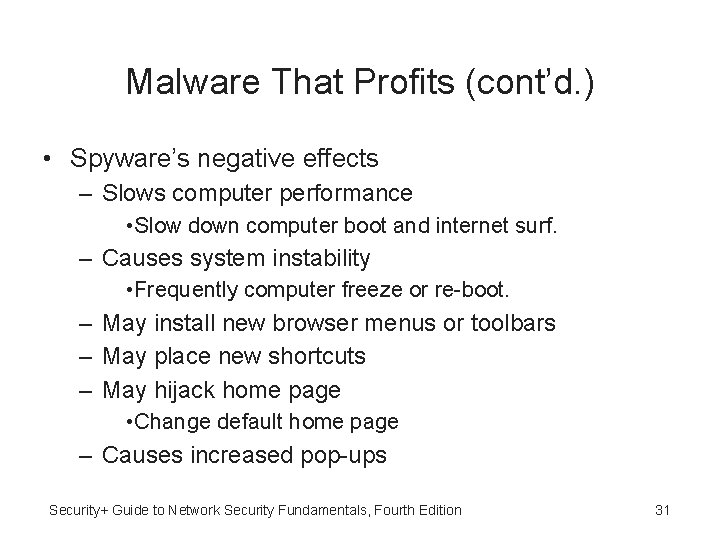
Malware That Profits (cont’d. ) • Spyware’s negative effects – Slows computer performance • Slow down computer boot and internet surf. – Causes system instability • Frequently computer freeze or re-boot. – May install new browser menus or toolbars – May place new shortcuts – May hijack home page • Change default home page – Causes increased pop-ups Security+ Guide to Network Security Fundamentals, Fourth Edition 31

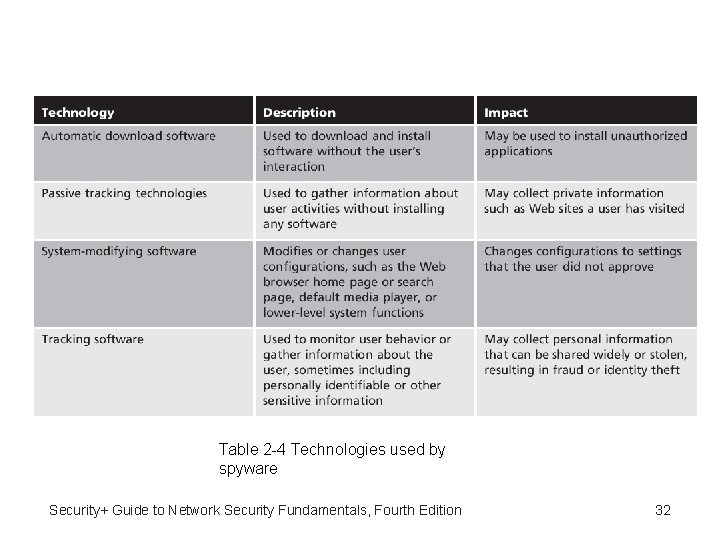
Table 2 -4 Technologies used by spyware Security+ Guide to Network Security Fundamentals, Fourth Edition 32

Malware That Profits (cont’d. ) • Adware – Program that delivers advertising content: • In manner unexpected and unwanted by the user – Typically displays advertising banners and pop-up ads – May open new browser windows randomly – Can also perform tracking of user online activities Security+ Guide to Network Security Fundamentals, Fourth Edition 33

Malware That Profits (cont’d. ) • Downsides of adware for users – May display objectionable content, such as gambling sites. – Frequent pop-up ads cause lost user productivity – Pop-up ads slow computer or cause crashes – Unwanted ads can be a nuisance ( )ﻣﺰﻋﺠﺔ Security+ Guide to Network Security Fundamentals, Fourth Edition 34

