Securing Remote Access using SSLVPN Niklas Henriksson Systems













- Slides: 23

Securing Remote Access using SSL-VPN Niklas Henriksson – Systems Engineer nhenriksson@juniper. net Copyright © 2008 2007 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1

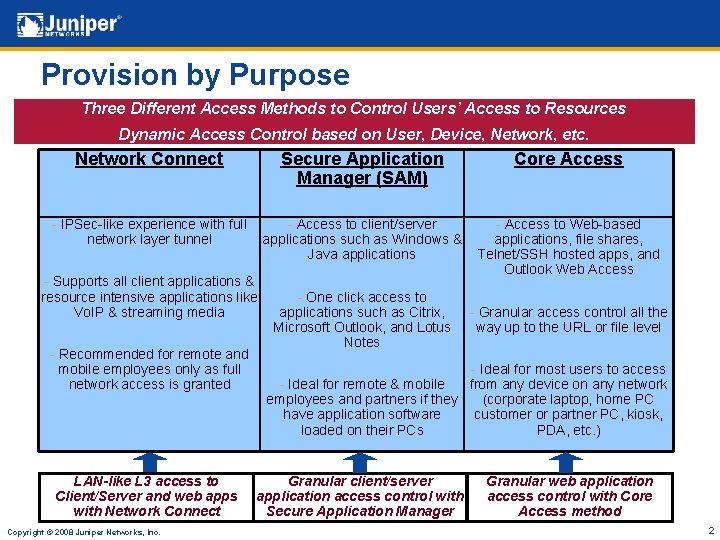
Provision by Purpose Three Different Access Methods to Control Users’ Access to Resources Dynamic Access Control based on User, Device, Network, etc. Network Connect Secure Application Manager (SAM) Core Access - IPSec-like experience with full network layer tunnel - Access to client/server applications such as Windows & Java applications - Access to Web-based applications, file shares, Telnet/SSH hosted apps, and Outlook Web Access - Supports all client applications & resource intensive applications like Vo. IP & streaming media - Recommended for remote and mobile employees only as full network access is granted LAN-like L 3 access to Client/Server and web apps with Network Connect Copyright © 2008 Juniper Networks, Inc. - One click access to applications such as Citrix, Microsoft Outlook, and Lotus Notes - Granular access control all the way up to the URL or file level - Ideal for most users to access - Ideal for remote & mobile from any device on any network employees and partners if they (corporate laptop, home PC have application software customer or partner PC, kiosk, loaded on their PCs PDA, etc. ) Granular client/server application access control with Secure Application Manager Granular web application access control with Core Access method 2

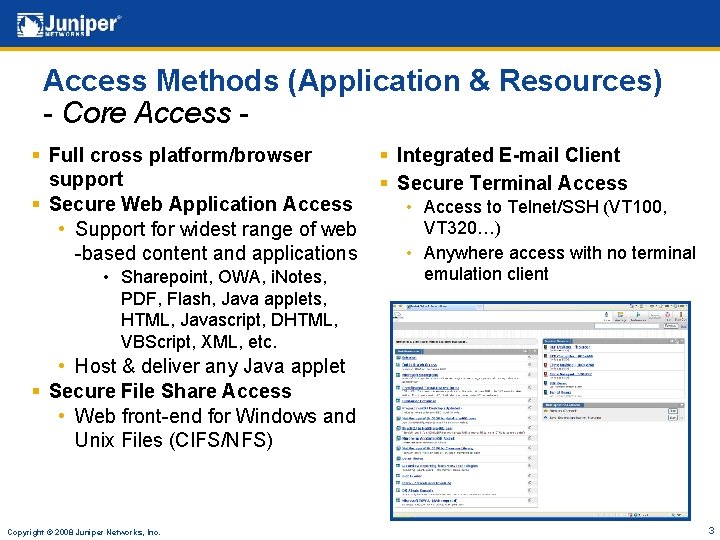
Access Methods (Application & Resources) - Core Access § Full cross platform/browser support § Secure Web Application Access • Support for widest range of web -based content and applications • Sharepoint, OWA, i. Notes, PDF, Flash, Java applets, HTML, Javascript, DHTML, VBScript, XML, etc. § Integrated E-mail Client § Secure Terminal Access • Access to Telnet/SSH (VT 100, VT 320…) • Anywhere access with no terminal emulation client • Host & deliver any Java applet § Secure File Share Access • Web front-end for Windows and Unix Files (CIFS/NFS) Copyright © 2008 Juniper Networks, Inc. 3

