Security for Project Management Professionals National Industrial Security




















- Slides: 33

Security for Project Management Professionals National Industrial Security Program SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 1

Purpose The purpose of this briefing is to provide Project Management Professionals and others engaged in project management with an overview of the National Industrial Security Program (NISP). The goal of any industrial security program is the protection of classified information. Physical safeguards are important in this effort – but just as important – is the education of those entrusted with the safeguarding of classified information. Policies and procedures tells us what and how to do something, but we also need to understand WHY things are done a certain way. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 2

What you will learn At the end of this briefing the Project Management Professional will: • Have an understanding of the National Industrial Security Program (NISP) and the Operating Manual (NISPOM) • Become familiar with the requirements imposed by the Contract Security Classification Specification (DD Form 254) • Have an understanding of the difference in requirements between those stated in Section H of the contract and those imposed by the DD 254. • How do we get the people with the right clearances in the right positions in a timely manner. • Become familiar with Joint Personnel Adjudication System (JPAS) and requirements for Visit Authorization Letters / Requests. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 3

What is a facility (in NISPOM-speak)? The solicitation states that the company must have an active TOP SECRET facility clearance at time of award. In NISPOM-speak, this means that the company awarded a contract must have gone through a vetting process with the Department of Defense (or other Cognizant Security Agency – DNI; DOE and NRC*) based upon a valid contractual need to access classified information. NOTE: The NISPOM is applicable to ALL executive branch departments and agencies. Once this process is favorably completed the company is granted a “Facility Clearance” (FCL) at the level required by contract (generally SECRET or TOP SECRET). For our purposes, this information is then entered into the Industrial Security Facilities Database together with the company CAGE code; location of the company and Facility Security Officer (FSO) information. This would be an industrial security version of the Central Contractor Registration (CCR). * Director of National Intelligence (DNI); Department of Energy (DOE); Nuclear Regulatory Commission (NRC) SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 4

FCL Level v. Storage Authorization The solicitation states that the company must have classified storage authorized for classified information up to the SECRET level. The fact the we have a TOP SECRET Facilities Clearance (FCL) covers us – right? Actually, NO! Having a TS FCL means that the company may enter into contracts and have access to classified material at a level up to an including TS. It may also employee “cleared” personnel for that purpose. The storage, processing, safekeeping, manufacturing, etc. , of classified material and information is a separate process. In order to be authorized classified storage, the cleared company must demonstrate they have sufficient safeguards (physical, personnel, procedural, etc. ) in place prior to receiving authorization and have a contractually based NEED for maintaining classified information on-site. In this case, the company would need authorization to store and process SECRET material SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 5

As a PM, where do I find security related information in the contract? For the FSO the only source of information is the DD 254 (Contract Security Classification Specification). In most cases though – at the time of solicitation a DD 254 will not be available. So your sources are: Section H of the solicitation / contract will normally have general information regarding security requirements: type of personnel clearance required; type facility clearance required; IT access requirements; policies regarding access to facilities, etc. The Statement of Work (SOW) will also have general requirements – hopefully specific to the position being filled or the security access required for a particular location. Generally one or both of these documents will also let us know if we need approval of the government to subcontract – and if so, do we need approval of the government security group to subcontract security requirements. (Mandatory for Department of State; FBI and some Naval activities) SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 6

The DD 254 – Why is this so important? As a PM, you understand that without a contract in place, work does not start, people don’t get paid and invoices don’t get submitted. The contract includes all of the specifications needed to be met. The DD 254 is a part of that contract – just as the statement of work; your proposal; invoicing instructions, etc. The Government Contracting Activity (GCA) is responsible for incorporating appropriate security requirements clauses in a classified contract, Invitation for Bid (IFB), Request for Proposal (RFP), Request for Quotation (RFQ), or other solicitation, and for providing the contractor with the security classification guidance needed during the performance of the contract. This guidance is provided to the contractor by the Contract Security Classification Specification. The Contract Security Classification Specification must identify the specific elements of classified information involved in the contract that require security protection. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 7

