Security Considerations for Deterministic Networking Draft Update IETF





![Attacker Types [Based on RFC 7384] Internal / external External Internal Man-in-the-middle (MITM) / Attacker Types [Based on RFC 7384] Internal / external External Internal Man-in-the-middle (MITM) /](https://slidetodoc.com/presentation_image_h2/3e8555f43b9fcb8fa81d86c8b8b8627f/image-7.jpg)
- Slides: 12

Security Considerations for Deterministic Networking Draft Update IETF 106 Singapore 2019 Ethan Grossman Senior Software Engineering Manager Dolby Laboratories, San Francisco

Det. Net Security Considerations Scope l Draft: https: //datatracker. ietf. org/doc/draft-ietf-detnet-security/ l Scope A reference/toolkit for those who have not built time-sensitive networks before l Exclusively addresses time-related threats l Other Det. Net drafts address draft-topic-specific considerations then refer here (as informational) l 2

Det. Net Security Considerations Status l Data plane technology-independent sections § l IP- and MPLS-specific sections § l No unique threats identified – discussion on this later TSN-specific section § l Mature, but still some editing and a few small sections to fill in Not started Security-related statements from Use Cases § Update? Delete? 3

Det. Net Security Considerations Discussion and Next Steps l Discussion l Data plane technology-specific threats - are we missing something? § l l l There will be more data planes – so maybe that info should not be in here? Security-related statements from Use Cases – Update? Delete? Sec. Dir review – before or after WG LC? Next Steps l l Finish edits, add any new material Working Group Last Call 4

Det. Net Security Considerations l The End l Remaining slides are optional, a brief overview of the draft 5

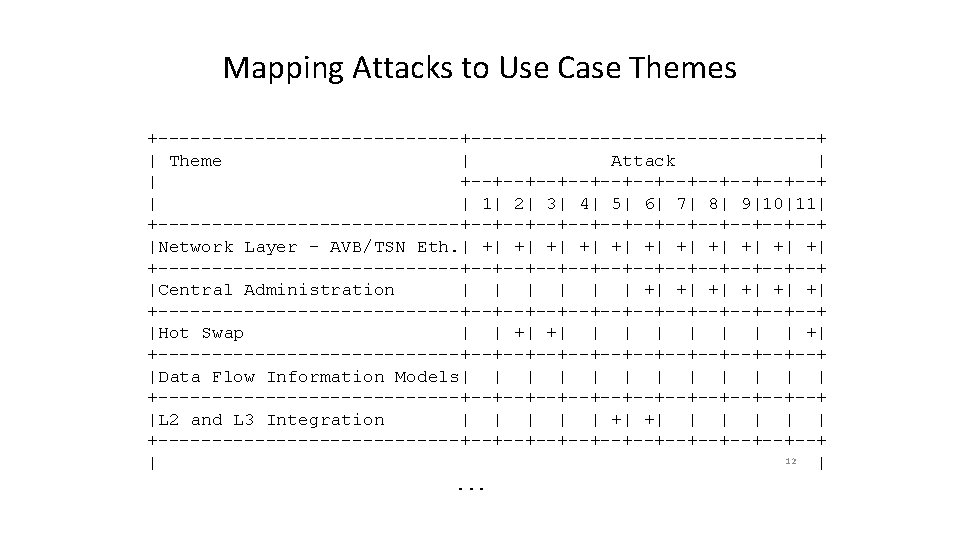
Det. Net Security Considerations l Security Considerations draft as ”toolkit” l Attackers l Attacks l Impacts l Mitigations l Table of attacks to impacts and mitigation l Table of use cases to relevant attacks 6
![Attacker Types Based on RFC 7384 Internal external External Internal Maninthemiddle MITM Attacker Types [Based on RFC 7384] Internal / external External Internal Man-in-the-middle (MITM) /](https://slidetodoc.com/presentation_image_h2/3e8555f43b9fcb8fa81d86c8b8b8627f/image-7.jpg)
Attacker Types [Based on RFC 7384] Internal / external External Internal Man-in-the-middle (MITM) / Injector MITM Injector 7


