Securing or Not Accelerator Control Systems The permanent
















- Slides: 62

Securing (or Not) Accelerator Control Systems The permanent challenge to CERN security Dr. Stefan Lüders (CERN Computer Security Officer) European Spallation Source (ESS) Seminar November 23 rd, 2012, Lund (Sweden)

Security in a Nutshell “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Security is as good as the weakest link: ►Attacker chooses the time, place, method ►Defender needs to protect against all possible attacks (currently known, and those yet to be discovered) Security is a system property (not a feature) Security is a permanent process (not a product) Security cannot be proven (phase-space-problem) Security is difficult to achieve, and only to 100%-ε. ►At home (like at CERN), it is you who defines ε !!! BTW: Security is not a synonym for safety.

Overview “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint Operational Noise Control System Cyber-Security Securing (or Not) Accelerator Control Systems This is a “people” problem

“Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint

Academic Freedom at CERN’s Mission: “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 ►Research: Seeking and finding answers to questions about the Universe ►Technology: Advancing the frontiers of technology ►Collaborating: Bringing nations together through science ►Education: Training the scientists of tomorrow CERN’s Users: ►…from 100 s of universities worldwide ►Pupils, students, post-docs, professors, technicians, engineers, physicists, … ►High turn-over (~10 k user per year) Academic Freedom in Research: ►Open campus attitude (consider CERN as an ISP): No boundaries if possible: free communication & freedom to publish ►Merge of professional & private life: we have hostels on site ►BYOD (the mobile revolution), the trial of the new, and all-time prototypes

Academic Freedom at CERN’s Mission: “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 . ►Research: Seeking and finding answers to questions about the Universe e d i s ►Technology: Advancing the frontiers of technology n i st ►Collaborating: Bringing nations together through scienceady u e m r l ►Education: Training the scientists of tomorrow ” a m g dom s i i d t a a e r e e a r CERN’s Users: r p h F t y c t e i i ►…from 100 s of universities worldwide Th ecur dem ►Pupils, students, post-docs, professors, s Aca d technicians, engineers, physicists, … o “ o s i ►High turn-over (~10 k user h t Aperg year) e c n a l a Research: Academic Freedombin ►Open campus attitude (consider CERN as an ISP): No boundaries if possible: free communication & freedom to publish ►Cacophony of O/S, programming languages, applications; all-time prototypes ►Merge of professional & private life incl. mobile revolution: the trial of the new

CERN Sectors of Operations “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Office Computing Security Computing Services Security Grid Computing Security Control Systems Security

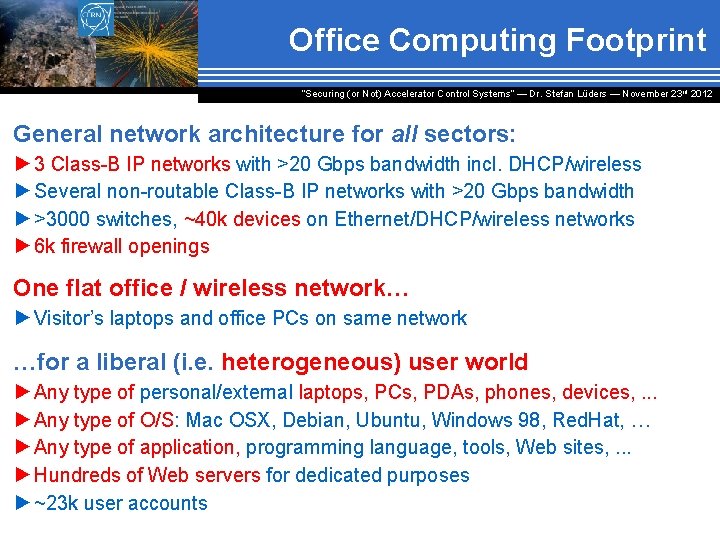
Office Computing Footprint “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 General network architecture for all sectors: ► 3 Class-B IP networks with >20 Gbps bandwidth incl. DHCP/wireless ►Several non-routable Class-B IP networks with >20 Gbps bandwidth ►>3000 switches, ~40 k devices on Ethernet/DHCP/wireless networks ► 6 k firewall openings One flat office / wireless network… ►Visitor’s laptops and office PCs on same network …for a liberal (i. e. heterogeneous) user world ►Any type of personal/external laptops, PCs, PDAs, phones, devices, . . . ►Any type of O/S: Mac OSX, Debian, Ubuntu, Windows 98, Red. Hat, … ►Any type of application, programming language, tools, Web sites, . . . ►Hundreds of Web servers for dedicated purposes ►~23 k user accounts

Computer Services Footprint “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 7 computer centers ►each with up to ~10 k nodes (~64 k cores, ~64 k HDDs) ►for central computing, accelerator operations, and physics experiments Serving a multitude of services & systems… ►Central O/S: Windows XP/7 (~6500 PCs), Windows Server 2008++, Scientific Linux 5/6, Mac OS X ►~2 M mails per day: 95% SPAM, 1% unidentified SPAM, 4% regular ►AV, file systems (AFS, DFS), disk pools (~63 PB), tape stores (~15 PB/yr), DBs, versioning systems, document servers, HR/FI/engineering app’s, collaboration tools, Paa. S virtualization service (~4 k VMs), … ►~10 k Web sites on 50 Web servers + many more for dedicated purposes ►CERN Internet Exchange Point (22 European ISPs + Telecom providers) …incl. GRID Computing ►Tier-0 (~7 k nodes), 11 x Tier-1 s, and O(100) Tier-2 s

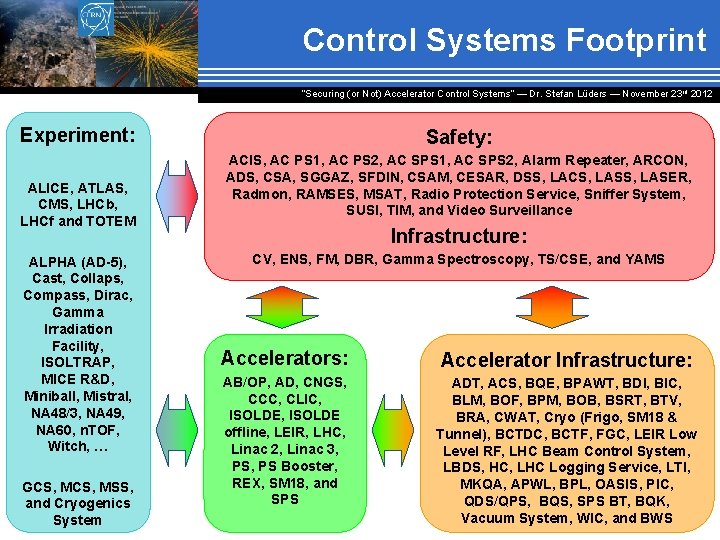
Control Systems Footprint “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Experiment: ALICE, ATLAS, CMS, LHCb, LHCf and TOTEM ALPHA (AD-5), Cast, Collaps, Compass, Dirac, Gamma Irradiation Facility, ISOLTRAP, MICE R&D, Miniball, Mistral, NA 48/3, NA 49, NA 60, n. TOF, Witch, … GCS, MSS, and Cryogenics System Safety: ACIS, AC PS 1, AC PS 2, AC SPS 1, AC SPS 2, Alarm Repeater, ARCON, ADS, CSA, SGGAZ, SFDIN, CSAM, CESAR, DSS, LACS, LASER, Radmon, RAMSES, MSAT, Radio Protection Service, Sniffer System, SUSI, TIM, and Video Surveillance Infrastructure: CV, ENS, FM, DBR, Gamma Spectroscopy, TS/CSE, and YAMS Accelerators: Accelerator Infrastructure: AB/OP, AD, CNGS, CCC, CLIC, ISOLDE offline, LEIR, LHC, Linac 2, Linac 3, PS Booster, REX, SM 18, and SPS ADT, ACS, BQE, BPAWT, BDI, BIC, BLM, BOF, BPM, BOB, BSRT, BTV, BRA, CWAT, Cryo (Frigo, SM 18 & Tunnel), BCTDC, BCTF, FGC, LEIR Low Level RF, LHC Beam Control System, LBDS, HC, LHC Logging Service, LTI, MKQA, APWL, BPL, OASIS, PIC, QDS/QPS, BQS, SPS BT, BQK, Vacuum System, WIC, and BWS

“Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint Operational Noise

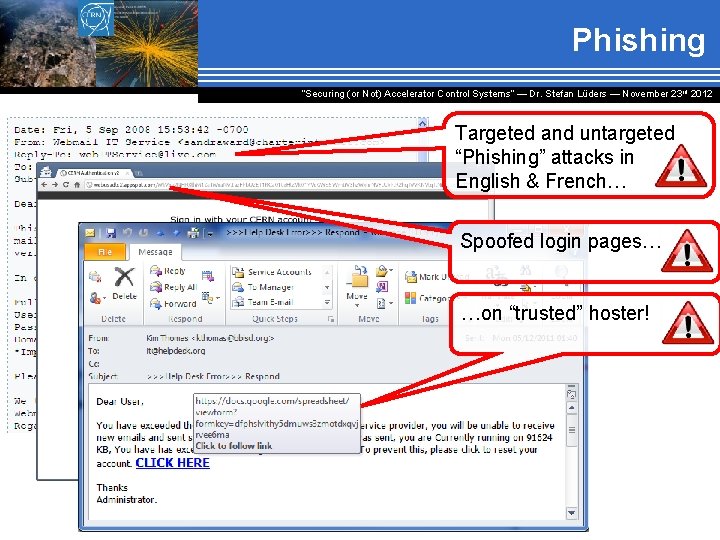
Phishing “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Targeted and untargeted “Phishing” attacks in English & French… Spoofed login pages… …on “trusted” hoster!

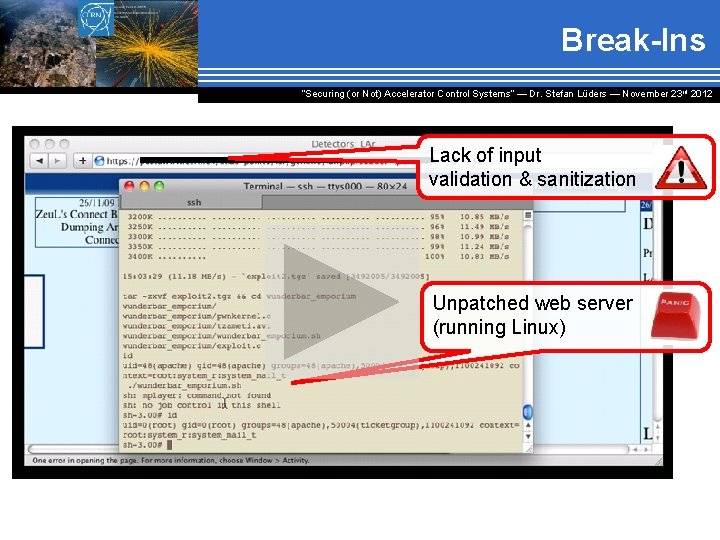
Break-Ins “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Lack of input validation & sanitization Unpatched web server (running Linux)

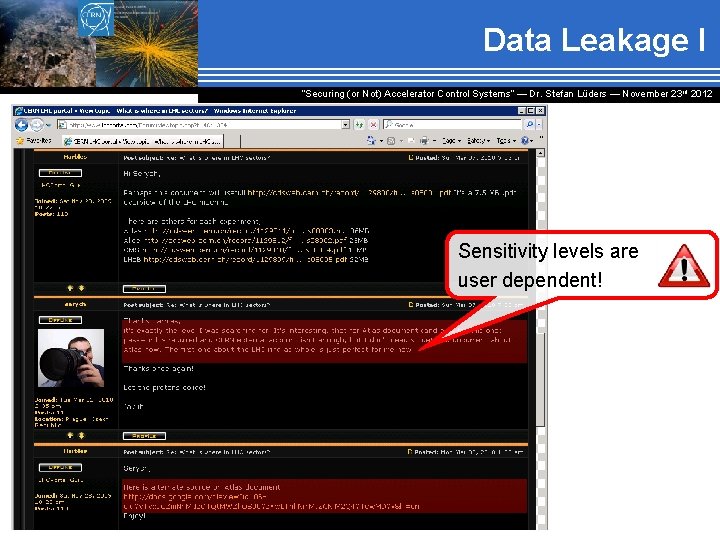
Data Leakage I “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Sensitivity levels are user dependent!

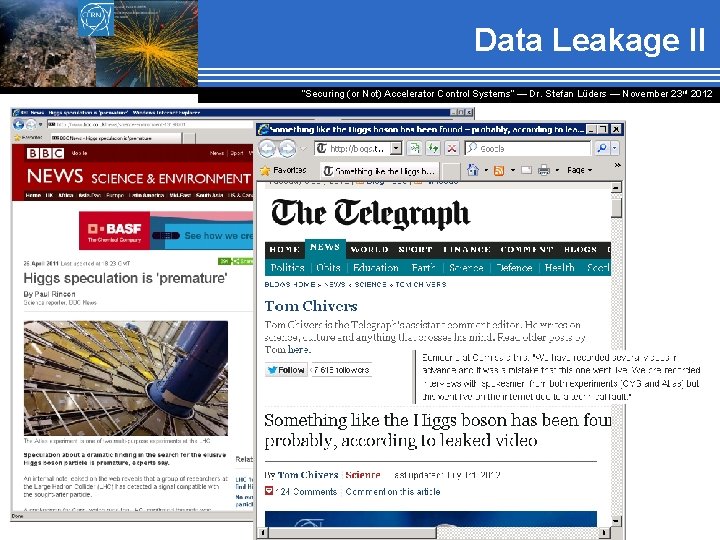
Data Leakage II “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

