SECURITY ARCHITECTURE MODELS Seminario de Preparacin para el

















































- Slides: 66

SECURITY ARCHITECTURE & MODELS Seminario de Preparación para el Examen CISSP Gonzalo Espinosa, CISSP, CISM Abril 2006

Introduction The Enterprise Security Architecture domain contains the concepts, principles, structures, and standards used to design, monitor, and secure operating systems, hardware, networks, applications and those controls used to enforce various levels of availability, integrity, and confidentiality.

Introduction The infrastructure includes items such as: • Hardware • Software • Operating System and all associated functions • Applications • Utilities • Network environment • Security awareness and training • Information system security supporting policies, procedures, baselines, and standards

Objectives The CISSP should be able to: – Identify the security issues and controls that can be associated with architectures and designs. – Describe the principles of common computer and network organization, enterprise architectures, and designs. – Define and understand security models.

Definitions Enterprise - Multiple internal networks, internal areas or domains, and various internal devices and systems, applications, and a diverse user presence as a single collective unit. Architecture - The highest level concept of a system in its environment.

Definitions Security Architecture - A high-level design used to satisfy a system’s security requirements as defined in an organization’s security policy Enterprise Security Architecture - Defines the information security strategy that consists of layers of policy, standards, and procedures and the way they are linked across an enterprise

Common Computer Architecture Operating System Operating system services include: • • • Program execution Access to Input/Output devices Controlled access to files System access Error detection and response Accounting

CPU States • Supervisor State – Program can access entire system – Both privileged and non-privileged instructions • Problem State – User State or Program State – Only non-privileged instructions executed – Intended for application programs

CPU States (cont. ) Process States are: • Stopped vs. operating • Wait vs. running • Masked/interruptible – Example: If masked bit not set, interrupts are disabled (masked off) - known as IRQs in systems

CPU Process Threads • Many, if not most, of today’s programs are comprised of many individual modules, programs or processes that are separately written and work together to fulfill the overall objective of the application. • These may be called modules or process threads. • The security problems lie in the fact that these independent sections may be written by someone else then they may link dynamically and not be controlled by the Operating System.

Memory Management The five requirements for memory management are: 1. 2. 3. 4. Relocation Protection Sharing Logical Organization 5. Physical Organization

Platform - Memory Management Addressing • There are three types of memory addresses: – Logical - references to a memory location that is independent of the current assignment of data to memory. Requires a translation to the physical address – Relative - address expressed as a location relative to a known point – Physical - the absolute address or actual location

Virtual Memory • Extends memory by using secondary storage for program pages not being executed. • Composed of independent numbered segments.

Swapping • In a Virtual Memory system, swapping is the act of transferring pages between physical memory and the swap space on the disk • Pages are fixed blocks of memory usually 4 KBytes or 8 KBytes. • Swapped Pages are stored on disk • Pages are swapped into memory as needed – A page fault is taken when a reference is taken to a nonresident Page

Paging • Paging involves: – Splitting memory into equal sized, small chunks that are called page frames. – Splitting programs (processes) into equal sized small chunks that are called pages. – Allocate the required number page frames to a process. – Operating System maintains list of free frames.

Common Computer Architecture (I/O) Devices - Swapping and Paging • Paging is used to transfer data between the I/O device and main memory • Hardware must support paging and segmentation. • Operating system must be able to manage the movement of pages and/or segments between secondary memory and main memory.

Memory Protection • Protection Benefits – Every reference checked for protection. – Different data classes can be assigned different levels of protection. – Two or more users can share access to same segment with potentially different access rights. – User cannot generate an un-permitted address or gain access to an un-permitted segment.

Trusted Computing Base (TCB) • The Trusted Computing Base is the totality of protection mechanisms within a computer system including – – – hardware, firmware, software, processes, and some inter-process communications that combined are responsible for enforcing a security policy.

