Security Guide to Network Security Fundamentals Fifth Edition




























- Slides: 60

Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 5 Basic Cryptography

Objectives • Define cryptography • Describe hash, symmetric, and asymmetric cryptographic algorithms • List the various ways in which cryptography is used Security+ Guide to Network Security Fundamentals, Fifth Edition 2

Introduction • Multilevel approach to information security using physical and technical security • For high-value data that must be fully protected second level of protection also should be used: encryption • If attackers penetrate the host and reach data, they still must uncover key to unlock encrypted contents: a virtually impossible task (if encryptions are properly applied) • As more data taken off-premises it becomes increasingly important to use encryption Security+ Guide to Network Security Fundamentals, Fifth Edition 3

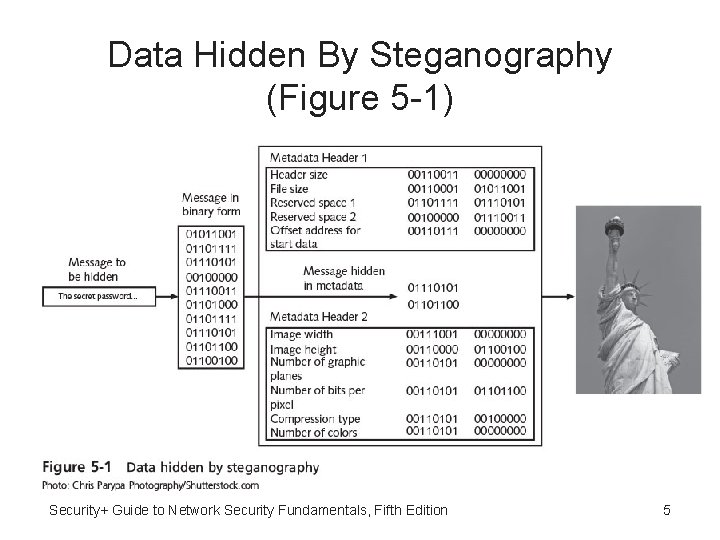
Defining Cryptography • Cryptography – Science of transforming information into secure form so that unauthorized persons cannot access it • Stenography - Hides existence of data: – Image, audio, or video files containing hidden message embedded in the file – Achieved by dividing data and hiding in unused portions of the file Security+ Guide to Network Security Fundamentals, Fifth Edition 4

Data Hidden By Steganography (Figure 5 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 5

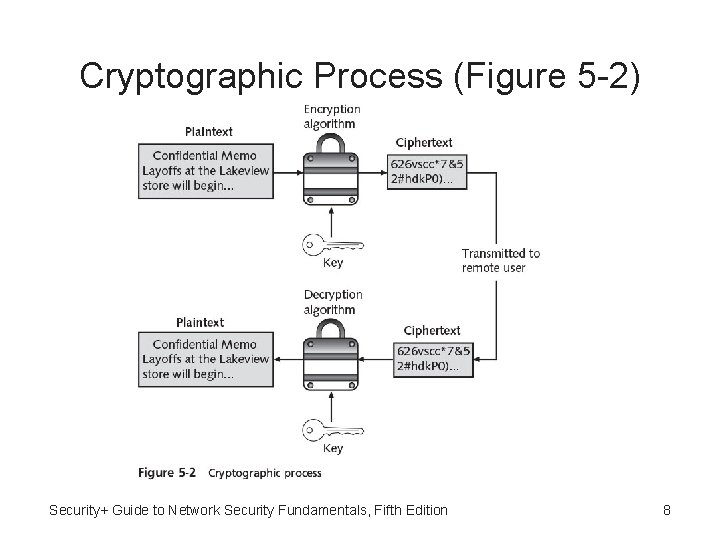
Origins of Cryptography • Origins of cryptography dates back centuries to time of Julius Caesar • Encryption - Changing original text into secret message using cryptography • Decryption - Changing secret message back to original form • Cleartext - Data in unencrypted form • Plaintext – Cleartext data to be encrypted (and is result of decryption) Security+ Guide to Network Security Fundamentals, Fifth Edition 6

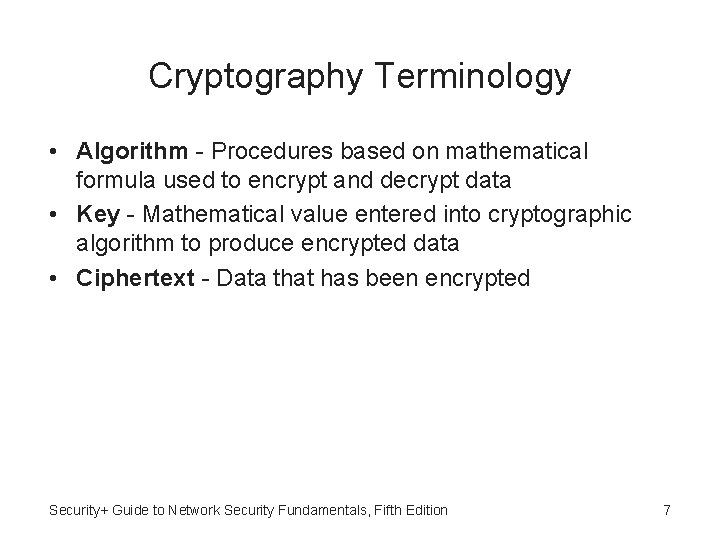
Cryptography Terminology • Algorithm - Procedures based on mathematical formula used to encrypt and decrypt data • Key - Mathematical value entered into cryptographic algorithm to produce encrypted data • Ciphertext - Data that has been encrypted Security+ Guide to Network Security Fundamentals, Fifth Edition 7