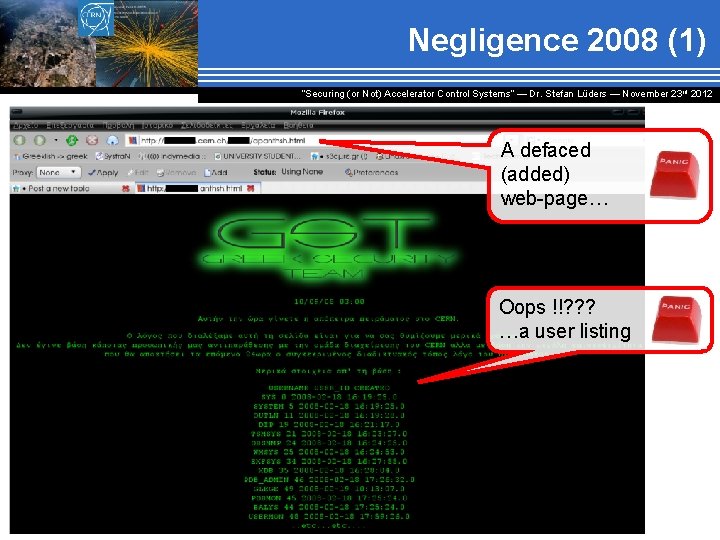
Negligence 2008 (1) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 A defaced (added) web-page… Oops !!? ? ? …a user listing

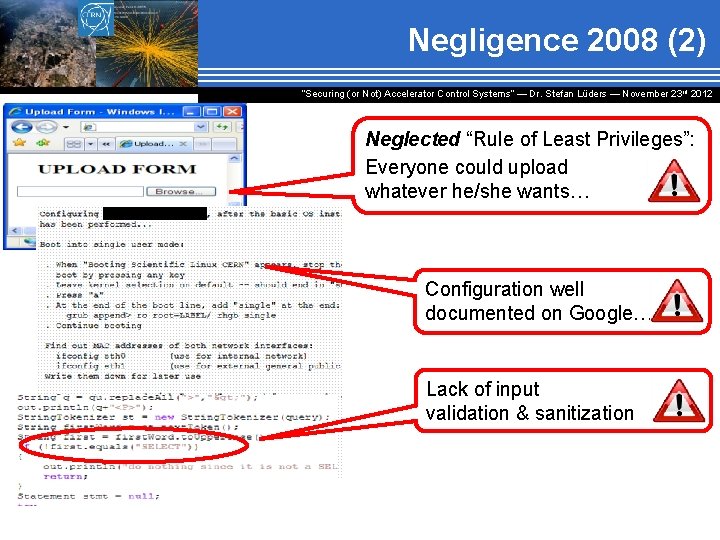
Negligence 2008 (2) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Neglected “Rule of Least Privileges”: Everyone could upload whatever he/she wants… Configuration well documented on Google… Lack of input validation & sanitization

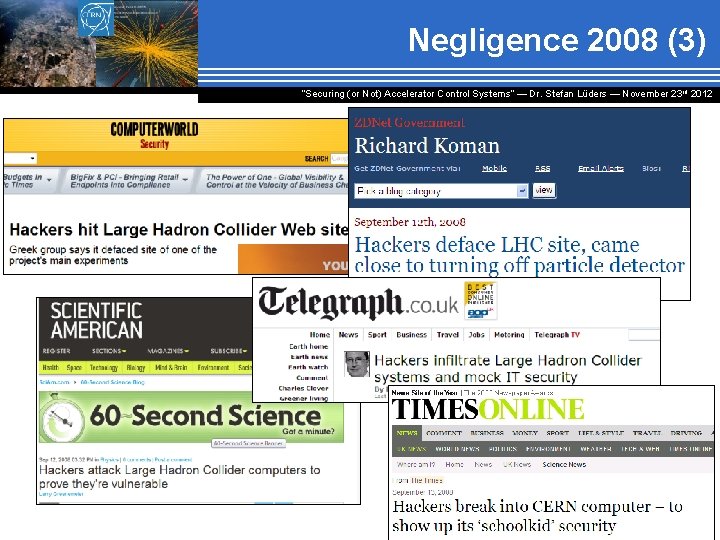
Negligence 2008 (3) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

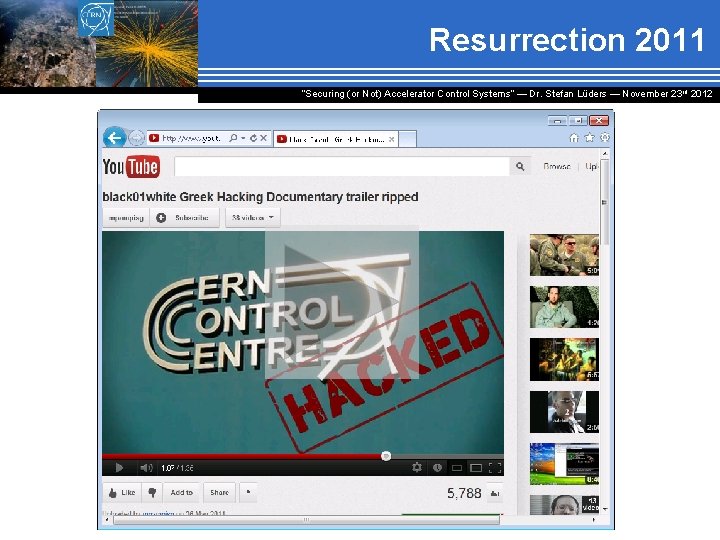
Resurrection 2011 “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

“Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint Operational Noise Control System Cyber-Security

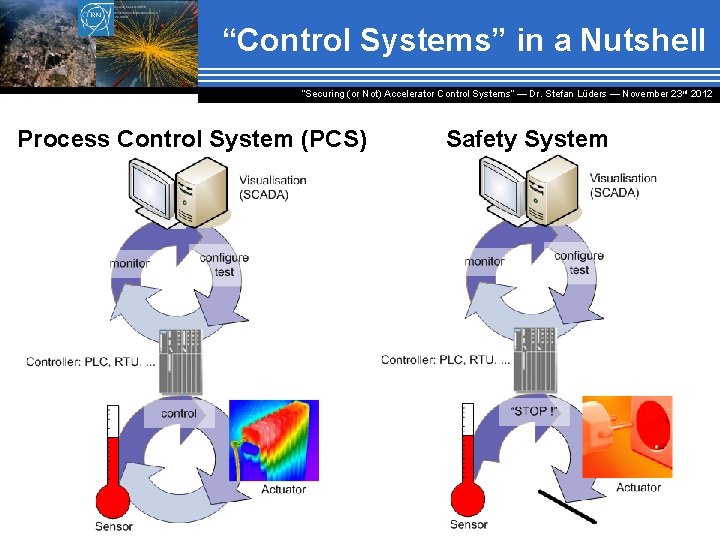
“Control Systems” in a Nutshell “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Process Control System (PCS) Safety System

This is how PCS can look like “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Controller Connections to sensors & actuators Controller Sensors & actuators

