Security Analysis of Block Cipher 2002 10 8

Security Analysis of Block Cipher 2002. 10. 8 20022057 Park, Sang. Bae
Contents q Introduction of Boolean Function q Block Cipher Design Review – Cryptanalysis Method &Provable Security q Design Issue – S-box Design & Diffusion Layer q Example of S-box analysis q Future Works pinnon@lycos. co. kr 1
Introduction q Boolean Fucntion – Function from GF(2 n) to GF(2 m) – Generally, when m > 1, Vector-valued Boolean Function (or Vector Boolean Function) – Example • f(x 1, x 2, x 3) = x 1 x 2 + x 2 x 3 • Sequence of f(): 00010010 pinnon@lycos. co. kr 2
Introduction q Block Cipher as Boolean Function – Block Cipher • F: P ⅹ K → C with F(P, K) = C • GF(2128) ⅹ GF(2128) → GF(2128) – Round Function • f: Pi ⅹ Ki → Ci with F(Pi, Ki) = Ci • GF(264) ⅹ GF(264) → GF(264) – S-box • s: Ini ⅹ ki → Outi with F(Ini, ki) = Outi • GF(28) ⅹ GF(28) → GF(28) pinnon@lycos. co. kr 3
Basic Properties q Representation – The Algebraic Normal Form • Well known representation • ex) x 1 x 2 + x 3 x 1 – The Sequence of Given function • Value of given Boolean function • ex) 00010010 – The Walsh-Hadamard Transform • The correlation value to linear functions • ex) 2 0 -2 0 0 2 0 -2 pinnon@lycos. co. kr 4
