Security Authorization Access Control and Usage Control Andrew








- Slides: 16

Security: Authorization, Access Control and Usage Control Andrew Mc. Nab, University of Manchester mcnab@hep. man. ac. uk Andrew Mc. Nab - Security - 1 July 2003

Outline u Certificates u New and VO servers VOMS system u Using VOMS u Access Control: GACL u mod_gridsite u mod_slashgrid? u Usage Control: PBS and Unix disk quotas u “Usage peering” and retrospective usage targets u Genuine u Future Grid. PP / EDG / WP 6 accounting security work Andrew Mc. Nab - Security - 1 July 2003

Certificates and VO servers u EDG users and hosts are identified by X. 509 certificates, signed by one of ~20 “national” Certificate Authorities. n Jobs use a short term certificate derived from this: GSI Proxy. u X. 509 defines how user’s public key and the CA’s signature of key + the user’s name is stored. n This provides authentication: equivalent to an ID Card. u Simplest way to build authorization and access control using this, is with a list of authorized users for a resource. u This n n is what EDG currently does with LDAP VO servers. Lists of members for each Virtual Organisation (ATLAS, Ba. Bar etc) are published. Sites make local authorized user lists (grid-mapfile) from this. u However, scaling and latency issues since all sites must fetch list of all users currently authorized Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Virtual Organisation Membership Service: VOMS u Instead of publishing lists of VO and group membership, supply signed attribute certificates to users: Ticket rather than ID Card. u Users can then present these attribute certificates to sites/resources and obtain access with group privilege, role etc. u Certificates n can be included in GSI proxy certificates as extensions “A ticket in your ID card wallet. ” u Multiple attribute certificates can be used simultaneously, even from different VOMS servers and VOs. u Potential to allow users to create ad-hoc groups within VO, and to discard unnecessary VOMS credentials at delegation steps. u Implementation is backwards compatible with normal Globus and HTTPS use of certificates n so still compatible with other Grid projects and HTTPS webservers. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

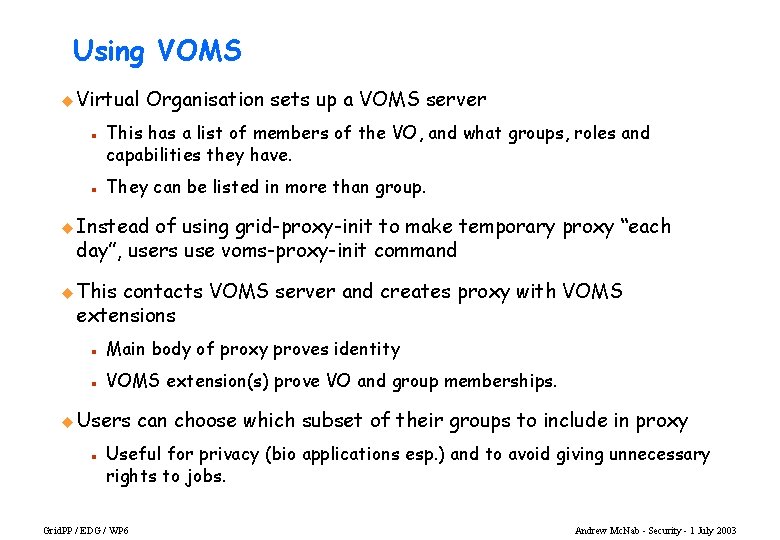
Using VOMS u Virtual n n Organisation sets up a VOMS server This has a list of members of the VO, and what groups, roles and capabilities they have. They can be listed in more than group. u Instead of using grid-proxy-init to make temporary proxy “each day”, users use voms-proxy-init command u This contacts VOMS server and creates proxy with VOMS extensions n Main body of proxy proves identity n VOMS extension(s) prove VO and group memberships. u Users n can choose which subset of their groups to include in proxy Useful for privacy (bio applications esp. ) and to avoid giving unnecessary rights to jobs. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Access Control: GACL u When going beyond simple lists of users, need a more flexible way of writing access control policies that can include individuals, VO-LDAP or VOMS groups. u Grid. Site, Slash. Grid and Storage Element use GACL, simple Access Control Lists written in XML. u Simplicity important because these fileserver / filesystem applications involve very many access control evaluations. u However, GACL isn’t a recognised standard and something standards -based would be better. n Could go to, say, an equivalent subset of XACML. u Proposed OGSA Authorization WG in GGF may endorse some way of using (probably) XACML as an “Authorization Language. ” Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Grid. Site u Grid. Site manages access to websites and HTTP(S) fileservers n Users and admins load GSI cert + key into unmodified web browsers n Originally produced for www. gridpp. ac. uk u GACL n n ACL’s control level of read and write access to file/directory Write access by HTML forms (interactive) or HTTP PUT (programmatic) Programmatic access makes webserver export something looking more like a filesystem: GET (read), PUT (write), HEAD (stat), DELETE (unlink) u New 0. 9 architecture provides extended functionality via Apache module. u Support u ACLs n for efficient HTTP GET and PUT operations. enforced at low level inside Apache request processing so now available for coarse grained access control to PHP, CGI, JSP etc as well as HTML. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