Trusted Computing Base (TCB) • The TCB maintains the confidentiality and integrity of each domain and monitors four basic functions: – – Process activation Execution domain switching Memory protection Input/Output operation

Trusted Computing Base (TCB) • Two primary concepts: – Subjects – Active entities - includes users, programs, processes, logon identifiers – Objects – Passive entities - includes files, programs, data, hardware

Objects Requiring Protection • Memory • File or Data Set • Executing Program in Memory • Directory of Files • Hardware Device • Data Structure • Operating System Table(s) • Instructions (especially privileged) • Passwords / Authentication Mechanisms • Protection Mechanisms

Reference Monitor Concept • Abstract machine that must mediate all access of subjects to objects. • Features include: – Must mediate all access – Be protected from modification – Be verifiable as correct – Always be invoked

Security Kernel The hardware, firmware, and software elements of a trusted computing base that implement the reference monitor concept.

Reference Monitor / Security Kernel • Complementary goals: – Check every access – Allow least privilege – Verify acceptable usage • Appropriate use • Authorization Concept

Privilege Levels • Subjects of higher trust can access more system instructions and operate in privileged mode • Subjects with lower trust can only access a smaller portion of system instructions and operate in user mode

Process Isolation • Preserve object’s integrity and subject’s adherence to access controls • Prevents objects from interacting with each other and their resources • Actions of one object should not affect the state of other objects

Process Isolation (cont. ) • Process Isolation: – Encapsulation of objects – Time multiplexing of shared resources – Naming distinctions – Virtual mapping

Layering and Data Hiding Layering: • Processes operate at different layers within a system and must communicate through interfaces – Layers can be divided by functionality or security Data Hiding: • If a process does not have an interface to another process at another layer, it cannot have access to its data

Security Domains • Sometimes referred to as a ‘execution’ or ‘protection’ domain. • Includes all objects that a subject has access to.

Virtual Machines • Virtual machines mimic the architecture of the actual system and on multilevel systems they can run at different security levels. • An operating system provides an application a working environment

Operating System Protection • User Identification and Authentication – Must authenticate or verify users to the system • Discretionary access control – All object access control left to owner • Mandatory access control – Access control decisions jointly controlled by object owner and the system

Operating System Protection • Complete mediation – All accesses must be intercepted and verified – Difficult as more paths are created • Object reuse protection – Memory leakage – Magnetic Remanence • Audit – Security-relevant events – Protection of audit logs

Operating System Protection • Audit log reduction – Volume and analysis problem – Simplification – Correlation • Trusted path – Protection of critical operations • Intrusion Detection – Patterns, Analysis, Recognition

Product Evaluation Criteria • Trusted Computer System Evaluation Criteria (TCSEC) The Orange Book • Trusted Network Interpretation (TNI) - The Red Book • Information Technology Security Evaluation Criteria (ITSEC) • Common Criteria

Common Criteria ISO 15408 • Provides a common structure and language for expressing product/system security evaluations and requirements • Provides a catalog of standardized security requirement components and packages

Parts of the Common Criteria • Part One: Introduction and General model • Part Two: Security Functional Requirements (defines 11 security functional components - Security Functional Requirements) • Part Three: Security Assurance Requirements (establishes a set of assurance components - Evaluation Assurance Levels)

Common Criteria Goals • Have a single international (common) product and system security criteria. • Resolve conceptual and technical differences between the various source criteria. • Provide an international mutual recognition of product evaluation. • Level international playing field for developers • Provide world-wide availability of security-capable products.

Common Criteria Key Terms • Protection Profile (PP) - an implementation-independent set of security functional and assurance requirements for a category of products that meet specific consumer needs. • Security Functional Requirements - requirements, that when taken together, specify the security capabilities of a product or system. • Security Assurance Requirements – address the confidence in the security capabilities of a product or system.

Common Criteria Key Terms (cont. ) • Security Target (ST) - a set of security functional and assurance requirements and specifications to be used as the basis for evaluation of an identified product or system. • Target of Evaluation (TOE) - another name for a product or system described in a Protection Profile or Security Target. The TOE is the entity that is subject to security evaluation.

Common Criteria Key Terms (cont. ) • Evaluation - assessment of a product or system against defined security functional and assurance criteria, performed by a combination of testing and analytic techniques. • Evaluation Assurance Level (EAL) - one of seven increasingly rigorous levels of assurance requirements. An EAL can be considered a level of confidence in the security functions of a product or system.