Cryptographic Process (Figure 5 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 8

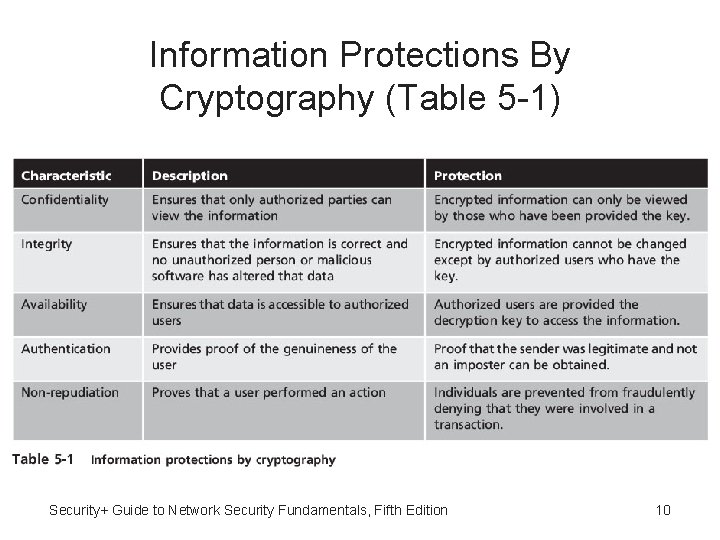
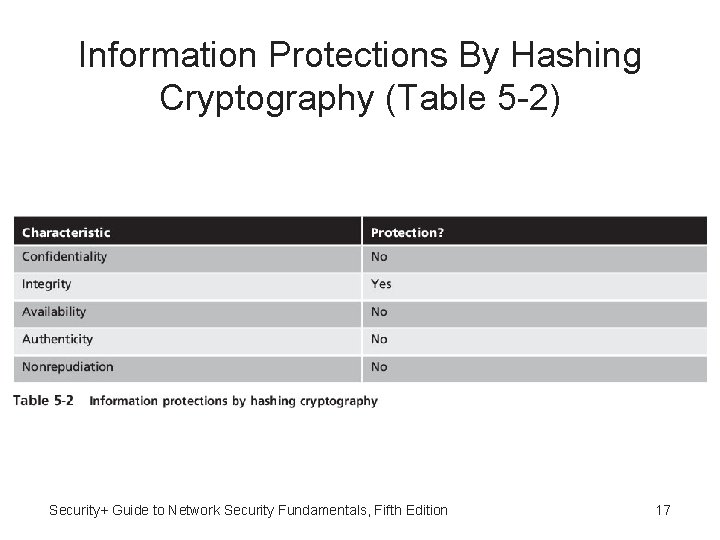
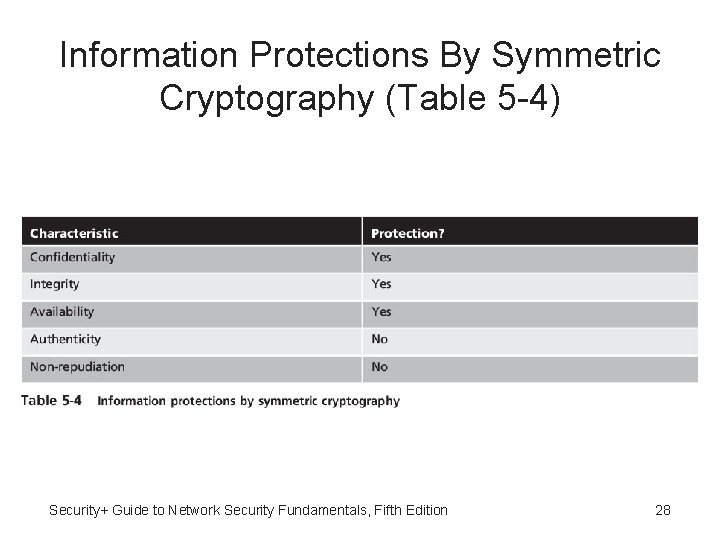
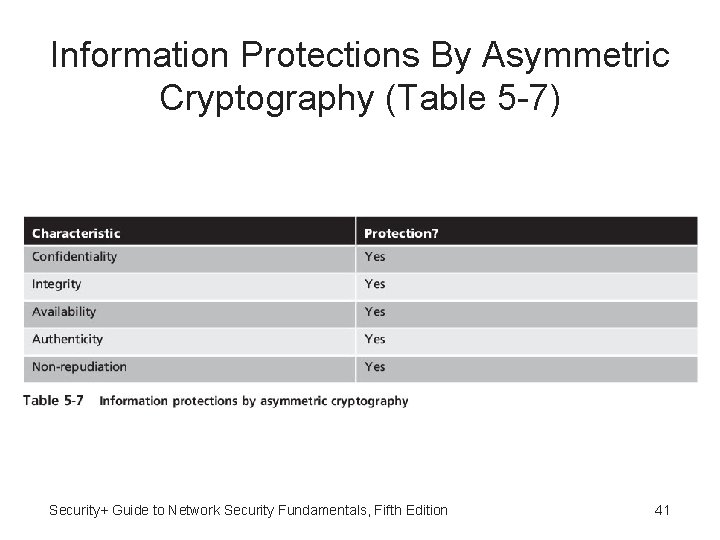
Cryptography and Security • Cryptography can provide five basic information protections: – Confidentiality - Insures only authorized parties can view it – Integrity - Insures information is correct and unaltered – Availability - Authorized users can access it – Authentication – Verify sender – Nonrepudiation - Proves that a user performed an action Security+ Guide to Network Security Fundamentals, Fifth Edition 9