Basic Properties q Balancedness – Hamming weight of given sequence q Nonlinear Order – Algebraic Nonlinear Order (Not Robust) q Completeness – Every input bit affect to the outptu bit pinnon@lycos. co. kr 5
Basic Properties q Nonlinearity – minimum Hamming distance to linear functions q Correlation – autocorrelation – cross correlation q Propagation Criterion (including SAC) – can be guaranteed by high nonlinearity – diffusion property pinnon@lycos. co. kr 6

Cryptanalysis Methods q Differential Cryptanalysis q Linear Cryptanalysis q Interpolation Attack q Square Attack pinnon@lycos. co. kr 7

Differential Cryptanalysis q General – The First Attack against full round DES – Using the biased distribution of XOR pairs Uniform f f (S-Box) Uniform pinnon@lycos. co. kr = Input XOR(Uniform) = Output XOR(Biased) 8
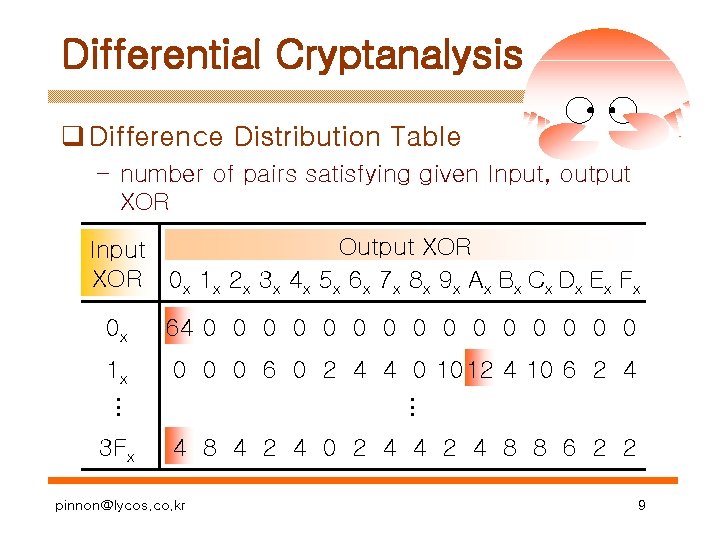
Differential Cryptanalysis q Difference Distribution Table – number of pairs satisfying given Input, output XOR Input XOR Output XOR 0 x 1 x 2 x 3 x 4 x 5 x 6 x 7 x 8 x 9 x Ax Bx Cx Dx Ex Fx 0 x 64 0 0 0 0 1 x 0 0 0 6 0 2 4 4 0 10 12 4 10 6 2 4 … … 3 Fx 4 8 4 2 4 0 2 4 4 2 4 8 8 6 2 2 pinnon@lycos. co. kr 9
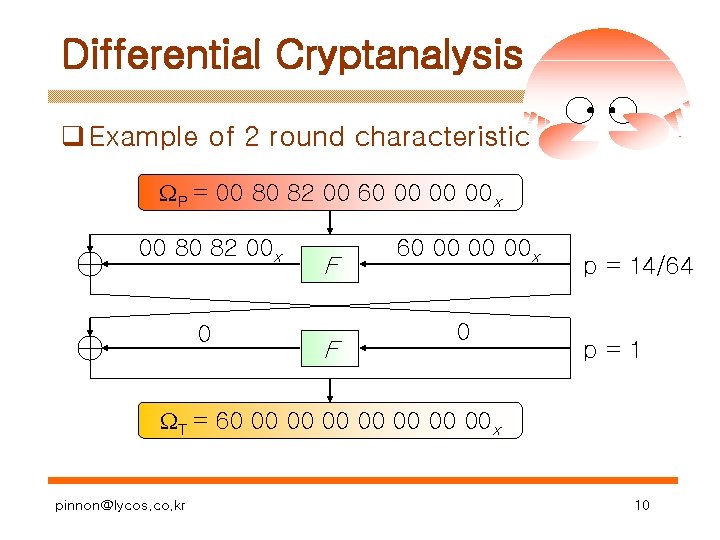
Differential Cryptanalysis q Example of 2 round characteristic P = 00 80 82 00 60 00 00 00 x 00 80 82 00 x 0 F F 60 00 00 00 x 0 p = 14/64 p=1 T = 60 00 00 x pinnon@lycos. co. kr 10
