Security cryptography Java ECommerce Martin Cooke 2003 This




















- Slides: 47

Security: cryptography Java E-Commerce © Martin Cooke, 2003

This lecture • Cryptographic concepts • Authentication and trust Next lecture • SSL and SET • Java support for cryptography 9/10/2020 Java E-Commerce © Martin Cooke, 2003 2

Four cornerstones of security & trust authorisation authentication Integrity & confidentiality nonrepudiation 9/10/2020 Java E-Commerce © Martin Cooke, 2003 3

Key issues Trusted downloads • authentication: identity of site is valid signatures & certificates message digests • integrity: classes have not been altered Privacy encryption & decryption engines secure transport protocols eg SSL 9/10/2020 Java E-Commerce © Martin Cooke, 2003 4

Cryptographic concepts Java E-Commerce © Martin Cooke, 2003

Definitions • Cryptography: “science of secret writing” • Cryptanalysis: art of decoding encoded information without access to keys 9/10/2020 Java E-Commerce © Martin Cooke, 2003 6

Lock and key analogy • Lock = algorithm • Key = private, public or secret key • Locks come in various strengths – Implication for key complexity (generation) • Doesn’t rely on secrecy of locks – Enables security experts to find holes 9/10/2020 Java E-Commerce © Martin Cooke, 2003 7

Issues for keys • • • How used? Where generated? How? Where stored? Transmitted? How revoked? 9/10/2020 Java E-Commerce © Martin Cooke, 2003 8

“Cryptography is rarely ever the solution to a security problem. Cryptography is a translation mechanism, usually converting a communications security problem into a key management problem and ultimately into a computer security problem. Hopefully, the resulting problem is easier to solve than the original problem. ” Gollmann, p 203 9/10/2020 Java E-Commerce © Martin Cooke, 2003 9

Weakest links • Since good cryptographical solutions are hard to break, security is a matter of – key protection • ie access control & key management – proper use of algorithm • Key generation (cf Enigma) 9/10/2020 Java E-Commerce © Martin Cooke, 2003 10

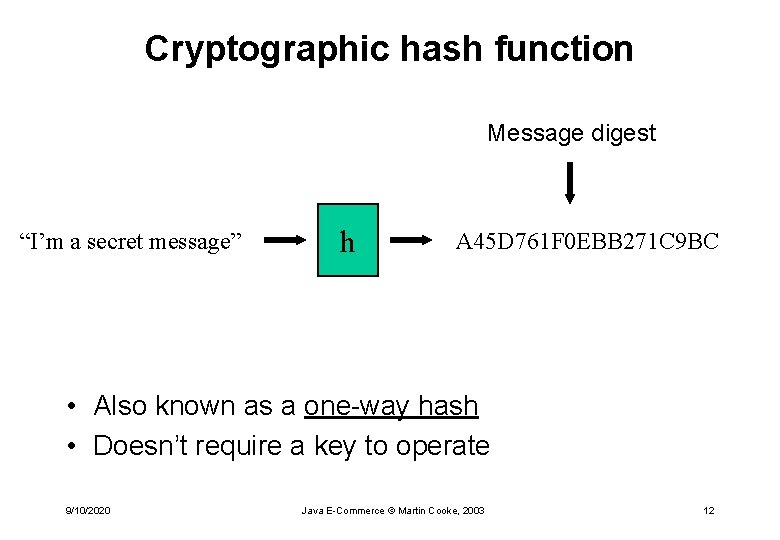
Cryptographic algorithms Keyless algorithms • Cryptographic hash function, used to produce message digests (aka “digital fingerprint”) Algorithms with keys • Secret keys • Public key system 9/10/2020 Java E-Commerce © Martin Cooke, 2003 11

Cryptographic hash function Message digest “I’m a secret message” h A 45 D 761 F 0 EBB 271 C 9 BC • Also known as a one-way hash • Doesn’t require a key to operate 9/10/2020 Java E-Commerce © Martin Cooke, 2003 12

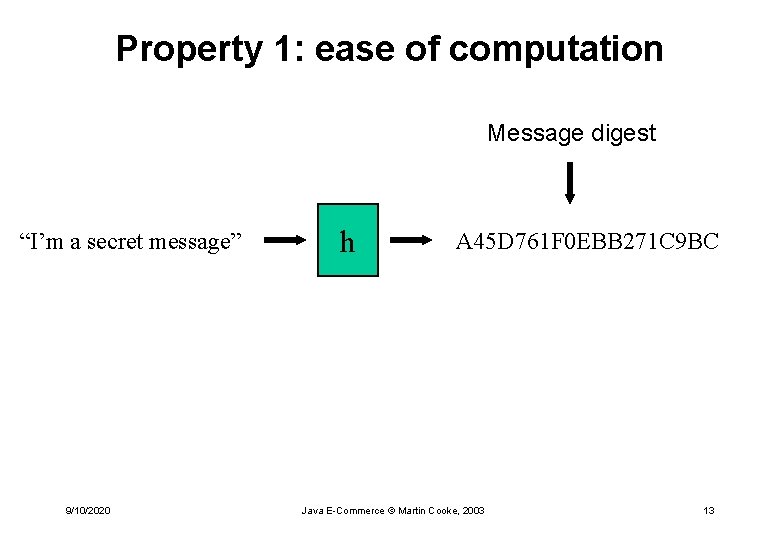
Property 1: ease of computation Message digest “I’m a secret message” 9/10/2020 h A 45 D 761 F 0 EBB 271 C 9 BC Java E-Commerce © Martin Cooke, 2003 13