Information Protections By Cryptography (Table 5 -1) Security+ Guide to Network Security Fundamentals, Fifth Edition 10

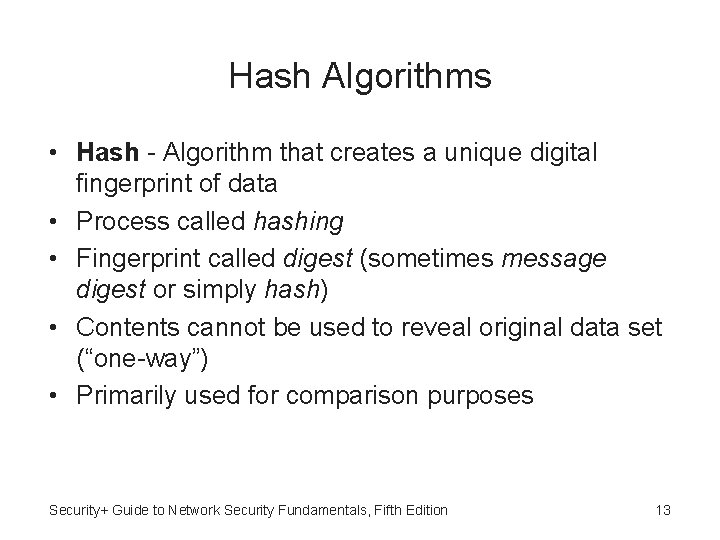
Data Processed • One of fundamental differences in cryptographic algorithms is amount of data that is processed at a time: – Stream cipher - Takes one character and replaces it with one character – Block cipher - Manipulates entire block of plaintext at one time – Sponge function - Takes as input a string of any length, and returns a string of any requested variable length Security+ Guide to Network Security Fundamentals, Fifth Edition 11

Cryptographic Algorithms • Three categories of cryptographic algorithms: – Hash algorithms – Symmetric encryption algorithms – Asymmetric encryption algorithms Security+ Guide to Network Security Fundamentals, Fifth Edition 12

Hash Algorithms • Hash - Algorithm that creates a unique digital fingerprint of data • Process called hashing • Fingerprint called digest (sometimes message digest or simply hash) • Contents cannot be used to reveal original data set (“one-way”) • Primarily used for comparison purposes Security+ Guide to Network Security Fundamentals, Fifth Edition 13

Example of Hashing • Example of hashing concept: – 12 * 34 = 408 – If user asked to determine the two numbers used to create the number 408, it would not be possible to “work backward” and derive the original numbers with absolute certainty because there are too many mathematical possibilities – 204+204, 407+1, 999‒ 591, 361+47, etc. • Hashing is similar: used to create a value, but it is not possible to determine the original set of data Security+ Guide to Network Security Fundamentals, Fifth Edition 14

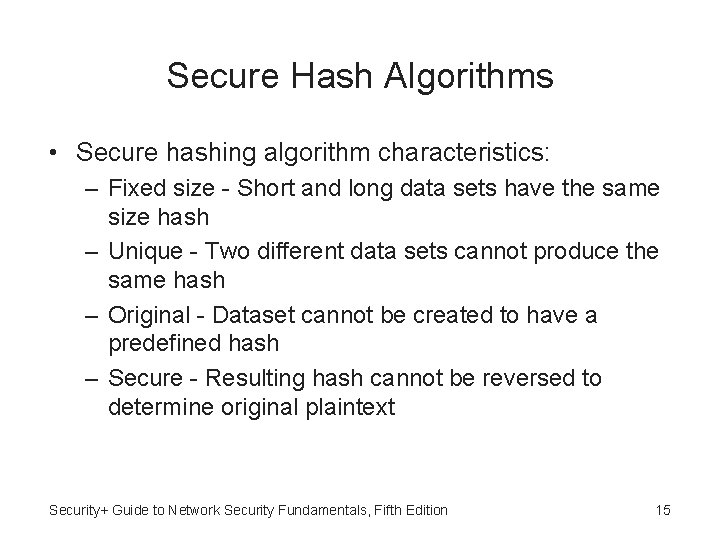
Secure Hash Algorithms • Secure hashing algorithm characteristics: – Fixed size - Short and long data sets have the same size hash – Unique - Two different data sets cannot produce the same hash – Original - Dataset cannot be created to have a predefined hash – Secure - Resulting hash cannot be reversed to determine original plaintext Security+ Guide to Network Security Fundamentals, Fifth Edition 15

