Security Governance Best Practices and Trends in State

Security Governance Best Practices and Trends in State Government Bob Smock, CISSP, CISM, PMP Vice President, Program Lead Security and Risk Management, Public Sector Gartner Consulting bob. smock@gartner. com © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. If you are authorized to access this publication, your use of it is subject to the Usage Guidelines for Gartner Services posted on gartner. com. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner's research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner's Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see " Guiding Principles on Independence and Objectivity. "
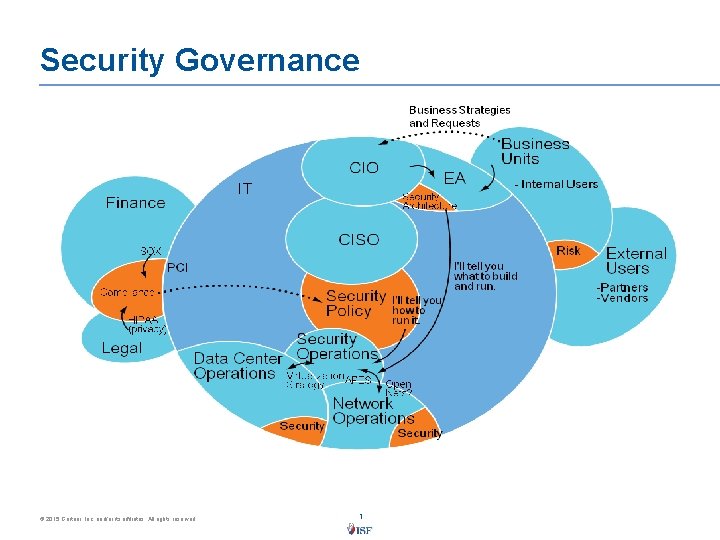
Security Governance © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. 1

What is Governance? n A theoretical concept referring to the actions and processes by which stable practices and organizations arise and persist. The term conveys the administrative and process-oriented elements of governing. [Wikipedia] n A method or system of government or management; the exercise of authority and control. [Dictionary. com] n The set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately and verifying that the enterprise’s resources are used responsibly. [IT Governance Institute] Security Governance exists to ensure that the Security Program adequately meets the strategic needs of the business. Security Management implements that Program. Security Operations executes the processes defined by that Program. © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. 2

Two Immutable Truths n Most security program failures are not technology-related; failures are due to a lack clear priorities, a lack of clear goals and objectives, and the lack of clear decision-making processes n Security programs tend to be viewed as obstacles to business, not facilitators of business © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Clients Speak Hard and Crunchy: "This is not a democracy — personnel are expected to follow organizational security policies" Soft and Chewy: "Trust but verify — approach to an open business culture" Necessary Evil: "Security should not be a disruption to the business" Important but Not Urgent: "We (security) may be boring, but we’re predictably boring" Game Philosopher: "Security is a game of inches — change does not happen overnight" Auditor Antagonist: "Compliance is not equal to security" Ostrich: "We trust IT to have good judgment" © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Objectives of Security Governance n To coordinate and control protection within the enterprise commensurate with enterprise needs n To provide consistent management through the use of cohesive policies, processes, and decision rights y it ur c se n Establish balanced and effective control of key components of business and information operations n Create the internal business conditions that allow enterprise needs to be met n Migrate away from traditional security risk management toward business risk management s bu n Transform approaches that simply meet security objectives into those that achieve business objectives Clearly delivering the right balance of protection needed for the nature of the business risk is both important to do and hard to achieve. © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. s s e in
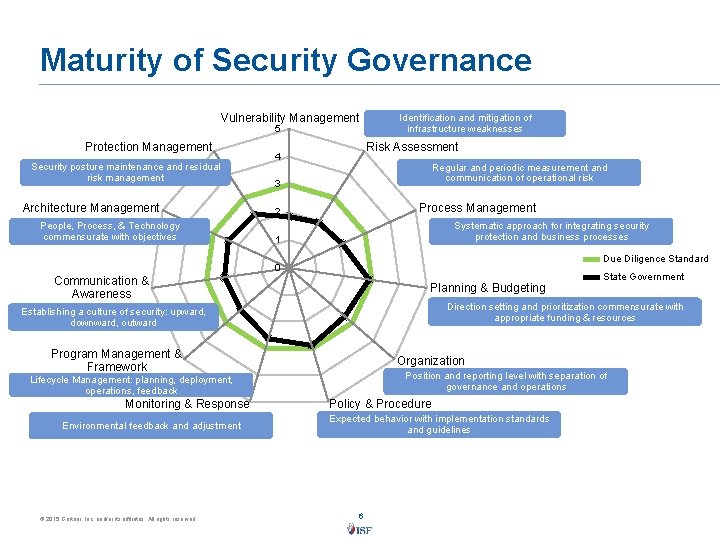
Maturity of Security Governance Vulnerability Management 5 Protection Management Security posture maintenance and residual risk management Architecture Management People, Process, & Technology commensurate with objectives Identification and mitigation of infrastructure weaknesses Risk Assessment 4 Regular and periodic measurement and communication of operational risk 3 Process Management 2 Systematic approach for integrating security protection and business processes 1 0 Communication & Awareness Planning & Budgeting Direction setting and prioritization commensurate with appropriate funding & resources Establishing a culture of security: upward, downward, outward Program Management & Framework Organization Position and reporting level with separation of governance and operations Lifecycle Management: planning, deployment, operations, feedback Monitoring & Response Environmental feedback and adjustment © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. Due Diligence Standard State Government Policy & Procedure Expected behavior with implementation standards and guidelines 6

