Security administrators The experts need better tools too
Security administrators The experts need better tools too!

Agenda n Projects? – Final conflicts? – Report and presentations Security admins n General wrap-up n

Report and presentation n n Intro and motivation Describe the study - tasks, surveys, how many users, etc. Describe the results – tables of data, issues observed, etc. Describe the implications – what do the results mean? What would someone do with these results? Future work – how would you modify study based on your pilot? What future studies does this suggest?

Security Administrator Knowledge n n Growing more and more difficult Decade ago: – possible for intimate knowledge of smaller computer systems, fewer applications and infrastructures to support – An intruder also likely needed intimate knowledge, less malicious code out there n Now: – large operating systems, 10 s of thousands of files, large infrastructures – Widely distributed attack tools, very interconnected networks, infection occurs everywhere all the time Slides adapted from Matthew De. Santis, CMU
(Some) tools of the trade n Intrusion Detection Systems (IDS) – Monitor network traffic and alert to suspicious patterns n Scanning tools – Look for known vulnerabilities in networks and machines n File/host integrity tools – Virus detection – Filesystem monitoring n Home made scripts – Filter and process log files, run services, etc. n Information sources – Descriptions of attacks, source code, etc.

Admin challenges n n n Problems complex, still require human judgement to determine and solve Information overload – – – Large numbers of alerts and emails Large log files Many tools to help with different tasks Usability still not an aspect of these tools – Command lines rule – No standards for tool output, difficult to synthesize