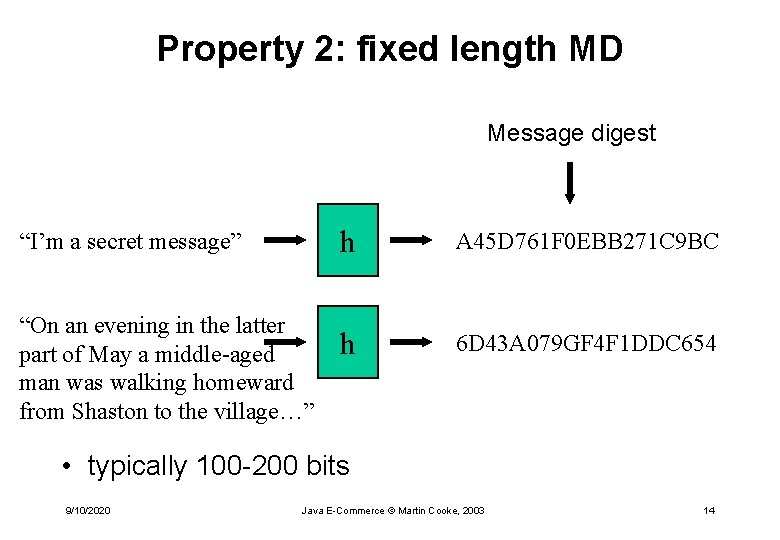
Property 2: fixed length MD Message digest “I’m a secret message” “On an evening in the latter part of May a middle-aged man was walking homeward from Shaston to the village…” h A 45 D 761 F 0 EBB 271 C 9 BC h 6 D 43 A 079 GF 4 F 1 DDC 654 • typically 100 -200 bits 9/10/2020 Java E-Commerce © Martin Cooke, 2003 14

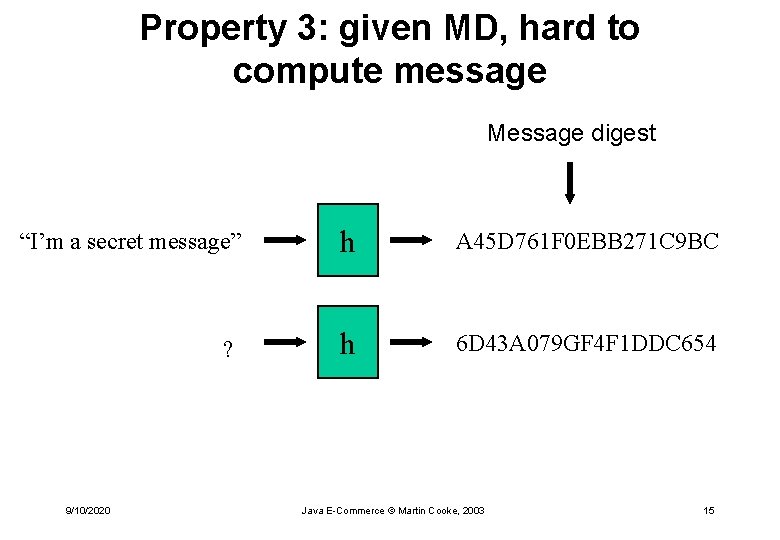
Property 3: given MD, hard to compute message Message digest “I’m a secret message” h A 45 D 761 F 0 EBB 271 C 9 BC ? h 6 D 43 A 079 GF 4 F 1 DDC 654 9/10/2020 Java E-Commerce © Martin Cooke, 2003 15

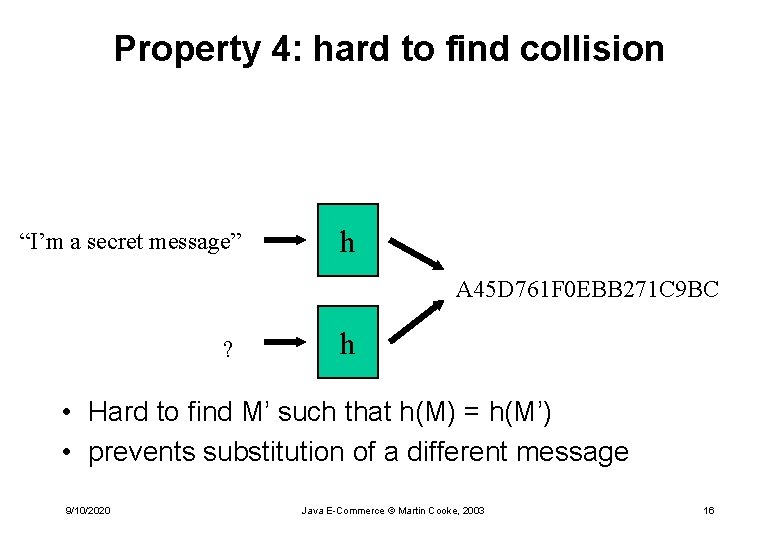
Property 4: hard to find collision “I’m a secret message” h A 45 D 761 F 0 EBB 271 C 9 BC ? h • Hard to find M’ such that h(M) = h(M’) • prevents substitution of a different message 9/10/2020 Java E-Commerce © Martin Cooke, 2003 16

