Security and Cryptography CS502 Operating Systems Fall 2007





















![Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp('binsh', 'bin Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp('binsh', 'bin](https://slidetodoc.com/presentation_image_h2/962e34923f163f10181ed69e4958abab/image-27.jpg)
























- Slides: 54

Security and Cryptography CS-502 Operating Systems Fall 2007 (Slides include materials from Operating System Concepts, 7 th ed. , by Silbershatz, Galvin, & Gagne and from Modern Operating Systems, 2 nd ed. , by Tanenbaum) CS-502 Fall 2007 Security and Cryptography 1

Puzzle • Alice wishes to send secret message to Bob – She places message in impenetrable box – Locks the box with unbreakable padlock – Sends locked box to Bob • Problem: – Bob has no key to unlock box – No feasible way to securely send key to Bob • How does Bob retrieve message? CS-502 Fall 2007 Security and Cryptography 2

Answer • Bob adds 2 nd unbreakable padlock to box – Locks with own key – Sends box back to Alice (with two padlocks!) • Alice unlocks and removes her lock – Sends box back to Bob • Bob unlocks his lock – Opens box and reads message • What could go wrong? CS-502 Fall 2007 Security and Cryptography 3

Authentication • How does the machine know who it is talking to? • Who do I say that I am? • How can I verify that? • Something I know (that nobody else should know) • Something I have (that nobody else should have) • Something I am (that nobody else should be…) CS-502 Fall 2007 Security and Cryptography 4

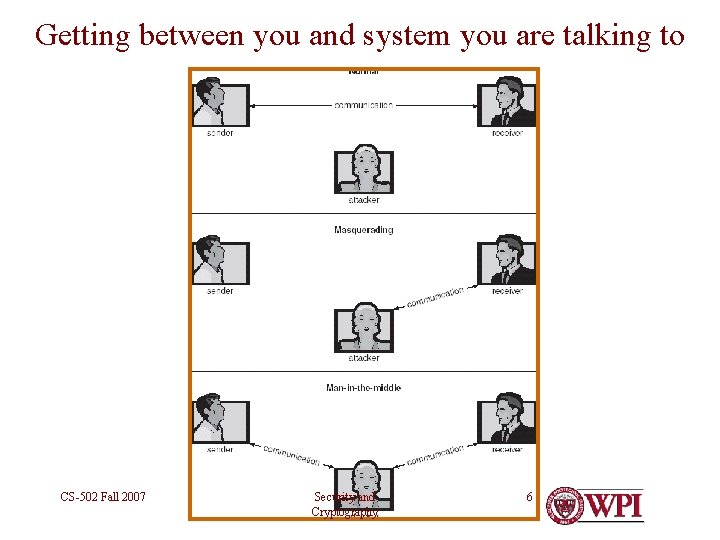
Threats against authentication I want to pretend to be you: • I can steal your password – the sticky note on your monitor or the list in your desk drawer – by monitoring your communications or looking over your shoulder • I can guess your password – particularly useful if I can also guess your user name • I can get between you and the system you are talking to CS-502 Fall 2007 Security and Cryptography 5

Getting between you and system you are talking to CS-502 Fall 2007 Security and Cryptography 6

Login Spoof • I create a login screen in my process – On a public machine – Looks exactly like real one • You log into system – My login process records your user ID and password – Logs you in normally • Result: – I have gotten between you and system without your knowledge – Also, I have stolen your user ID and password CS-502 Fall 2007 Security and Cryptography 7

The Trouble with Passwords • • • They are given away They are too easy to guess They are used too often There are too many of them They are used in too many places CS-502 Fall 2007 Security and Cryptography 8

Some ways around the problem • Better passwords – longer – larger character set – more random in nature/encrypted • Used less often – changed frequently, one system per password – challenge/response – use only once CS-502 Fall 2007 Security and Cryptography 9

