Security Encryption and Management Brian Murgatroyd Chairman TETRA

Security Encryption and Management Brian Murgatroyd Chairman: TETRA Association Security and Fraud Prevention Group

Agenda Ø Security threats Ø TETRA security features Ø Overall system security measures Ø Air interface security functions Ø End to end encryption Ø Interoperability and practical security measures 13 th June 2006 TETRA Experience - Poland

Security Threats ØWhat are the main threats to your system? ØConfidentiality? ØAvailability? ØIntegrity? 13 th June 2006 TETRA Experience - Poland
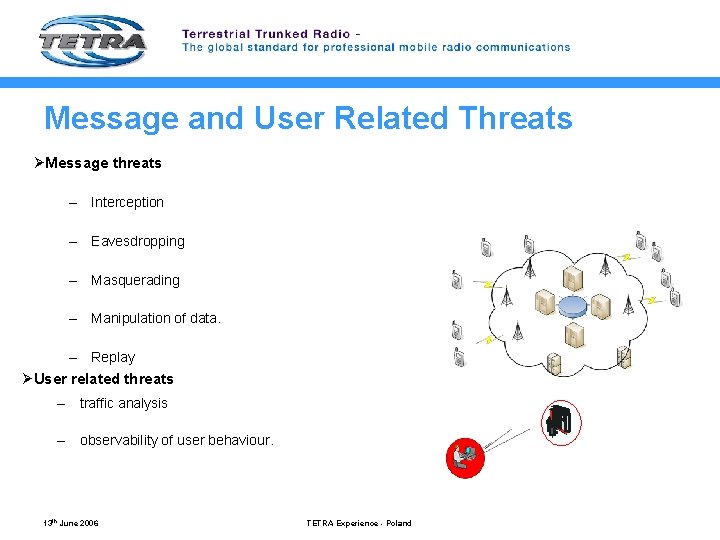
Message and User Related Threats ØMessage threats – Interception – Eavesdropping – Masquerading – Manipulation of data. – Replay ØUser related threats – traffic analysis – observability of user behaviour. 13 th June 2006 TETRA Experience - Poland
System Related Threats ØDenial of service – Jamming – Attacks via the IP network to switch off the functional boxes – Natural disasters • fire, flood, earthquake 13 th June 2006 TETRA Experience - Poland • ,
Overall TETRA Security Ø Several aspects to TETRA security – – 13 th June 2006 Technical security countermeasures Secure Network Management and procedure Lawful Interception Standard algorithms TETRA Experience - Poland
Network Security ØIT security is vital in TETRA networks ØGateways are particularly vulnerable. ØOperating staff need vetting ØFirewalls required at access points to the network 13 th June 2006 TETRA Experience - Poland
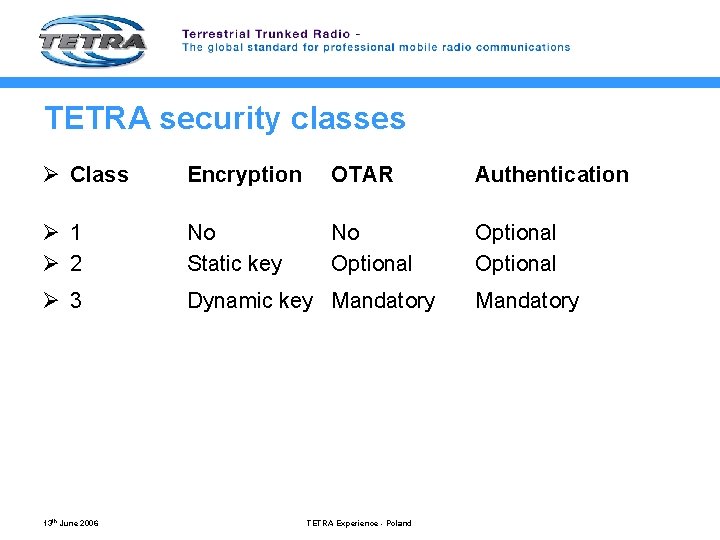
TETRA security classes Ø Class Encryption OTAR Authentication Ø 1 Ø 2 No Static key No Optional Ø 3 Dynamic key Mandatory 13 th June 2006 TETRA Experience - Poland Mandatory
Authentication Ø Used to ensure that terminal is genuine and allowed on network. Ø Mutual authentication ensures that in addition to verifying the terminal, the Sw. MI can be trusted. Ø Authentication requires both Sw. MI and terminal have proof of secret key. Ø Successful authentication permits further security related functions to be downloaded. 13 th June 2006 TETRA Experience - Poland
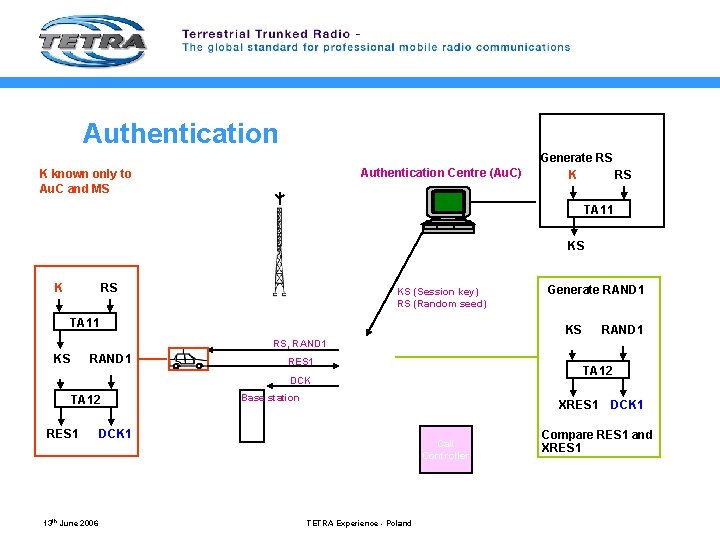
Authentication Centre (Au. C) K known only to Au. C and MS Generate RS K RS TA 11 KS K RS KS (Session key) RS (Random seed) TA 11 Generate RAND 1 KS RAND 1 RS, RAND 1 KS RAND 1 RES 1 TA 12 DCK TA 12 RES 1 13 th June 2006 Base station XRES 1 DCK 1 Call Controller TETRA Experience - Poland DCK 1 Compare RES 1 and XRES 1