Differential Cryptanalysis q Research Issue – Cryptanalysis • How to find a characteristic with high probability – Cryptography • How to construct secure S-Boxes • Markov Cipher • Boolean Function – Nonlinearity – Propagation criteria – Bent function – Vector-valued Boolean function pinnon@lycos. co. kr 11
Provable Security q Main Idea – Approach in the view of differential – Provable Security against DC and LC • KN-Cipher – Lars R. Knudsen, Kaisa Nyberg – Round Function : g(x) = x 3 in GF(233) • MISTY – Mitsuru Matsui – Recursive Structure – Modified Feistel Network pinnon@lycos. co. kr 12
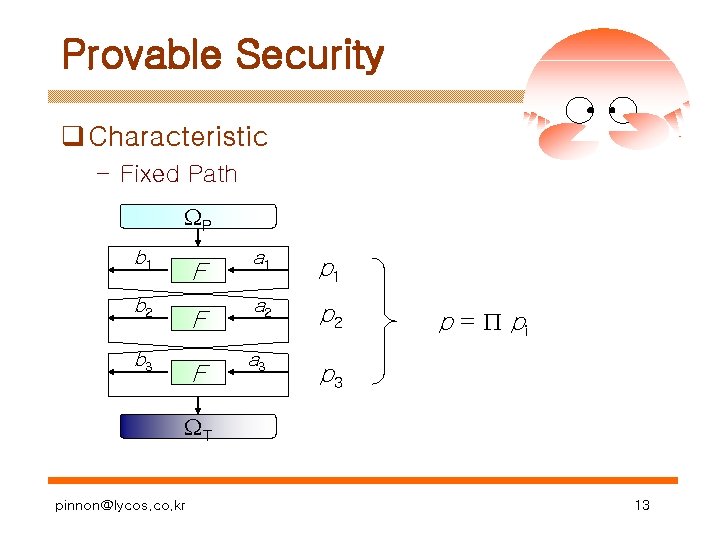
Provable Security q Characteristic – Fixed Path P b 1 F b 2 F b 3 F a 1 p 1 a 2 p 2 a 3 p = pi p 3 T pinnon@lycos. co. kr 13
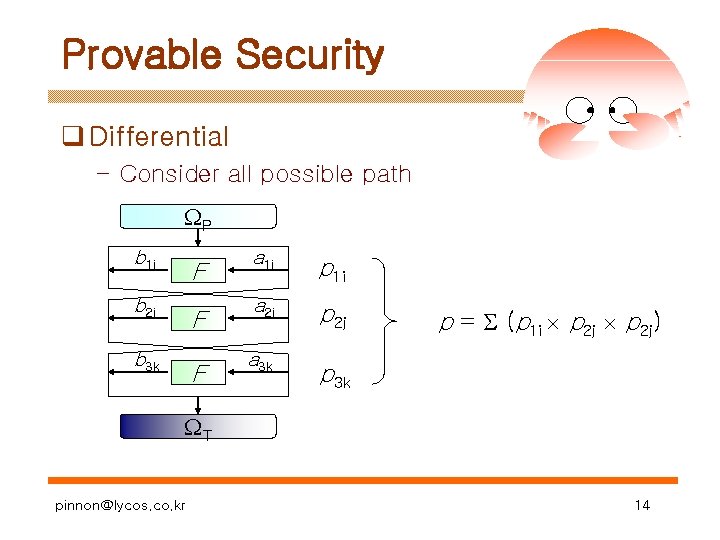
Provable Security q Differential – Consider all possible path P b 1 i F b 2 j F b 3 k F a 1 i p 1 i a 2 j p 2 j a 3 k p = (p 1 i p 2 j) p 3 k T pinnon@lycos. co. kr 14
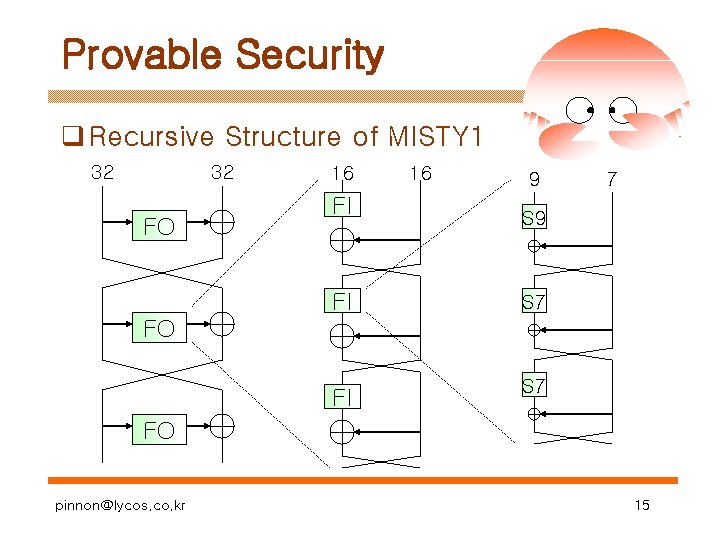
Provable Security q Recursive Structure of MISTY 1 32 32 FO 16 16 9 FI S 7 7 FO FI S 7 FO pinnon@lycos. co. kr 15