The Challenge/Response Protocol Art Mary Hello, I’m Art Decrypt This {R}P R Hello Art! How can I help you? CS-502 Fall 2007 Security and Cryptography 10

Threat: Steal passwords from the system • Don’t keep them in an obvious place • Encrypt them so that version system sees is not same as what user enters – or version on the wire CS-502 Fall 2007 Security and Cryptography 11

Too many passwords to remember? • Third-party authentication – Get someone to vouch for you • The basics: “This guy says you know him. . ” “Yes, I trust him, so you should too. . ” • Kerberos – Certificate-based authentication within a trust community CS-502 Fall 2007 Security and Cryptography 12

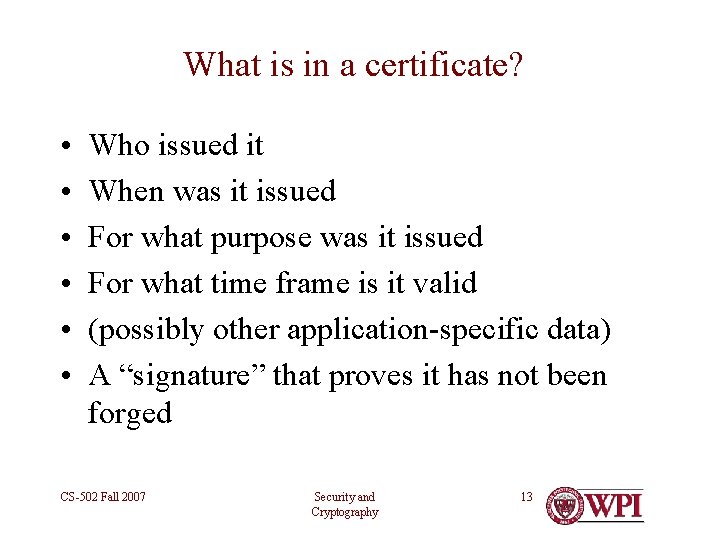
What is in a certificate? • • • Who issued it When was it issued For what purpose was it issued For what time frame is it valid (possibly other application-specific data) A “signature” that proves it has not been forged CS-502 Fall 2007 Security and Cryptography 13

Systems and Networks Are Not Different • Same basic rules about • Same coding rules code behavior apply to: – An application • Same authentication – Code which manages rules apply incoming messages • The same security – Code which imposes principles apply access controls on a network –. . . CS-502 Fall 2007 Security and Cryptography 14

The Principles • Understand what you are trying to protect • Understand the threat(s) you are trying to protect against – Also, costs and risks • Be prepared to establish trust by telling people how you do it • Assume that the bad guys are at least as clever as you are! CS-502 Fall 2007 Security and Cryptography 15

Security must occur at four levels to be effective • Physical – The best security system is no better than the lock on your front door (or desk, or file cabinet, etc. )! • Human – Phishing, dumpster diving, social engineering • Operating System – Protection and authentication subsystems • Network – Similar to OS • Security is as weak as the weakest link in chain CS-502 Fall 2007 Security and Cryptography 16

How do these attacks work? • Messages that attack mail readers or browsers • Denial of service attacks against a web server • Password crackers • Viruses, Trojan Horses, other “malware” CS-502 Fall 2007 Security and Cryptography 17