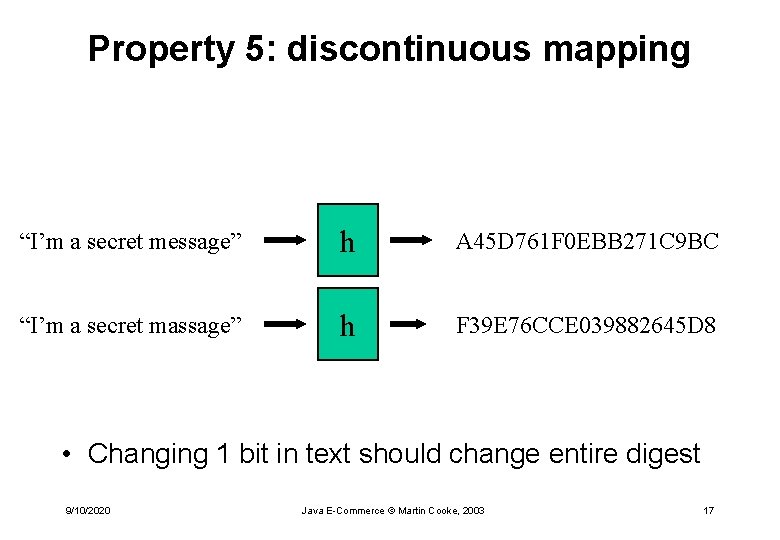
Property 5: discontinuous mapping “I’m a secret message” h A 45 D 761 F 0 EBB 271 C 9 BC “I’m a secret massage” h F 39 E 76 CCE 039882645 D 8 • Changing 1 bit in text should change entire digest 9/10/2020 Java E-Commerce © Martin Cooke, 2003 17

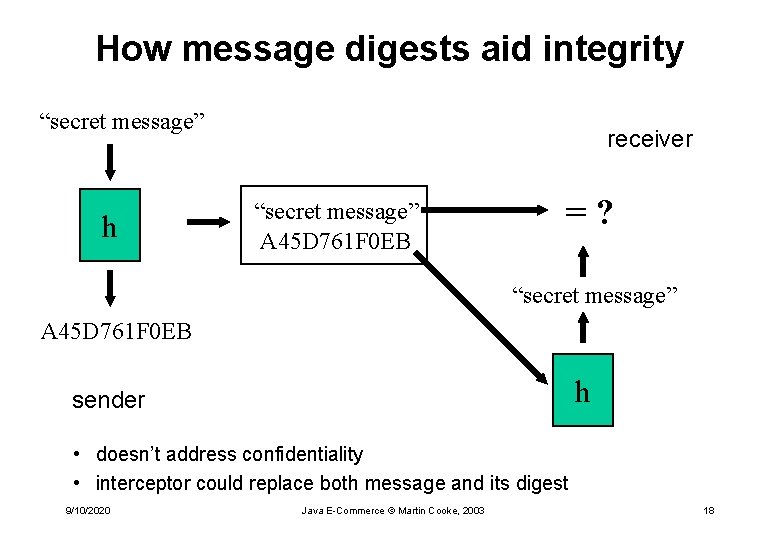
How message digests aid integrity “secret message” h receiver “secret message” A 45 D 761 F 0 EB =? “secret message” A 45 D 761 F 0 EB h sender • doesn’t address confidentiality • interceptor could replace both message and its digest 9/10/2020 Java E-Commerce © Martin Cooke, 2003 18

Message authentication codes • A MAC is a secure message digest • Approach: • Use a password, p • Calculate md = h(p || message) • Calculate mac = h(p || md) • Receiver: • Calculates md = h(p || message) • Checks mac = h(p || md) • But: requires that p is known to both parties 9/10/2020 Java E-Commerce © Martin Cooke, 2003 19

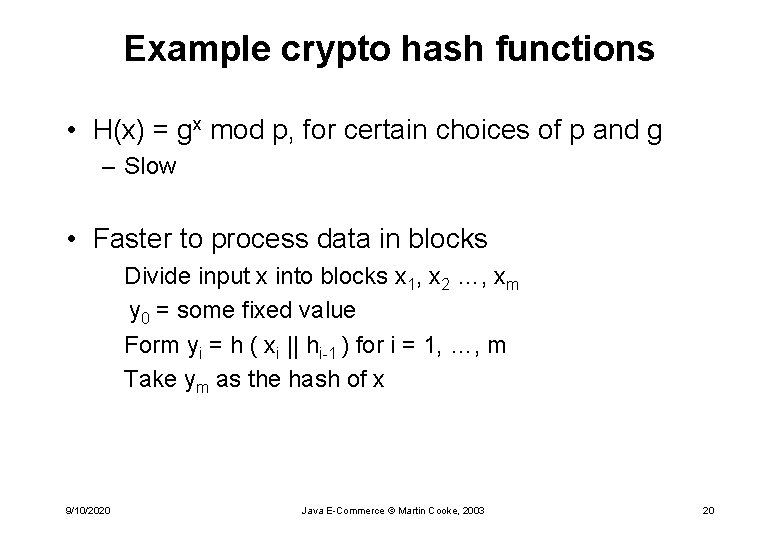
Example crypto hash functions • H(x) = gx mod p, for certain choices of p and g – Slow • Faster to process data in blocks Divide input x into blocks x 1, x 2 …, xm y 0 = some fixed value Form yi = h ( xi || hi-1 ) for i = 1, …, m Take ym as the hash of x 9/10/2020 Java E-Commerce © Martin Cooke, 2003 20