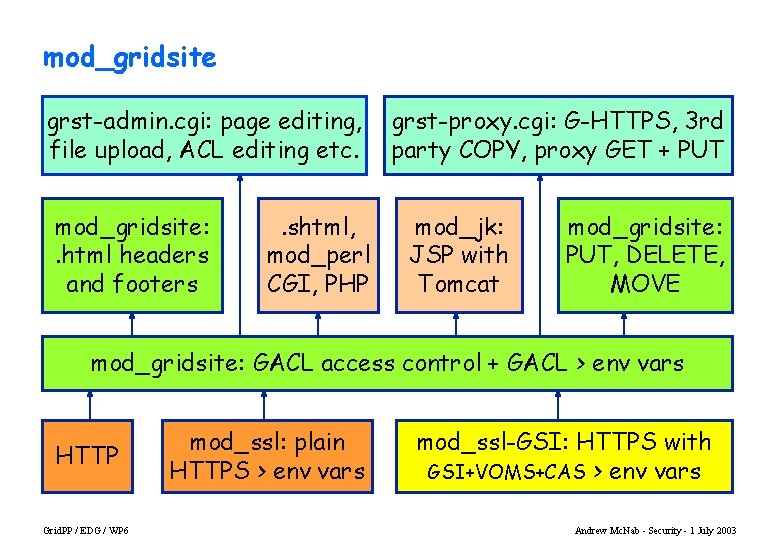
mod_gridsite grst-admin. cgi: page editing, file upload, ACL editing etc. mod_gridsite: . html headers and footers . shtml, mod_perl CGI, PHP grst-proxy. cgi: G-HTTPS, 3 rd party COPY, proxy GET + PUT mod_jk: JSP with Tomcat mod_gridsite: PUT, DELETE, MOVE mod_gridsite: GACL access control + GACL > env vars HTTP Grid. PP / EDG / WP 6 mod_ssl: plain HTTPS > env vars mod_ssl-GSI: HTTPS with GSI+VOMS+CAS > env vars Andrew Mc. Nab - Security - 1 July 2003

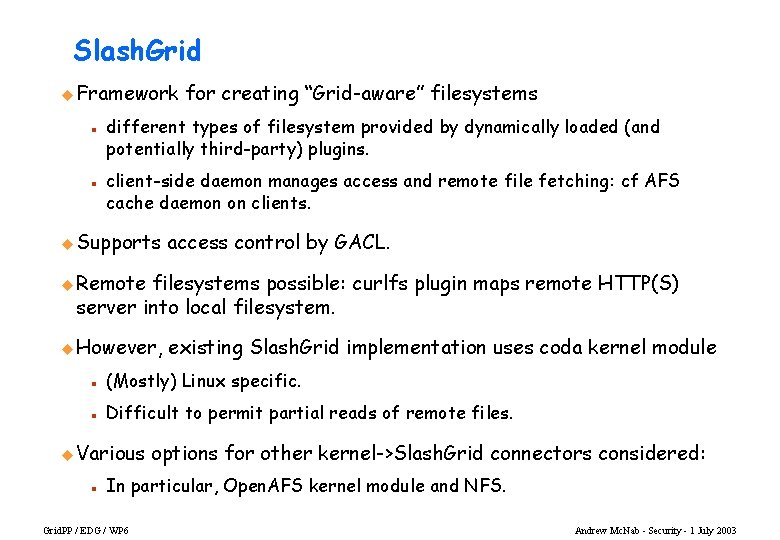
Slash. Grid u Framework n n for creating “Grid-aware” filesystems different types of filesystem provided by dynamically loaded (and potentially third-party) plugins. client-side daemon manages access and remote file fetching: cf AFS cache daemon on clients. u Supports access control by GACL. u Remote filesystems possible: curlfs plugin maps remote HTTP(S) server into local filesystem. u However, existing Slash. Grid implementation uses coda kernel module n (Mostly) Linux specific. n Difficult to permit partial reads of remote files. u Various n options for other kernel->Slash. Grid connectors considered: In particular, Open. AFS kernel module and NFS. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