Access Methods (Application & Resources) - Terminal Services § Seamlessly and securely access any Citrix or Windows Terminal Services deployment • Intermediate traffic via native TS support, WSAM, JSAM, Network Connect, Hosted Java Applet • Replacement for Web Interface/Nfuse § Native TS Support • • • Granular Use Control Secure Client delivery Integrated Single Sign-on Java RDP/JICA Fallback WTS: Session Directory Citrix: Auto-client reconnect/ session reliability • Many additional reliability, usability, access control options Copyright © 2008 Juniper Networks, Inc. 4

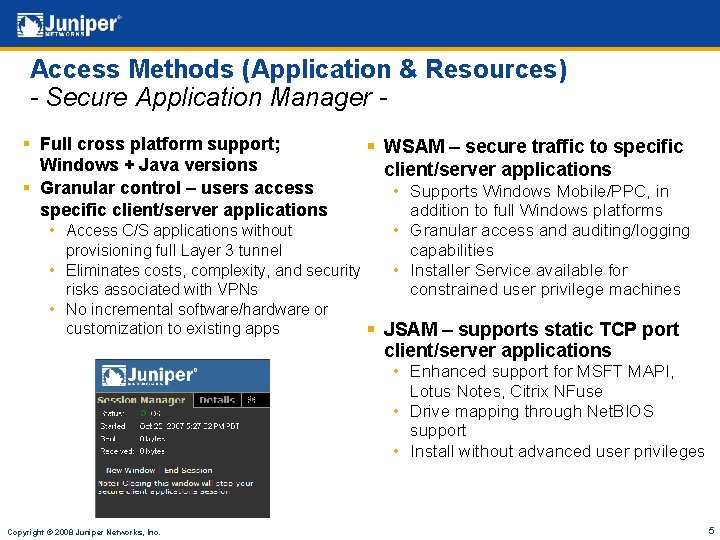
Access Methods (Application & Resources) - Secure Application Manager § Full cross platform support; Windows + Java versions § Granular control – users access specific client/server applications § WSAM – secure traffic to specific client/server applications • Supports Windows Mobile/PPC, in addition to full Windows platforms • Granular access and auditing/logging capabilities • Installer Service available for constrained user privilege machines • Access C/S applications without provisioning full Layer 3 tunnel • Eliminates costs, complexity, and security risks associated with VPNs • No incremental software/hardware or customization to existing apps § JSAM – supports static TCP port client/server applications • Enhanced support for MSFT MAPI, Lotus Notes, Citrix NFuse • Drive mapping through Net. BIOS support • Install without advanced user privileges Copyright © 2008 Juniper Networks, Inc. 5

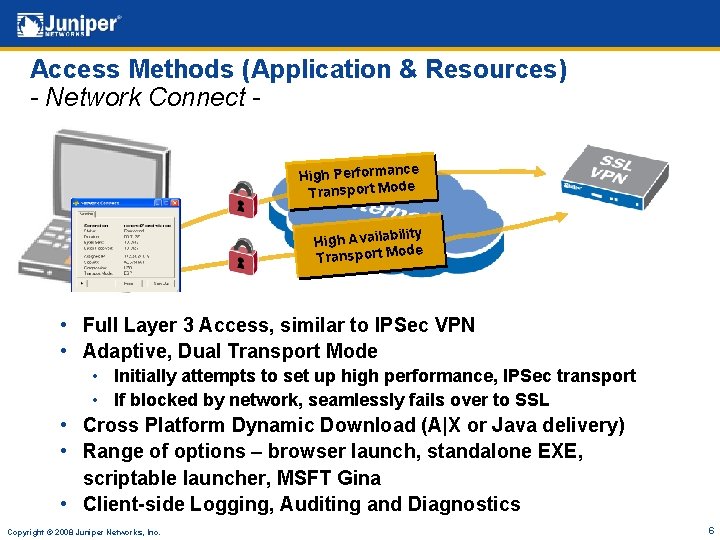
Access Methods (Application & Resources) - Network Connect - X ce High Performan Transport Mode ility High Availab ode Transport M • Full Layer 3 Access, similar to IPSec VPN • Adaptive, Dual Transport Mode • Initially attempts to set up high performance, IPSec transport • If blocked by network, seamlessly fails over to SSL • Cross Platform Dynamic Download (A|X or Java delivery) • Range of options – browser launch, standalone EXE, scriptable launcher, MSFT Gina • Client-side Logging, Auditing and Diagnostics Copyright © 2008 Juniper Networks, Inc. 6