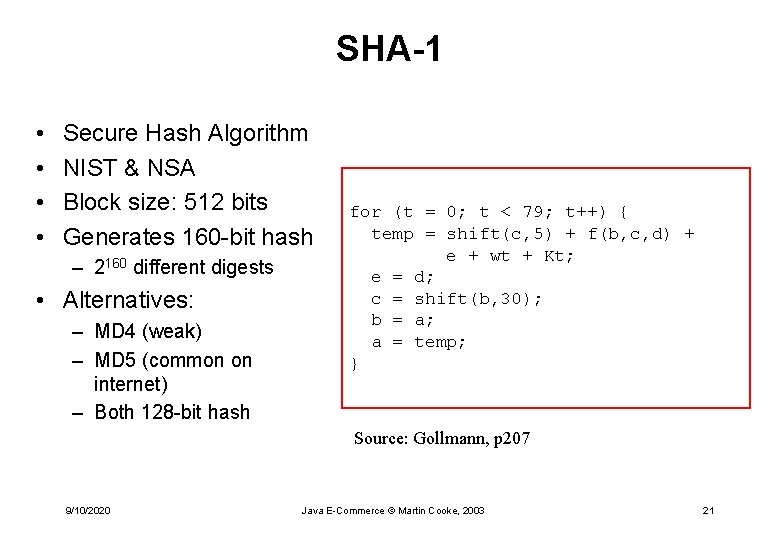
SHA-1 • • Secure Hash Algorithm NIST & NSA Block size: 512 bits Generates 160 -bit hash – 2160 different digests • Alternatives: – MD 4 (weak) – MD 5 (common on internet) – Both 128 -bit hash for (t = 0; t < 79; t++) { temp = shift(c, 5) + f(b, c, d) + e + wt + Kt; e = d; c = shift(b, 30); b = a; a = temp; } Source: Gollmann, p 207 9/10/2020 Java E-Commerce © Martin Cooke, 2003 21

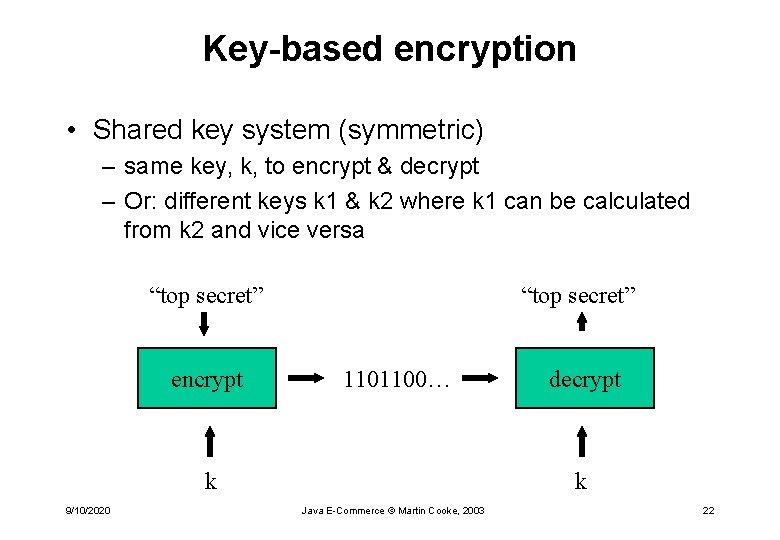
Key-based encryption • Shared key system (symmetric) – same key, k, to encrypt & decrypt – Or: different keys k 1 & k 2 where k 1 can be calculated from k 2 and vice versa “top secret” encrypt “top secret” 1101100… k 9/10/2020 decrypt k Java E-Commerce © Martin Cooke, 2003 22

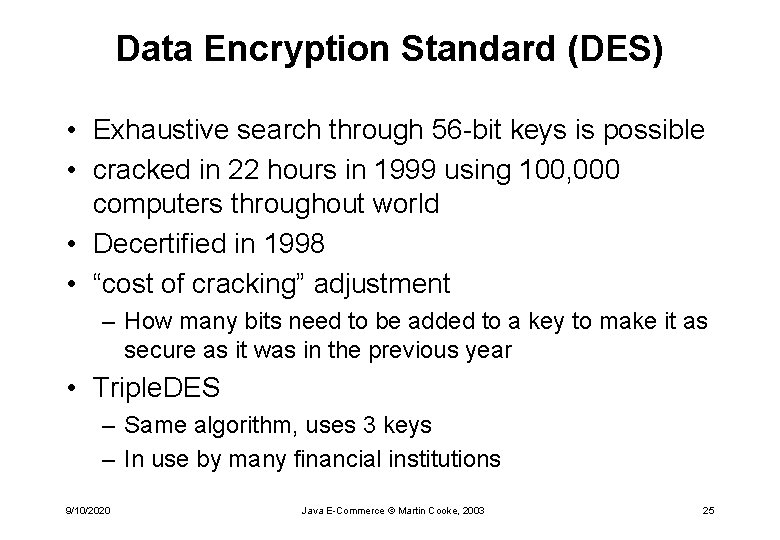
Data Encryption Standard (DES) • • • Proposed in 1974 by IBM US government standard, used since 1977 56 -bit key Designed for easy hardware implementation Also efficient to implement in software Message broken into 64 -bit blocks, each of which is transformed and passed through 16 stages 9/10/2020 Java E-Commerce © Martin Cooke, 2003 23