Practical Security q The Wide Trail Strategy – Design the round transformation in such a way that only trails with many S-boxes occur – Maximize the number of Active S-boxes – Branch Number B(f) = minx 0(wh(x) + wh(f(x))) – SQUARE • following the Wide Trail Strategy • MDS (Maximal Distance Separable) code – Maximum Branch number • Self-reciprocal structure pinnon@lycos. co. kr 16
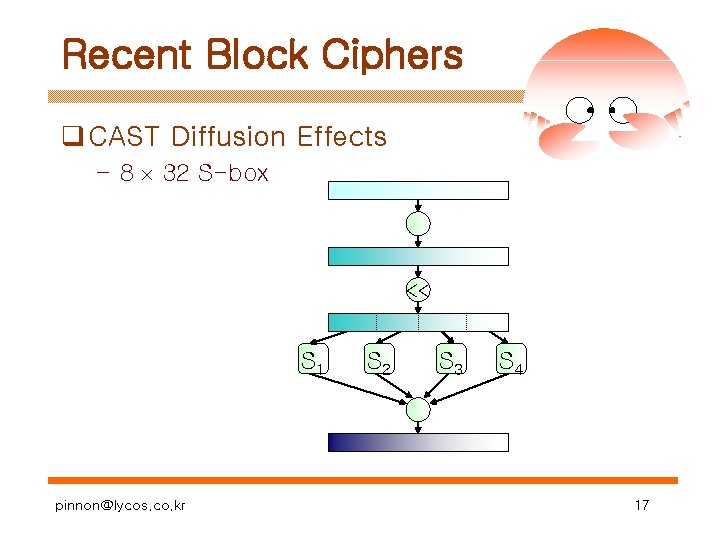
Recent Block Ciphers q CAST Diffusion Effects – 8 32 S-box << S 1 pinnon@lycos. co. kr S 2 S 3 S 4 17
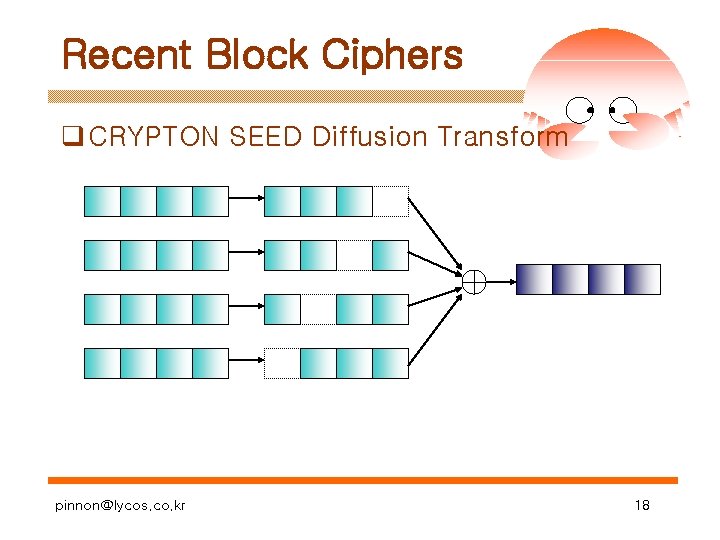
Recent Block Ciphers q CRYPTON SEED Diffusion Transform pinnon@lycos. co. kr 18
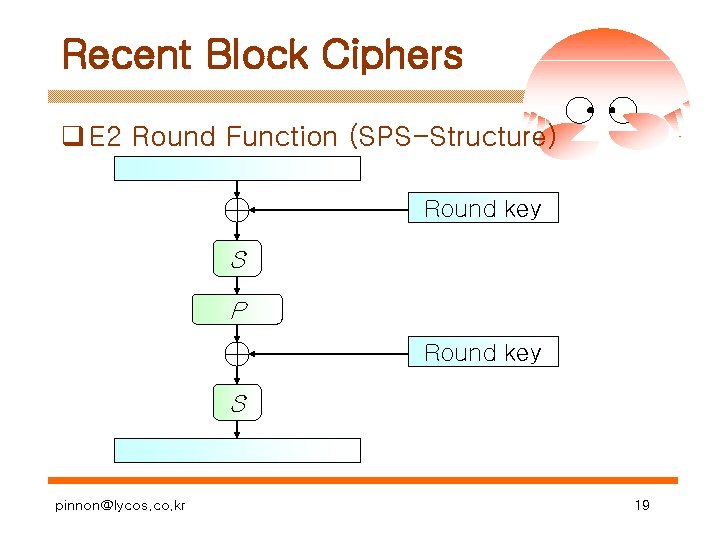
Recent Block Ciphers q E 2 Round Function (SPS-Structure) Round key S P Round key S pinnon@lycos. co. kr 19
S-box Construction q Simulation – DES q Combination of Boolean Function – CAST q Vector-valued Boolean Function – KN-Cipher, SEED, AES q Small Feistel Network – MISTY, Crypton pinnon@lycos. co. kr 20
Diffusion Layer q Perfect S-box cannot guarantee the security of round function – 8 32 S-box – Wide Trail Strategy (using a MDS code) – SPS Structure pinnon@lycos. co. kr 21
Project Progress q Boolean function analysis library – Three Representation • sequence • algebraic normal form • Walsh-Hadamard – Hamming Weight – Nonlinearity – Autocorrelation q Review recent block cipher algorithm and cryptanalysis methods pinnon@lycos. co. kr 22
