SECURITY AND PRIVACY FOR STORAGE AND COMPUTATION IN













- Slides: 22

SECURITY AND PRIVACY FOR STORAGE AND COMPUTATION IN CLOUD COMPUTING Lifei Wei, Haojin Zhu, Zhenfu Cao, Xiaolei Dong, Weiwei Jia, Yunlu Chen, Athanasios V. Vasilakos Presented By: Srinivas Balivada

OUTLINE: 1) Introduction 2) Problem Formulation 3) Basic Sec. Cloud Platform 4) Advanced Protocol with Batch Verification 5) Security Analysis 6) Performance Analysis 7) Conclusions

INTRODUCTION: � Cloud Computing Cloud computing is a new computing paradigm that aims to provide reliable, customized and quality of service guaranteed computation environments for cloud users. � Benefits of Cloud Computing � � � Flexible way to obtain computation and storage resources on demand. Avoids potentially large up-front investment. Reduce operational costs through economies of scale by the help of Pay as you go scheme. Managements of physical data and machines are delegated to the Cloud Service Providers Optimum Utilization of commonly shared computation resources.

INTRODUCTION (CONTD. ): Cloud Computing Security: Can be classified into two major classes : � Cloud Storage Security: � Cloud Computation Security: � Concerns in Cloud Computing Security:

INTRODUCTION (CONTD. ): � Approaches to Cloud Computation Security: Prevent the cloud users from incurring expensive verification costs by introducing a trusted auditor who conducts cloud auditing on behalf of the users. � To achieve secure computing auditing in cloud, one straightforward method is to double-check each result. � The cloud providers may give the inputs and overall computing result to the auditor, which will follow an identical procedure to compute the result and then compare it with the one provided by the cloud providers. However, these schemes may lead to a wastage of time and computation resources. �

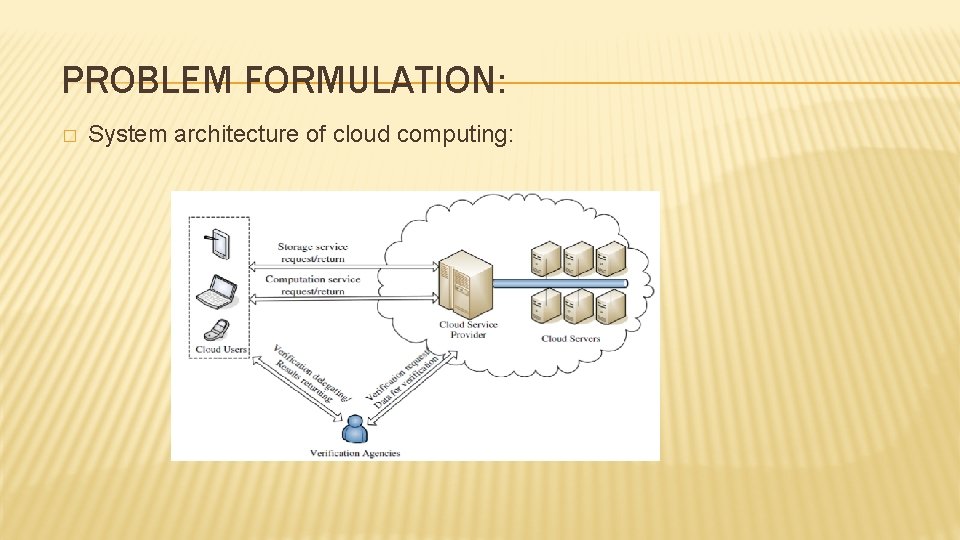
PROBLEM FORMULATION: � System architecture of cloud computing:

PROBLEM FORMULATION(CONTD. ): � Adversarial Model: An Adversary A could corrupt a small set of cloud servers and control these servers to launch various cheating attacks. The various attacks are: � Storage Cheating Attack Model: � Computation Cheating Attack Model: . Privacy Cheating Attack Model: � Privacy-cheating discouragement: �

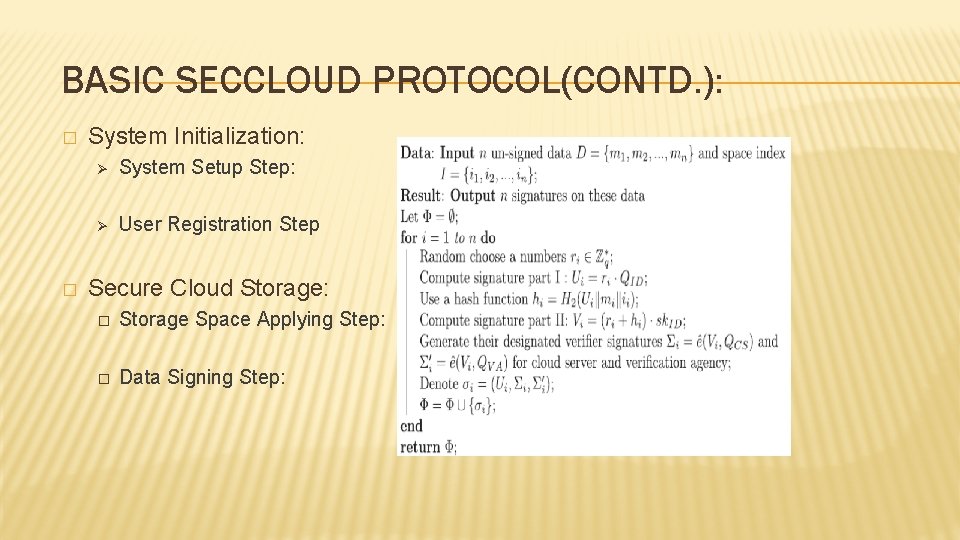
PROBLEM FORMULATION(CONTD. ): Design Goals: The proposed protocol is expected to achieve the following security and performance goals: � Data Storage Security: � Data Computation Security: � Privacy Cheating Discouragement: � Efficiency: � � It relies on Identity based cryptography and consists of four phases : Ø Ø System Initialization Secure Cloud Storage Secure Cloud Computation Result Auditing

BASIC SECCLOUD PROTOCOL(CONTD. ): � � System Initialization: Ø System Setup Step: Ø User Registration Step Secure Cloud Storage: � Storage Space Applying Step: � Data Signing Step:

BASIC SECCLOUD PROTOCOL(CONTD. ): � Secure Cloud Storage: • Data Encapsulation Step • � Data Receiving Step Secure Cloud Computation: The protocol is based on a commitment scheme using Merkle hash tree and has 2 steps: � Computation Request Step: � Commitment Generation Step:

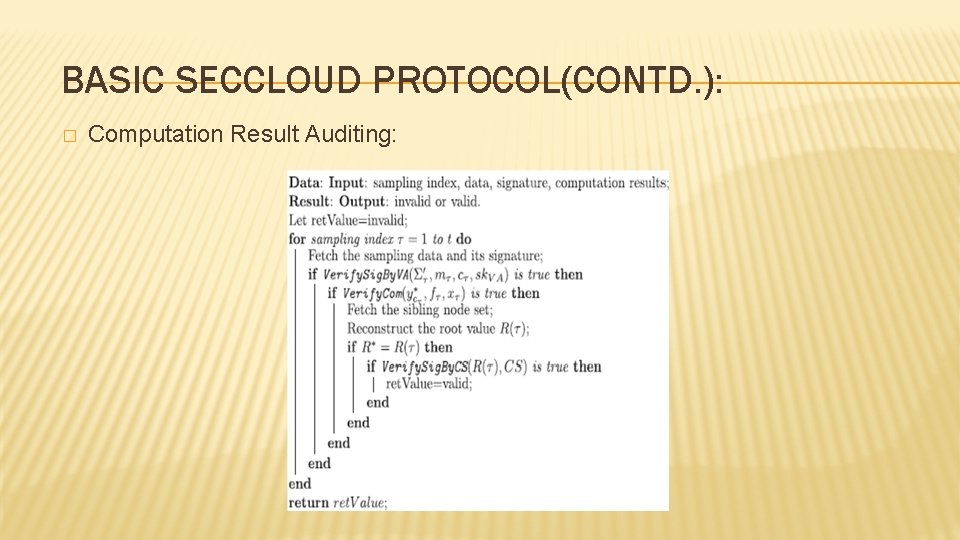
BASIC SECCLOUD PROTOCOL(CONTD. ): � Computation Result Auditing: � CU sends {F, P, Y, R, Sig. CS(R)} as well as a warrant include the identity of the delegate right and the expired time to VA for auditing. � VA not only checks if the data has been appropriately stored at the cloud server but also ensures if the computation process has been performed correctly. � Auditing Challenge Step: � Auditing Response Step:

BASIC SECCLOUD PROTOCOL(CONTD. ): � Computation Result Auditing:

ADVANCED PROTOCOL WITH BATCH VERIFICATION: � � � The authors introduce an advanced protocol to further reduce the computational and communication overhead comes from verification of the signatures. The idea comes from aggregate signatures with batch verification. The scheme can achieve almost constant computation overhead for VA in the data verification as well as CSP. VA can concurrently handle multiple verification requests from various clouds. Given n unauthenticated signatures, in such batch verification, the major computational cost is bounded by 2 pairings while it costs 2 n pairings by individual verification, which is a significant improvement on computational efficiency.

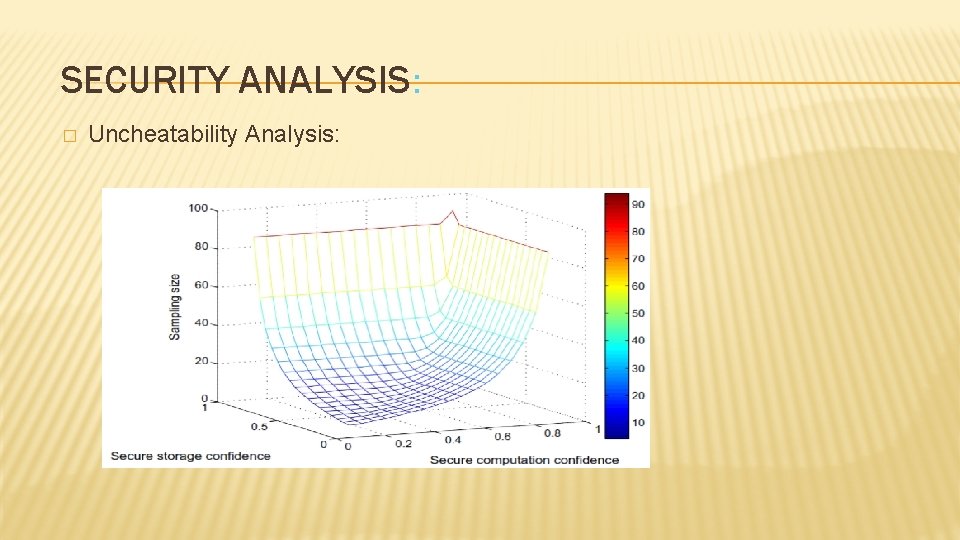
SECURITY ANALYSIS: � Uncheatability Analysis:

SECURITY ANALYSIS(CONTD. ): � Privacy Discouragement Analysis: � Optimal Sample Size to Minimize Total Cost: � Cryptographic Overhead Evaluation:

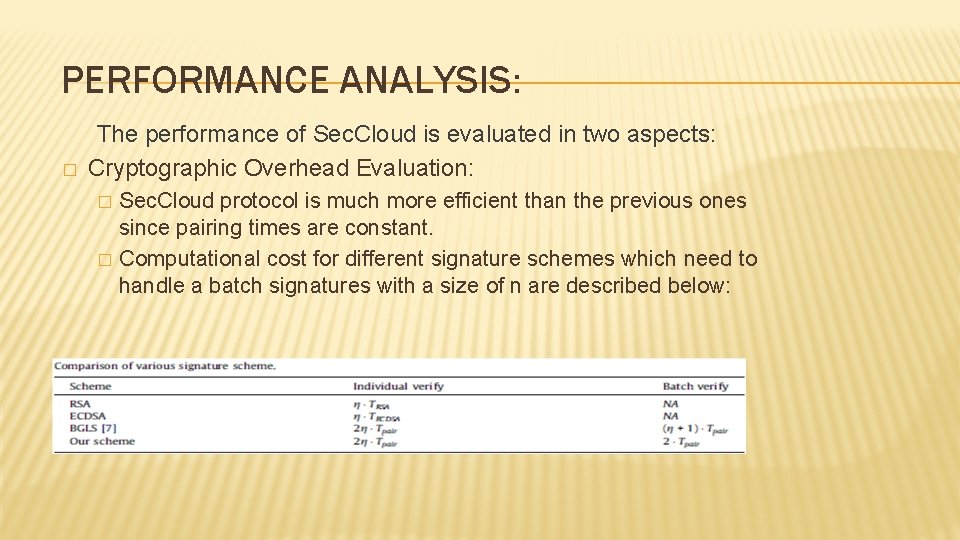
PERFORMANCE ANALYSIS: � The performance of Sec. Cloud is evaluated in two aspects: Cryptographic Overhead Evaluation: � � Sec. Cloud protocol is much more efficient than the previous ones since pairing times are constant. Computational cost for different signature schemes which need to handle a batch signatures with a size of n are described below:

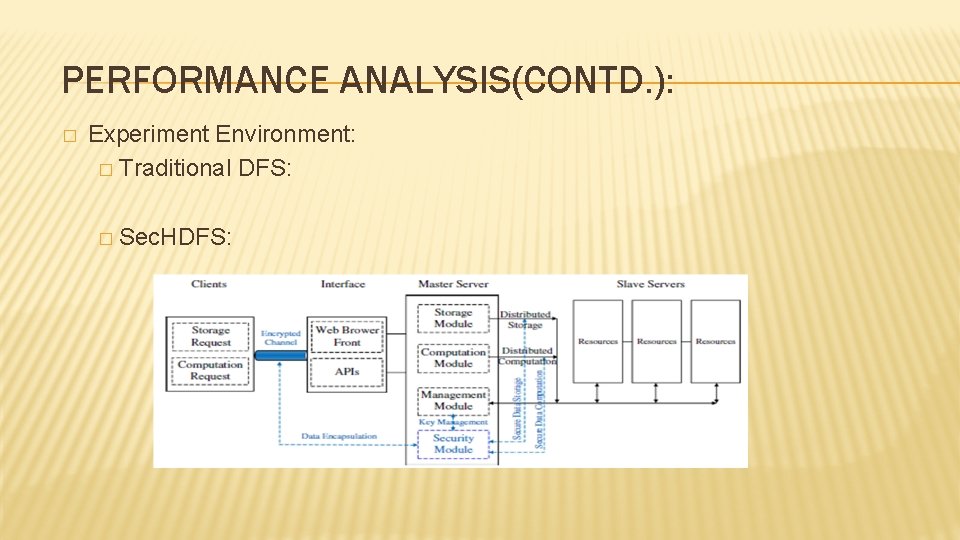
PERFORMANCE ANALYSIS(CONTD. ): � Experiment Environment: � Traditional DFS: � Sec. HDFS:

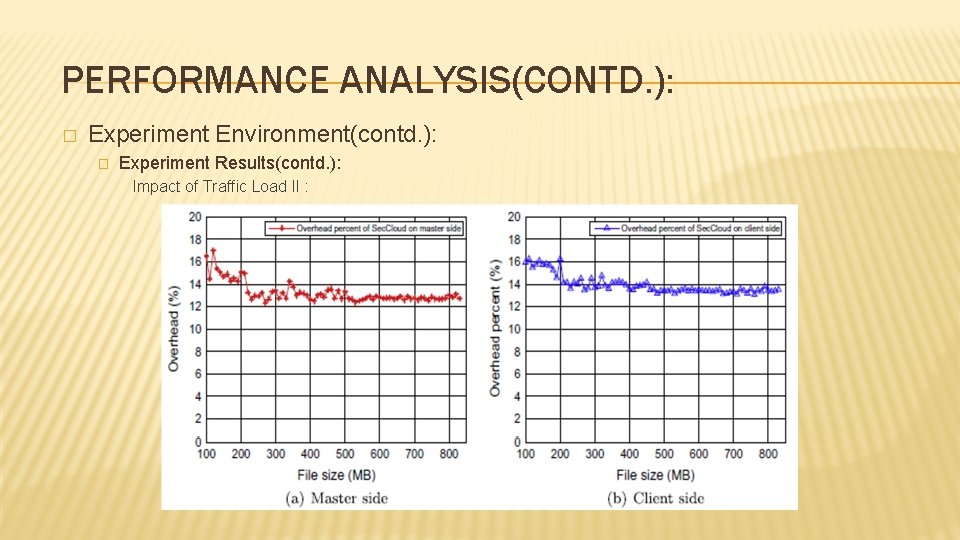
PERFORMANCE ANALYSIS(CONTD. ): � Experiment Environment(contd. ): � Experiment Results(contd. ): Impact of Traffic Load II : and in the client’s side, respectively.

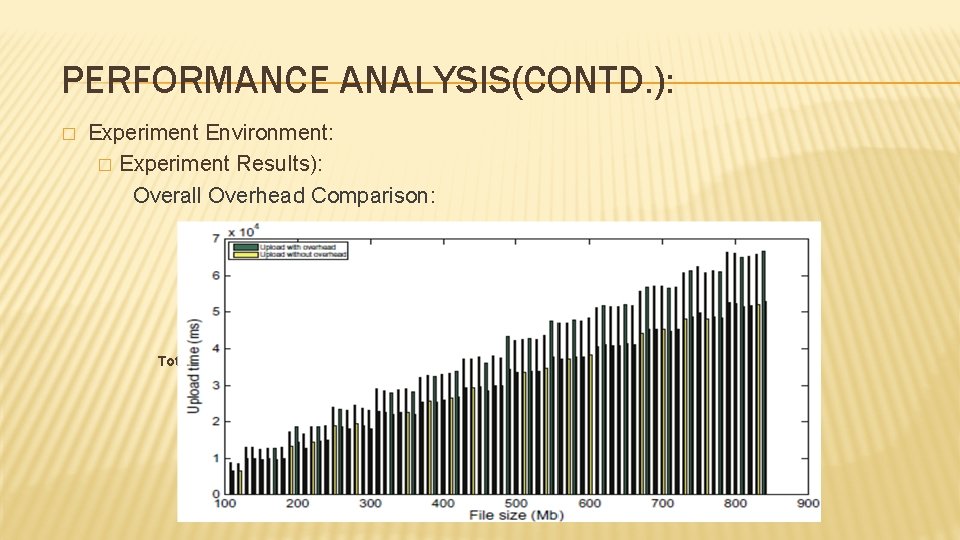
PERFORMANCE ANALYSIS(CONTD. ): � Experiment Environment: � Experiment Results): Overall Overhead Comparison: Total uploading time comparison between the original protocol and Sec. Cloud.

CONCLUSION: � The authors have proposed, Sec. Cloud, a privacy-cheating discouragement and securecomputation auditing protocol for data security in the cloud. � It is the first work that jointly considers both of data storage security and computation auditing security in the cloud. � The authors defined the concepts of uncheatable cloud computation and privacy-cheating discouragement and proposed Sec. Cloud to achieve the security goals.

CONCLUSION: � To improve the efficiency, different users’ requests can be concurrently handled through the batch verification. � By the extensive security analysis and performance simulation in the developed Sec. HDFS, it is showed that protocol is effective and efficient for achieving secure cloud computing without affecting the system performance. � Future Works : �Consideration some detailed computation such as linear program computation and data mining and formalize these security models in the cloud computing.

THANK YOU