SECURING WEB APPLICATIONS EXTERNALLY WITH AZURE ACTIVE DIRECTORY

SECURING WEB APPLICATIONS EXTERNALLY WITH AZURE ACTIVE DIRECTORY APPLICATION PROXY.
QUICK SURVEY • At your Board, are employee Web sites / applications currently internet facing (ex: SIS, Report cards, etc)? • Does your Board currently use Azure Active Directory? • Is your Board using office 365? • Are you already using an Employee portal or gateway product to secure internal Board resources externally? ARE YOU AT RISK? Are you aware that your data could be at risk, and what are you doing about it? page 2
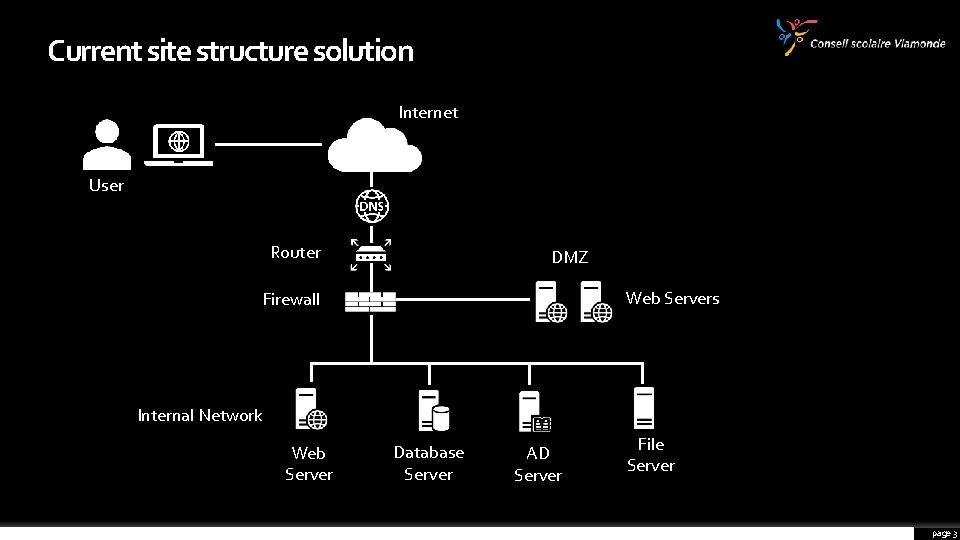
Current site structure solution Internet User Router DMZ Web Servers Firewall Internal Network Web Server Database Server AD Server File Server page 3
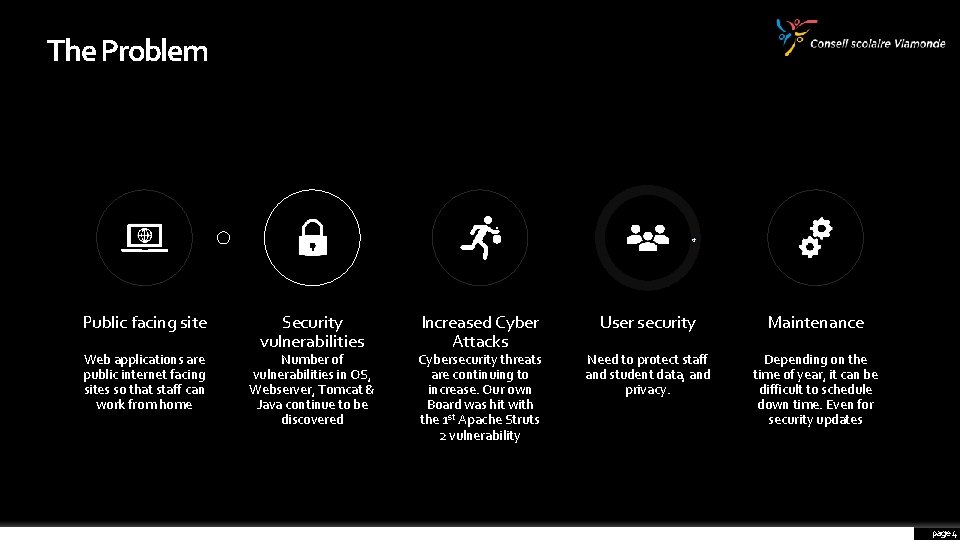
The Problem Public facing site Web applications are public internet facing sites so that staff can work from home Security vulnerabilities Number of vulnerabilities in OS, Webserver, Tomcat & Java continue to be discovered Increased Cyber Attacks Cybersecurity threats are continuing to increase. Our