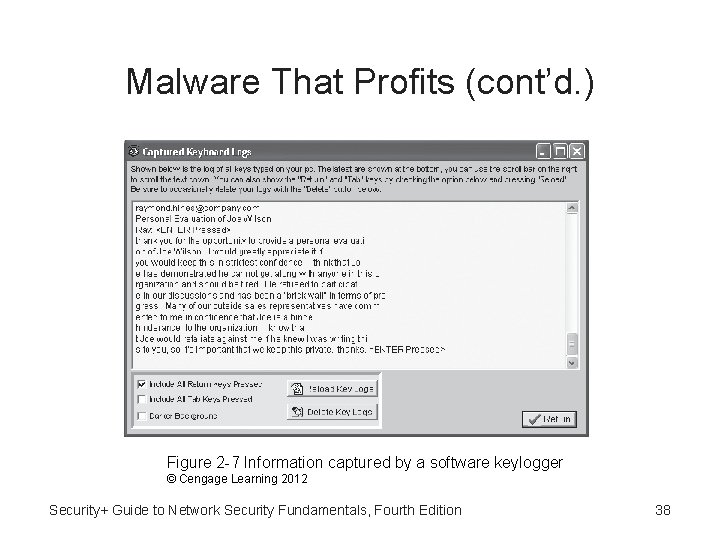
Malware That Profits (cont’d. ) • Keyloggers – Program that silently captures and stores each keystroke that a user types on the computer’s keyboard. – Information later retrieved by attacker. – Attacker searches for useful information • Passwords • Credit card numbers • Personal information Security+ Guide to Network Security Fundamentals, Fourth Edition 35

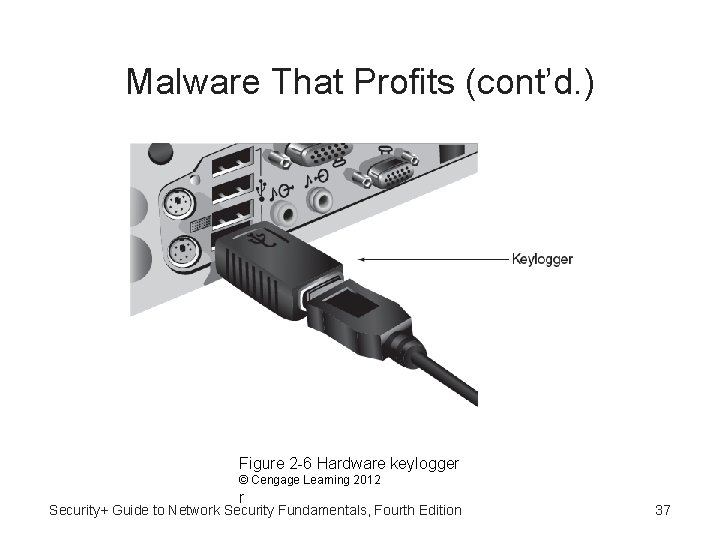
Malware That Profits (cont’d. ) • Keyloggers (cont’d. ) –A keylogger can be a small hardware device or a software program. – keylogger as hardware device • inserted between the computer keyboard connection and USB port. • Unlikely to be detected • Attacker physically removes device to collect information. Security+ Guide to Network Security Fundamentals, Fourth Edition 36

Malware That Profits (cont’d. ) Figure 2 -6 Hardware keylogger © Cengage Learning 2012 r Security+ Guide to Network Security Fundamentals, Fourth Edition 37

Malware That Profits (cont’d. ) Figure 2 -7 Information captured by a software keylogger © Cengage Learning 2012 Security+ Guide to Network Security Fundamentals, Fourth Edition 38

Social Engineering Attacks • Gathering information for an attack by relying on the weaknesses of individuals. –Relies on trusting nature of individuals • Social engineering attacks can involve psychological approaches as well as physical procedures. • Psychological approaches –mental and emotional approach rather than the physical. – Goal: persuade ﺍﻗﻨﺎﻉ the victim to provide information or take action – Flattery or flirtation ﺍﻹﻃﺮﺍﺀ ﺃﻮ ﺍﻟﻤﻐﺎﺯﻟﺔ – Friendliness Security+ Guide to Network Security Fundamentals, Fourth Edition 39