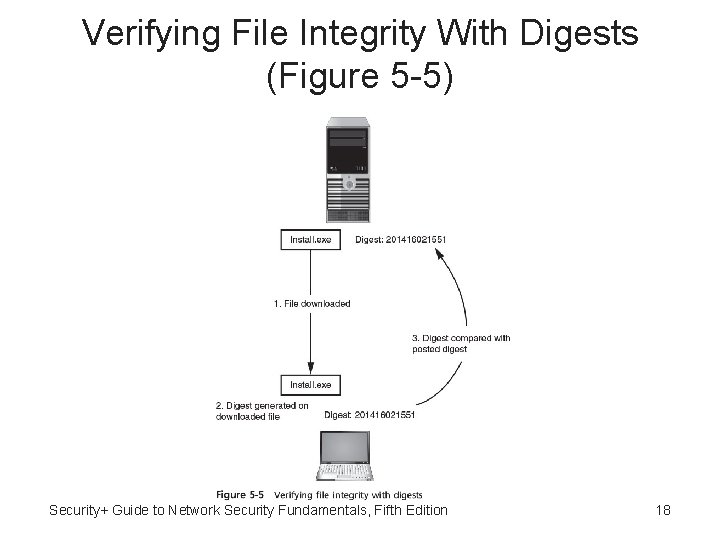
Hashed Message Authentication Code (HMAC) • Hashing used to determine message integrity (digests often posted on download sites so user can verify file integrity after download) • Hashed Message Authentication Code (HMAC) Hash variation providing improved security: – Uses secret key possessed by sender and receiver – Receiver uses key to decrypt the hash Security+ Guide to Network Security Fundamentals, Fifth Edition 16

Information Protections By Hashing Cryptography (Table 5 -2) Security+ Guide to Network Security Fundamentals, Fifth Edition 17

Verifying File Integrity With Digests (Figure 5 -5) Security+ Guide to Network Security Fundamentals, Fifth Edition 18

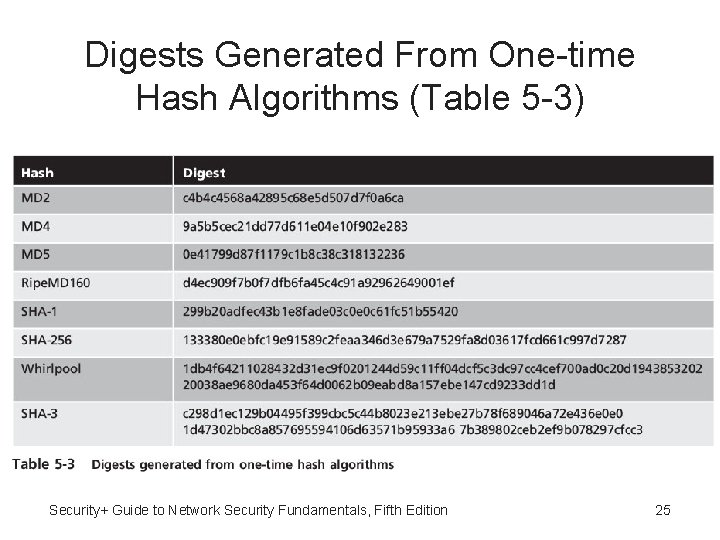
Common Hash Algorithms • Most common hash algorithms: – – Message Digest Secure Hash Algorithm Whirlpool RIPEMD Security+ Guide to Network Security Fundamentals, Fifth Edition 19

Message Digest • Message Digest (MD) – One of most common hash algorithms • Message Digest 2: – Takes plaintext of any length and creates 128 bit hash – Padding added to make short messages 128 bits – No longer considered secure • Message Digest 4 - Has flaws and was not widely accepted Security+ Guide to Network Security Fundamentals, Fifth Edition 20

Message Digest 5 • Message Digest 5: – Designed to address MD 4’s weaknesses – Message length padded to 512 bits – Weaknesses in compression function could lead to collisions – Some security experts recommend using a more secure hash algorithm Security+ Guide to Network Security Fundamentals, Fifth Edition 21

Secure Hash Algorithm (SHA) • Secure Hash Algorithm (SHA): – Family of hashes – SHA-0 – Design flaw and withdrawn – SHA-1 - Developed 1993 and patterned after MD 4 and MD 5 – SHA-2 – Six variations and considered secure – SHA-3 – Different from previous hash algorithms and approved in 2012 Security+ Guide to Network Security Fundamentals, Fifth Edition 22