own Board was hit with the 1 st Apache Struts 2 vulnerability User security Maintenance Need to protect staff and student data, and privacy. Depending on the time of year, it can be difficult to schedule down time. Even for security updates page 4
Increased Security SOLUTION USE AZURE ACTIVE DIRECTORY APPLICATION PROXY TO SECURE BOARD EMPLOYEE SITES FOR EXTERNAL USE Increase security of externally available resources, with experience that users are already accustomed to Integration Cost Already integrates with existing technologies such as Active Directory and office 365 Reduce cost by using additional features of software that we already own. page 5

WHAT IS AZURE AD APPLICATION PROXY? REMOTE ACCESS SOLUTION FOR ON-PREMISES RESOURCES Easily publish your on -premises application to users outside your corporate network Can leverage benefits of Azure AD such as Multi factor authentication Doesn’t open access to your entire network like VPN. You control was is accessible Works across multiple devices page 6
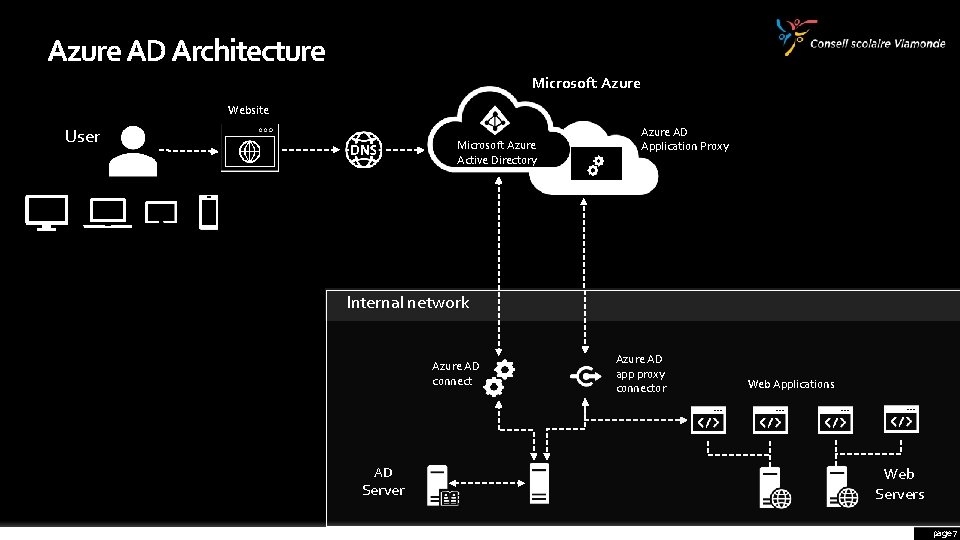