Social Engineering Attacks • In Psychological approaches attackers use a variety of techniques to gain trust without moving quickly so as to become suspicious. For example: – An attacker will not ask for too much information at one time, but instead will gather small amounts. – Slight flattery or flirtation can be helpful to “soften up” the victim to cooperate. – A smile and a simple question such as “I’m confused, can you please help me? ” or a “Thanks” can usually work. 40

Social Engineering Attacks • True example of social engineering attack – One attacker called human resources office • Asked for and got names of key employees – Small group of attackers approached door to building • Pretended to have lost key code • Let in by friendly employee • Entered another secured area in the same way – Group had learned CFO was out of town • Because of his voicemail greeting message Security+ Guide to Network Security Fundamentals, Fourth Edition 41

Social Engineering Attacks • True example of social engineering attack (cont’d. ) – – Group entered CFO’s(chief financial officer ) office Gathered information from unprotected computer Dug through trash to retrieve useful documents One member called help desk from CFO’s office • Pretended to be CFO • Asked for password urgently • Help desk gave password – Group left building with complete network access Security+ Guide to Network Security Fundamentals, Fourth Edition 42

Social Engineering Attacks (cont’d. ) • Social engineering psychological approaches often involve impersonation, phishing, spam and hoaxes. • Impersonation – Attacker pretends to be someone else • Help desk support technician • Trusted third party • Individuals in roles of authority Security+ Guide to Network Security Fundamentals, Fourth Edition 43

Social Engineering Attacks (cont’d. ) • Phishing – Sending an email claiming to be from legitimate source • May contain legitimate logos and wording – Tries to trick user into giving private information • Variations of phishing – Pharming • automatically redirects the user to the fake site. This is accomplished by attackers penetrating the servers on the Internet that direct traffic or altering a file on the host computer. Security+ Guide to Network Security Fundamentals, Fourth Edition 44

Social Engineering Attacks (cont’d. ) • Variations of phishing (cont’d. ) – Spear phishing • Whereas phishing involves sending millions of generic email messages to users, spear phishing targets only specific users. – Whaling • One type of spear phishing. Instead of going after the “smaller fish, ” targets the “big fish, ” like wealthy individuals. Security+ Guide to Network Security Fundamentals, Fourth Edition 45

Social Engineering Attacks (cont’d. ) • Variations of phishing (cont’d. ) –Vishing (voice phishing) • an attacker calls a victim who, upon answering, hears a recorded message that pretends to be from the user’s bank stating that her credit card has experienced fraudulent activity or that her bank account has had unusual activity. • The victim is instructed to call a specific phone number immediately (which has been set up by the attacker). When the victim calls, it is answered by automated instructions telling her to enter her credit card number, bank account number, Social Security number, or other information on the telephone’s 46 keypad.

Figure 2 -8 Phishing message © Cengage Learning 2012 Security+ Guide to Network Security Fundamentals, Fourth Edition 47

Social Engineering Attacks (cont’d. ) • Ways to recognize phishing messages – Deceptive ﻣﺨﺎﺩﻉ web links. Phishers like to use variations of a legitimate address, such as www. ebay_secure. com, www. e—bay. com, or www. e -baynet. com. – Logos. Phishers often include the logo of the vendor and try to make the email look like the vendor’s website. – Urgent request. Many phishing emails include an instruction for the recipient to act immediately or else. . . Security+ Guide to Network Security Fundamentals, Fourth Edition 48