DD 254 v. Section H or SOW Typical Section H / SOW Security Requirements: Contractor must have a TS FCL and provide personnel with access authorized to TS or TS/SCI level. Normally just a paragraph or two. The DD 254 can range from 2 to ? ? pages depending on the contract. It tells us (or at least should tell us): • Basic Requirements (See follow on slides) • Who has security cognizance. • If SCI, COMSEC, or other, specific guidance • Who the Security POC is on site; for the contract and how visit requests will be managed. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 8

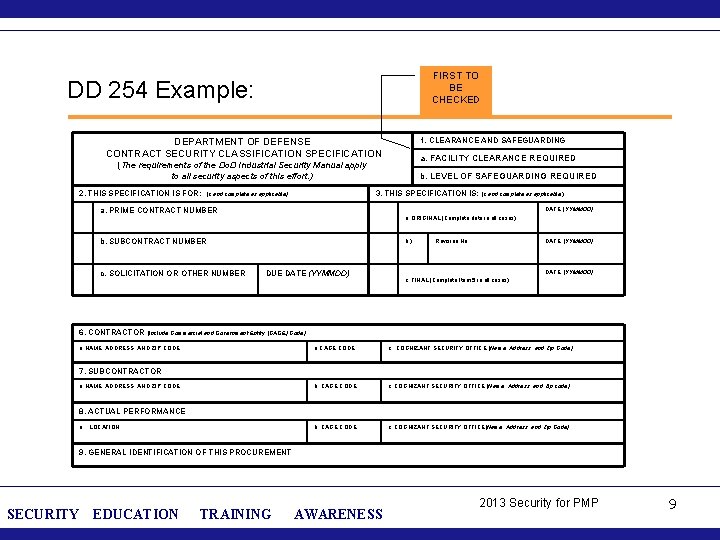
FIRST TO BE CHECKED DD 254 Example: 1. CLEARANCE AND SAFEGUARDING DEPARTMENT OF DEFENSE CONTRACT SECURITY CLASSIFICATION SPECIFICATION a. FACILITY CLEARANCE REQUIRED (The requirements of the Do. D Industrial Security Manual apply to all security aspects of this effort. ) b. LEVEL OF SAFEGUARDING REQUIRED 2. THIS SPECIFICATION IS FOR: 3. THIS SPECIFICATION IS: (x and complete as applicable) DATE (YYMMDD) a. PRIME CONTRACT NUMBER a. ORIGINAL (Complete date in all cases) b. SUBCONTRACT NUMBER c. SOLICITATION OR OTHER NUMBER (x and complete as applicable) DUE DATE (YYMMDD) Revision No. DATE (YYMMDD) c. FINAL (Complete Item 5 in all cases) 6. CONTRACTOR (Include Commercial and Government Entity (CAGE) Code) a. NAME, ADDRESS, AND ZIP CODE a. CAGE CODE c. . COGNIZANT SECURITY OFFICE (Name, Address, and Zip Code) b. CAGE CODE c. COGNIZANT SECURITY OFFICE (Name, Address, and Zip code) b. CAGE CODE c. COGNIZANT SECURITY OFFICE(Name, Address, and Zip Code) 7. SUBCONTRACTOR a. NAME, ADDRESS, AND ZIP CODE 8. ACTUAL PERFORMANCE a. LOCATION 9. GENERAL IDENTIFICATION OF THIS PROCUREMENT SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 9