Solutions? n Identify work practices and needs of these users – What is the implications of having security experts as users? – What usability properties do tools need to have? n Visualization – Help users identify patterns in high volume data – Synthesize data from multiple sources to provide higher level views – Challenge: another thing to attack
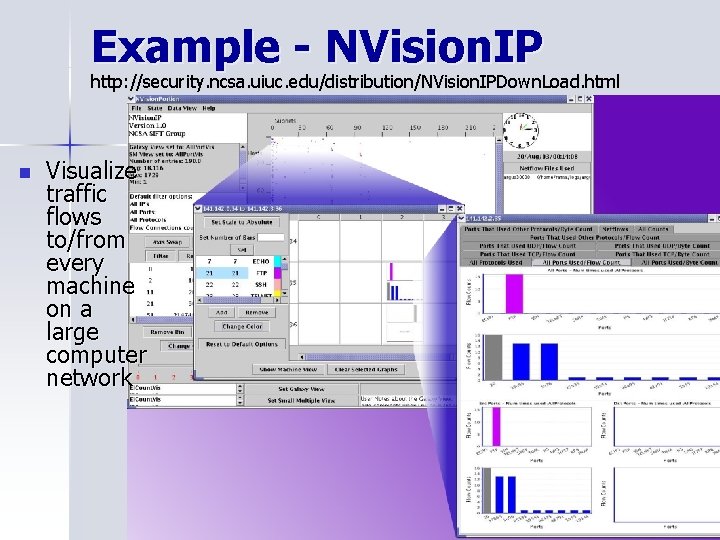
Example - NVision. IP http: //security. ncsa. uiuc. edu/distribution/NVision. IPDown. Load. html n Visualize traffic flows to/from every machine on a large computer network
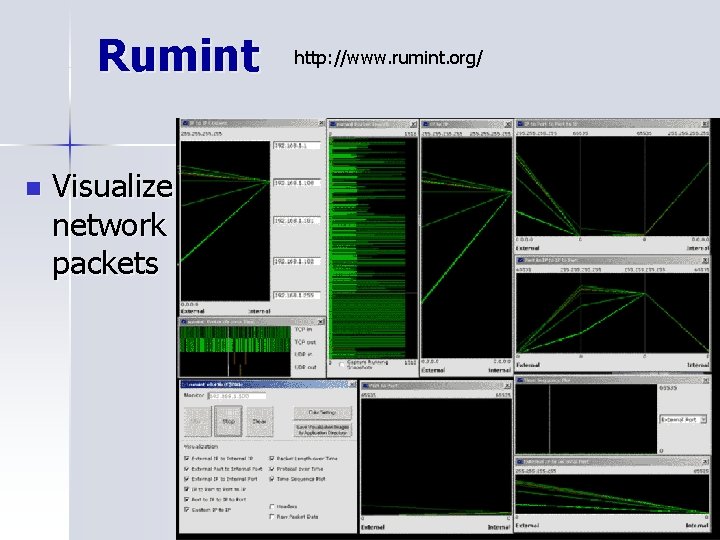
Rumint n Visualize network packets http: //www. rumint. org/
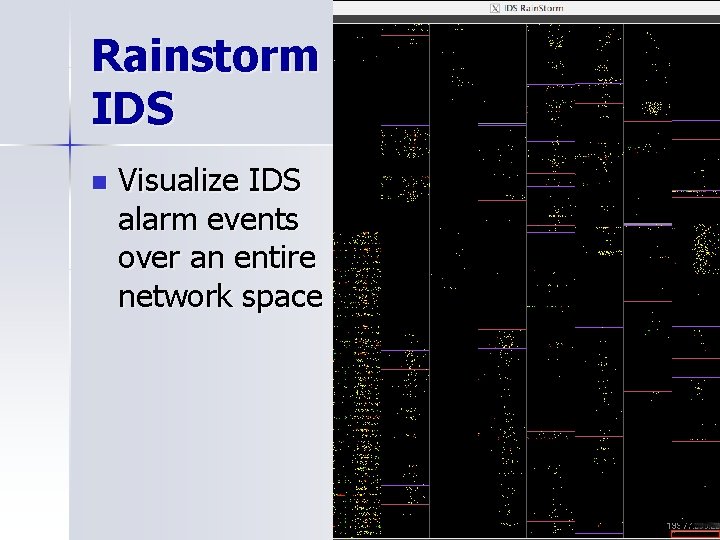
Rainstorm IDS n Visualize IDS alarm events over an entire network space
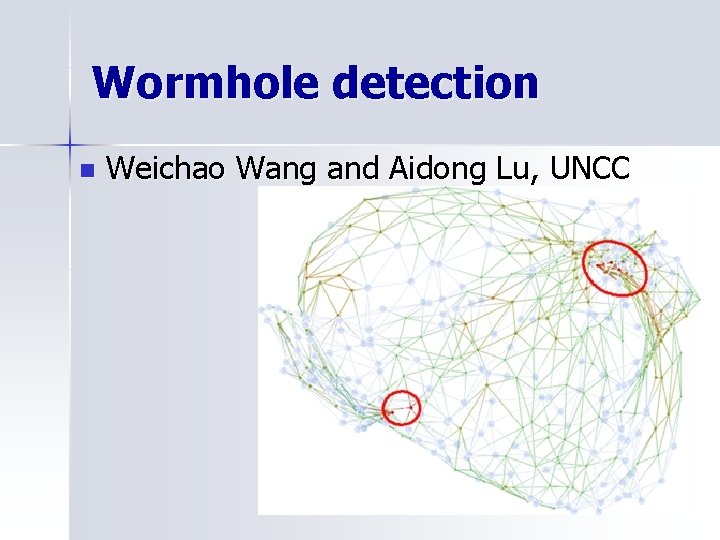
Wormhole detection n Weichao Wang and Aidong Lu, UNCC

What else? Advantages, disadvantages of visualizations? n Why don’t sysadmins use more of these visualization tools? n What else could potentially make security administrator’s jobs easier? n What do end user’s need to know about security administrators? n

Course wrap-up n Big lessons: – HCI can play a role in security and privacy solutions – Security and privacy are secondary tasks – Usability is not necessarily contrary to security – As with anything, tradeoffs in approaches – Good user-centered design can improve today’s tools

So what have you learned? n n n What are the biggest lessons you take away from this course? How will you incorporate what you have learned into your job or life? What are important new themes to study in this area? – What needs additional focus? – anything we didn’t cover you think is really important?
Next week Give me 24 hours to give you feedback on a project draft n Presentations: 6: 30 pm in CHHS 285 n
- Slides: 15