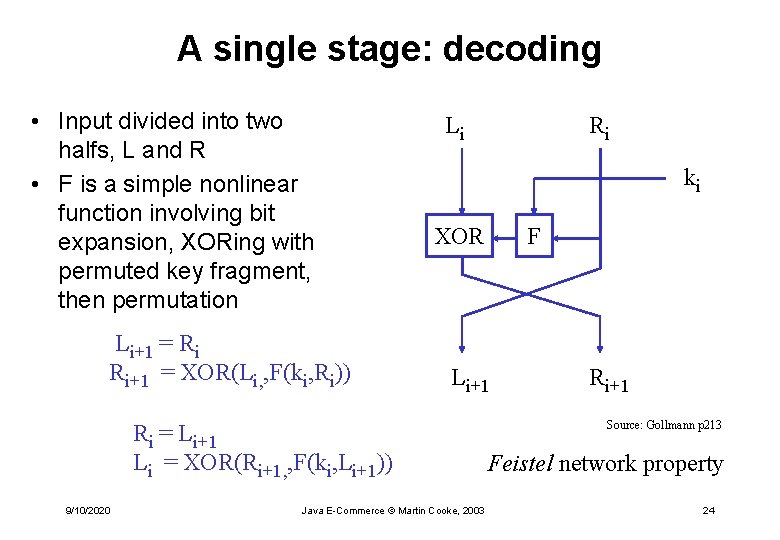
A single stage: decoding • Input divided into two halfs, L and R • F is a simple nonlinear function involving bit expansion, XORing with permuted key fragment, then permutation Li+1 = Ri Ri+1 = XOR(Li, , F(ki, Ri)) Li ki XOR F Li+1 Ri = Li+1 Li = XOR(Ri+1, , F(ki, Li+1)) 9/10/2020 Ri Java E-Commerce © Martin Cooke, 2003 Ri+1 Source: Gollmann p 213 Feistel network property 24

Data Encryption Standard (DES) • Exhaustive search through 56 -bit keys is possible • cracked in 22 hours in 1999 using 100, 000 computers throughout world • Decertified in 1998 • “cost of cracking” adjustment – How many bits need to be added to a key to make it as secure as it was in the previous year • Triple. DES – Same algorithm, uses 3 keys – In use by many financial institutions 9/10/2020 Java E-Commerce © Martin Cooke, 2003 25

Problems with shared key approach • How to share keys? • Requires a separate key for every pair of parties wishing to communicate securely: a big key management problem 9/10/2020 Java E-Commerce © Martin Cooke, 2003 26

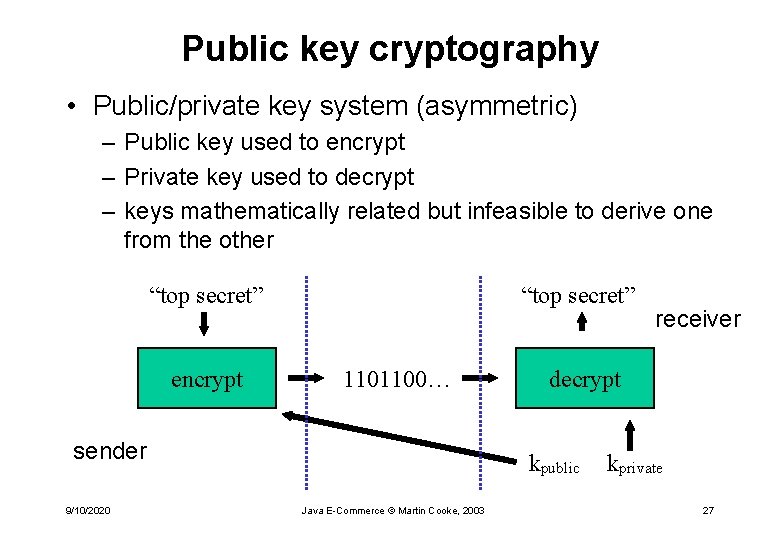
Public key cryptography • Public/private key system (asymmetric) – Public key used to encrypt – Private key used to decrypt – keys mathematically related but infeasible to derive one from the other “top secret” encrypt “top secret” 1101100… sender 9/10/2020 decrypt kpublic Java E-Commerce © Martin Cooke, 2003 receiver kprivate 27

Public key cryptography • Introduced in 1976 by Diffie & Hellman • Algorithms based on the fact that finding prime factors of very large integers (> 10100) is very difficult • Much larger keys (> 512 bits) needed • Consequently, very slow in use (though sped up by factor of 30 by 16 -year old Irish school girl, Sarah Flannery, in 1999) • RSA (Rivest-Shamir-Adelman) is best known 9/10/2020 Java E-Commerce © Martin Cooke, 2003 28

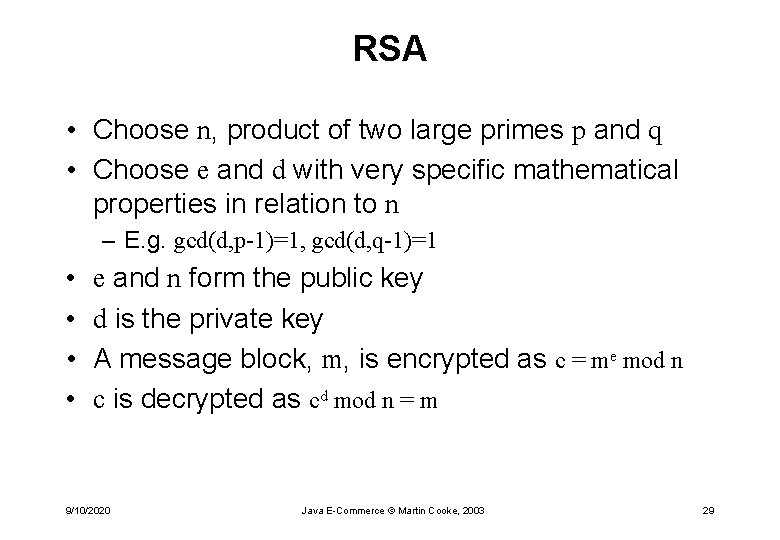
RSA • Choose n, product of two large primes p and q • Choose e and d with very specific mathematical properties in relation to n – E. g. gcd(d, p-1)=1, gcd(d, q-1)=1 • • e and n form the public key d is the private key A message block, m, is encrypted as c = me mod n c is decrypted as cd mod n = m 9/10/2020 Java E-Commerce © Martin Cooke, 2003 29