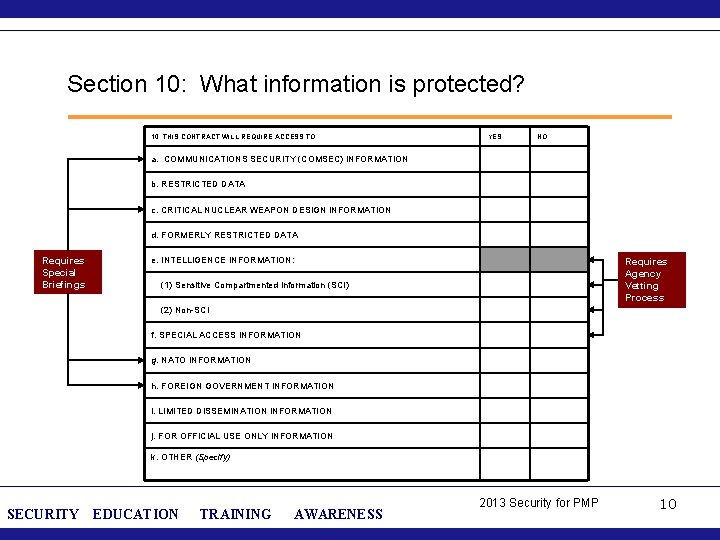
Section 10: What information is protected? 10. THIS CONTRACT WILL REQUIRE ACCESS TO: YES NO a. COMMUNICATIONS SECURITY (COMSEC) INFORMATION b. RESTRICTED DATA c. CRITICAL NUCLEAR WEAPON DESIGN INFORMATION d. FORMERLY RESTRICTED DATA Requires Special Briefings e. INTELLIGENCE INFORMATION: Requires Agency Vetting Process (1) Sensitive Compartmented information (SCI) (2) Non-SCI f. SPECIAL ACCESS INFORMATION g. NATO INFORMATION h. FOREIGN GOVERNMENT INFORMATION i. LIMITED DISSEMINATION INFORMATION j. FOR OFFICIAL USE ONLY INFORMATION k. OTHER (Specify) SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 10

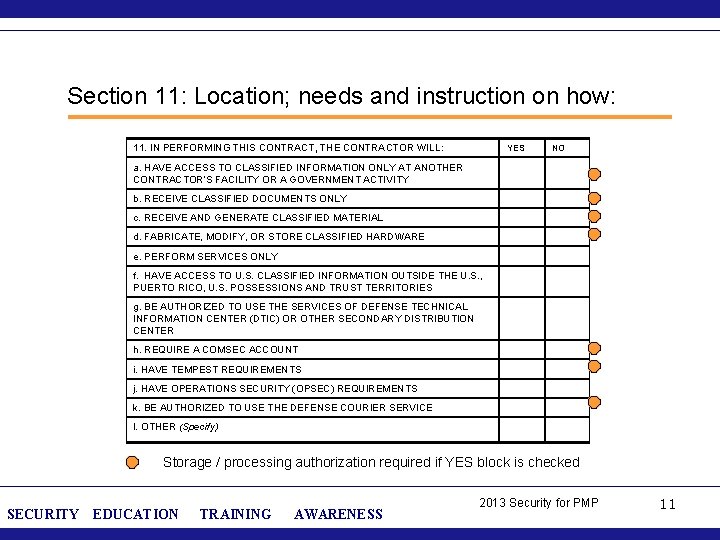
Section 11: Location; needs and instruction on how: 11. IN PERFORMING THIS CONTRACT, THE CONTRACTOR WILL: YES NO a. HAVE ACCESS TO CLASSIFIED INFORMATION ONLY AT ANOTHER CONTRACTOR’S FACILITY OR A GOVERNMENT ACTIVITY b. RECEIVE CLASSIFIED DOCUMENTS ONLY c. RECEIVE AND GENERATE CLASSIFIED MATERIAL d. FABRICATE, MODIFY, OR STORE CLASSIFIED HARDWARE e. PERFORM SERVICES ONLY f. HAVE ACCESS TO U. S. CLASSIFIED INFORMATION OUTSIDE THE U. S. , PUERTO RICO, U. S. POSSESSIONS AND TRUST TERRITORIES g. BE AUTHORIZED TO USE THE SERVICES OF DEFENSE TECHNICAL INFORMATION CENTER (DTIC) OR OTHER SECONDARY DISTRIBUTION CENTER h. REQUIRE A COMSEC ACCOUNT i. HAVE TEMPEST REQUIREMENTS j. HAVE OPERATIONS SECURITY (OPSEC) REQUIREMENTS k. BE AUTHORIZED TO USE THE DEFENSE COURIER SERVICE l. OTHER (Specify) Storage / processing authorization required if YES block is checked SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 11