Seamless AAA Integration § Full Integration into customer AAA infrastructure • AD, LDAP, RADIUS, Certificate, OTP, etc. § Password Management Integration • User self service for password management • Reduced support costs, increased productivity • All standard LDAP, MSFT AD § Single Sign-On – Native Capabilities • Leveraged across all web apps seamless user experience • Forms, Header, SAML, Cookie, Basic Auth, NTLM § SAML Support – Web single sign-on, integration with I&AM platforms • Standards-based Web SSO Partnerships with leading AM Vendors (CA, Oracle, RSA, etc. ) Copyright © 2008 Juniper Networks, Inc. 7

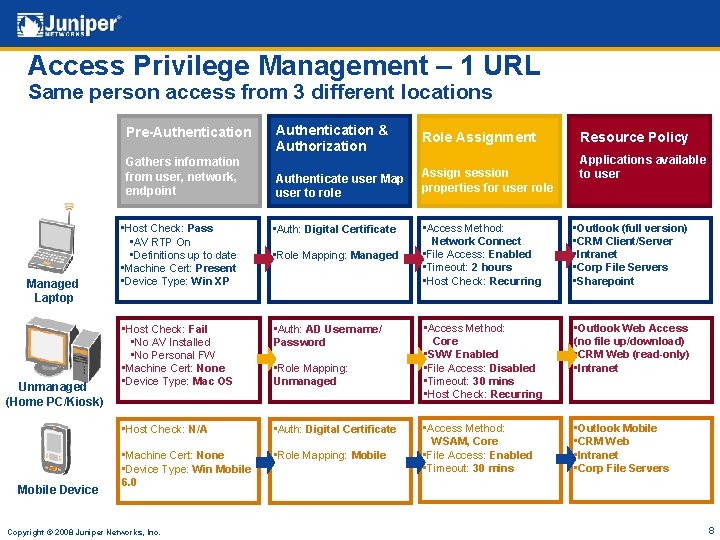
Access Privilege Management – 1 URL Same person access from 3 different locations Pre-Authentication Gathers information from user, network, endpoint Managed Laptop Unmanaged (Home PC/Kiosk) Mobile Device Authentication & Authorization Role Assignment Authenticate user Map user to role Assign session properties for user role • Host Check: Pass • AV RTP On • Definitions up to date • Machine Cert: Present • Device Type: Win XP • Auth: Digital Certificate • Host Check: Fail • No AV Installed • No Personal FW • Machine Cert: None • Device Type: Mac OS • Auth: AD Username/ Password • Host Check: N/A • Auth: Digital Certificate • Machine Cert: None • Device Type: Win Mobile 6. 0 • Role Mapping: Mobile Copyright © 2008 Juniper Networks, Inc. • Role Mapping: Managed • Role Mapping: Unmanaged Resource Policy Applications available to user • Access Method: Network Connect • File Access: Enabled • Timeout: 2 hours • Host Check: Recurring • Outlook (full version) • CRM Client/Server • Intranet • Corp File Servers • Sharepoint • Access Method: Core • SVW Enabled • File Access: Disabled • Timeout: 30 mins • Host Check: Recurring • Outlook Web Access (no file up/download) • CRM Web (read-only) • Intranet • Access Method: WSAM, Core • File Access: Enabled • Timeout: 30 mins • Outlook Mobile • CRM Web • Intranet • Corp File Servers 8

One Device for Multiple Groups Customize policies and user experience for diverse users partners. company. com “Partner” Role Authentication Username/Password employees. company. com Host Check Enabled – Any AV, PFW Access Core Clientless Applications MRP, Quote Tool “Employee” Role Authentication OTP or Certificate customers. company. com Host Check Enabled – Any AV, PFW Access Core + Network Connect Applications L 3 Access to Apps “Customer” Role Authentication Username/Password Copyright © 2008 Juniper Networks, Inc. Host Check Enabled – Any AV, PFW Access Core Clientless Applications Support Portal, Docs 9

End-to-End Security Copyright © 2008 2007 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10