On secrecy of the algorithm “One should generally be very wary of unpublished or secret algorithms. Quite often the designer is then not sure of the security of the algorithm, or its security depends on the secrecy of the algorithm. Generally, no algorithm that depends on the secrecy of the algorithm is secure. Particularly in software, anyone can hire someone to disassemble and reverse-engineer the algorithm. Experience has shown that the vast majority of secret algorithms that have become public knowledge later have been pitifully weak in reality. ” source: http: //www. ssh. fi/tech/crypto/intro. cfm 9/10/2020 Java E-Commerce © Martin Cooke, 2003 30

On secret key length & brute-force attacks 32 40 Easily done on home computer < week on home comp 56 Easily breakable with special hardware, cost within reach of organised criminals, major companies and governments 64 80 Probably breakable now by major governments and soon by criminals, major companies and lesser governments Good for many years 128 Good foreseeable future (but: quantum computing) source: http: //www. ssh. fi/tech/crypto/intro. cfm 9/10/2020 Java E-Commerce © Martin Cooke, 2003 31

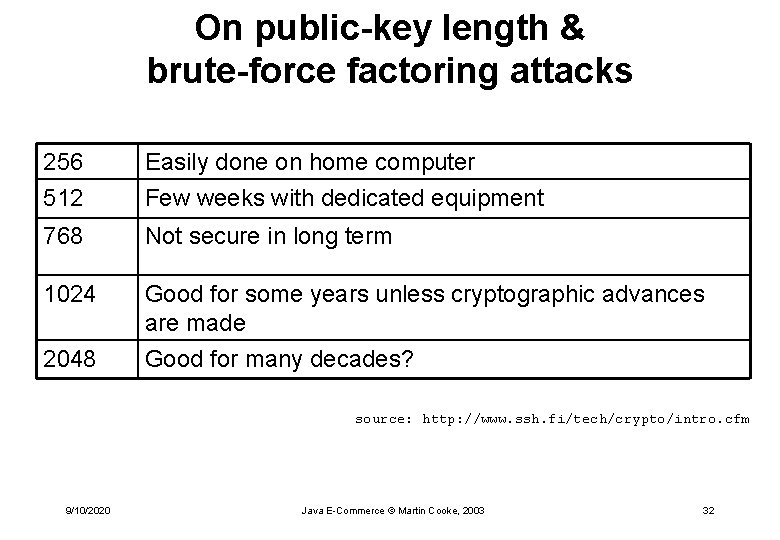
On public-key length & brute-force factoring attacks 256 512 Easily done on home computer Few weeks with dedicated equipment 768 Not secure in long term 1024 Good for some years unless cryptographic advances are made Good for many decades? 2048 source: http: //www. ssh. fi/tech/crypto/intro. cfm 9/10/2020 Java E-Commerce © Martin Cooke, 2003 32

Comparison 9/10/2020 Shared key Need to transmit shared key securely Public key No need to transmit key (no need for secure channel) Fast encrypt/decrypt 56 -112 bit keys Slow encrypt/decrypt 1024 -2048 bit keys How to manage hoards of shared keys? How to make public key available? Java E-Commerce © Martin Cooke, 2003 33

Effective hybrid used in practice • Use public-private key approach to confidentially exchange a secret key • Use secret key for bulk communication Remaining issue: • how are we going to ensure that we are exchanging keys with a known and trusted party? 9/10/2020 Java E-Commerce © Martin Cooke, 2003 34

Authentication and trust Digital signatures and certificates Java E-Commerce © Martin Cooke, 2003

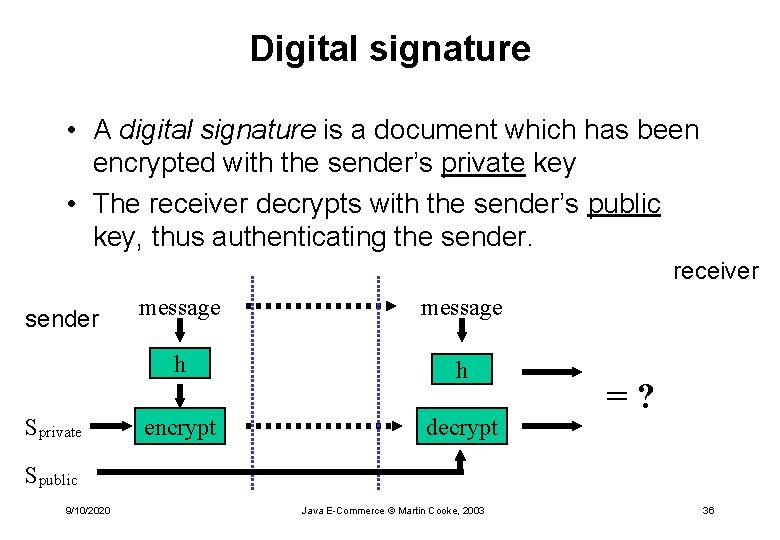
Digital signature • A digital signature is a document which has been encrypted with the sender’s private key • The receiver decrypts with the sender’s public key, thus authenticating the sender. receiver sender Sprivate message h h encrypt decrypt =? Spublic 9/10/2020 Java E-Commerce © Martin Cooke, 2003 36