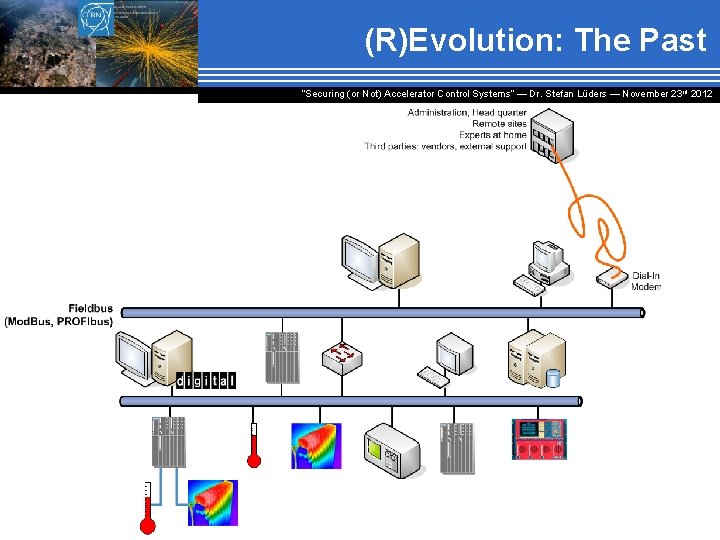
(R)Evolution: The Past “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

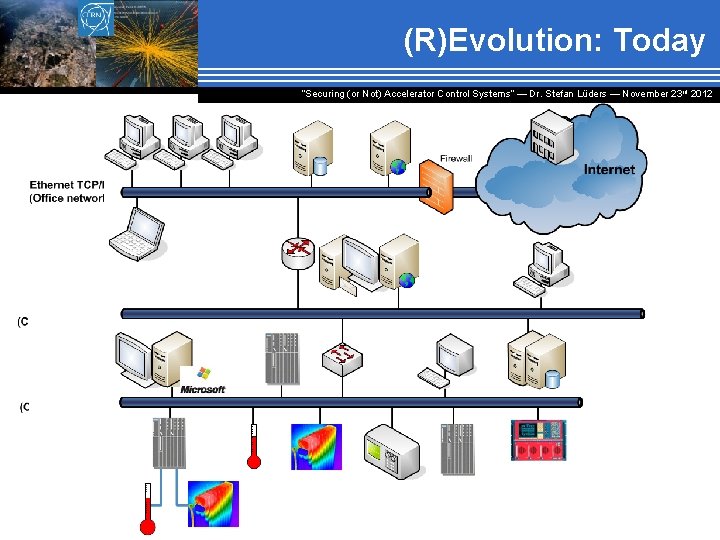
(R)Evolution: Today “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

Control Systems for Living “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 …in the electricity sector …in the oil & gas sector …in the water & waste sector …in the chemical and pharmaceutical industry …in the transport sector …for production: COBB County Electric, Georgia Middle European Raw Oil, Czech Republic Athens Water Supply & Sewage Merck Sharp & Dohme, Ireland CCTV Control Room, UK Reuters TV Master Control Room CERN Control Centre e. g. cars, planes, clothes, news …in supermarkets e. g. claimed scales, fridges The No. 1 goal for cyber-security in the 21 st century: …for facility management electricity, water, C&V …for accelerator controls

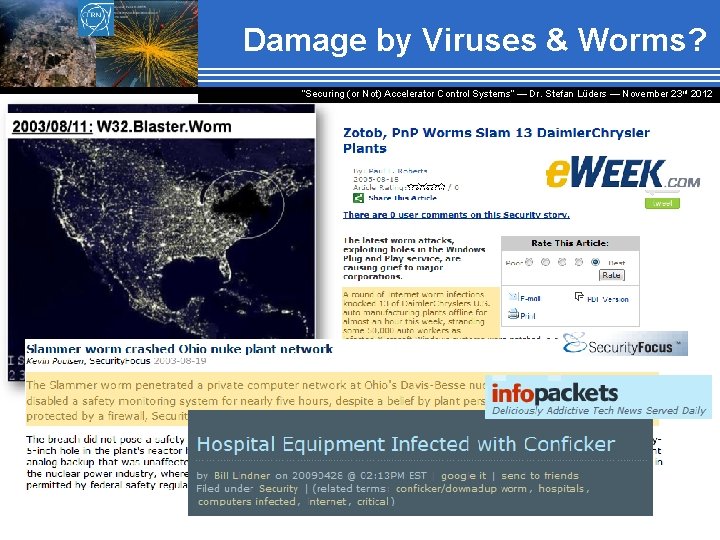
Damage by Viruses & Worms? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

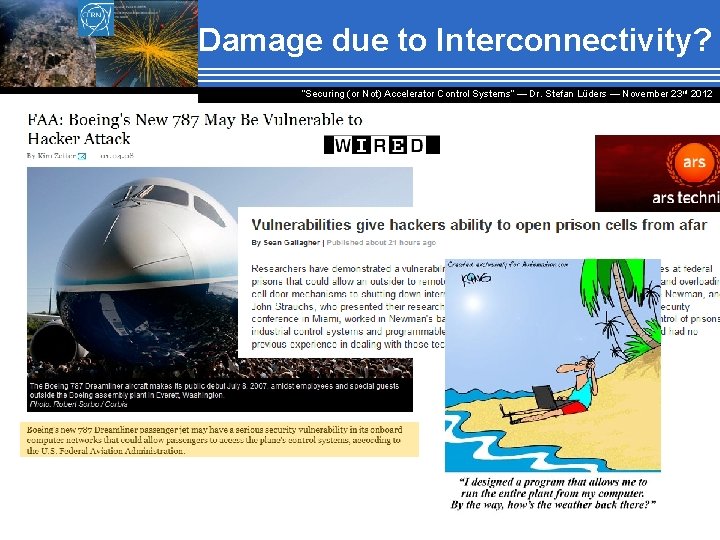
Damage due to Interconnectivity? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

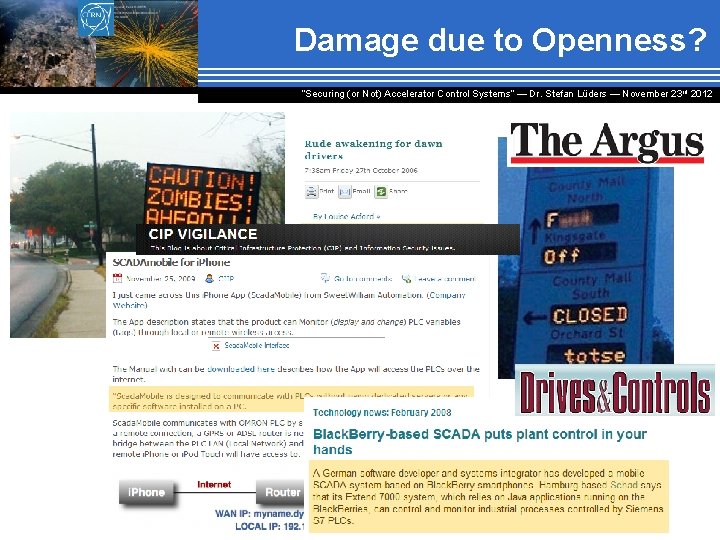
Damage due to Openness? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