Provisioning of authentication keys Ø Every terminal has a unique secret key (k) which has to be manually loaded to the terminal normally by the manufacturer Ø k associated with the TEI and sent to the network provider Ø Needs to be done securely and to the SFPG recommendation 01 file format Ø User organization provides the ISSI-TEI which it sends to the network provider Ø K-ISSI pairs in the authentication centre can be formed 13 th June 2006 TETRA Experience - Poland
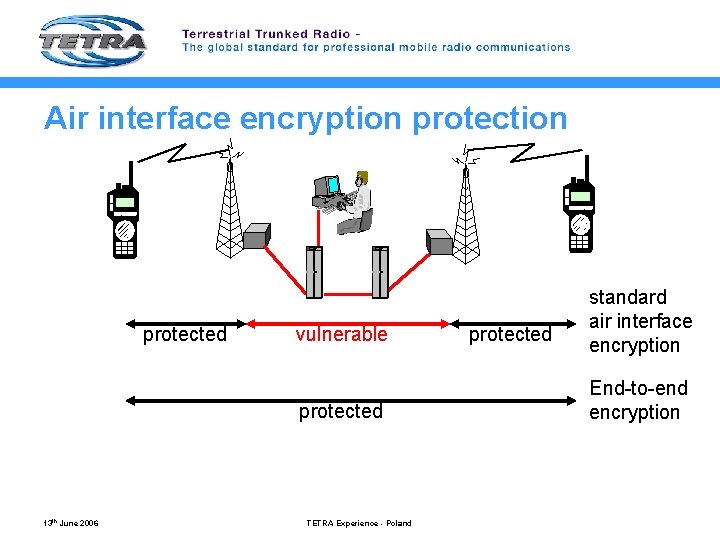
Air interface encryption protected vulnerable protected 13 th June 2006 TETRA Experience - Poland protected standard air interface encryption End-to-end encryption
Air interface encryption Ø As well as protecting voice, SDS and packet data transmissions: – AI encryption protects control channel messages as well as voice and data payloads – encrypted registration protects identities and gives anonymity – Protection against replay attacks using an initialization vector derived form system timing (frame numbering) 13 th June 2006 TETRA Experience - Poland

Over The Air Re-keying (OTAR) Ø Populations of terminals tend to be large and the only practical way to change encryption keys is by OTAR Ø This is done securely by using a derived cipher key or a session key to wrap the downloaded key Ø The security functionality is transparent to the user as the network provider would normally be responsible for OTAR and management of AI keys 13 th June 2006 TETRA Experience - Poland
Air Interface traffic keys Ø Four traffic keys are used in class 3 systems: Ø Derived cipher Key (DCK) – derived from authentication process used for protecting uplink, one to one calls Ø Common Cipher Key(CCK) – protects downlink group calls and ITSI on initial registration Ø Group Cipher Key(GCK) – Provides crypto separation, combined with CCK Ø Static Cipher Key(SCK) – Used for protecting DMO and TMO fallback mode 13 th June 2006 TETRA Experience - Poland

Disabling of terminals Ø Vital to ensure the reduction of risk of threats to system by stolen and lost terminals Ø Relies on the integrity of the users to report losses quickly and accurately. Ø Disabling may be either temporary or permanent Ø Disabling stops the terminal working as a radio and: – Permanent disabling removes all keys including (k) – Temporary disabling removes all traffic keys but allows ambience listening Ø The network or application must be able to remember disable commands to terminals that are not live on the network at the time of the original command being sent. 13 th June 2006 TETRA Experience - Poland