Whirlpool • Whirlpool - Recent cryptographic hash • Adopted by standards organizations • Creates hash of 512 bits Security+ Guide to Network Security Fundamentals, Fifth Edition 23

RIPEMD • Race Integrity Primitives Evaluation Message Digest (RIPEMD): – Two different and parallel chains of computation – Results are combined at end of process Security+ Guide to Network Security Fundamentals, Fifth Edition 24

Digests Generated From One-time Hash Algorithms (Table 5 -3) Security+ Guide to Network Security Fundamentals, Fifth Edition 25

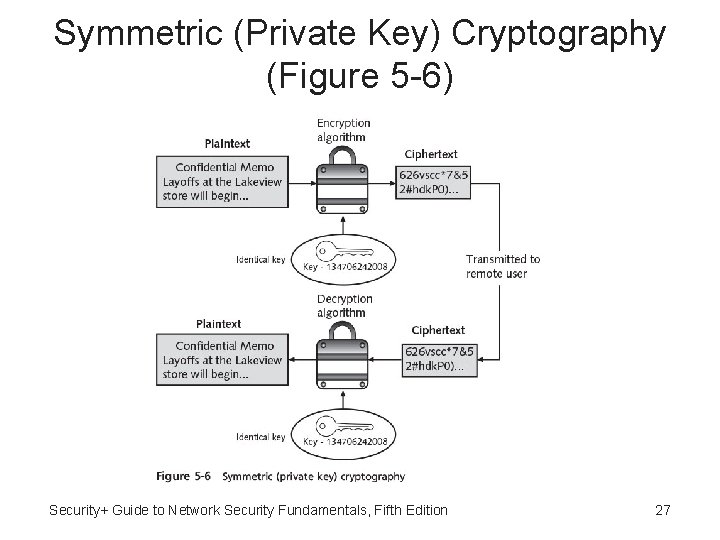
Symmetric Cryptographic Algorithms • Symmetric cryptographic algorithms - Uses same single key to encrypt and decrypt document • Unlike hashing, symmetric algorithms are designed to encrypt and decrypt the ciphertext • Data encrypted with a symmetric cryptographic algorithm will be decrypted when received • Essential that the key be kept private (confidential) • Symmetric encryption is also called private key cryptography Security+ Guide to Network Security Fundamentals, Fifth Edition 26

Symmetric (Private Key) Cryptography (Figure 5 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 27

Information Protections By Symmetric Cryptography (Table 5 -4) Security+ Guide to Network Security Fundamentals, Fifth Edition 28

Data Encryption Standard (DES) • Data Encryption Standard (DES) - One of first widely popular symmetric cryptography algorithms • Predecessor of DES was product originally designed early 1970 s by IBM called Lucifer that had key length 128 bits • Key was later shortened to 56 bits and renamed DES • Four modes of DES encryption exist • No longer considered secure Security+ Guide to Network Security Fundamentals, Fifth Edition 29

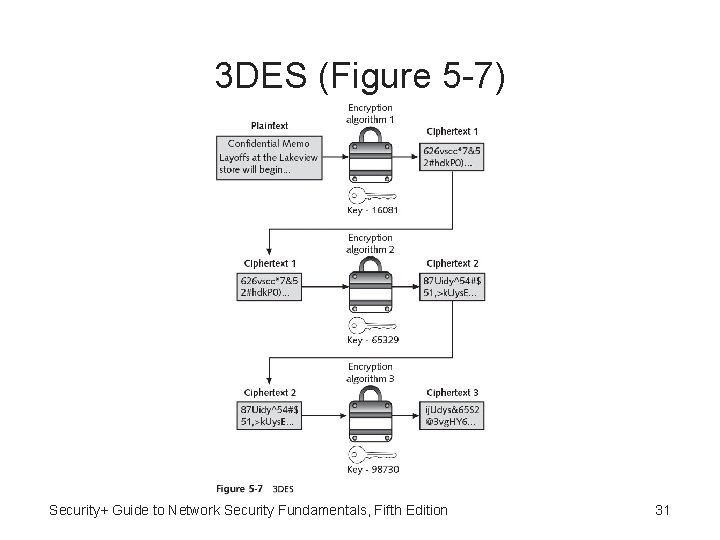
Triple Data Encryption Standard (3 DES) • Triple Data Encryption Standard (3 DES) Designed to replace DES • 3 DES uses three rounds of encryption instead of just one • Most secure versions of 3 DES use different keys for each round • Performs better in hardware than as software Security+ Guide to Network Security Fundamentals, Fifth Edition 30

3 DES (Figure 5 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 31

Advanced Encryption Standard (AES) • Advanced Encryption Standard (AES) Symmetric cipher approved as replacement for DES • AES performs three steps on every block (128 bits) of plaintext • To date, no attacks have been successful against AES Security+ Guide to Network Security Fundamentals, Fifth Edition 32

Other Symmetric Encryption Algorithms • RC 4 - Stream cipher that accepts keys up to 128 bits in length • International Data Encryption Algorithm (IDEA) Block cipher that processes 64 bits with a 128 -bit key with 8 rounds • Blowfish - Block cipher algorithm that operates on 64 -bit blocks and can have a key length from 32 to 448 bits • Twofish - Derivation of Blowfish considered to be a strong algorithm, although has not been used as widely as Blowfish Security+ Guide to Network Security Fundamentals, Fifth Edition 33