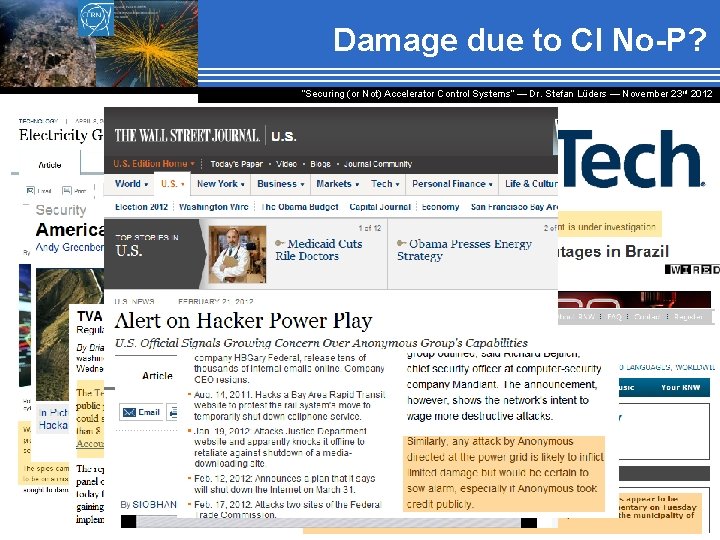
Damage due to CI No-P? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

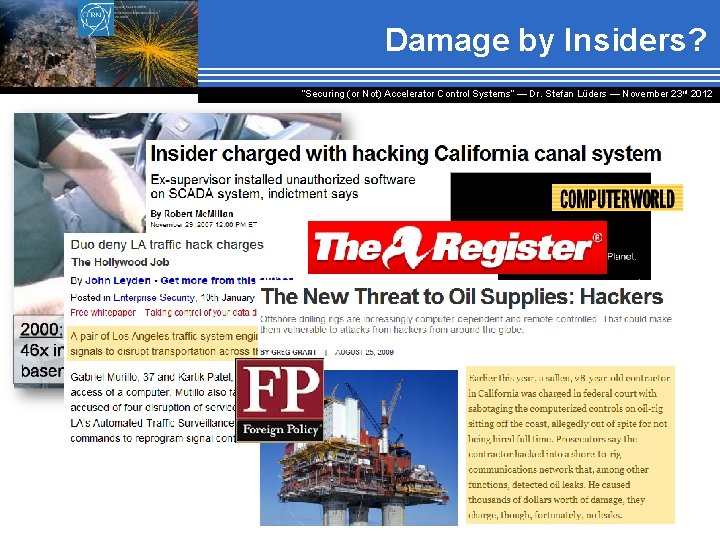
Damage by Insiders? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

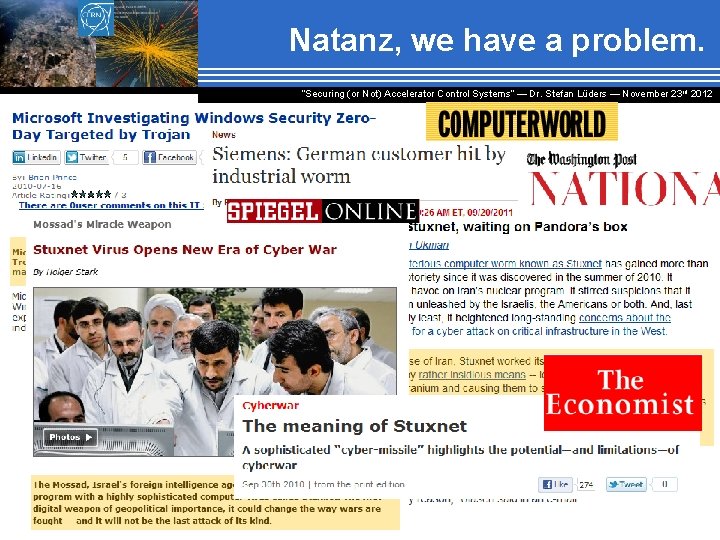
Natanz, we have a problem. “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

The Workings of Stuxnet (1) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 ► An infected USB stick was infiltrated into the plant either by malicious act or through social engineering. ► Once inserted into a Windows PC, the stick tried to compromize the O/S with up to 4(!) zero-day exploits (worth >$100 k). ► There were 4 -5 evolutions starting 6/2009. ► Infected 100. 000 PCs (60% Iran, 10% Indonesia). ► Using “rootkit” technologies and two stolen certificates, it hid from being detected. ► It tried to infect other hosts and establish a P 2 P connection “home”. So far, nothing new: A standard, but expensive virus!

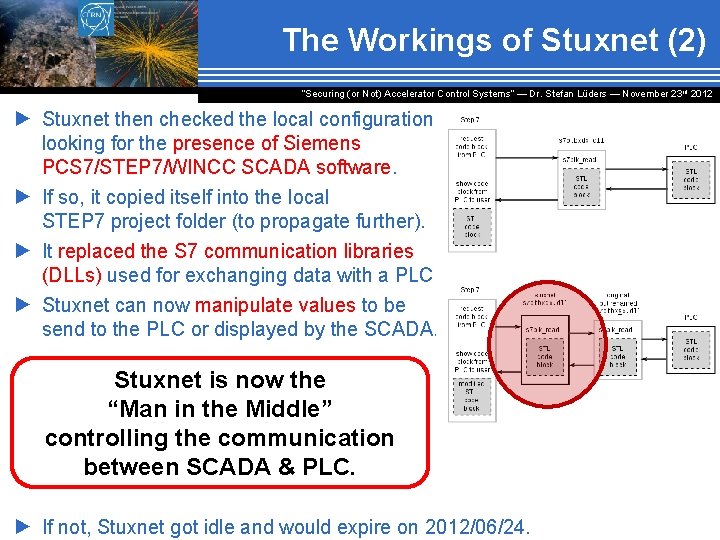
The Workings of Stuxnet (2) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 ► Stuxnet then checked the local configuration looking for the presence of Siemens PCS 7/STEP 7/WINCC SCADA software. ► If so, it copied itself into the local STEP 7 project folder (to propagate further). ► It replaced the S 7 communication libraries (DLLs) used for exchanging data with a PLC. ► Stuxnet can now manipulate values to be send to the PLC or displayed by the SCADA. Stuxnet is now the “Man in the Middle” controlling the communication between SCADA & PLC. ► If not, Stuxnet got idle and would expire on 2012/06/24.

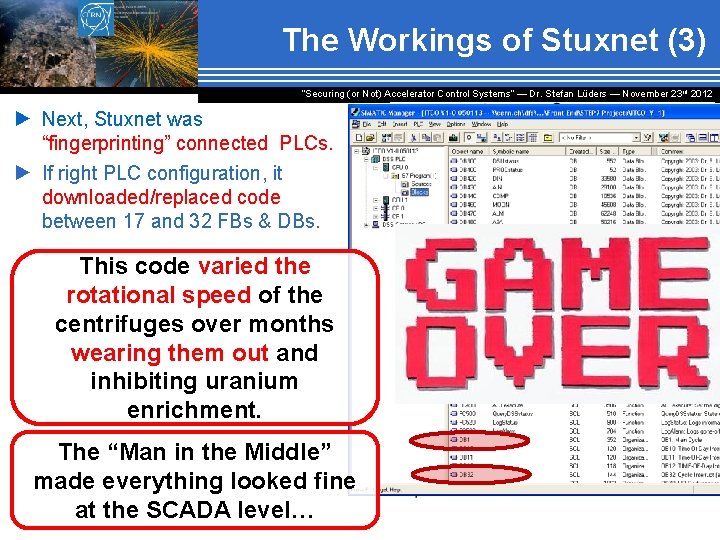
The Workings of Stuxnet (3) “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 ► Next, Stuxnet was “fingerprinting” connected PLCs. ► If right PLC configuration, it downloaded/replaced code between 17 and 32 FBs & DBs. This code varied the rotational speed of the centrifuges over months wearing them out and inhibiting uranium enrichment. The “Man in the Middle” made everything looked fine at the SCADA level…