Standard air interface algorithms Ø TEA 1 and TEA 4 – Generally exportable outside Europe. Designed for non public safety use Ø TEA 2 – Only for use in Europe for public safety and military organizations. Strictly export controlled Ø TEA 3 – For use by public safety and military organizations where TEA 2 is not allowed. Strictly export controlled 13 th June 2006 TETRA Experience - Poland

Transfer of security parameters between networks Ø The authentication parameters (based on k) are very sensitive and should never be sent to a visited network Ø The way forward is to provide a set of parameters that will only be used in the visited network Ø WG 6 are working on a revision to the standard to accommodate practical security functionality across an ISI 13 th June 2006 TETRA Experience - Poland

Evaluation of security mechanisms Ø How can a system be judged secure? – – – 13 th June 2006 Evaluate threats and risks, independently if possible Ensure correct implementation of security Ensure mobile terminals have been evaluated Use standard encryption algorithms Regular audit and inspection TETRA Experience - Poland
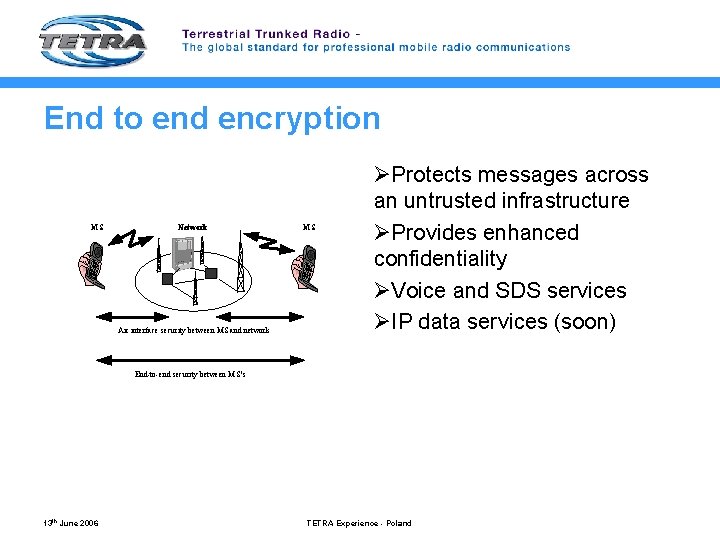
End to end encryption MS Network Air interface security between MS and network MS ØProtects messages across an untrusted infrastructure ØProvides enhanced confidentiality ØVoice and SDS services ØIP data services (soon) End-to-end security between MS’s 13 th June 2006 TETRA Experience - Poland

Benefits of end to end encryption in combination with Air Interface encryption Ø Air interface (AI) encryption alone and end to end encryption alone both have their limitations Ø For most users AI security measures are completely adequate Ø Where either the network is untrusted, or the data is extremely sensitive then end to end encryption may be used in addition as a overlay. Ø Brings the benefit of encrypting addresses and signalling as well as user data across the Air Interface and confidentiality right across the network 13 th June 2006 TETRA Experience - Poland
Standard end to end encryption algorithms Ø There are no ‘standard’ algorithms defined by SFPG but: Ø IDEA was defined as a good candidate 64 bit block cipher algorithm for use with TETRA and test data and an example implementation was produced Ø AES 128 (Rijndael) was defined as a good candidate 128 bit block cipher algorithm for use with TETRA and test data and an example implementation was produced Ø Both algorithms have proved popular with public safety organizations and give a good level of security assurance to sensitive data 13 th June 2006 TETRA Experience - Poland
Export control of crypto material Ø All cryptographic material and terminals capable of encryption are subject to export control Ø The authority has to be satisfied that the key length and algorithms used are allowed to be exported. Ø Guidance is given in the Wassenaar arrangement www. wassenaar. org but the export control authority must be approached in all cases 13 th June 2006 TETRA Experience - Poland

Lawful interception Ø In most countries public telecoms systems are subject to lawful interception by the security authorities Ø TETRA provides a standard interface to allow this functionality Ø Operators need to check with their security authorities whether their system needs to be equipped with this interface 13 th June 2006 TETRA Experience - Poland
Question Ø What would be the main reason for using end to end encryption for your users and is the additional expense worth the money and additional management bearing in mind the threats? 13 th June 2006 TETRA Experience - Poland
Conclusion Ø Security functions built in to TETRA from the start! Air interface encryption protects, control traffic, IDs as well as voice and user traffic. End to end encryption gives higher level of assurance Ø Key management comes without user overhead because of OTAR. 13 th June 2006 TETRA Experience - Poland
- Slides: 26