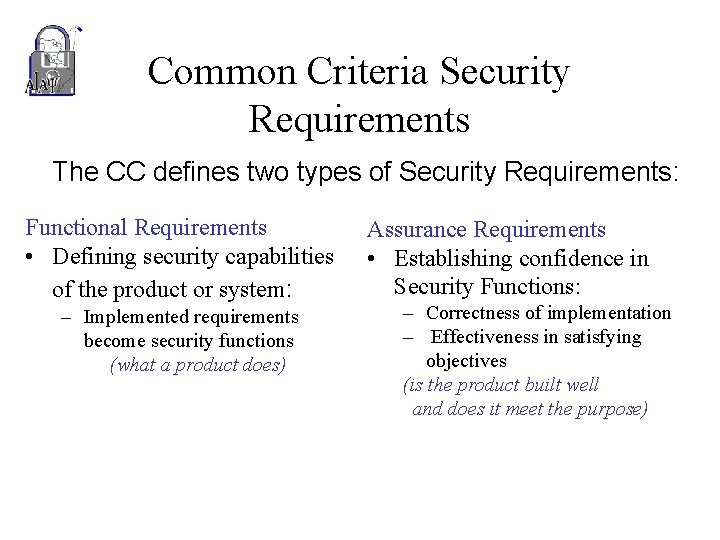
Common Criteria Security Requirements The CC defines two types of Security Requirements: Functional Requirements • Defining security capabilities of the product or system: – Implemented requirements become security functions (what a product does) Assurance Requirements • Establishing confidence in Security Functions: – Correctness of implementation – Effectiveness in satisfying objectives (is the product built well and does it meet the purpose)

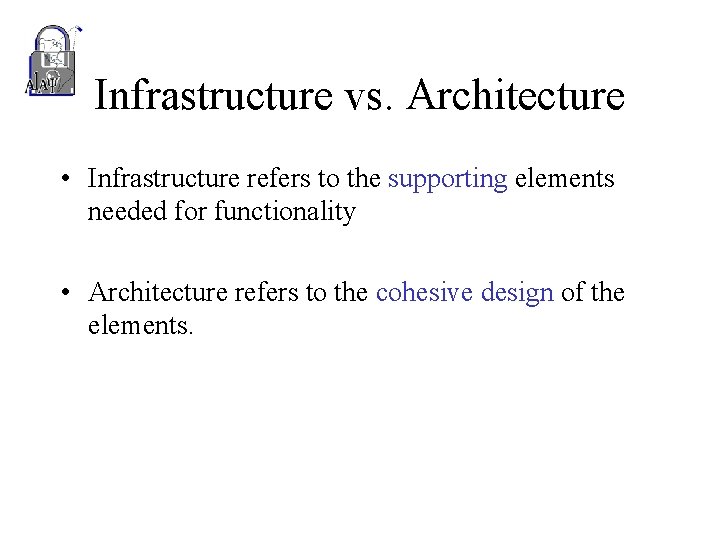
Infrastructure vs. Architecture • Infrastructure refers to the supporting elements needed for functionality • Architecture refers to the cohesive design of the elements.

Objectives of an Enterprise Security Architecture • Guidance for decision makers. – The resulting business and security decisions will be strategically aligned and consistent across the enterprise. – Provides specific security-related guidance to decision makers.

Objectives of an Enterprise Security Architecture (cont. ) • Security-related input into IT technology, system and application design. • Ensures application of security best practices. • Describes security zones, to compartmentalize the enterprise security environment.

The Enterprise Security Architecture… • Strategic – longer life than a blueprint, design specification, topology or configuration – Constrained by current or changing circumstances if too specific, – Cannot provide good guidance if it is too general, – Support long term view of technical direction, not short term technical constraints, – Not invalidated by changes in technical direction

The Enterprise Security Architecture… (cont. ) • Business centered acceptance and management of risk • Allows for multiple implementations depending on requirements – Guidance for implementation of security for internal and external organizations • Interoperability • Integration • Ease-of-use • Standardization

Benefits of an Enterprise Security Architecture • Consistently manage IT risk across the enterprise while leveraging industry best practices. • Reduce the costs of managing IT risk and improve flexibility by implementing common security solutions across the enterprise. • Allow decision makers to make better and quicker securityrelated decisions across the enterprise. • Promote interoperability, integration and ease-of-access while effectively managing risk. • Provide a reference for guidance to other organizations interacting with the enterprise.