Digital signature • Digital signatures are actually based on the message digest (plus other info such as timestamp) – faster – also called digital fingerprints. • In order to be successful, digital signatures must not be reusable 9/10/2020 Java E-Commerce © Martin Cooke, 2003 37

What security requirements do digital signatures meet? • Integrity & non-repudiation – Secure form of message digest • Authentication – Can only be decoded with a given individual’s public key • Not confidential, since original text needs to be sent so that MD can be calculated 9/10/2020 Java E-Commerce © Martin Cooke, 2003 38

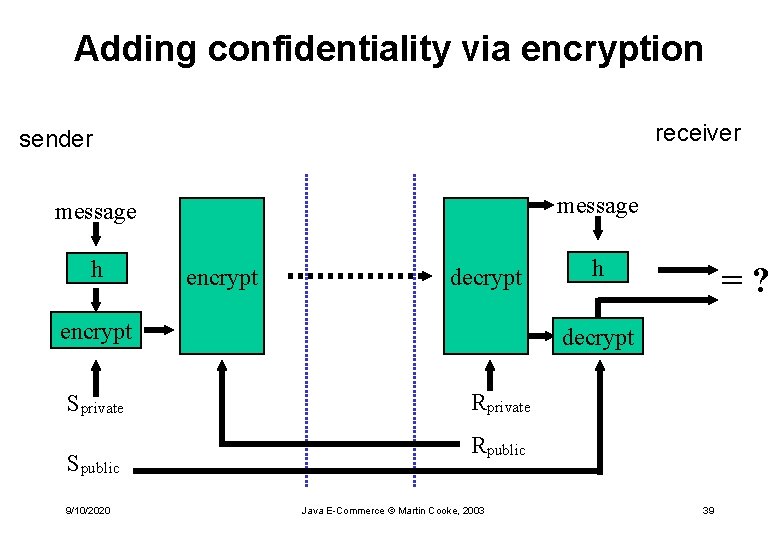
Adding confidentiality via encryption receiver sender message h encrypt decrypt encrypt Sprivate Spublic 9/10/2020 h =? decrypt Rprivate Rpublic Java E-Commerce © Martin Cooke, 2003 39

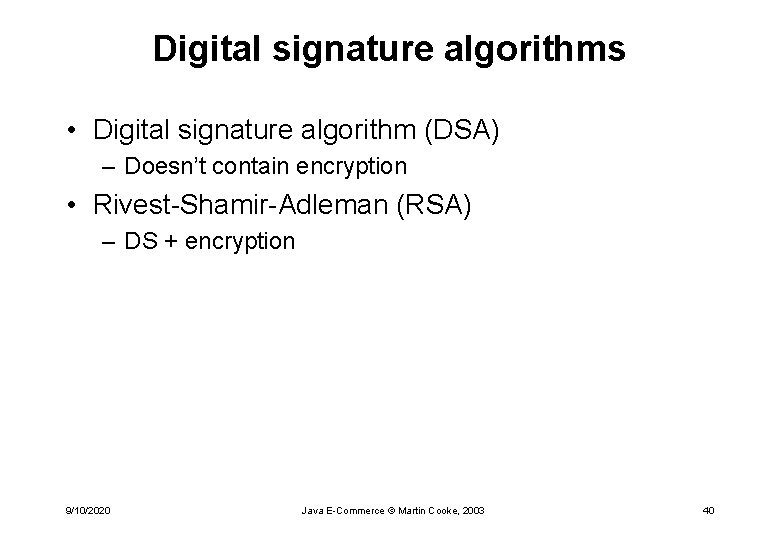
Digital signature algorithms • Digital signature algorithm (DSA) – Doesn’t contain encryption • Rivest-Shamir-Adleman (RSA) – DS + encryption 9/10/2020 Java E-Commerce © Martin Cooke, 2003 40

Trust Suppose authentication between A and B has succeeded – If A knows B (in person), then no problem – What if A doesn’t know B? B might be a criminal with a (possible stolen) public key Solution: find a 3 rd party (trusted by A) who can vouch for B – Certificate authority (eg Verisign, Entrust) 9/10/2020 Java E-Commerce © Martin Cooke, 2003 41

Digital certificate • Contains data such as – – Name Unique serial number Public key Digital signature of certificate authority (CA) • Based on X. 509 standard • Client checks that signature of CA is valid using its (widely-available) public key 9/10/2020 Java E-Commerce © Martin Cooke, 2003 42

Should you trust a digital certificate? • How are they obtained? – How much & what security checks? cheap, only check is ownership of a credit card expensive, thorough vetting • Do you trust the certificate authority? – each CA is certified by a more trustworthy CA: chain of certificates in a hierarchy of trust – Ultimately, a self-signed certificate at the root • Eg post office 9/10/2020 Java E-Commerce © Martin Cooke, 2003 43