DD 254 – Reverse and Continuation Pages 12. PUBLIC RELEASE. Any information (classified or unclassified) pertaining to this contract shall not be released for public dissemination except as provided by the i. NISPOM or unless it has been approved for public release by appropriate U. S. Government authority. Proposed public releases shall be submitted for approval prior to release Direct Through (Specify): IN ALMOST ALL INSTANCES PUBLIC RELEASE WILL NOT BE AUTHORIZED to the Directorate for Freedom of Information and Security Review, Office of the Assistant Secretary of Defense (Public Affairs)* for review. *In the case of non-Do. D User Agencies, requests for disclosure shall be submitted to that agency. 13. SECURITY GUIDANCE. The security classification guidance needed for this classified effort is identified below. If any difficulty is encountered in applying this guidance or if any other contributing factor indicates a need for changes in this guidance, the contractor is authorized and encouraged to provide recommended changes; to challenge the guidance or the classification assigned to any information or material furnished or generated under this contract; and to submit any questions for interpretation of this guidance to the official identified below. Pending final decision, the information involved shall be handled and protected at the highest level of classification assigned or recommended. (Fill in as appropriate for the classified effort. Attach, or forward under separate correspondence, any documents/guides/extracts referenced herein. Add additional pages as needed to provide complete guidance. ) This section will contain (or should contain) detailed information on what is being protected; how it must be protected; the types of information; specific instructions, Security Points of Conduct, etc. Typical continuation pages and attachments: Refer to Annex A for instructions regarding SCI Information Refer to Annex B for instructions on non-SCI intelligence information Refer to Annex C for instructions on handing Controlled Unclassified Information (CUI); Sensitive But Unclassified (SBU) information; For Official Use Only (FOUO Information). Refer to Annex D for information regarding COMSEC instructions Refer to Annex E for information regarding access to NATO information. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 12

A Special Note about SCI This contract states that everyone must be cleared to the TS/SCI level or be SCI eligible. What is SCI and what is the difference between TS/SCI and “eligible? ” There are only three levels of classified information: TOP SECRET (TS); SECRET (S) and CONFIDENTIAL (C). SCI implements tighter safeguards for some TS information. SCI refers to Sensitive Compartmented Information and the DNI is the proponent for SCI access for the federal government. To have access to SCI, the agency holding that information (FBI; Do. D; CIA; DOJ) will conduct a separate background investigation before you may be granted access. The individual may be asked to undergo a polygraph – generally limited to National Security matters. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 13

Who’s a SAP? One part of this project is referred to as a Special Access Program (SAP) and information is considered Special Access Required (SAR). As mentioned, there are only three levels of classified information: TS; S and C. SAPs are the responsibility of the CSA – and require special oversight by the CSA. They may be acknowledged or unacknowledged. As is the case with SCI information – additional safeguards and requirements are applied prior to granting access. Consider secret programs used for the development of weapons systems – or information regarding a Delta classified operations mission; or the intelligence platform added to that new Gulfstream that can find a penny in your pocket. These are all types of Special Access Programs. There will be additional safeguards – some physical; some personnel security and dependent upon the program – the guy down the hall will have no idea what you are working on. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 14

Billets The DD 254 in my case states that we have been provided four (4) “billets. ” What is a billet? For SAP and some SCI programs, a set number of people may have access to part or all of the information within that program. These are referred to as billets – or positions. In this case, no more than four individuals may be read on to the program and provide support to the program at any one time. A person leaves – the replacement must be nominated and accepted by the agency before access is granted. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 15