Azure AD Architecture Microsoft Azure Website User Microsoft Azure Active Directory Azure AD Application Proxy Internal network Azure AD connect AD Server Azure AD app proxy connector Web Applications Web Servers page 7

INITIAL CHALLENGES HERE ARE THE MAIN CHALLENGES THAT WE NEED TO OVERCOME TO MAKE THIS SOLUTION VIABLE. URL name Site structure Use same URL internally and externally Some Trillium are structured in a way that make it difficult to access top level resources (ex: css) Linking to Jasper User experience Issues launching Jasper Reports from Landing Page Make end user experience seamless, despite new URL’s page 8
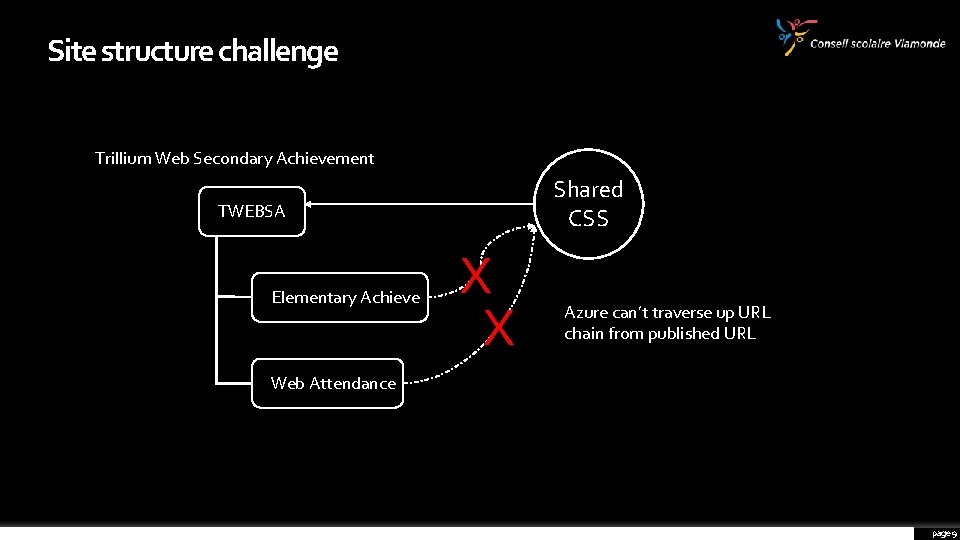
Site structure challenge Trillium Web Secondary Achievement Shared CSS TWEBSA Elementary Achieve X X Azure can’t traverse up URL chain from published URL Web Attendance page 9
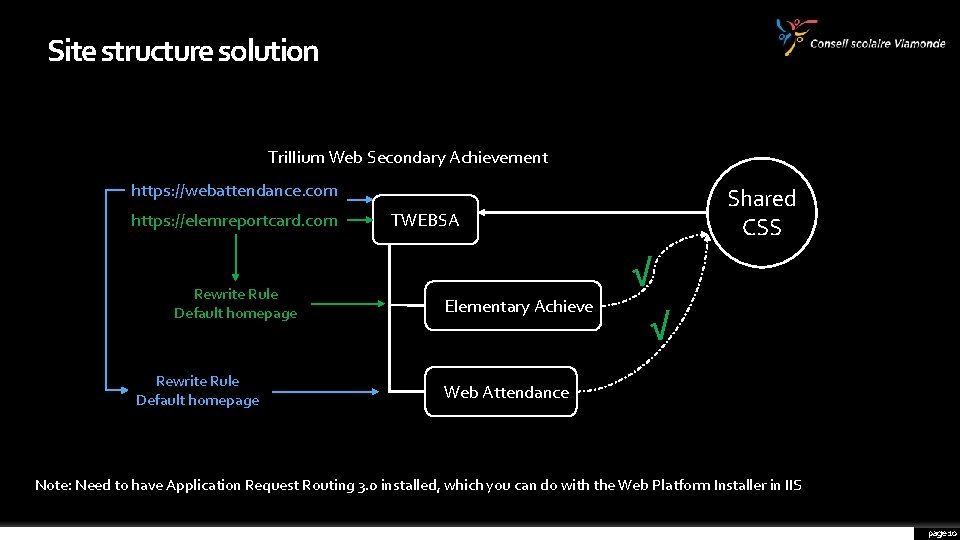
Site structure solution Trillium Web Secondary Achievement https: //webattendance. com https: //elemreportcard. com Rewrite Rule Default homepage Shared CSS TWEBSA √ Elementary Achieve √ Web Attendance Note: Need to have Application Request Routing 3. 0 installed, which you can do with the Web Platform Installer in IIS page 10