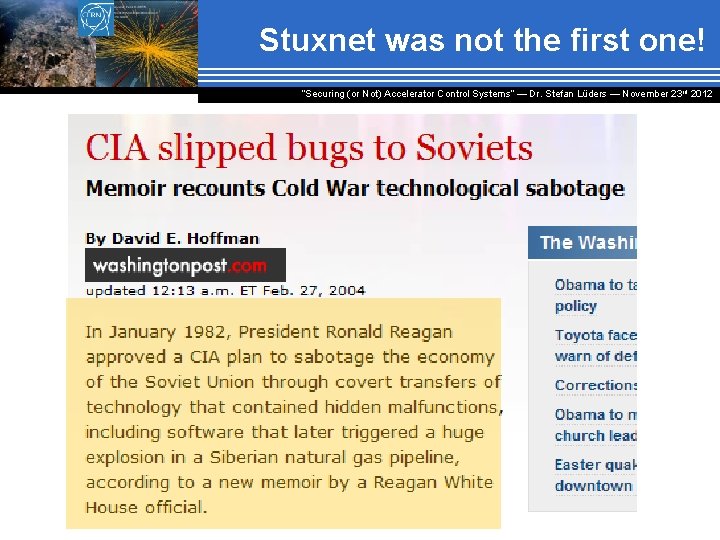
Stuxnet was not the first one! “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

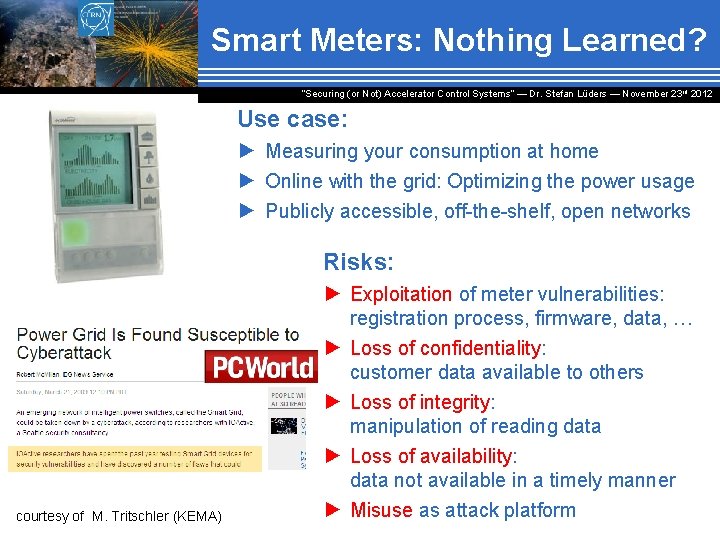
Smart Meters: Nothing Learned? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Use case: ► Measuring your consumption at home ► Online with the grid: Optimizing the power usage ► Publicly accessible, off-the-shelf, open networks Risks: courtesy of M. Tritschler (KEMA) ► Exploitation of meter vulnerabilities: registration process, firmware, data, … ► Loss of confidentiality: customer data available to others ► Loss of integrity: manipulation of reading data ► Loss of availability: data not available in a timely manner ► Misuse as attack platform

Smart Meters: Nothing Learned? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Use case: ► Measuring your consumption at home ► Online with the grid: Optimizing the power usage ► Publicly accessible, off-the-shelf, open networks Risks: ► Exploitation of P meter 2) vulnerabilities: S registration process, firmware, data, … P X : e r o e f ► Loss of confidentiality: r e o f b (customer data available to others s e ’ b s 0 ’ 8 0 is 9 e h t h e t d th ► Loss of integrity: n a i n h i s s m manipulation of reading data We C e d P o s M w o ► Loss of availability: u d n i W data not available in a timely manner u ► Misuse as attack platform courtesy of M. Tritschler (KEMA)

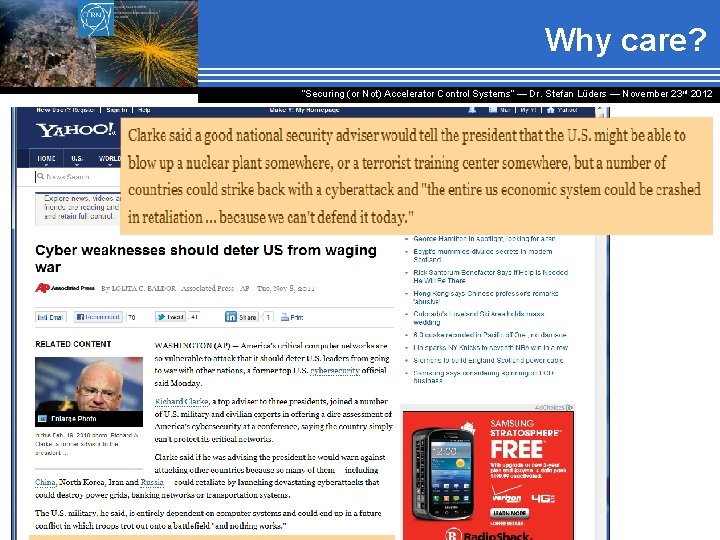
Why care? “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

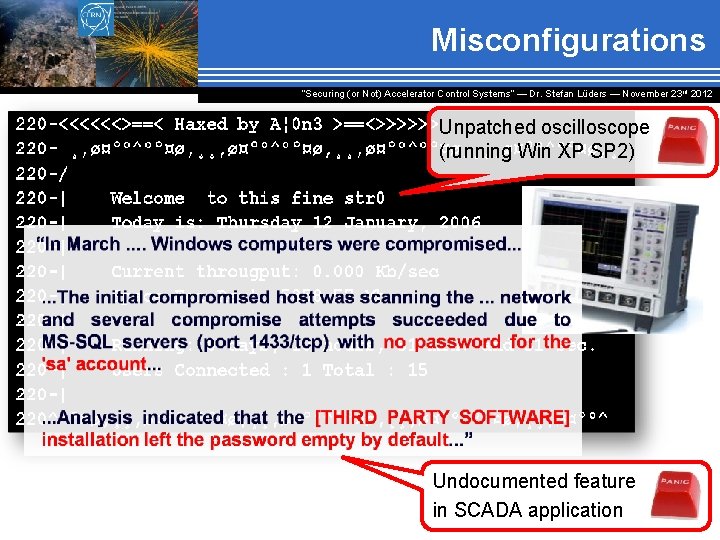
Misconfigurations “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Unpatched oscilloscope (running Win XP SP 2) Undocumented feature in SCADA application