mod_slashgrid u Old Slash. Grid daemon has to: n listen on a socket for filesystem operations (from kernel) n manage a hierarchy of files, including access control n support third party plugins in C, Java, other languages u This sounds very like a web server. u Apache n 2. 0 transports/filters stack allows non-HTTP protocols eg mod_ftp and even mod_pop 3 has been written. u Rework Slash. Grid as an Apache module, exporting Grid. Site web server “filesystem” via local TCP NFS rather than HTTP. n We get remote filesystems “for free” via mod_proxy and mod_cache n Access control already done, via mod_gridsite. n Can now write third-party filesystem plugins in C/C++, Perl, Python, Java, PHP, Bash - anything you can write web server CGI/dynamic content in. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

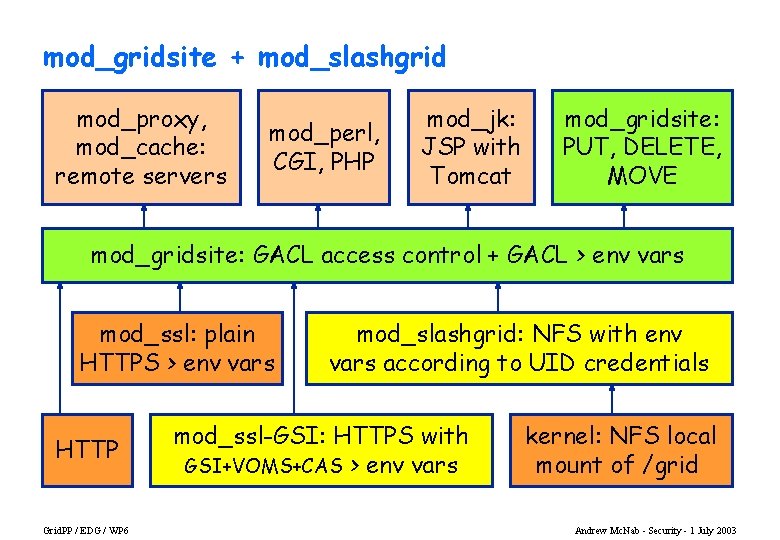
mod_gridsite + mod_slashgrid mod_proxy, mod_cache: remote servers mod_perl, CGI, PHP mod_jk: JSP with Tomcat mod_gridsite: PUT, DELETE, MOVE mod_gridsite: GACL access control + GACL > env vars mod_ssl: plain HTTPS > env vars HTTP Grid. PP / EDG / WP 6 mod_slashgrid: NFS with env vars according to UID credentials mod_ssl-GSI: HTTPS with GSI+VOMS+CAS > env vars kernel: NFS local mount of /grid Andrew Mc. Nab - Security - 1 July 2003

Usage Control: PBS and Unix quotas u Of Security’s “Authentication, Authorization and Accounting”, we have made significant progress with the first two. n But without Accounting, individual users can monopolise resources. u First step towards Accounting is local Usage Control: “quotas” etc. u Can already implement basic usage control using PBS and Unix quotas, resource limits etc. n n Since users allocated to one of a pool of accounts for their VO, could set up pool accounts with appropriate Unix groups, quotas etc. This has been investigated by some Testbed sites in various ways. u However, this is quite inflexible and imposes static upper limits rather than allocating some amount of resources for the job duration. u Ideally should be integrated into the job description and management somehow, so know how much is allowed and to clean up afterwards. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