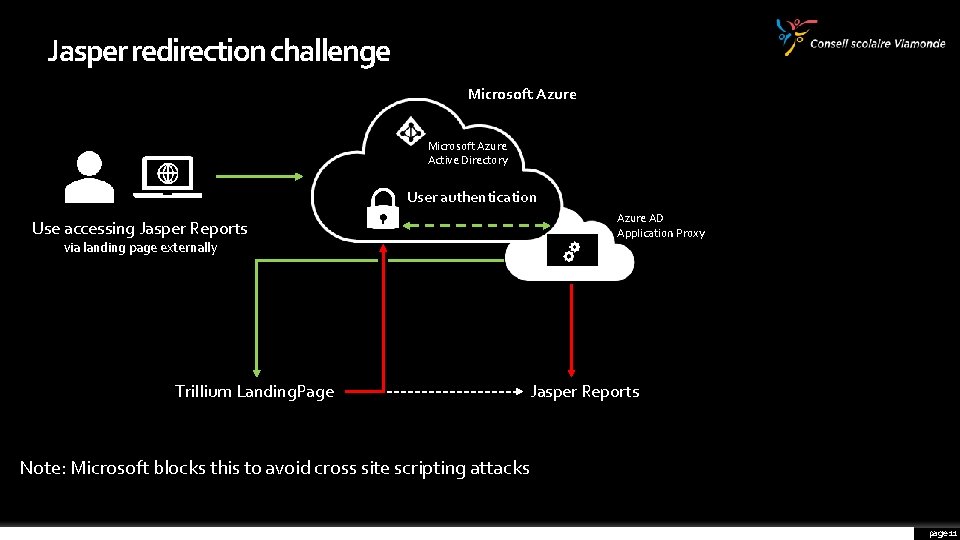
Jasper redirection challenge Microsoft Azure Active Directory User authentication Use accessing Jasper Reports via landing page externally Trillium Landing. Page Azure AD Application Proxy Jasper Reports Note: Microsoft blocks this to avoid cross site scripting attacks page 11
DEMO GO THROUGH BASIC STEPS AND SHOW SETUP IN OUR TEST ENVIRONMENT • Custom IIS sites • URL rewrite rules • Azure AD configurations • DNS configurations • More rewrite rules • Core Trillium Configurations page 12
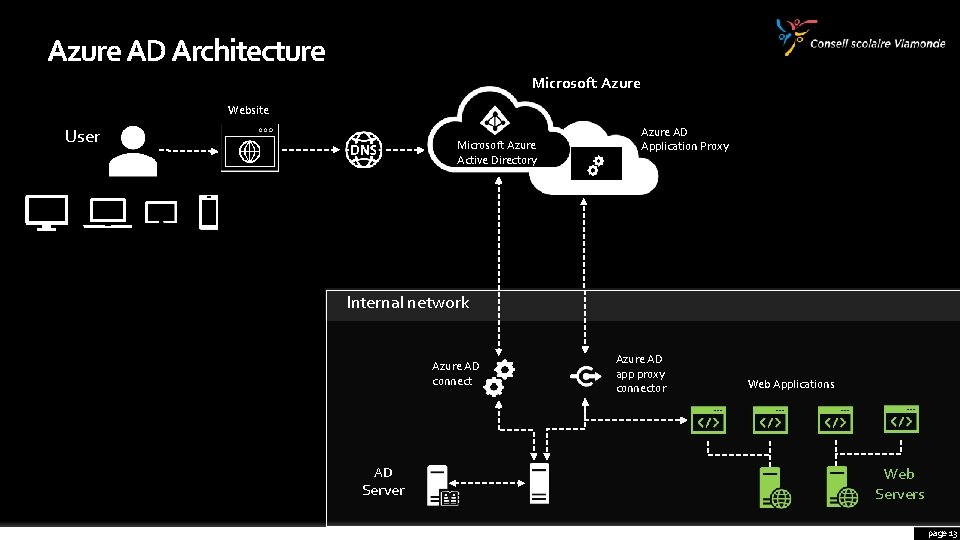
Azure AD Architecture Microsoft Azure Website User Microsoft Azure Active Directory Azure AD Application Proxy Internal network Azure AD connect AD Server Azure AD app proxy connector Web Applications Web Servers page 13
IIS Configurations (part 1) Custom Sites • Web Attendance • Elementatry achievement • Secondary achievement Steps • Create new IIS sites to over come site structure challenges • Add SSL Certs & HTTPS binding • Add URL Rewrite Rules • • HTTP to HTTPS Default homepage redirection to appropriate sub URL Redirection to Tomcat web app For webapps with link to jasper also setup jasper rewrite rules. page 14