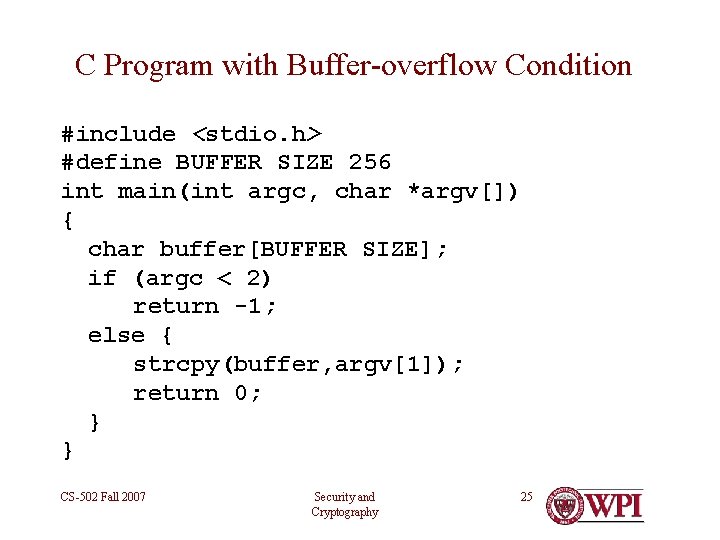
The concept of a “Vulnerability” • Buffer overflow • Protocol/bandwidth interactions – Protocol elements which do no work • “execute this” messages – The special case of “mobile agents” • Human user vulnerabilities – e. Mail worms – Phishing CS-502 Fall 2007 Security and Cryptography 18

Another Principle • There is a never-ending war going on between the “black hats” and the rest of us. • For every asset, there is at least one vulnerability • For every protective measure we add, “they” will find another vulnerability CS-502 Fall 2007 Security and Cryptography 19

Yet Another Principle • There is no such thing as a bullet-proof barrier • Every level of the system and network deserves an independent threat evaluation and appropriate protection • Only a multi-layered approach has a chance of success! CS-502 Fall 2007 Security and Cryptography 20

Actual Losses: • Approximately 70% are due to user error • More than half of the remainder are caused by insiders • “Social Engineering” accounts for more loss than technical attacks. CS-502 Fall 2007 Security and Cryptography 21

What is “Social Engineering”? “Hello. This is Dr. Burnett of the cardiology department at the Conquest Hospital in Hastings. Your patient, Sam Simons, has just been admitted here unconscious. He has an unusual ventricular arrhythmia. Can you tell me if there is anything relevant in his record? ” CS-502 Fall 2007 Security and Cryptography 22

Social Engineering (2) From: 3 dksobinsky@zoom-internet. net Sent: Sunday, December 3, 2006 8: 10 AM To: rmstronger@charter. net Subject: Re: Approved Please read the attached file. CS-502 Fall 2007 Security and Cryptography 23

Program Threats • Trojan Horse – Code segment that misuses its environment – Exploits mechanisms for allowing programs written by users to be executed by other users – Spyware, pop-up browser windows, covert channels • Trap Door – Specific user identifier or password that circumvents normal security procedures – Could be included in a compiler • Logic Bomb – Program that initiates a security incident under certain circumstances • Stack and Buffer Overflow – Exploits a bug in a program (overflow either the stack or memory buffers) CS-502 Fall 2007 Security and Cryptography 24

C Program with Buffer-overflow Condition #include <stdio. h> #define BUFFER SIZE 256 int main(int argc, char *argv[]) { char buffer[BUFFER SIZE]; if (argc < 2) return -1; else { strcpy(buffer, argv[1]); return 0; } } CS-502 Fall 2007 Security and Cryptography 25

