Security flaws in Windows XP due to Kernel








- Slides: 13

Security flaws in Windows XP due to Kernel Complexity Presented by: Zubin Lalani Daniel Beech Professor : Mike Burmester

Presentation Outline • Windows Vs Linux Kernel Organization • Windows Security Model • Security Flaws in Windows • Microsoft Future plans for security

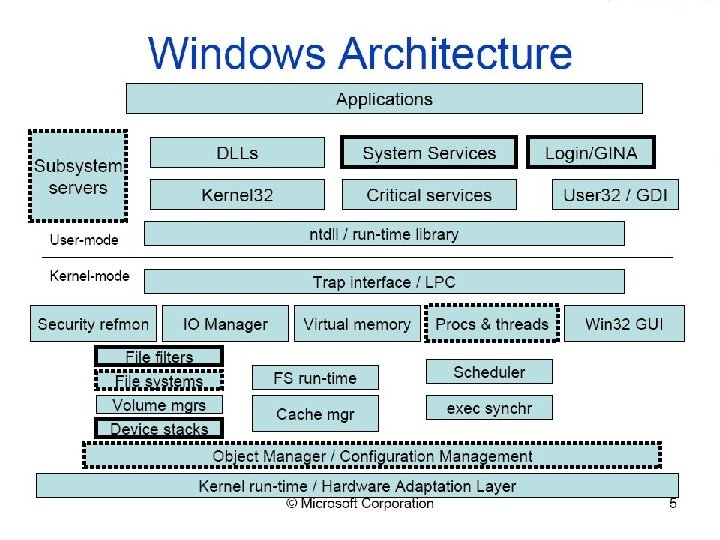
Windows Kernel Organization • Originally designed as stand alone “offline” system • Over 3000 + System calls • Supports over 4000 distinct system configuration • Over 50 million lines of code • 600 million Windows copies (figures of July 2004) • Windows 2000 supports more than 7, 000 devices

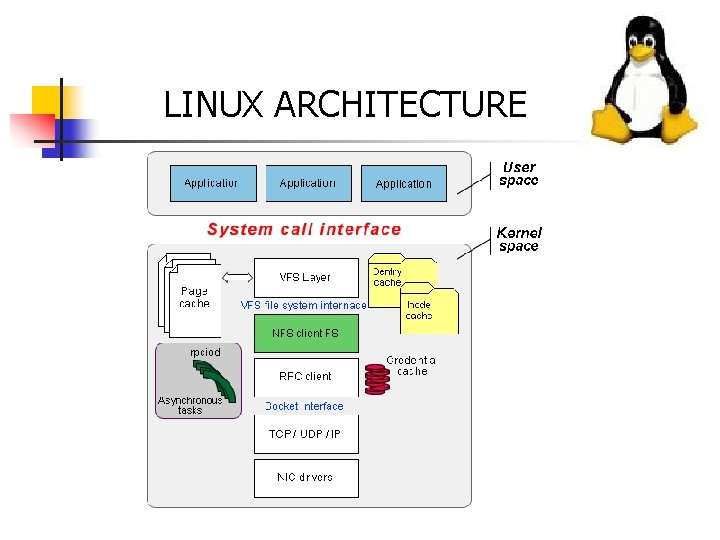
Linux Kernel Organization • Less than 255 system calls for linux • Linux 2. 6 has not more than 4 million phyiscal line of code • Approximate 18 million users • Lack of distinct hardware support

Kernel Organization Kernel-mode organized into NTOS (kernel-mode services) –Run-time Library, Scheduling, Executive services, object manager, services for I/O, memory, processes, … Hal (hardware-adaptation layer) –Insulates NTOS & drivers from hardware dependencies –Providers facilities, such as device access, timers, interrupt servicing, clocks, spinlocks

LINUX ARCHITECTURE

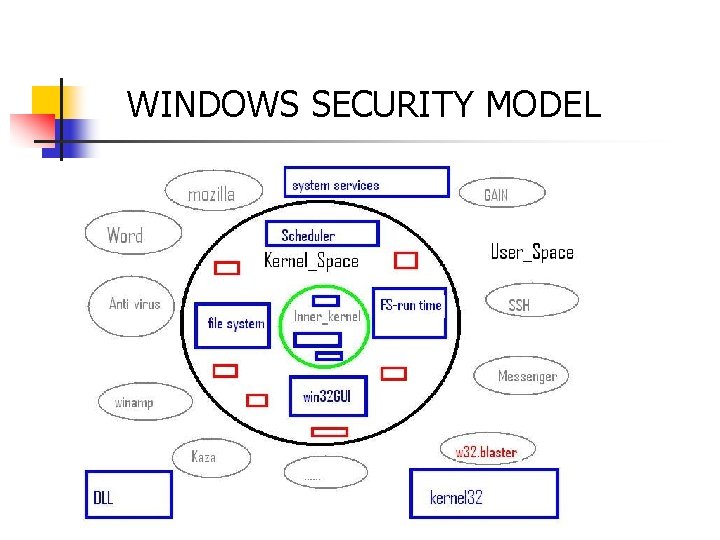
Windows Security Model … • Security Model based on securable objects • Based on per-object rights – “Generic read, write and execute” • Model Involves following concepts : • Security Identifiers • Access Tokens • Security Descriptors • Access Control Lists and Privileges

WINDOWS SECURITY MODEL

FAMOUS FLAWS … • Mellissa Virus Forced Microsoft to completely turn off their email system Started to affect in March 1999 More than $80 million • I Love You Virus Affected May 2000 Brought down www. skyinet. net, deleted. mp 3 and. jpg files and mails to every contact in microsoft Outlook $1 Billion financial loss in North America alone and more than $2. 5 in total Affected more than 600000 computer

FAMOUS FLAWS • Code Red The economic cost more than $2 billion Was so powerful that it forced White House to change its numerical IP address and prompted the Pentagon to takes its website offline • Blaster Worm $500 million or more estimate in Financial loss 16 million or more system fell victim Exploited the DCOM(Distributed component object Model) vulnerability Happened in August 2003

LATEST SECURITY THREATS • SPYWARE Not a virus but a complete program Tracks internet habits and nags you with advertisment About 2/3 rd personal computers are infected How it works? - Piggybacked software installation, Drive-by download, Browser add-ons, Masquerading as anti-spy ware

FUTURE PLANS Include Windows Anti Spy-ware Technology Improvements in Windows Update Site “Singularity” prototype OS - said to be Very Secure

Biblography • http: //www. acmqueue. org/modules. php? name=Content&pa=showpage&pid=159&page=5 • http: //archives. cnn. com/2001/TECH/internet/08/08/code. red. II/ • http: //computer. howstuffworks. com/virus 4. htm • http: //www. exn. ca/nerds/virus. cfm • http: //www. legalelite. com/articles/a-kpasich-0500 -iloveyoubug. htm • http: //news. com/2100 -1001 -240304. html? legacy=cnet • http: //users. dot. net. au/~rick/ms/culp. html • http: //www. microsoft. com