Security and Wireless LANs Or Fun and Profit










- Slides: 15

Security and Wireless LANs Or Fun and Profit With Your Neighbor’s Bandwidth Chris Murphy MIT Information Systems

The Problem • Wireless LANs broadcast your network connections – Radio doesn’t care about firewalls – Data can be captured without physical access – Network resources can be hijacked


The Solution? • Access Control – By MAC addresses – By network names (SSID) • Data Encryption – WEP (Wired Equivalent Privacy) – Can also be used for access control • All these schemes have limits and flaws

MAC Address Access Control • Access Points have a list of allowed MAC addresses • Often stored in each Access Point – Limited to about 500 addresses • Some products use a server-based list, using systems like RADIUS • Easily defeated by sniffing for an allowed address

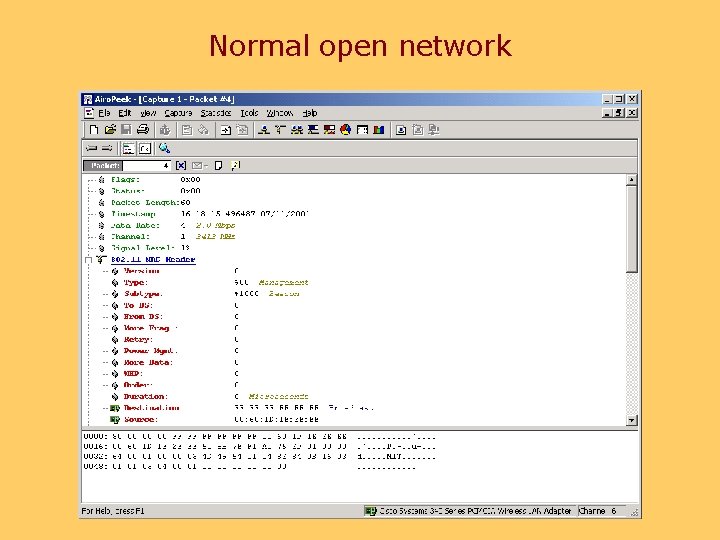
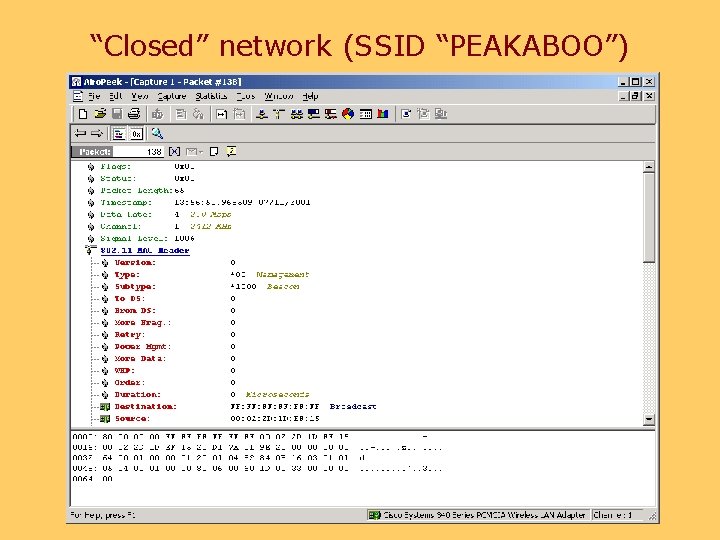
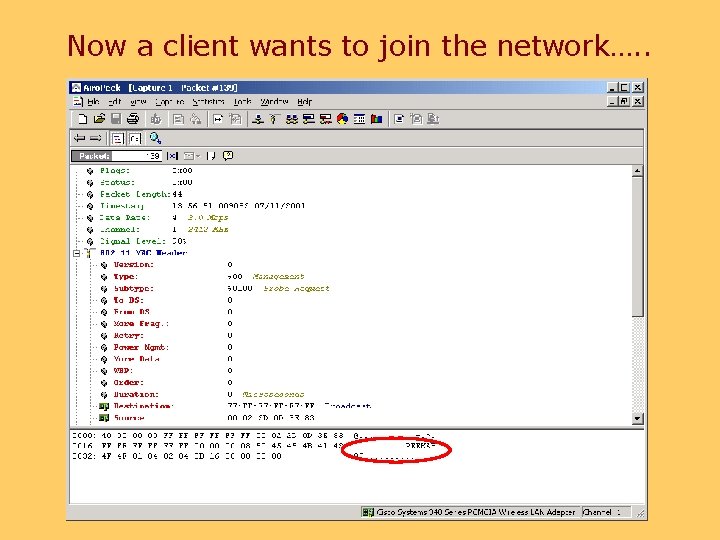
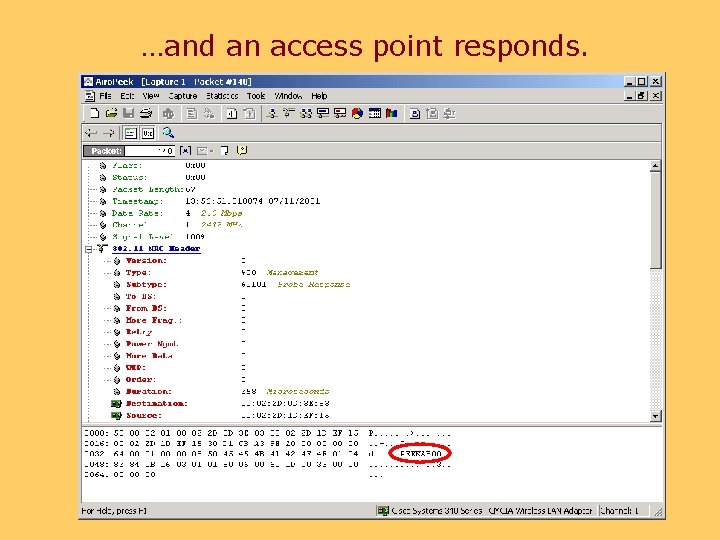
SSID Access Control • Normally, the SSID is broadcast in beacon packets • A “closed” network does not include the SSID in beacons • NOT part of the 802. 11 standard • Has a fatal flaw…. .

Normal open network

“Closed” network (SSID “PEAKABOO”)

Now a client wants to join the network…. .

…and an access point responds.

Data Encryption WEP – Wired Equivalent Privacy • 40 bit RC 4, 128 bit optional • Most APs support up to 4 keys • How do you manage keys in a large organization? • This assumes all users are “good guys”

Data Encryption • A group at Berkeley has published some flaws in WEP – http: //www. isaac. cs. berkeley. edu/isaac/wepfaq. html – Outlines a number of design flaws in WEP – A number of (currently theoretical) attacks are outlined in the referenced document – A response from the IEEE 802. 11 group chair is available at http: //www. wi-fi. com/pdf/Wi. Fi. WEPSecurity. pdf

Spread Spectrum as Security? • Spread Spectrum technology, while touted as difficult to intercept, offers little here as NICs are preprogrammed with the spreading sequences and can talk to each other out of the box.

So What Are Our Options? • While flawed, the described methods can provide some protection from casual abuse • Treat wireless clients as remote clients – Place APs outside firewalls – Use VPNs to access internal network • And as always, use secure protocols

Future Wireless Security • 802. 11 e should provide a standardsbased path for actual user authentication, and negotiation of user and session specific encryption keys • This group is working in conjunction with the 802. 1 x group, relating to per-port network access control