IT Access Levels I, II or III We have an IT Services support contract pending. The SOW states that some personnel will require IT Level I access while others require levels II or III. This is not a classified contract. What’s this all about? Vulnerability. That’s what it is all about. Where is our system most vulnerable; who could be the biggest threat to the system and what can we do to protect the system or network from compromise or damage? If you think about the financial industry – none of their information is classified information by National Security standards. Yet, protections imposed on access to financial systems, networks, transactions, etc. are super tight. Generally – the government will identify the AIS level of the system which sets the stage for who can get access. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 16

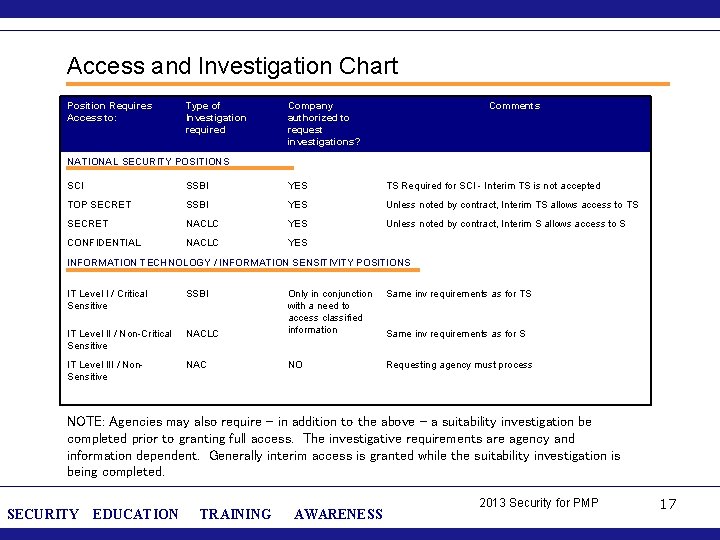
Access and Investigation Chart Position Requires Access to: Type of Investigation required Company authorized to request investigations? Comments NATIONAL SECURITY POSITIONS SCI SSBI YES TS Required for SCI - Interim TS is not accepted TOP SECRET SSBI YES Unless noted by contract, Interim TS allows access to TS SECRET NACLC YES Unless noted by contract, Interim S allows access to S CONFIDENTIAL NACLC YES INFORMATION TECHNOLOGY / INFORMATION SENSITIVITY POSITIONS IT Level I / Critical Sensitive SSBI Same inv requirements as for TS NACLC Only in conjunction with a need to access classified information IT Level II / Non-Critical Sensitive IT Level III / Non. Sensitive NAC NO Requesting agency must process Same inv requirements as for S NOTE: Agencies may also require – in addition to the above – a suitability investigation be completed prior to granting full access. The investigative requirements are agency and information dependent. Generally interim access is granted while the suitability investigation is being completed. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 17

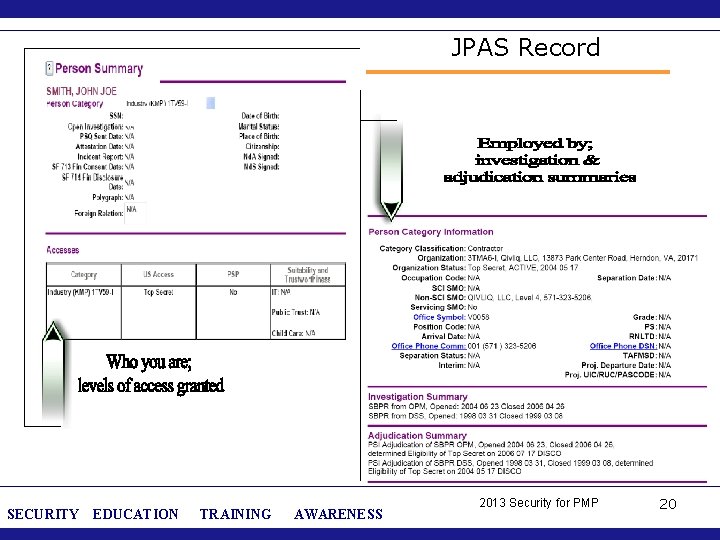
The Joint Personnel Adjudication System (JPAS) JPAS is the system of record for personnel clearances within the Department of Defense and its contractors. If our company has a classified contract with DOD and most federal agencies – they require us to submit a JPAS record. If “it ain’t in JPAS – then it ain’t” WHAT IT DOES DO: • Displays all relevant information regarding background investigation and adjudication dates. • Displays the association between an individual and a company • Displays what access the person has been granted. Displays any special accesses – NATO, Nuclear, etc. • Allows for Visit Requests to be submitted electronically. WHAT IT DOES NOT DO: • Does not link with other agency databases (Scattered Castles). • Does not track “favorable” access determinations (no access to classified) • Does not allow contractors to initiate SF 85 for suitability determinations. . SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 18