What Do We Need To Do 1. Security Governance Goals 2. Organizational Structure 3. Rules and Rule Sources 4. The [Chief] Information Security Officer 5. Power and Influence 6. Supporting Functions and Groups 7. Funding 8. Assessment and Enforcement 9. Metrics and the Enterprise Security Control System © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. 7

The Goals of Security Governance Appropriate Examples for Goals n Meet due diligence, regulatory, and contractual requirements n Establish minimum standards for compliance n Respond to audit findings n Meet business needs for data integrity, availability, confidentiality, and accountability n Ensure ongoing utility of data and systems n React effectively to the business environ n Meet budget objectives, control costs, and manage mandatory compliance costs n Protect and manage the organization’s reputation and constituent satisfaction n Protect customer data & intellectual property n Monitor adherence to code of conduct n Protect inside from outside and inside from inside The Trends Maturity of security governance varies due to program youth, size of the organization, and limited direct leadership Security is viewed as a “business enabler” for organizations in highly regulated industries or with requirements to protect critical infrastructure ý Organizations that have not experienced a recent intrusion or malware outbreak have reduced vigilance Prevention of a data breach and potential fines for compliance failure motivates organizations Near-term security plans are made on an annual basis ý Failing to address strategic security planning which considers a 2 to 4 year horizon Governance councils are important to formulate interactions between centralized and decentralized functions © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Organizational Structure Best Practices n The structure of the enterprise must be reflected in the structure of the security governance program n An independent structure for the security program is necessary to its function. n Other enterprise governance councils provide a forum for security to provide input on risk n Mergers can result in cultures that need different approaches n Governance is about controlling organizational behavior; this is accomplished by applying change strategies to organizational structures The Trends Infosec overwhelmingly still belongs to IT Leadership — At least one full time enterprise ISO; missing matrixed decentralized ISO ý Reporting — More than one level removed from senior staff ý Lack of separation between governance and operations ý Staffing — Insufficient resources; security team size varies based on part-time functions, extent of operational involvement, and availability of necessary skills Skills and certifications requirements growing but not always recognized ý Lacking coordination – Operational managers should coordinate via a security leadership council Centralized security works with de-centralized resources to coordinate on programs and standards © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Rules and Rule Sources Best Practices n n Rules for governance come from regulatory and corporate drivers They also come from industry standards for due diligence and appropriate behavior Policies, standards, and processes are put in place to create the environment that fosters appropriate behavior The overall governance process is rarely successful without a systematic application of a set of governance rules The Trends ý Failure to map controls to security objectives ý Failure to establish a "minimum standard" or "best practices" approach to controls. Leverage NIST or other frameworks as a source for control standards ý Failure to leverage frameworks such as ISO and ITIL as a program management benchmark for consistency ý No security policies defined as strategic to the enterprise ý Security policies not integrated with overall enterprise policies ý Lacking comprehensive standards and guidelines to define acceptable implementations of policy There a variety of control frameworks in use with mapping of internal standards (often involving ISO 27000 or NIST) © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