End-Point Security - Host Checker - Check devices before & during session - Ensure device compliance with corporate policy - Remediate devices when needed - Cross platform support Virus Home PC User - No anti-virus installed - No personal firewall - User granted minimal access - No Anti-Virus Installed - Personal Firewall enabled - User remediated install anti-virus - Once installed, user granted access Managed PC User Copyright © 2008 Juniper Networks, Inc. Airport Kiosk Mobile User - AV Real-Time Protection running - Personal Firewall Enabled - Virus Definitions Up To Date - User granted full access 11

Endpoint Security - Secure Virtual Workspace • Host Checker (Java/Active. X) delivery • Win 2 k/XP Systems (user privileges) • Admin-specified application access Limited/Blocked I/O Access Real Desktop SVW Clipboard Operations Blocked (Virtual Real) • Do. D Cleaning/Sanitizing standard compliant • Password-protected persistent sessions • Controlled I/O Access • Configurable look/feel Session Data Encrypted on-the-fly (AES) File System Real Copyright © 2008 Juniper Networks, Inc. Virtual End of Session: Secure Delete OR Persistent Session (Encrypted) 12

System Security § “Security First” approach to development • Hardened OS based on Linux variant • Protection against many known attacks • AES encrypted hard disk on every appliance § In-Transit Data Protection • Data trapping • URL obfuscation § Numerous 3 rd party security audits § Juniper Security Incident Response Team (SIRT) to quickly investigate any potential vulnerabilities Copyright © 2008 Juniper Networks, Inc. 13

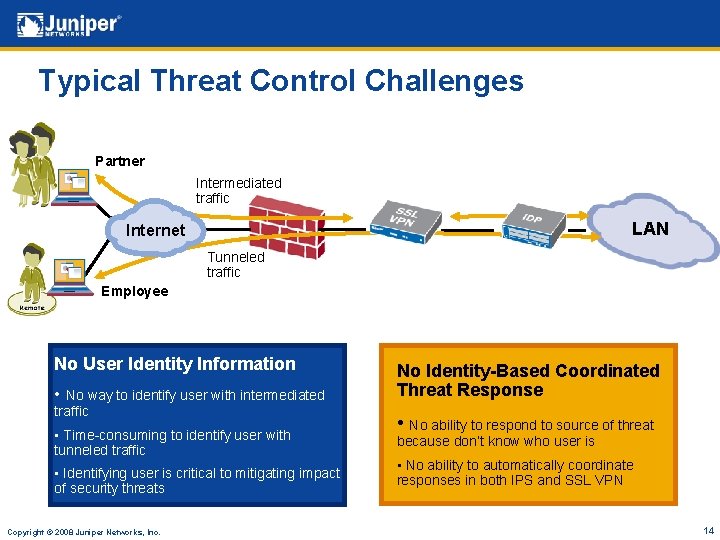
Typical Threat Control Challenges Partner Intermediated traffic LAN Internet Tunneled traffic Employee No User Identity Information • No way to identify user with intermediated traffic • Time-consuming to identify user with tunneled traffic • Identifying user is critical to mitigating impact of security threats Copyright © 2008 Juniper Networks, Inc. No Identity-Based Coordinated Threat Response • No ability to respond to source of threat because don’t know who user is • No ability to automatically coordinate responses in both IPS and SSL VPN 14

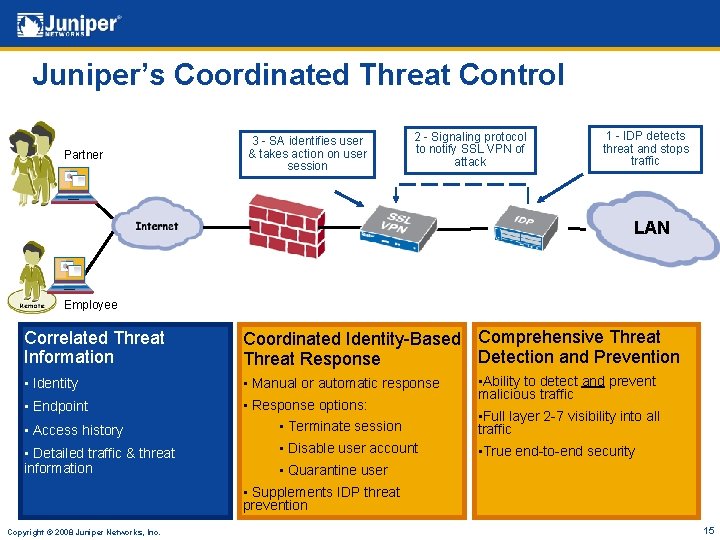
Juniper’s Coordinated Threat Control Partner 3 - SA identifies user & takes action on user session 2 - Signaling protocol to notify SSL VPN of attack 1 - IDP detects threat and stops traffic LAN Employee Correlated Threat Information Coordinated Identity-Based Comprehensive Threat Detection and Prevention Threat Response • Identity • Manual or automatic response • Endpoint • Response options: • Ability to detect and prevent malicious traffic • Access history • Terminate session • Full layer 2 -7 visibility into all traffic • Detailed traffic & threat information • Disable user account • True end-to-end security • Quarantine user • Supplements IDP threat prevention Copyright © 2008 Juniper Networks, Inc. 15