IT Security Principles • Are fundamental statements of value, operation or belief that defines the overall approach to IT security, • Define the philosophy of the organization that directs the definition of the security policies, • Will require formal commitment from the executives to be relied upon for guidance, and • Often are challenging to define. – May require assistance with scope definition and management, issue validation, and the definition of the resulting Security Principles.

Enterprise Security Architecture The security architecture must address all components of the enterprise security program not just the technical components: • Strategic alignment • Process enhancement • Business Enablement • Security Foundation • Aligned with best practices

Bell-La. Padula Confidentiality Model • Formal treatment of information confidentiality issues. • Defines notion (concept) of secure state. – Secure state – access is only permitted in accordance with specific security policy. – Secure state is when rules are security-preserving.

Bell-La. Padula Confidentiality Model (cont. ) • Defines fundamental modes of access. – Read only, write only, or read and write. • Rules for giving subjects access to objects. – Dominance Relation • Clearances of subjects to classifications of objects. – Discretionary Security Property • Specific subject authorized for particular mode of access.

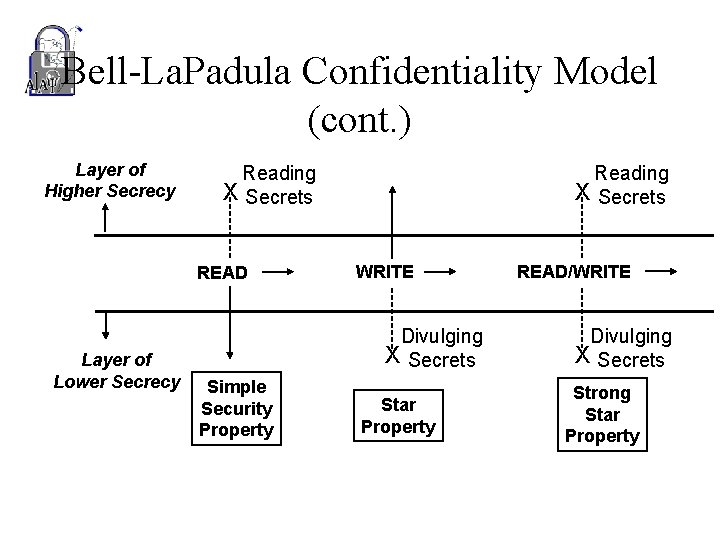
Bell-La. Padula Confidentiality Model (cont. ) • Bell-La. Padula introduced the following concepts: – Simple security property • Subject cannot read object of higher sensitivity. – Star property (* property) • Subject cannot write to object of lower sensitivity. – Strong Star property (Strong * property) • Subject cannot read/write to object of higher/lower sensitivity.

Bell-La. Padula Confidentiality Model (cont. ) Layer of Higher Secrecy READ Layer of Lower Secrecy Reading X Secrets WRITE Divulging X Secrets Simple Security Property Star Property READ/WRITE Divulging X Secrets Strong Star Property

Biba Integrity Model • First to address integrity in computer systems. • Based on hierarchical lattice of integrity levels. • Elements – Set of subjects (Active, information processing) – Set of objects (Passive, information repository) • Addresses first goal of integrity – Prevent unauthorized users from making modifications. • Mathematical dual of confidentiality policy – Access tuple: subject & object