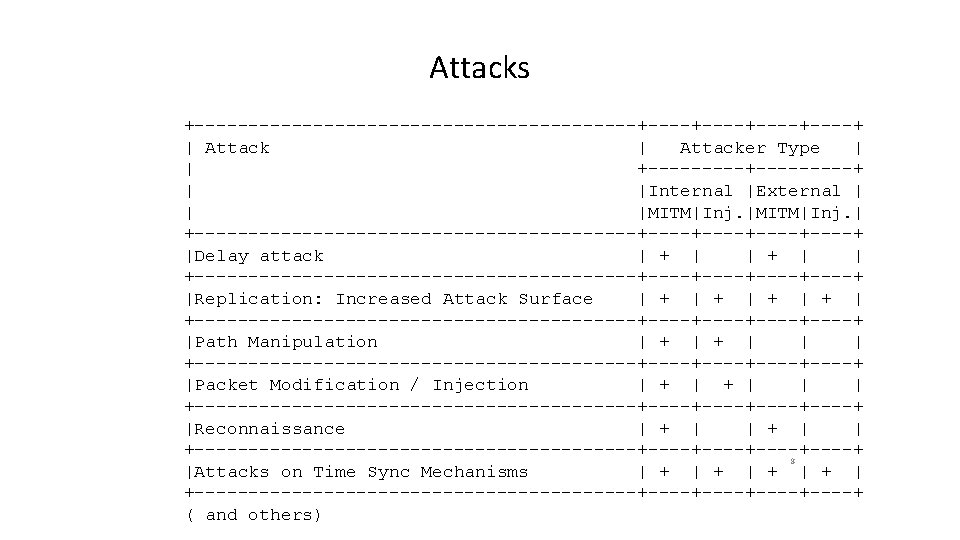
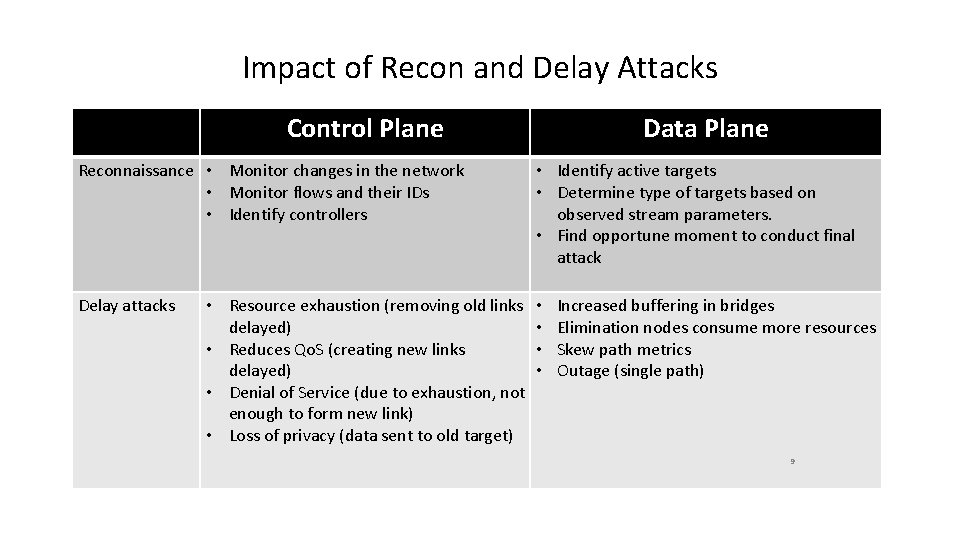
Impact of Recon and Delay Attacks Control Plane Data Plane Reconnaissance • Monitor changes in the network • Monitor flows and their IDs • Identify controllers • Identify active targets • Determine type of targets based on observed stream parameters. • Find opportune moment to conduct final attack Delay attacks • • • Resource exhaustion (removing old links delayed) • Reduces Qo. S (creating new links delayed) • Denial of Service (due to exhaustion, not enough to form new link) • Loss of privacy (data sent to old target) Increased buffering in bridges Elimination nodes consume more resources Skew path metrics Outage (single path) 9