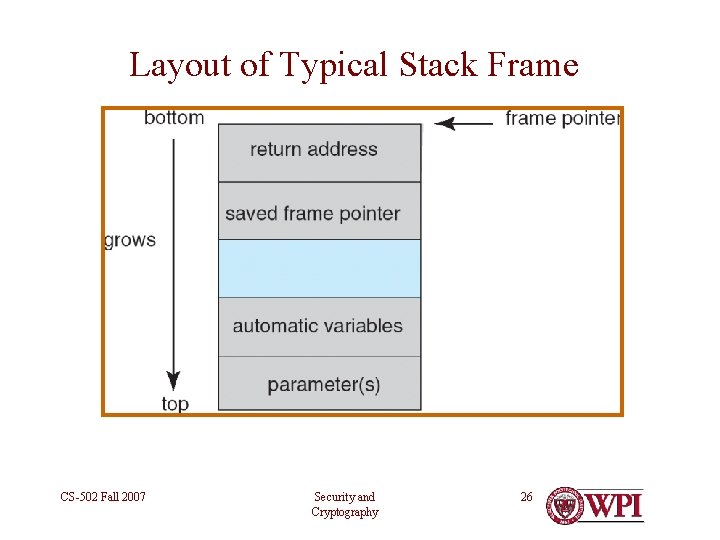
Layout of Typical Stack Frame CS-502 Fall 2007 Security and Cryptography 26
![Modified Shell Code include stdio h int mainint argc char argv execvpbinsh bin Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp('binsh', 'bin](https://slidetodoc.com/presentation_image_h2/962e34923f163f10181ed69e4958abab/image-27.jpg)
Modified Shell Code #include <stdio. h> int main(int argc, char *argv[]) { execvp('binsh', 'bin sh', NULL); return 0; } CS-502 Fall 2007 Security and Cryptography 27

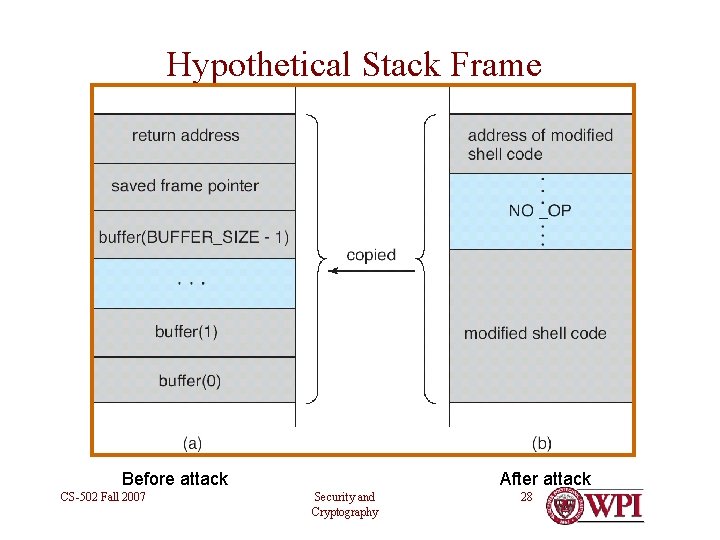
Hypothetical Stack Frame After attack Before attack CS-502 Fall 2007 Security and Cryptography 28

Effect • If you can con a privileged program into reading a string into a buffer unprotected from overflow, then … • …you have just gained the privileges of that program in a shell! CS-502 Fall 2007 Security and Cryptography 29

Program Threats – Viruses • Code fragment embedded in legitimate programs • Very specific to CPU architecture, operating system, applications • Usually borne via email or as a macro • E. g. , Visual Basic Macro to reformat hard drive Sub Auto. Open() Dim o. FS Set o. FS = Create. Object(’’Scripting. File. System. Object’ ’) vs = Shell(’’c: command. com /k format c: ’’, vb. Hide) End Sub CS-502 Fall 2007 Security and Cryptography 30

Program Threats (Cont. ) • Virus dropper inserts virus onto the system • Many categories of viruses, literally many thousands of viruses – – – – – File Boot Macro Polymorphic Source code Encrypted Stealth Tunneling Multipartite Armored CS-502 Fall 2007 Security and Cryptography 31

Questions? CS-502 Fall 2007 Security and Cryptography 32

Part 3: Fun with Cryptography • What is cryptography about? • General Principles of Cryptography • Basic Protocols – Single-key cryptography – Public-key cryptography • An example. . . CS-502 Fall 2007 Security and Cryptography 33

Cryptography as a Security Tool • Broadest security tool available – Source and destination of messages cannot be trusted without cryptography – Means to constrain potential senders (sources) and / or receivers (destinations) of messages • Based on secrets (keys) CS-502 Fall 2007 Security and Cryptography 34