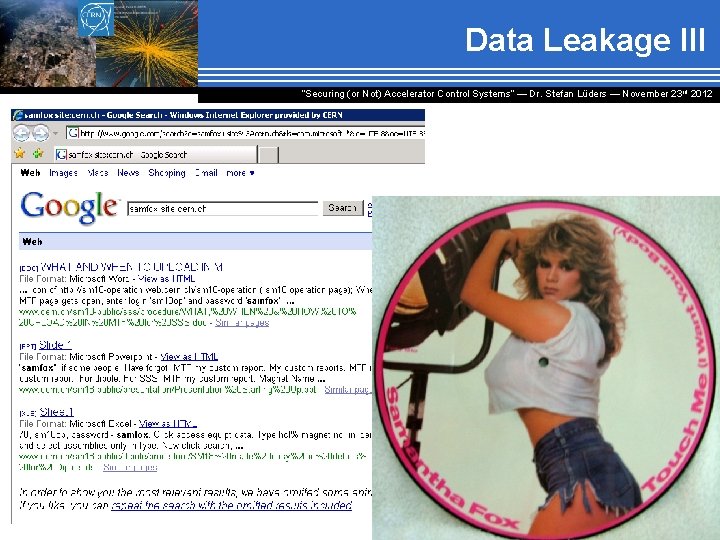
Data Leakage III “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

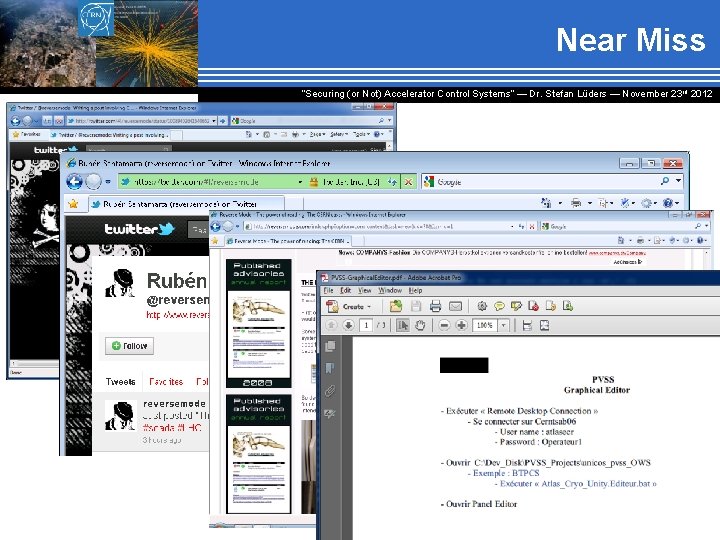
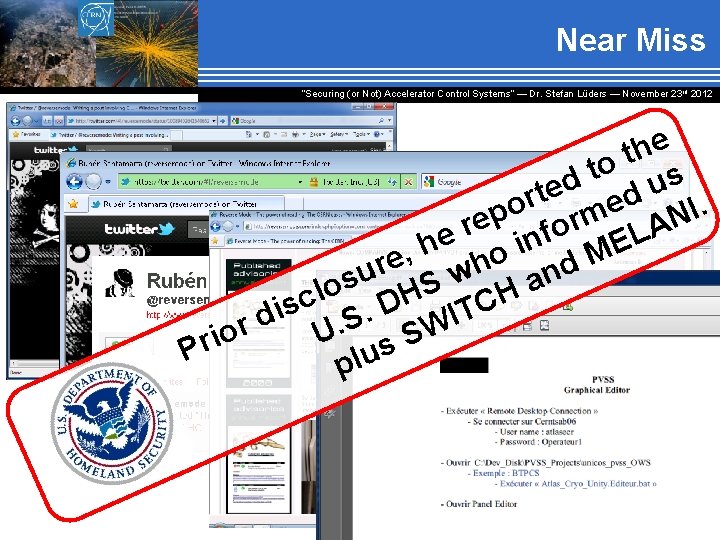
Near Miss “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

Near Miss “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 e h t o t s d u e t d r e. o I p m N r e r A o f L e n E i h , M o e wh r d u n s a S o l H H c C D s i T. I d S. r W U o S i s Pr u l p

“Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint Operational Noise Control System Cyber-Security Securing (or Not) Accelerator Control Systems

Difficult to Act “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 For the LHC, the priorities are: ► 1. Safety 2. Availability 3. (or lower) Security Accelerator controls depends on lots of legacy: ► Paradigms, mindsets and basic designs fixed long time ago ► Complexity makes major changes difficult (impossible? ) ► IT principles were embraced, but not necessarily security Security is usually plugged on top (if at all) ► Implementation faces human/technical/management resistance (“Nothing happened so far”) ► We have an all-time prototype…: dev & ops on “live” hardware Defense-in-Depth is the key… ► …but extremely difficult!!!

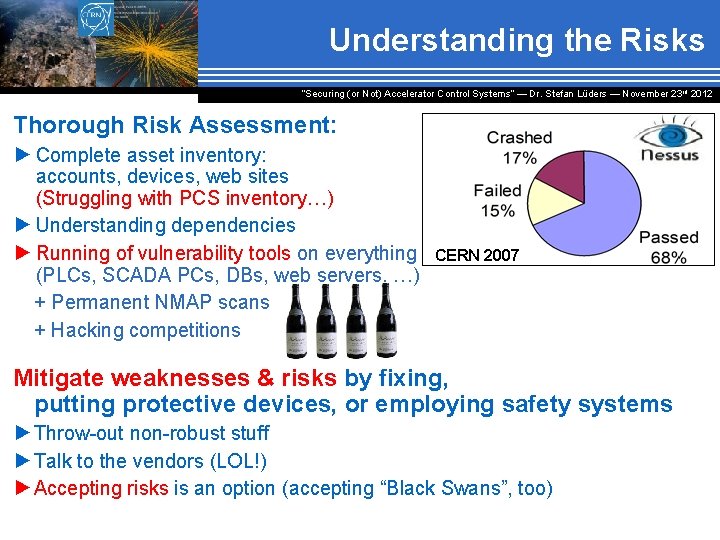
Understanding the Risks “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Thorough Risk Assessment: ► Complete asset inventory: accounts, devices, web sites (Struggling with PCS inventory…) ► Understanding dependencies ► Running of vulnerability tools on everything (PLCs, SCADA PCs, DBs, web servers, …) + Permanent NMAP scans + Hacking competitions CERN 2007 Mitigate weaknesses & risks by fixing, putting protective devices, or employing safety systems ►Throw-out non-robust stuff ►Talk to the vendors (LOL!) ►Accepting risks is an option (accepting “Black Swans”, too)

Understanding the Risks “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Thorough Risk Assessment: , e l ► Complete asset inventory: p i t l accounts, devices, web sites u ms. m (Struggling with PCS inventory…) y e t b s y y d t i ► Understanding dependencies s e l r i y e b t fe vaila ► Running of vulnerability tools on everything ov. CERNs 2007 a c y (PLCs, SCADA PCs, DBs, web servers, …) nt a t e n f e u a d : s + Permanent NMAP scans n e e c C p uen e + Hacking competitions. LH d n q i e T ons I Mitigate weaknesses & risks by fixing, c. ax putting protective M devices, or employing safety systems ►Throw-out non-robust stuff ►Talk to the vendors (LOL!) ►Accepting risks is an option (accepting “Black Swans”, too)