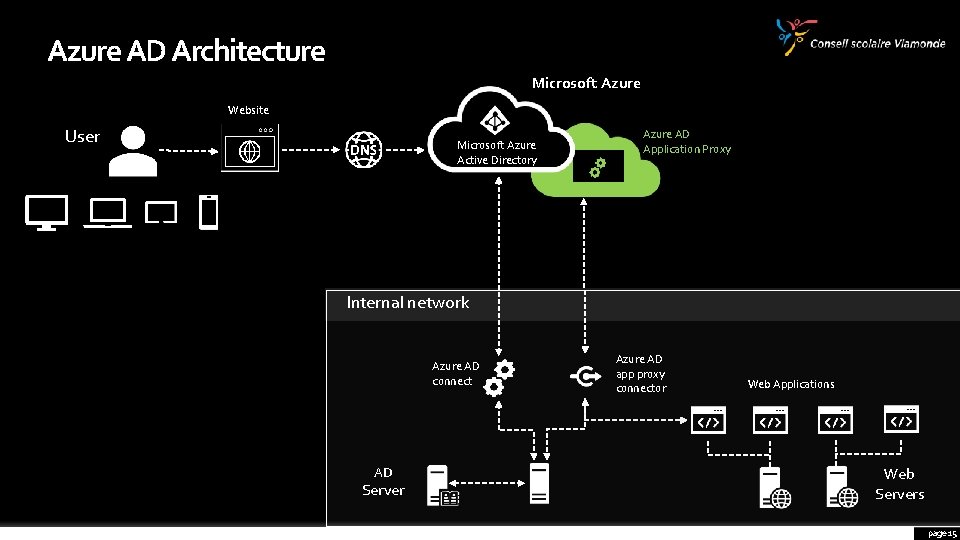
Azure AD Architecture Microsoft Azure Website User Microsoft Azure Active Directory Azure AD Application Proxy Internal network Azure AD connect AD Server Azure AD app proxy connector Web Applications Web Servers page 15
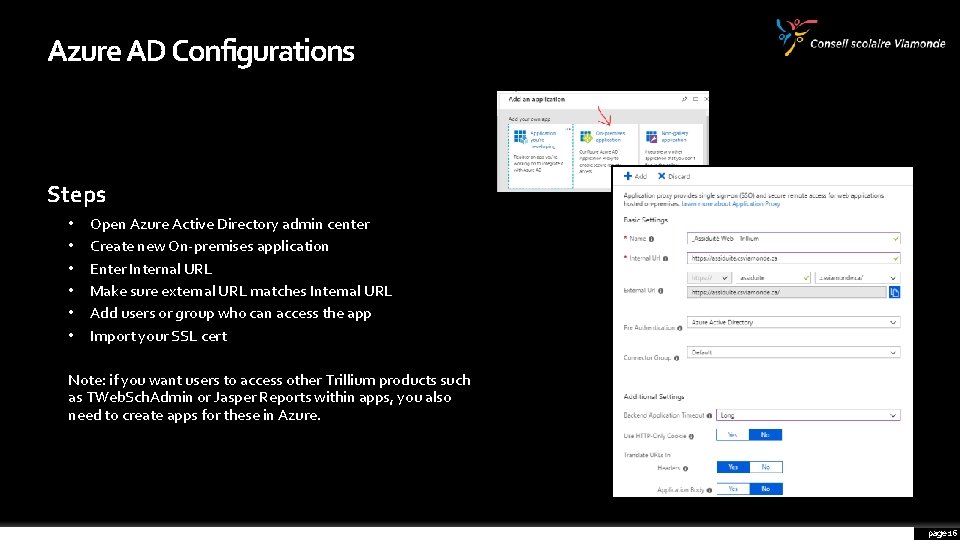
Azure AD Configurations Steps • • • Open Azure Active Directory admin center Create new On-premises application Enter Internal URL Make sure external URL matches Internal URL Add users or group who can access the app Import your SSL cert Note: if you want users to access other Trillium products such as TWeb. Sch. Admin or Jasper Reports within apps, you also need to create apps for these in Azure. page 16
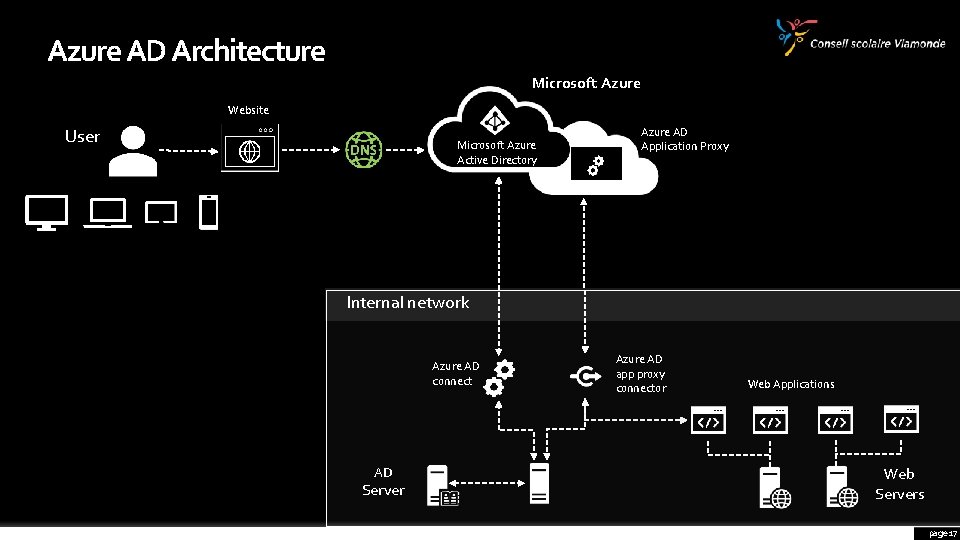
Azure AD Architecture Microsoft Azure Website User Microsoft Azure Active Directory Azure AD Application Proxy Internal network Azure AD connect AD Server Azure AD app proxy connector Web Applications Web Servers page 17