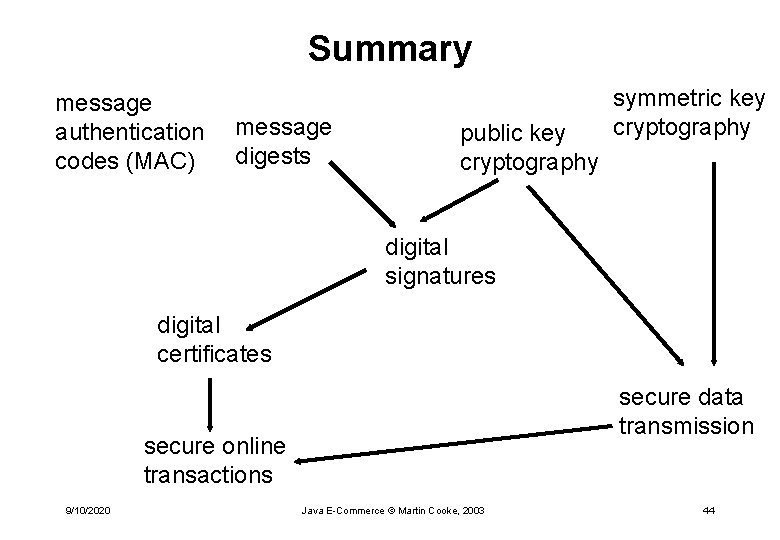
Summary message authentication codes (MAC) message digests public key cryptography symmetric key cryptography digital signatures digital certificates secure data transmission secure online transactions 9/10/2020 Java E-Commerce © Martin Cooke, 2003 44

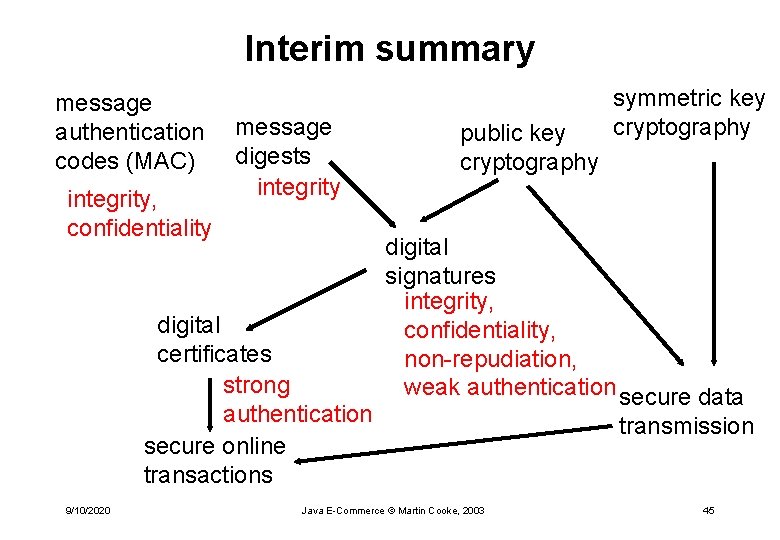
Interim summary message authentication codes (MAC) integrity, confidentiality message digests integrity digital certificates strong authentication secure online transactions 9/10/2020 public key cryptography symmetric key cryptography digital signatures integrity, confidentiality, non-repudiation, weak authentication secure data Java E-Commerce © Martin Cooke, 2003 transmission 45

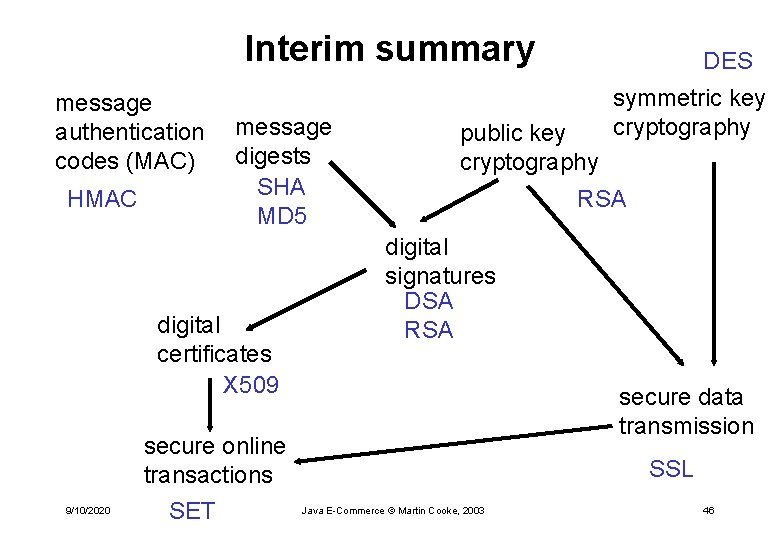
Interim summary message authentication codes (MAC) HMAC message digests SHA MD 5 digital certificates X 509 9/10/2020 secure online transactions SET DES public key cryptography symmetric key cryptography RSA digital signatures DSA RSA secure data transmission SSL Java E-Commerce © Martin Cooke, 2003 46

Resources Books • Oaks, S (2001) Java Security (2 nd ed), O’Reilly, 0 -596 -00157 -6 • Gollmann, D. (1999) Computer Security, John Wiley, 0 -471 -97844 -2 Online Compact overview of cryptography & algorithms respectively http: //www. ssh. fi/tech/crypto/intro. cfm http: //www. ssh. fi/tech/crypto/algorithms. cfm Certificates http: //www. javaworld. com/javaworld/jw-01 -2001/jw 0112 -howto. html Tutorial on Java Security Evolution and Concepts, Srinivas, Java. World. 9/10/2020 Java E-Commerce © Martin Cooke, 2003 47