Secure Access 2500 § Targeted to small to mid-sized businesses § Up to 100 concurrent user scalability § Industry leading SSL VPN feature set such as: • Comprehensive end-point security checks on devices • Dynamic, granular access control to resources based on each user’s role • Support for wide array of mobile devices & cross platforms Copyright © 2008 Juniper Networks, Inc. 16

Secure Access 4500 § Targeted to mid to large-sized businesses § Up to 1000 concurrent user scalability § Industry leading SSL VPN feature set such as: • Comprehensive end-point security checks on devices • Dynamic, granular access control to resources based on each user’s role • Support for wide array of mobile devices & cross platforms § Optional hardware-based SSL acceleration module Copyright © 2008 Juniper Networks, Inc. 17

Secure Access 6500 § Targeted to large enterprises and service providers § Up to 10, 000 concurrent user scalability on single unit § Up to 30, 000 concurrent user cluster scalability on four-unit cluster § Includes the optional components previously found on SA 6000 SP (memory upgrade, hot swappable fans & drives) § Dual, mirrored hot swappable SATA hard drives § Dual, hot swappable fans Copyright © 2008 Juniper Networks, Inc. 18

Juniper SSL VPN Product Family Functionality and Scalability to Meet Customer Needs Breadth of Functionality Options/upgrades: • 10 -25 conc. users • Core Clientless Access Options/upgrades: • 25 -100 conc. users • Secure Meeting • Cluster Pairs Options/upgrades: • 50 -1000 conc. users • Secure Meeting • Instant Virtual System • SSL Acceleration • Cluster Pairs Secure Access 4500 Options/upgrades: • Up to 30, 000 conc. users • Secure Meeting • Instant Virtual System • 4 -port SFP card • 2 nd power supply or DC power supply • Multi-Unit Clusters Secure Access 6500 Secure Access 2500 Secure Access 700 Designed for: SMEs Secure remote access Includes: Network Connect Designed for: Medium enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access SAMNC Advanced with Central Manager Designed for: Medium to large enterprise Secure remote, intranet and extranet access Includes: Core Clientless Access SAMNC Advanced with Central Manager Designed for: Large enterprises & SPs Secure remote, intranet and extranet access Includes: Core Clientless Access SAMNC Advanced with Central Manager SSL acceleration Hot swap drives, fans Enterprise Size Copyright © 2008 Juniper Networks, Inc. 19

System Management § Granular Role-based administration • Leverages leading AAA framework used for user sessions • Assign tasks to appropriate groups (helpdesk, security, operations, etc. ) § Central Manager • Manage/maintain all clustered devices from a single console § Config Import/Export • Make offline config changes and import • Configuration backup/archiving § Push Configuration • Push full or partial configurations to other devices § Granular logging and log filtering • Analysis, compliance, and auditing requirements § Advanced troubleshooting tools for quick issue resolution • Policy trace, session recording, system snapshot, etc. Copyright © 2008 Juniper Networks, Inc. 20

Clustering/High Availability § Native Clustering • SA 2500, SA 4500 Cluster Pairs • SA 6500 Multi-unit clusters § Stateful system peering • System state and configuration settings • User profile and personalized configuration • User session synch (users don’t have to login again in failover scenario) § Active/Passive configuration for seamless failover § Active/Active configuration for increased throughput and failover § Enterprise and Service Provider Value • • Ensured reliability of critical access infrastructure Seamless failover, no loss of productivity Expansive user scalability via replication Management efficiency via central administration interface Copyright © 2008 Juniper Networks, Inc. 21

Questions? Copyright © 2008 Juniper Networks, Inc. 22

Copyright © 2008 2007 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 23