Clearance Processing Have a new employee with no • HR provides completed security clearance? Requires questionnaire to Security. Upon access to Secret? receipt, applicant is added to JPAS and If all is well with his investigation request is initiated under e. QIP submitted on the contract number provided. (1 Day) Monday – your • Applicant completes e. QIP and employee can be submits to FSO. (up to applicant – sitting at your client’s after 90 days – start over) desk with an Interim • FSO reviews and either returns for Secret on Wed or correction or submits to DSS for Thu at the latest! TOP SECRET processing. (1 day) • DSS grants Interim SECRET clearance and submits e. QIP to OPM for investigation. (3 days) • Investigation completed. (Many variables – generally 6 - 12 months) • Investigation completed. (Many variables – generally 3 to 6 months) • DSS adjudicates investigation and grants final TOP SECRET clearance (within 30 days) • DSS adjudicates investigation and grants final SECRET clearance (within 30 days) SECURITY EDUCATION TRAINING AWARENESS A Tip 4 U! Make all hiring agreements contingent upon the applicant being able to obtain and hold on to eligibility to access classified. 2013 Security for PMP 19

JPAS Record SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 20

Visit requests OK – the contract is in place; we have hired the right person with the right clearance. Now, how do we get our employee on site? We are required to show a contractual relationship between the government and our company and a link between the person and our company. This is generally managed through the submission of a Visit Authorization Letter (or Visit Request) – prepared by the company security staff and submitted to the government client’s security staff. With the development of JPAS – this can be done electronically if the government client is a user of JPAS. If not, a hard copy letter (on company letterhead) is submitted via fax. Data included in the letter: • Contract Number; Security POC at agency; Project POC at Agency; Period of visit. • Employees Full Name; DOB; POB; SSN • Employee background investigation data; access granted and indoctrination. • Company CAGE; FCL; Date Granted and information concerning the Cognizant Security Office. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 21

Subcontractor Responsibilities Are security requirements passed down to subcontractors? How do we know they are cleared? If not cleared can they get cleared? If the subcontractor is required to have access to classified information, then YES, the security requirements will be passed down to that company. This is accomplished via a Sub-Contractor DD 254 – which is prepared by the company and signed by the FSO – which is then submitted to the sub. The Sub-Contractor is responsible for the security program for its own employees and will submit visit requests based on our DD 254. In order to issue the subcontractor DD 254, the following must be provided to security: • A copy of the sub-contract signed by both the company and the subcontractor. • Period of performance. We will then verify the subcontractor’s FCL in the ISFD, prepare and issue the DD 254. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 22