One-Time Pad (OTP) • One-time pad (OTP) - Combines plaintext with random key • Only known method to perform encryption that cannot be broken mathematically • Does not require the use of computer Security+ Guide to Network Security Fundamentals, Fifth Edition 34

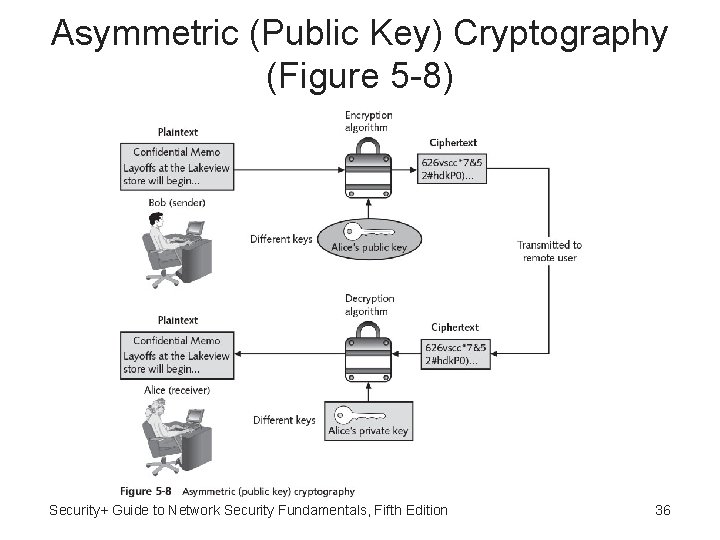
Asymmetric Cryptographic Algorithms • Weakness of symmetric algorithms: distributing and maintaining a secure single key among multiple users distributed geographically • Asymmetric cryptographic algorithms (public key cryptography) - Uses two keys instead of only one • Keys are mathematically related: – Public key - Known to everyone and can be freely distributed – Private key - Known only to the individual to whom it belongs Security+ Guide to Network Security Fundamentals, Fifth Edition 35

Asymmetric (Public Key) Cryptography (Figure 5 -8) Security+ Guide to Network Security Fundamentals, Fifth Edition 36

Asymmetric Cryptographic Algorithm Principles • Important principles – – Key pairs – Requires pair of keys Public key – Do not need to be protected Private key – Must be kept confidential Both directions - Document encrypted with public key can be decrypted with corresponding private key (and document encrypted with private key can be decrypted with public key) Security+ Guide to Network Security Fundamentals, Fifth Edition 37

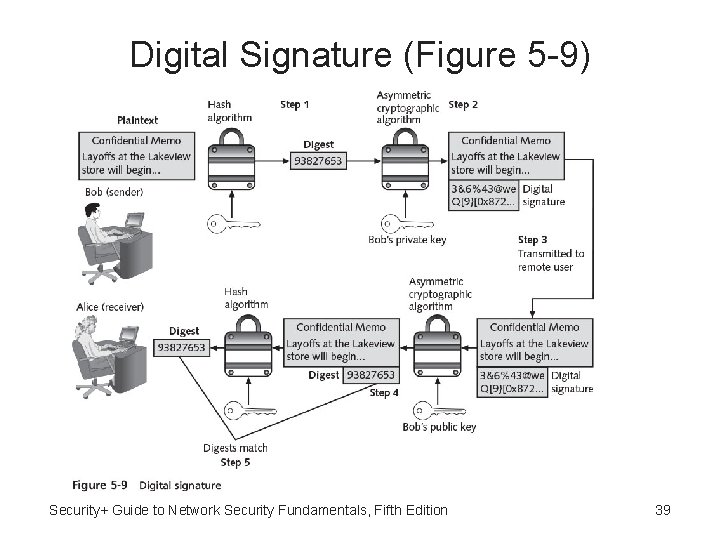
Digital Signature • Digital signature - Electronic verification of the sender: – Prevents sender from disowning the message – Proves message integrity Security+ Guide to Network Security Fundamentals, Fifth Edition 38

Digital Signature (Figure 5 -9) Security+ Guide to Network Security Fundamentals, Fifth Edition 39

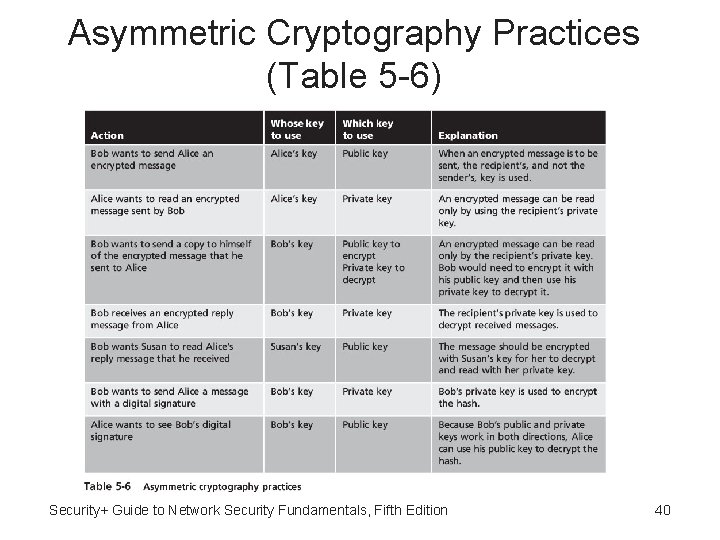
Asymmetric Cryptography Practices (Table 5 -6) Security+ Guide to Network Security Fundamentals, Fifth Edition 40