DNS Configurations Internal DNS • Add new A Host record for new url’s created External DNS • Add New Alias (CName) record for new url’s created • Alias name should point to the base of the url configured in IIS (ex: attendance) • Fully qualified domaine name (FQDN) should point to url configured in IIS (ex: attendance. mydomain. ca) • Fully qualified domaine name (FQDN) for target host should point to the Azure URL for the application. This value can be found in the application proxy page for the app. (ex: https: //attendance-mydomain. msappproxy. net) page 18
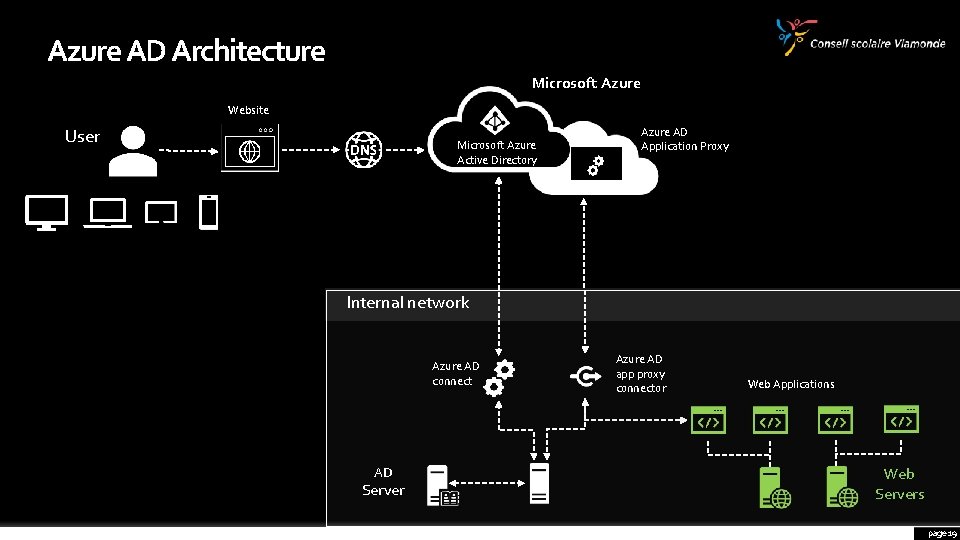
Azure AD Architecture Microsoft Azure Website User Microsoft Azure Active Directory Azure AD Application Proxy Internal network Azure AD connect AD Server Azure AD app proxy connector Web Applications Web Servers page 19
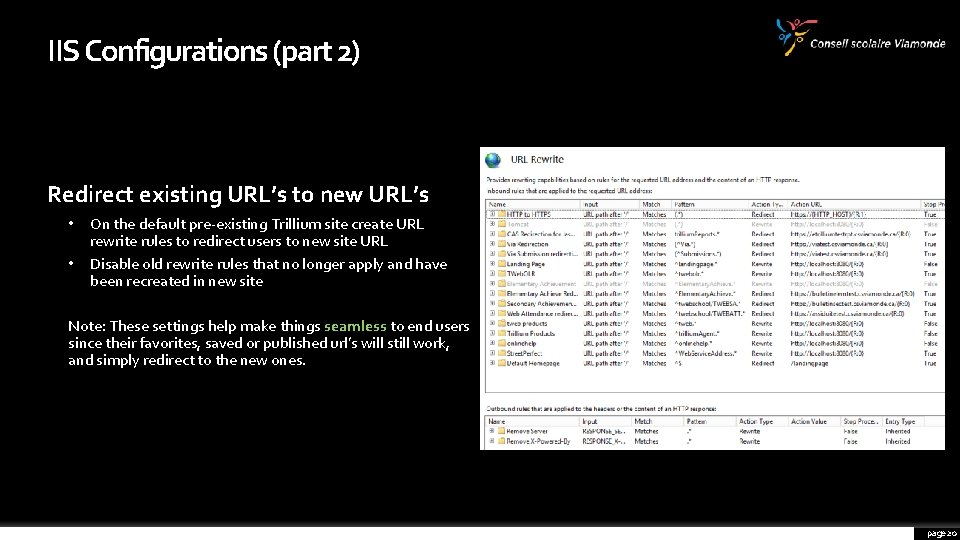
IIS Configurations (part 2) Redirect existing URL’s to new URL’s • On the default pre-existing Trillium site create URL rewrite rules to redirect users to new site URL • Disable old rewrite rules that no longer apply and have been recreated in new site Note: These settings help make things seamless to end users since their favorites, saved or published url’s will still work, and simply redirect to the new ones. page 20
Core Trillium Configurations Redirect existing URL’s to new URL’s • Under Trillium Security > Web Services update URL’S for elementary and secondary report card printing to new URL’s • If you made changes to URL’s found under Admin Gateway, make sure to change those as well page 21

Next steps? Move Trillium web server to internal network • Since Azure AD allows us to publish internal sites outside of our network without opening holes in our firewall, we would like to move our Trillium web server out of our DMZ, and into our internal network. • This will as another layer of protection for our Trillium Web applications page 22

• Increased security • Relative ease of setup • Familiar user experience SUMMARY • Documentation & presentation available at https: //bit. ly/2 Ks. GOf 0 page 23
Questions ? THANK YOU John-Rock Bilodeau bilodeauj@csviamonde. ca Richard Therrien therrienr@csviamonde. ca
- Slides: 24