Principles • Cryptography is about the exchange of messages • The key to success is that all parties to an exchange trust that the system will both protect them from threats and accurately convey their message • TRUST is essential CS-502 Fall 2007 Security and Cryptography 35

Therefore • Algorithms must be public and verifiable • We need to be able to estimate the risk of compromise • The solution must practical for its users, and impractical for an attacker to break CS-502 Fall 2007 Security and Cryptography 36

Guidelines • Cryptography is always based on algorithms which are orders of magnitude easier to compute in the forward (normal) direction than in the reverse (attack) direction. • The attacker’s problem is never harder than trying all possible keys • The more material the attacker has the easier his task CS-502 Fall 2007 Security and Cryptography 37

Example • What is 314159265358979? vs. • What are prime factors of 3912571506419387090594828508241? CS-502 Fall 2007 Security and Cryptography 38

Time marches on… • We must assume that there will always be improvements in computational power, mathematics and algorithms. – Messages which hang around get less secure with time! • Increases in computing power help the good guys and hurt the bad guys for new and short-lived messages CS-502 Fall 2007 Security and Cryptography 39

Caveat • We cannot mathematically PROVE that the inverse operations are really as hard as they seem to be…It is all relative… The Fundamental Tenet of Cryptography: If lots of smart people have failed to solve a problem, it won’t be solved (soon) CS-502 Fall 2007 Security and Cryptography 40

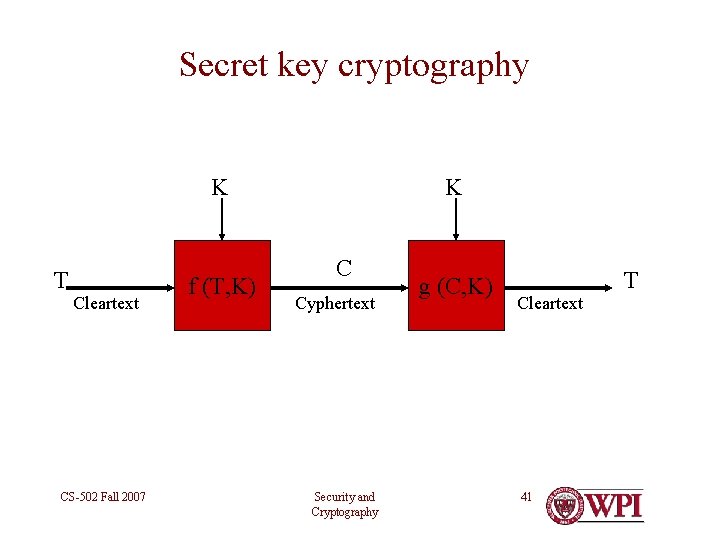
Secret key cryptography K T Cleartext CS-502 Fall 2007 f (T, K) K C Cyphertext Security and Cryptography g (C, K) Cleartext 41 T

Secret Key Methods • DES (56 bit key) • IDEA (128 bit key) • http: //www. mediacrypt. com/community/index. asp • Triple DES (three 56 bit keys) • AES – From NIST, 2000 – choice of key sizes up to 256 bits and more – Commercial implementations available CS-502 Fall 2007 Security and Cryptography 42

Diffie – Hellman Alice Agree on p, g choose random A Bob choose random B TA = g. A mod p TB = g. B mod p compute (TB)A compute (TA)B Shared secret key is g. AB mod p CS-502 Fall 2007 Security and Cryptography 43

D–H Problems • Not in itself an encryption method – we must still do a secret key encryption • Subject to a “man in the middle” attack – (Alice thinks she is talking to Bob, but actually Trudy is intercepting all of the messages and substitution her own) CS-502 Fall 2007 Security and Cryptography 44