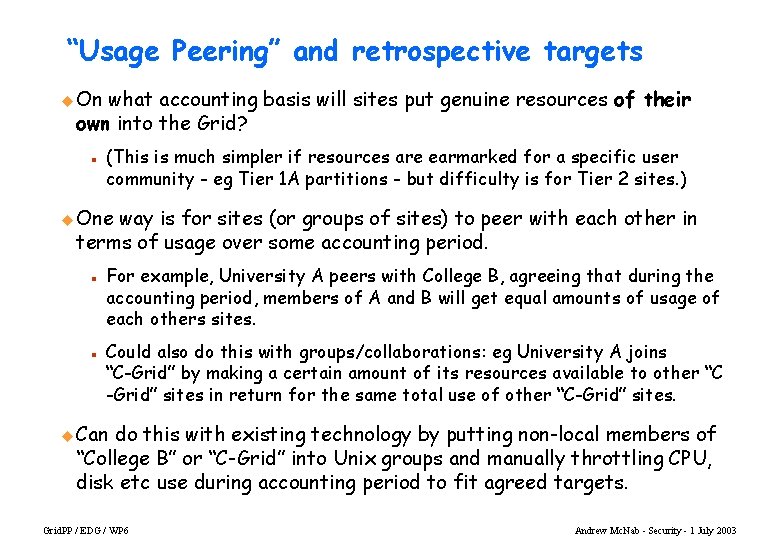
“Usage Peering” and retrospective targets u On what accounting basis will sites put genuine resources of their own into the Grid? n (This is much simpler if resources are earmarked for a specific user community - eg Tier 1 A partitions - but difficulty is for Tier 2 sites. ) u One way is for sites (or groups of sites) to peer with each other in terms of usage over some accounting period. n n For example, University A peers with College B, agreeing that during the accounting period, members of A and B will get equal amounts of usage of each others sites. Could also do this with groups/collaborations: eg University A joins “C-Grid” by making a certain amount of its resources available to other “C -Grid” sites in return for the same total use of other “C-Grid” sites. u Can do this with existing technology by putting non-local members of “College B” or “C-Grid” into Unix groups and manually throttling CPU, disk etc use during accounting period to fit agreed targets. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Genuine accounting u Genuine accounting may include: per-user measurement of use, enforcement of “credit limits”, charging, getting a price for a job and brokering based on price. u Would n eg University A gets £ 1, 000 of equipment from SRIF and rents it out to users on the open market. Uses the income to buy access to resources when its own users need it. s n be possible to do things purely economically with this in place: (Money was invented to save us from “peering” a. k. a “a barter economy. ”) In that kind of Grid, can choose how to operate between that and the other extreme position: “our equipment that only we use. ” u Even though optimisation / brokering / ”marketing” outside of the scope of Security, but we need to provide the local accounting tools needed. u The “choke points” we’ve put in place for Access Control are very suited to Usage Control and usage recording. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Future Developments u EU Data. Grid and Grid. PP-1 nearing end of lifespans u Security part of Grid. PP-2 proposal includes completion of Authorization work and implementing systems required for Accounting. u This n n n will need to be co-ordinated with: LCG requirements - already recognised the need for Usage Control as an urgent requirement from applications. EGEE work - again, Security Taskforce recognised Usage Control and Accounting as significant area that is missing. GGF - various accounting and economic models working groups already running, with large UK contributions from Manchester and London e -Science centres. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003

Summary u VOMS n provides users with authorization credentials more scalable than current VO-LDAP system u GACL represents Grid access control policies (“access control lists”) in XML. u Grid. Site enforces these for web/fileservers. u Slash. Grid n being brought into this system as Apache module more portable and better able to handle partial remote file access. u Basic Usage Control possible using Unix mechanisms. u “Usage Peering” with retrospective targets would provide a way of doing accounting in the near term. u Aim to provide more advanced accounting tools for LCG etc in Grid. PP-2. Grid. PP / EDG / WP 6 Andrew Mc. Nab - Security - 1 July 2003