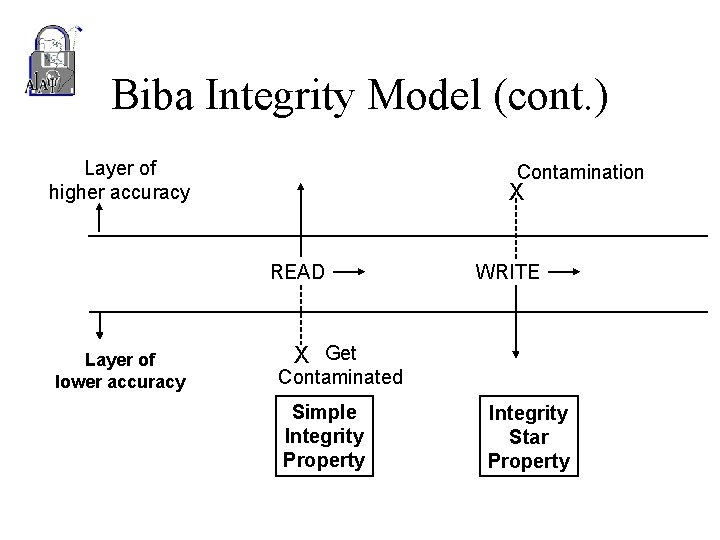
Biba Integrity Model (cont. ) Strict integrity policy: • Simple integrity condition – Subject cannot read objects of lesser integrity. • Integrity star * property – Subject cannot write to objects of higher integrity. • Invocation property – Subject cannot send messages (logical request for service) to subjects of higher integrity.

Biba Integrity Model (cont. ) Layer of higher accuracy Contamination X READ Layer of lower accuracy WRITE X Get Contaminated Simple Integrity Property Integrity Star Property

Clark and Wilson Integrity Model • Addresses all three integrity goals. – Preventing unauthorized users from making modifications. – Preventing authorized users from making improper modifications. – Maintaining internal and external consistency. • Well-formed transaction – Preserve/ensure internal consistency. – User can manipulate data only in ways that ensure internal consistency.

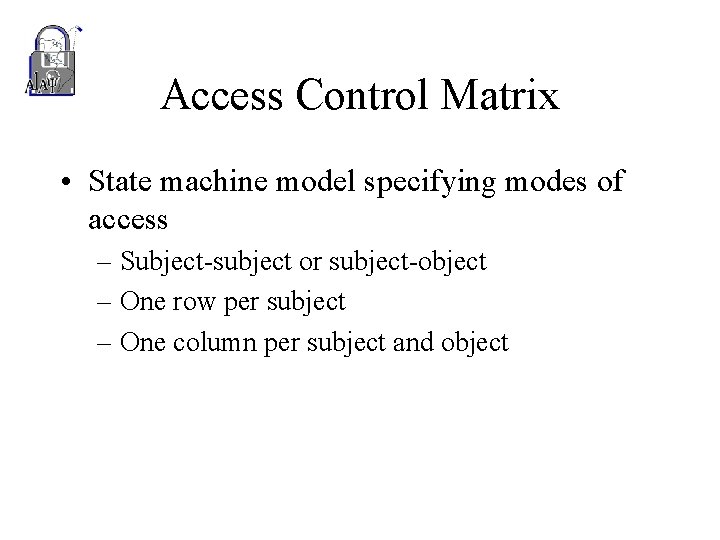
Access Control Matrix • State machine model specifying modes of access – Subject-subject or subject-object – One row per subject – One column per subject and object

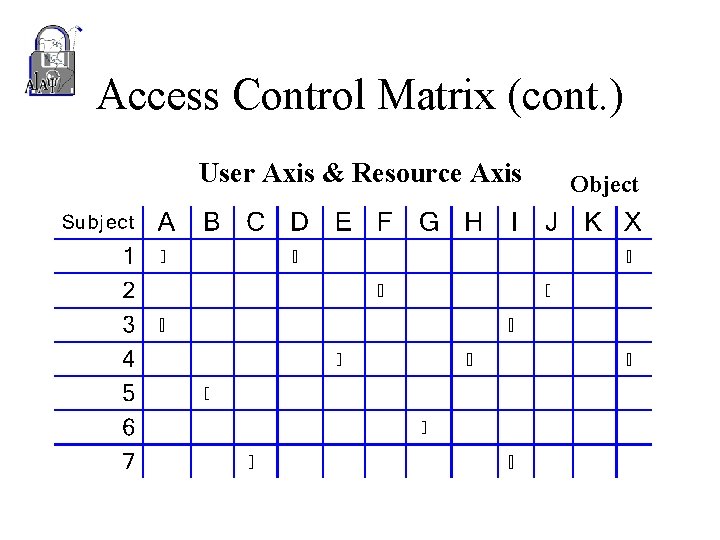
Access Control Matrix (cont. ) User Axis & Resource Axis Object