Information Protections By Asymmetric Cryptography (Table 5 -7) Security+ Guide to Network Security Fundamentals, Fifth Edition 41

RSA • RSA - Published in 1977 and patented by MIT in 1983 • Most common asymmetric cryptography algorithm • Uses two large prime numbers Security+ Guide to Network Security Fundamentals, Fifth Edition 42

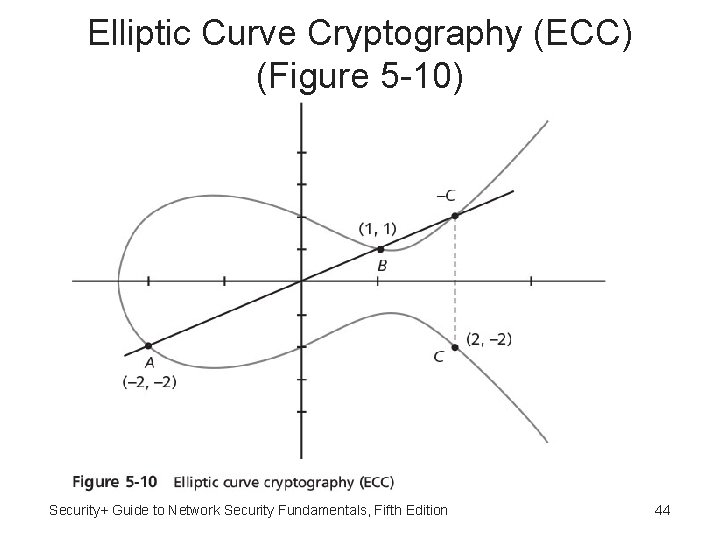
Elliptic Curve Cryptography (ECC) • Elliptic curve cryptography (ECC) - Users share one elliptic curve and one point on curve • Considered as an alternative for prime-numberbased asymmetric cryptography for mobile and wireless devices • Because mobile devices are limited in terms of computing power due to their smaller size, ECC offers security that is comparable to other asymmetric cryptography but with smaller key sizes • Can result in faster computations and lower power consumption Security+ Guide to Network Security Fundamentals, Fifth Edition 43

Elliptic Curve Cryptography (ECC) (Figure 5 -10) Security+ Guide to Network Security Fundamentals, Fifth Edition 44

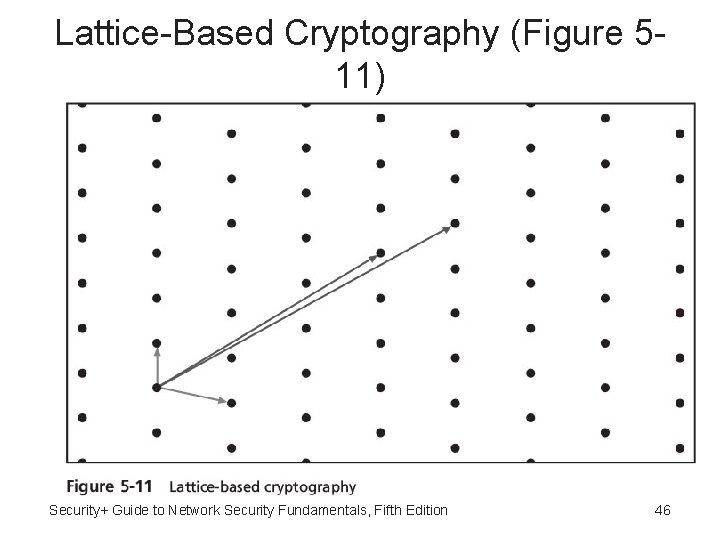
NTRUEncypt • NTRUEncypt: – – Uses lattice-based cryptography Relies on a set of points in space Faster than RSA and ECC More resistant to quantum computing attacks Security+ Guide to Network Security Fundamentals, Fifth Edition 45

Lattice-Based Cryptography (Figure 511) Security+ Guide to Network Security Fundamentals, Fifth Edition 46

Quantum Cryptography • Quantum cryptography - Exploits properties of microscopic objects such as photons • Does not depend on difficult mathematical problems Security+ Guide to Network Security Fundamentals, Fifth Edition 47

Key Exchange • Key exchange - Problem of sending and receiving keys • Out-of-band - Make the exchange outside of normal communication channels • In-band - Key exchange that occurs within normal communications channel Security+ Guide to Network Security Fundamentals, Fifth Edition 48