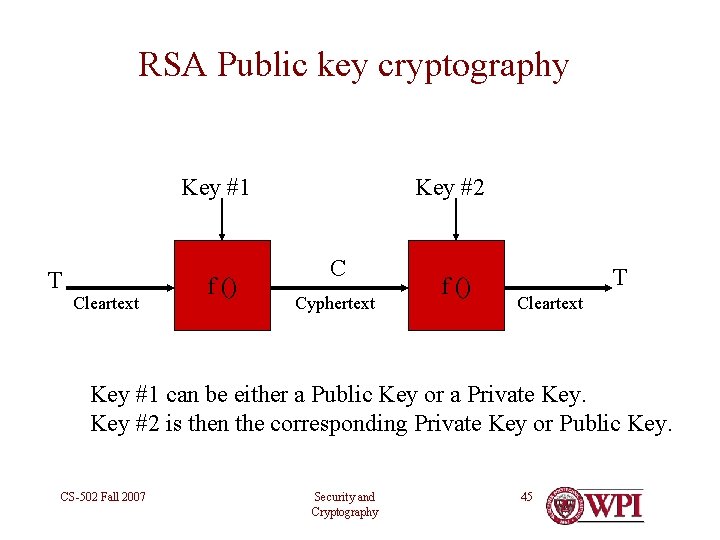
RSA Public key cryptography Key #1 T Cleartext f () Key #2 C Cyphertext f () T Cleartext Key #1 can be either a Public Key or a Private Key #2 is then the corresponding Private Key or Public Key. CS-502 Fall 2007 Security and Cryptography 45

RSA Public Key Cryptography • Rivest, Shamir and Adelman (1978) • I can send messages that only you can read • I can verify that you and only you could have sent a message • I can use a trusted authority to distribute my public key – The trusted authority is for your benefit! CS-502 Fall 2007 Security and Cryptography 46

RSA Details • We will use the same operation to encrypt and decrypt • To encrypt, we will use “e” as a key, to decrypt we will use “d” as a key • e and d are inverses with respect to the chosen algorithm CS-502 Fall 2007 Security and Cryptography 47

RSA Details • Choose n as the product of two large primes – Finding the factors of a large number is mathematically hard (difficult) – Finding primes is also hard • Choose e to be a (fairly small) prime and compute d from e and the factors of n • THROW AWAY THE FACTORS OF n! • Publish two numbers, e (public key) and n CS-502 Fall 2007 Security and Cryptography 48

RSA Details • Encryption: Cyphertext = (Cleartext)e mod n • Decryption: Cleartext = (Cyphertext)d mod n • Typical d will be on the order of 500 to 700 bits • The cost of the algorithm is between 1 and 2 the size of n, – Each operation is a giant shift and add (multiply by a power of 2) CS-502 Fall 2007 Security and Cryptography 49

RSA Problems • It is much more costly than typical secretkey methods – Use RSA to hide (i. e. , encrypt) a secret key, – Encrypt the message with the secret key and append/prefix the encrypted key • Requires a “Public Key Infrastructure” for effective key generation and distribution – Chain of trust thing again! CS-502 Fall 2007 Security and Cryptography 50

Message Digests (aka Digital Signatures) • A message digest is a non-reversable algorithm which reduces a message to a fixed-length “summary” • The summary has the property that a change to the original will produce a new summary • The probability that the new summary is the same as the old should be 1/(size of digest) • Silbershatz, p. 582 (§ 15. 4. 1. 3) CS-502 Fall 2007 Security and Cryptography 51

Message Digests (2) • There are several good (but possibly no perfect) message digest algorithms • MD 5 is probably the most common one in use – 128 bit digest • has known weaknesses • SHA-1 – 160 bit digest (current best choice) • [Another product of NIST] CS-502 Fall 2007 Security and Cryptography 52

Conclusion • Protection in OS is • Difficult • Important • Security is needed for • Authentication of users • Validation of communication CS-502 Fall 2007 Security and Cryptography 53

Reading Assignment Silbershatz, Chapter 15 CS-502 Fall 2007 Security and Cryptography 54