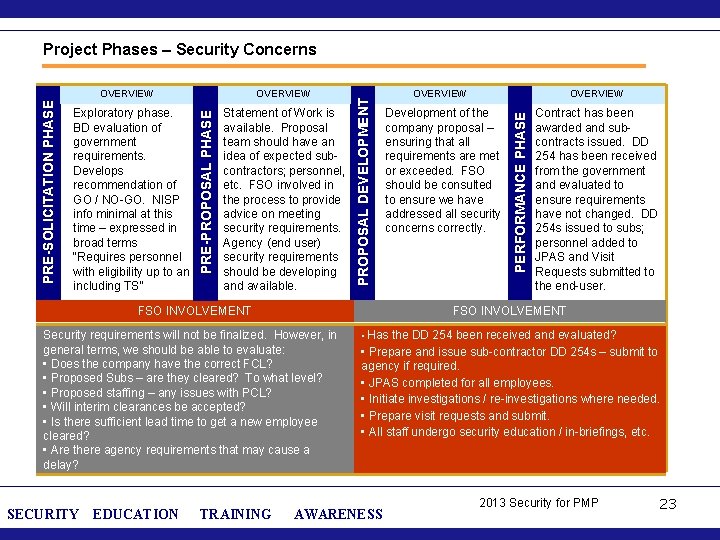
Statement of Work is available. Proposal team should have an idea of expected subcontractors; personnel, etc. FSO involved in the process to provide advice on meeting security requirements. Agency (end user) security requirements should be developing and available. FSO INVOLVEMENT EDUCATION TRAINING OVERVIEW Development of the company proposal – ensuring that all requirements are met or exceeded. FSO should be consulted to ensure we have addressed all security concerns correctly. Contract has been awarded and subcontracts issued. DD 254 has been received from the government and evaluated to ensure requirements have not changed. DD 254 s issued to subs; personnel added to JPAS and Visit Requests submitted to the end-user. FSO INVOLVEMENT Security requirements will not be finalized. However, in general terms, we should be able to evaluate: • Does the company have the correct FCL? • Proposed Subs – are they cleared? To what level? • Proposed staffing – any issues with PCL? • Will interim clearances be accepted? • Is there sufficient lead time to get a new employee cleared? • Are there agency requirements that may cause a delay? SECURITY OVERVIEW PERFORMANCE PHASE Exploratory phase. BD evaluation of government requirements. Develops recommendation of GO / NO-GO. NISP info minimal at this time – expressed in broad terms “Requires personnel with eligibility up to an including TS” OVERVIEW PRE-PROPOSAL PHASE PRE-SOLICITATION PHASE OVERVIEW PROPOSAL DEVELOPMENT Project Phases – Security Concerns • Has the DD 254 been received and evaluated? • Prepare and issue sub-contractor DD 254 s – submit to agency if required. • JPAS completed for all employees. • Initiate investigations / re-investigations where needed. • Prepare visit requests and submit. • All staff undergo security education / in-briefings, etc. AWARENESS 2013 Security for PMP 23

Required Reports The reality is that life happens. Sometimes what does happen may have an adverse affect on the ability of an individual to maintain a clearance. In some situations, the conduct of an employee brings his ability to maintain a clearance into question. We are required to report certain matters – like it or not – regardless of the government client’s decisions. TO THE FBI: TO THE CSA: actual, probable or possible • espionage, • sabotage, • terrorism, or • subversive activities at any of its (contractor) locations. Employee Status • Adverse information concerning a cleared employee • Suspicious contacts • Change in status: Name; citizenship; marital status; termination • Refusal of a cleared employee to work on classified contracts • Refusal to sign the SF 312 (Non-Disclosure Agreement) Company Status • Change of name; address; ownership • Change in Key management Personnel • Change in FOCI Status (Foreign Ownership, Control , Influence) • For possessing companies, any change in the ability to properly safeguard classified information SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 24

Targeting US Technologies SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 25

The Threat – Economic & Industrial Espionage Due to foreign policy considerations and the need to protect sources, the U. S. Government does not publicly name the countries that are most active in conducting espionage against the United States. However, several European and Asian countries have stated openly that their national intelligence services collect economic intelligence to benefit their industries at the expense of foreign competition. Considerable information on this subject is available in public sources. What Are They After? It would be nice to know exactly what classified, proprietary or other sensitive information foreign countries are trying to collect, so that we could then concentrate on protecting that information which is most at risk. Unfortunately, waiting for that kind of specific information before taking appropriate security measures would usually mean locking the barn door after the horses have left. March 7, 2008: a Reston, VA company, pleads guilty in federal court to illegally exporting "controlled power amplifiers, " which have military applications SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 26