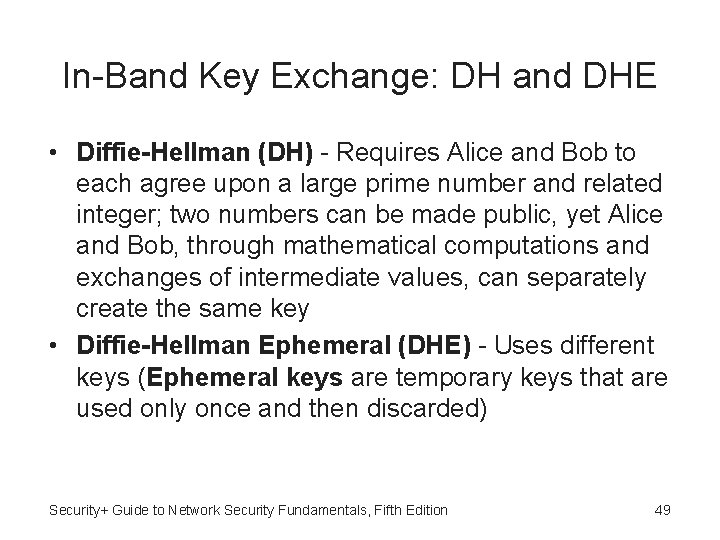
In-Band Key Exchange: DH and DHE • Diffie-Hellman (DH) - Requires Alice and Bob to each agree upon a large prime number and related integer; two numbers can be made public, yet Alice and Bob, through mathematical computations and exchanges of intermediate values, can separately create the same key • Diffie-Hellman Ephemeral (DHE) - Uses different keys (Ephemeral keys are temporary keys that are used only once and then discarded) Security+ Guide to Network Security Fundamentals, Fifth Edition 49

In-Band Key Exchange: ECDH and Perfect Forward Secrecy • Elliptic Curve Diffie–Hellman (ECDH) - Uses elliptic curve cryptography instead of prime numbers in its computation • Perfect forward secrecy - Public key systems that generate random public keys that are different for each session; value of perfect forward secrecy is that if the secret key is compromised, it cannot reveal the contents of more than one message Security+ Guide to Network Security Fundamentals, Fifth Edition 50

Using Cryptography • Cryptography: – Should be used to secure data that needs to be protected – Can be applied through either software or hardware Security+ Guide to Network Security Fundamentals, Fifth Edition 51

Encryption Through Software • File and file system cryptography - Encryption software can be applied to one or many files • Protecting groups of files based on operating system’s file system • Pretty Good Privacy (PGP): – Widely used asymmetric cryptography system – Used for files and e-mails on Windows systems • GNU Privacy Guard (GPG) - Runs on Windows, UNIX, and Linux Security+ Guide to Network Security Fundamentals, Fifth Edition 52

Microsoft Windows Encrypting File System (EFS) • Microsoft Windows Encrypting File System (EFS): – – – Cryptography system for Windows Uses NTFS file system Tightly integrated with the file system Encryption and decryption transparent to the user Users can set encryption attribute for a file in the Advanced Attributes dialog box Security+ Guide to Network Security Fundamentals, Fifth Edition 53

Whole Disk Encryption • Whole disk encryption: – Protects all data on a hard drive – Example: Bit. Locker drive encryption software Security+ Guide to Network Security Fundamentals, Fifth Edition 54

Hardware Encryption • Software encryption can be subject to attacks to exploit its vulnerabilities • Cryptography can be embedded in hardware to provide higher degree of security • Can be applied to USB devices and standard hard drives Security+ Guide to Network Security Fundamentals, Fifth Edition 55

Hardware Encryption: USB Drives • USB device encryption - Encrypted hardwarebased flash drives – Will not connect a computer until correct password has been provided – All data copied to the drive is automatically encrypted – Tamper-resistant external cases – Administrators can remotely control and track activity on the devices – Stolen drives can be remotely disabled Security+ Guide to Network Security Fundamentals, Fifth Edition 56

Hardware Encryption: HDD • Hard disk drive encryption – Self-encrypting hard disk drives protect all files stored on them – Drive and host device perform authentication process during initial power up – If authentication fails, drive can be configured to deny access or even delete encryption keys so all data is permanently unreadable Security+ Guide to Network Security Fundamentals, Fifth Edition 57

Hardware Encryption: TPM • Trusted Platform Module (TPM) – Chip on computer’s motherboard that provides cryptographic services – Includes a true random number generator – Entirely done in hardware so cannot be subject to software attack – Prevents computer from booting if files or data have been altered – Prompts for password if hard drive moved to a new computer Security+ Guide to Network Security Fundamentals, Fifth Edition 58

Hardware Encryption: HSM • Hardware Security Module (HSM) – Secure cryptographic processor – Includes onboard key generator and key storage facility – Performs accelerated symmetric and asymmetric encryption – Can provide services to multiple devices over a LAN Security+ Guide to Network Security Fundamentals, Fifth Edition 59

Security+ Guide to Network Security Fundamentals, Fifth Edition Chapter 5 Basic Cryptography