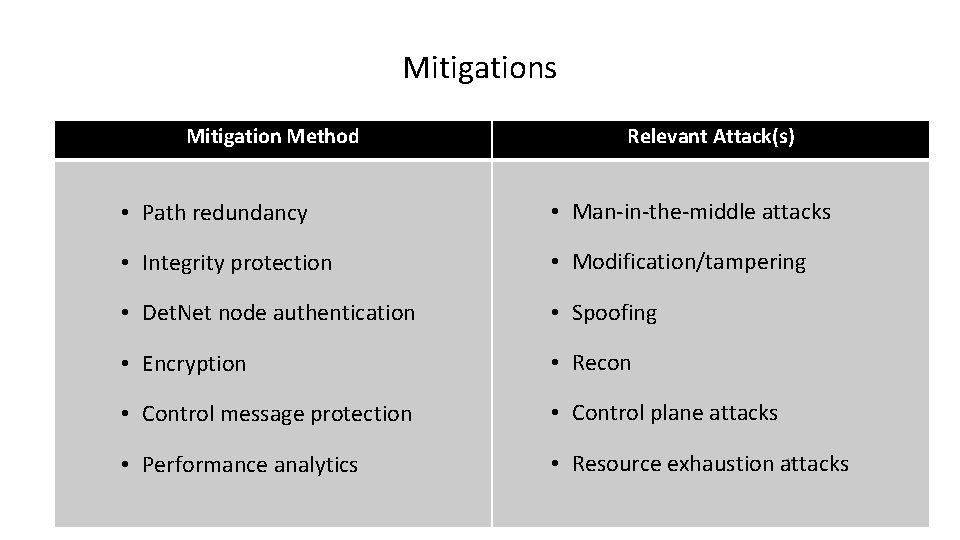
Mitigations Mitigation Method Relevant Attack(s) • Path redundancy • Man-in-the-middle attacks • Integrity protection • Modification/tampering • Det. Net node authentication • Spoofing • Encryption • Recon • Control message protection • Control plane attacks • Performance analytics • Resource exhaustion attacks 10

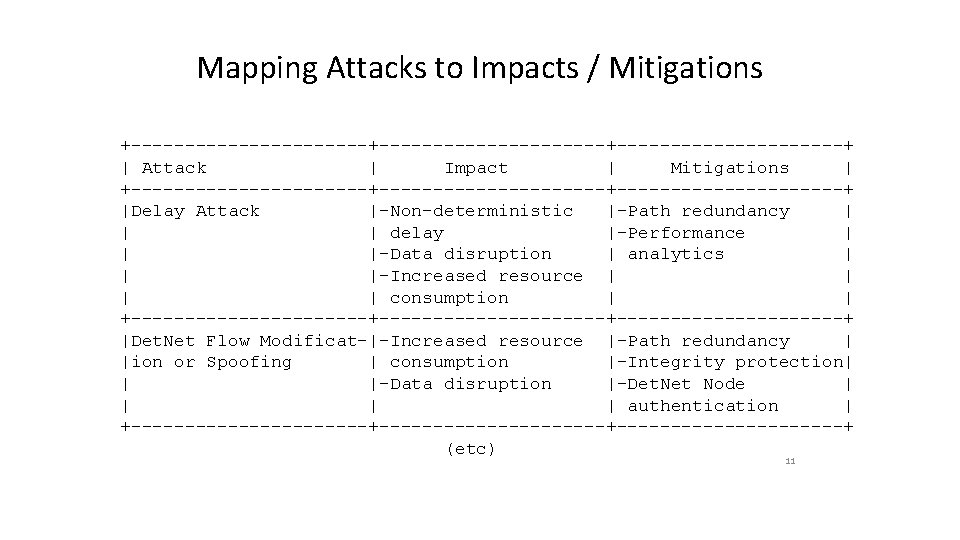
Mapping Attacks to Impacts / Mitigations +-----------+---------------------+ | Attack | Impact | Mitigations | +-----------+---------------------+ |Delay Attack |-Non-deterministic |-Path redundancy | | | delay |-Performance | | |-Data disruption | analytics | | |-Increased resource | | consumption | | +-----------+---------------------+ |Det. Net Flow Modificat-|-Increased resource |-Path redundancy | |ion or Spoofing | consumption |-Integrity protection| | |-Data disruption |-Det. Net Node | | authentication | +-----------+---------------------+ (etc) 11