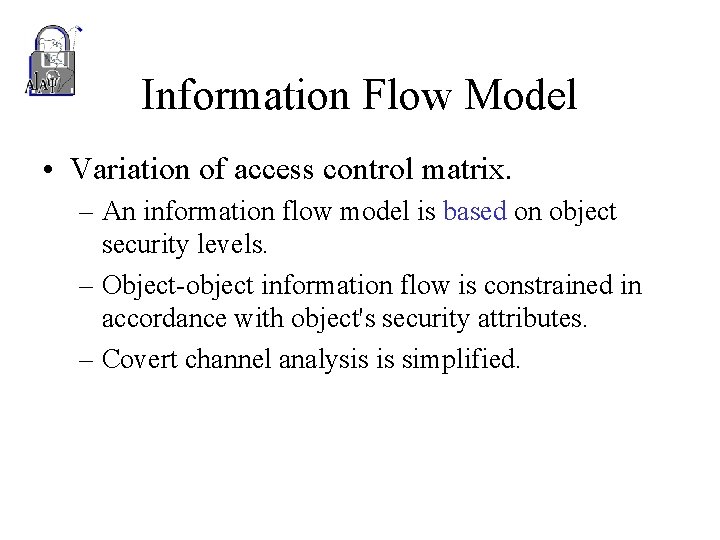
Information Flow Model • Variation of access control matrix. – An information flow model is based on object security levels. – Object-object information flow is constrained in accordance with object's security attributes. – Covert channel analysis is simplified.

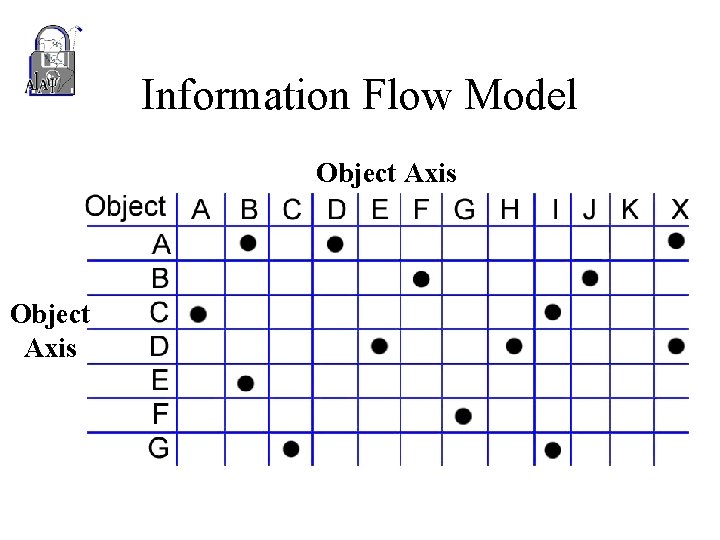
Information Flow Model Object Axis

Brewer and Nash Model – Chinese Wall Security Policy • Published in 1989 to ensure fair competition • Mathematical theory used to implement dynamically changing access permissions. • Defines a wall and develops a set of rules that ensure that no subject accesses objects on the other side of the wall. • Individuals are only allowed to access data that is not in conflict with data they accessed previously.

Brewer and Nash Model (cont. ) • It allows controls to be put into place to ensure that there is no conflict of interest. • If a user accesses one company’s data, the competitor’s data can automatically be deemed “off limits”. • Way of separating competitors’ data within the same integrated database. • Tries to ensure that users do not make fraudulent modifications to objects.

Other Security Models • Non-interference model - ways to prevent subjects operating in one domain from affecting each other in violation of security policy. • State machine model - abstract math model where state variables represent the system state. The transition functions define system moves between states. • Graham-Denning Model - Formal system of protection rules.

Other Security Models • Harrison-Ruzzo-Ullman Result - variation on Graham-Denning model. – In a model system, where commands are restricted to a single operation each, it is possible to decide whether a given subject can ever obtain a particular right to a given object. – If commands are not restricted to one operation each, it is not always decidable whether a given protection system can confer a given right.

SECURITY ARCHITECTURE & MODELS Seminario de Preparación para el Examen CISSP Gonzalo Espinosa, CISSP, CISM Abril 2006