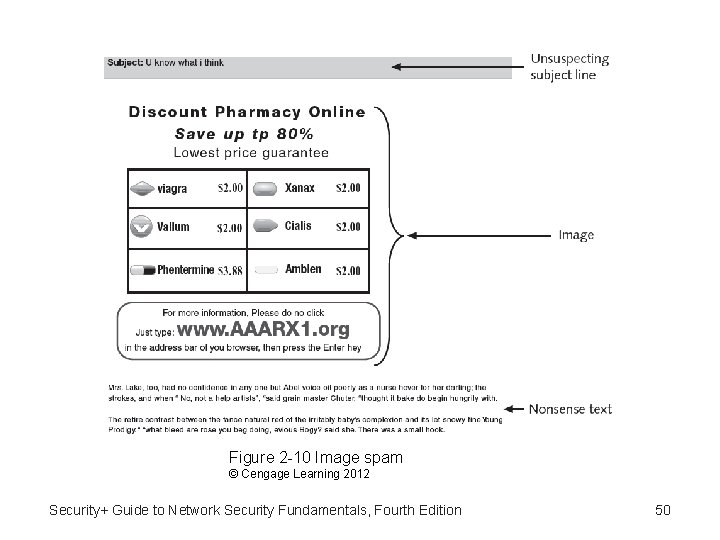
Social Engineering Attacks (cont’d. ) • Spam – Unsolicited e-mail ﺑﺮﻳﺪ ﺇﻟﻜﺘﺮﻭﻧﻲ ﻏﻴﺮ ﻣﺮﻏﻮﺏ ﻓﻴﻪ – The reason why users receive so many spam messages is because sending spam is a lucrative business ﺍﻷﻌﻤﺎﻝ ﺍﻟﻤﺮﺑﺤﺔ. It costs spammers very little to send millions of spam email messages. • Spim: targets instant messaging users instead of email users. • Image spam –Some words in text spam can easily be trapped by filters that look for these words and block the email. – Uses graphical images of text in order to Circumvents textbased filters – Often contains nonsense text so that it appears the email 49 message is legitimate

Figure 2 -10 Image spam © Cengage Learning 2012 Security+ Guide to Network Security Fundamentals, Fourth Edition 50

Social Engineering Attacks (cont’d. ) • Hoaxes – Is a false warning, often contained in an email message claiming to come from the IT department. – The hoax purports ﺗﺰﻋﻢ that there is a “deadly virus” circulating through the Internet and that the recipient should erase specific files or change security configurations, and then forward the message to other users. – However, changing configurations allow an attacker to compromise the system. Or, erasing files may make the computer unstable, prompting the victim to call the telephone number in the hoax email message for help, which is actually the phone number of the attacker. Security+ Guide to Network Security Fundamentals, Fourth Edition 51

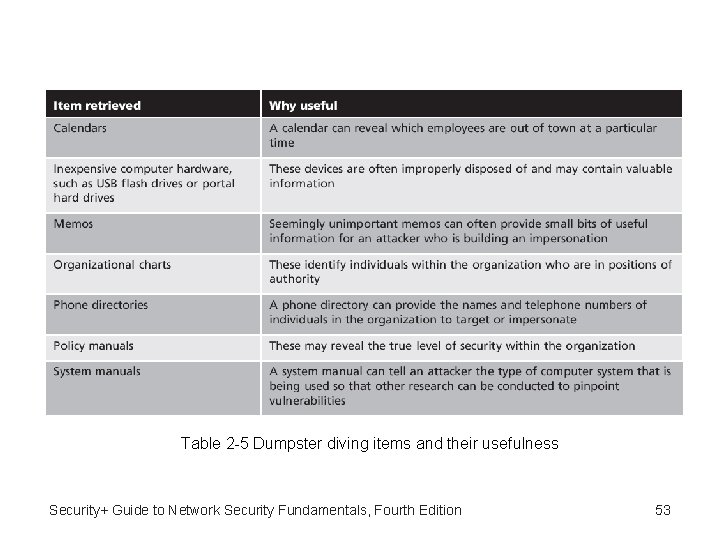
Social Engineering Attacks (cont’d. ) • Physical procedures: some social engineering attacks rely on psychological manipulation, other attacks rely on physical acts. –Dumpster diving • Digging through trash to find useful information –Tailgating • Following behind an authorized individual through an access thousands of dollars door that only permit access to authorized users who possess a special card or who can enter a specific code. 52

Table 2 -5 Dumpster diving items and their usefulness Security+ Guide to Network Security Fundamentals, Fourth Edition 53

Social Engineering Attacks (cont’d. ) • Methods of tailgating – Tailgater calls “please hold the door” – Waits outside door and enters when authorized employee leaves – Employee conspires with unauthorized person to walk together through open door • Shoulder surfing – Casually observing user entering keypad code Security+ Guide to Network Security Fundamentals, Fourth Edition 54