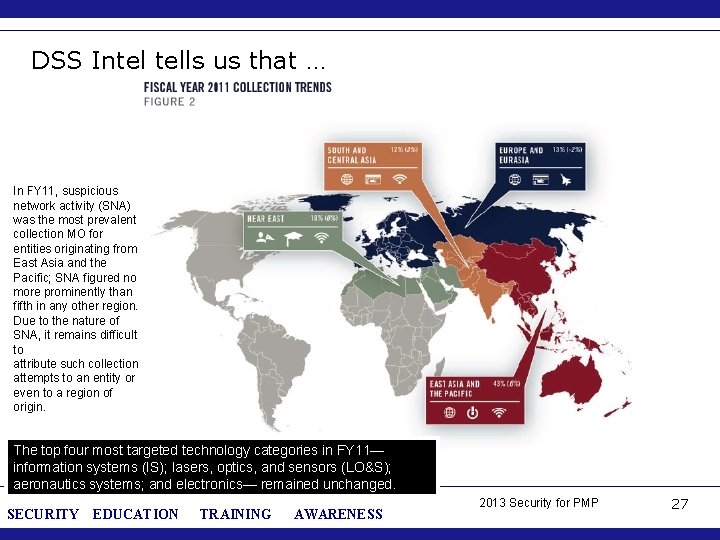
DSS Intel tells us that … In FY 11, suspicious network activity (SNA) was the most prevalent collection MO for entities originating from East Asia and the Pacific; SNA figured no more prominently than fifth in any other region. Due to the nature of SNA, it remains difficult to attribute such collection attempts to an entity or even to a region of origin. The top four most targeted technology categories in FY 11— information systems (IS); lasers, optics, and sensors (LO&S); aeronautics systems; and electronics— remained unchanged. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 27

SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 28

DSS Tells Us that … • Technologies resident in U. S. cleared industry remain highly sought after. Foreign intelligence entities (FIEs) continue to expand their collection networks and activities. These networks are growing like a malignant vine. • This ongoing theft—FIEs’ pilfering of U. S. technologies from cleared industry—could reduce or even end advantages in military capabilities the United States possesses over potential adversaries, thereby adversely affecting U. S. battlefield dominance. It also could strangle U. S economic growth, vitiating the nation’s economic health. • The overall number of reports submitted by cleared industry to the Defense Security Service (DSS) in FY 11 increased by nearly 65 percent over FY 10, and the number that actually became suspicious contact reports (SCRs) increased by 75 percent, likely due in large part to increased awareness and reporting by industry. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 29

The Threat – Economic & Industrial Espionage Foreign governments’ continued ability to acquire state-of-the-art U. S. technology at little or no expense has undermined U. S. national security by enabling foreign firms to push aside U. S. businesses in the marketplace and by eroding the U. S. military lead. A clear line must be drawn to protect information that is: • classified, or • subject to export controls because it concerns militarily critical technologies, or • proprietary information that is the intellectual property of a specific firm or individual. March 24, 2008: a former engineer at a naval contractor, is sentenced to 24 1/2 years in prison for conspiring to export warship technology. Aug. 1, 2007: Engineer pleads guilty to violating the Economic Espionage Act to benefit China's Navy Research Center. He exported source code for simulation software for the precision training of fighter pilots. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 30

“Globalization and growing economic interdependence, while creating new levels of wealth and opportunity, also create a web of interrelated vulnerabilities and spread risks even further… Department of Defense National Defense Strategy July, 2008 SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 31

Let us not forget who we support. Information concerning troop rotations, locations, equipment; and technology is classified for a reason. Unauthorized release of this information can have a detrimental effect on the Warfighters’ survivability. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 32

This concludes the briefing for Project Management Professionals. If you have questions, please do not hesitate to contact us. SECURITY EDUCATION TRAINING AWARENESS 2013 Security for PMP 33