The ISO Best Practices n Exists to run the enterprise information protection function n Has visibility in senior oversight/governance councils n The critical decision of where the function should be placed in the org hierarchy is directly related to how important information and security are to the business n The need for direct communication about key issues to top management should be seriously considered in placement n Rarely owns or leads senior management review of enterprise business risk n Uses a mix of relationship-based ad hoc contacts and regularly scheduled crossorganization committee meetings The Trends ý Rule of thumb: Successful security programs are run by strong characters; less successful programs flounder because of the weakness of the ISO; influence, not edict, is the key tool ý Establish a security management framework; all feedback is assimilated into the framework ý The Security Management Plan (SMP) — Describes the overall security program and provides foundational guidance Generally not responsible for defining privacy policies, business continuity, and IT disaster recovery, but may be involved in execution Typically provides baselines, templates or standards to leverage and build on. v The CISO should not be placed below other top management because of the need to mitigate insider threats at the highest levels of the enterprise and not be subject to undue internal political influence A role to "influence and inform" business decision makers and build relationships with people that can influence change © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Funding Best Practices n n n n The Trends ý Security groups are required to reduce costs due to unrecognized business impact/value Organizations with strong regulatory pressure or high potential impact of data breaches are Funding includes personnel, operations and not cutting security spending maintenance, and security-specific projects ý Hiring restrictions, staff cuts, and low retention About half of funding is for personnel create trade-offs with just being able to do what These numbers increase during program is required development, compliance efforts, and for high ý Investment in security awareness programs assurance situations remains unrecognized as a priority to mitigate Much of the true cost of security is hidden due security risks in the face of deep cuts or leveled to accounting processes, indirect influence on funding business operations, mounting requirements, ý Security-specific funding is rarely identified as legal costs, etc. a separate "line item" in the enterprise budget The costs associated with incidents and their resolutions are typically very hard to quantify However, the funding influenced or indirectly controlled by security typically ranges from 5% to 10% of total IT expenditures … as are those with consequences that were NOT incurred because of the effectiveness of security Security organizations continue to be reduced and cost-constrained as stand-alone functions © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Metrics and Enterprise Control Best Practices The Trends Organizations vary in the focus of their metrics programs as does the maturity of metrics programs Effective control implies meaningful Moving toward greater automation in metrics measurement and reporting with accuracy programs. "Meaningful" means costs, consequences, and ý Tie enterprise key risk indicator (KRI) metrics effectiveness to business key performance metrics (KPI). Establish metrics as meaningful and achievable ý Effective KRI metrics expands beyond by measuring progress over time relative to monitoring typical security vulnerabilities standards ý Results of risk assessments and audits are an Risk and threat metrics tend to be subjective important metric — demonstrates continuous and hard to quantify improvement; Metrics used as a performance improvement Data breach metrics get assigned a dollar cost. objective are highly visible and effective Transition from tactical risk metrics from point ý Technical metrics are tracked and reported but solutions to strategic risk metrics from the are usually the least useful security architecture (people, process, ý Security still need methods to measure technology) success; it remains difficult to demonstrate security's value to business or overall effectiveness of security programs n Feedback must be acquired in a form that can be applied to make corrections n n n Security metrics programs are immature but becoming more common and seeking more useful and higher quality metrics © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Pick-7 Key Points Review 1. Communicate: Establish a security program that identifies, measures, and communicates the dangers and reasons for security initiatives and employee vigilance while allowing for exceptions and acceptance of business risk under specific conditions 2. Influence: For ISO’s, collaboration, communication, and credibility are a must; influence, not edict, is the key tool 3. Lead: Security leadership needs participation in enterprise risk management process with senior management 4. Coordinate: Regular forums for coordination between security and other department and business unit stakeholders to cultivate credibility and influence 5. Culture: Use accepted standards and frameworks, then modify to suit the needs of the organizational culture 6. Invest: When budgets are tight or cut, focus available investments on security awareness and building the business case for projects when funding improves 7. Value: Track and report metrics as indicators of the effectiveness of protections as well as the value of security, not simply vulnerabilities mitigated Progressive organizations are building effective security governance focused on good communication and collaboration practices, and a philosophy of helping others understand manage risk © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Q&A What are the pros and cons of your security governance structure? © 2015 Gartner, Inc. and/or its affiliates. All rights reserved.

Security Governance Best Practices and Trends in State Government Bob Smock, CISSP, CISM, PMP Vice President, Program Lead Security and Risk Management, Public Sector Gartner Consulting bob. smock@gartner. com © 2015 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. If you are authorized to access this publication, your use of it is subject to the Usage Guidelines for Gartner Services posted on gartner. com. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner's research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner's Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see " Guiding Principles on Independence and Objectivity. "
- Slides: 17