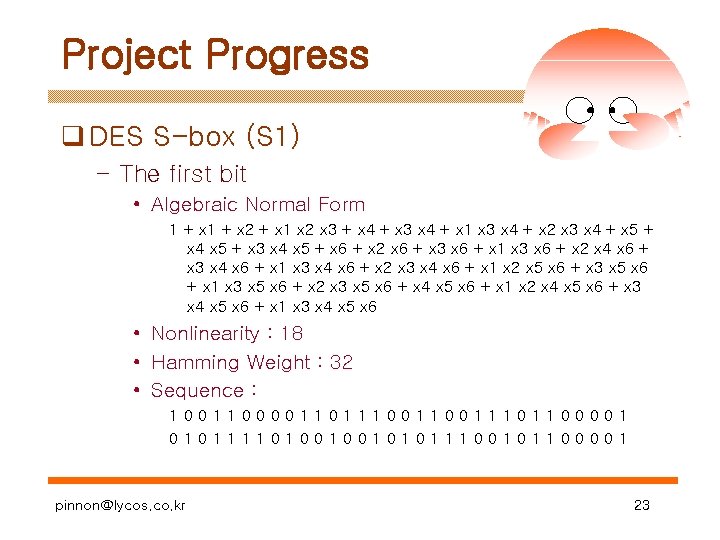
Project Progress q DES S-box (S 1) – The first bit • Algebraic Normal Form 1 + x 2 + x 1 x 2 x 3 + x 4 + x 3 x 4 + x 1 x 3 x 4 + x 2 x 3 x 4 + x 5 + x 4 x 5 + x 3 x 4 x 5 + x 6 + x 2 x 6 + x 3 x 6 + x 1 x 3 x 6 + x 2 x 4 x 6 + x 3 x 4 x 6 + x 1 x 3 x 4 x 6 + x 2 x 3 x 4 x 6 + x 1 x 2 x 5 x 6 + x 3 x 5 x 6 + x 1 x 3 x 5 x 6 + x 2 x 3 x 5 x 6 + x 4 x 5 x 6 + x 1 x 2 x 4 x 5 x 6 + x 3 x 4 x 5 x 6 + x 1 x 3 x 4 x 5 x 6 • Nonlinearity : 18 • Hamming Weight : 32 • Sequence : 1001100001101110011101100001 01011110100100101011100101100001 pinnon@lycos. co. kr 23
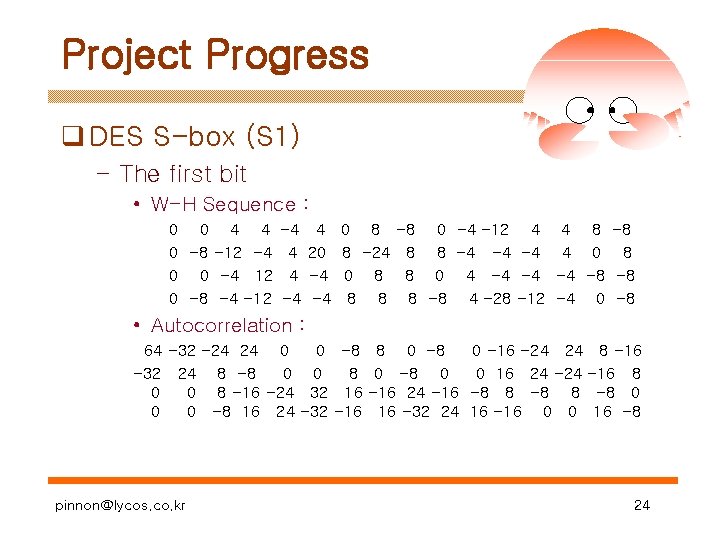
Project Progress q DES S-box (S 1) – The first bit • W-H Sequence : 0 0 4 4 0 -8 -12 -4 0 0 -4 12 0 -8 -4 -12 -4 4 4 -4 4 20 -4 -4 0 8 -8 0 -4 -12 4 4 8 -8 8 -24 8 8 -4 -4 -4 4 0 8 8 0 4 -4 -8 -8 4 -28 -12 -4 0 -8 • Autocorrelation : 64 -32 -24 24 0 0 -8 8 0 -16 -24 24 8 -16 -32 24 8 -8 0 0 8 0 -8 0 0 16 24 -16 8 0 0 8 -16 -24 32 16 -16 24 -16 -8 8 -8 0 0 0 -8 16 24 -32 -16 16 -32 24 16 -16 0 0 16 -8 pinnon@lycos. co. kr 24
Future Works q Security analysis of block ciphers consisting of Boolean function of low algebraic order q Implement S-box Analysis Tools using current library pinnon@lycos. co. kr 25
Qn. A pinnon@lycos. co. kr 26
- Slides: 27