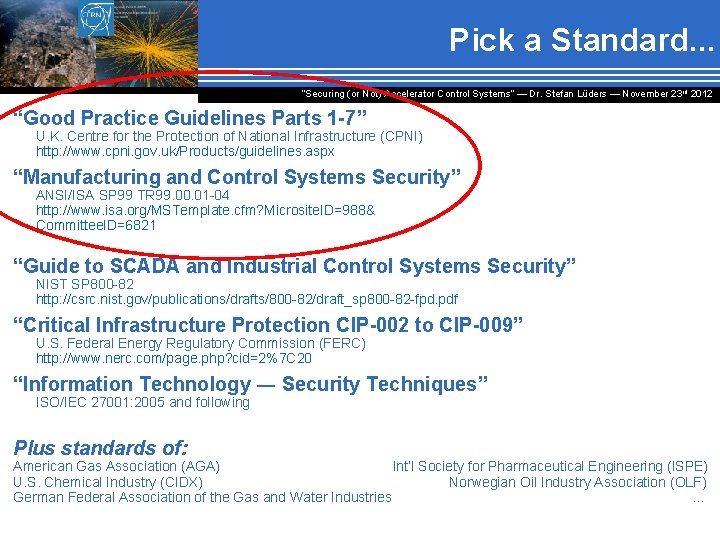
Pick a Standard. . . “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 “Good Practice Guidelines Parts 1 -7” U. K. Centre for the Protection of National Infrastructure (CPNI) http: //www. cpni. gov. uk/Products/guidelines. aspx “Manufacturing and Control Systems Security” ANSI/ISA SP 99 TR 99. 00. 01 -04 http: //www. isa. org/MSTemplate. cfm? Microsite. ID=988& Committee. ID=6821 “Guide to SCADA and Industrial Control Systems Security” NIST SP 800 -82 http: //csrc. nist. gov/publications/drafts/800 -82/draft_sp 800 -82 -fpd. pdf “Critical Infrastructure Protection CIP-002 to CIP-009” U. S. Federal Energy Regulatory Commission (FERC) http: //www. nerc. com/page. php? cid=2%7 C 20 “Information Technology ― Security Techniques” ISO/IEC 27001: 2005 and following Plus standards of: American Gas Association (AGA) Int’l Society for Pharmaceutical Engineering (ISPE) U. S. Chemical Industry (CIDX) Norwegian Oil Industry Association (OLF) German Federal Association of the Gas and Water Industries. . .

Pick a Standard. . . “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 http: //xkcd. com

Pick a Standard. . . “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 h c i h . e n o w r e att m y l l a ns. e r t o. ’ i t n a s nd t ’. e n e o a e n d o t m ou c I d. m ne reco re y econ o k e s Pic ly its n wh ith a p Ap e dow eck w t o N ss-ch Cdaro org ac. a /sc sis . m ww : //w http: //xkcd. com

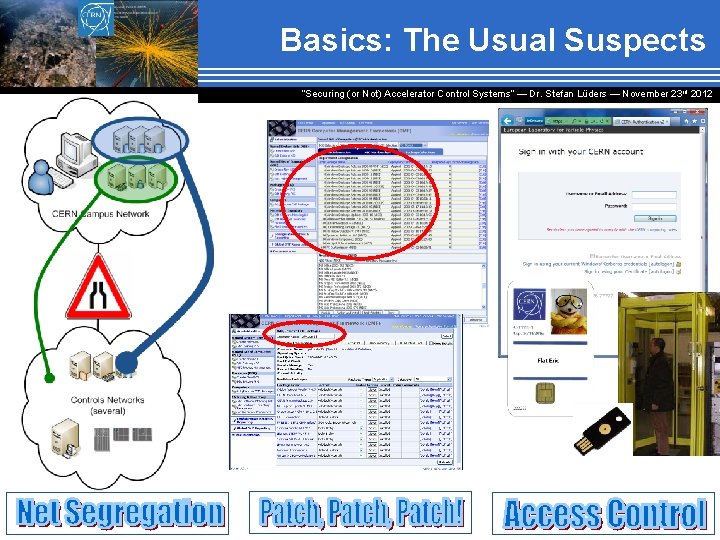
Basics: The Usual Suspects “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012

Basics: The Usual Suspects “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 l! a i c e. p t s p t e o d n. T I e y r l r a to a l s i e c m m r i e u t s o s g s y t n S i u l h o t o r y o t r t n e y v Co Tr re e u c e s &

Reviewing Procedures “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 ►Training! ►(Automatic) code analyzers ►Software integration framework with verified nightly builds (like for standard IT) Versioning ►Software versioning systems (CVS/SVN) Applying “Security Baselines” (i. e. a contract on security with simple recommendations for configuration settings, protective means, & procedures) Configuration Management ► Configuration verification prior each “fill” https: //cern. ch/security/rules/en/baselines. shtml Software Development Life-Cycle

Reviewing Procedures “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Software Development Life-Cycle settings, protective means, & procedures) Configuration Management ► Configuration verification prior each “fill” https: //cern. ch/security/rules/en/baselines. shtml f o t r a , p y t i e l a m n o ! o c i y t e t i c b l i n t s e fu inab u m lik Versioning a t ” n i ty ll – i a ►Software versioning systems (CVS/SVN) r m u a r , c e Se e ov bility “ Applying “Security Baselines” a h l t i a (i. e. a contract on security with v a simple recommendations for configuration ►Training! ►(Automatic) code analyzers ►Software integration framework with verified nightly builds (like for standard IT)

“Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s security footprint Operational Noise Control System Cyber-Security Securing (or Not) Accelerator Control System This is a “people” problem

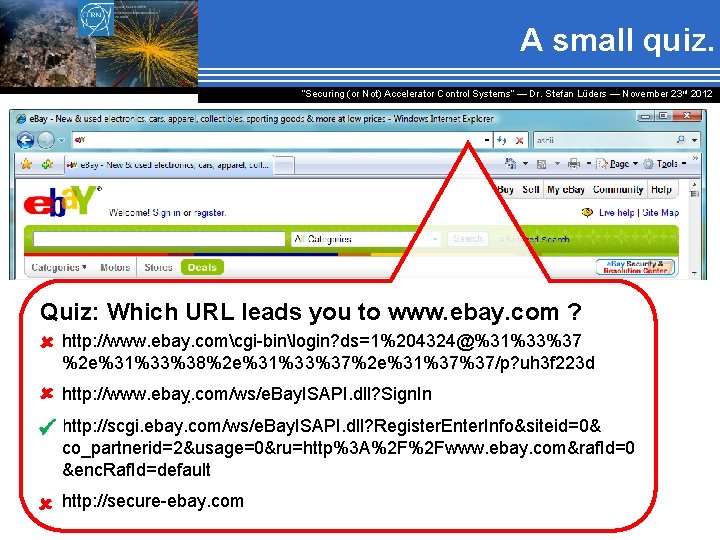
A small quiz. “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Quiz: Which URL leads you to www. ebay. com ? ► http: //www. ebay. comcgi-binlogin? ds=1%204324@%31%33%37 %2 e%31%33%38%2 e%31%33%37%2 e%31%37%37/p? uh 3 f 223 d ► http: //www. ebaỵ. com/ws/e. Bay. ISAPI. dll? Sign. In ► http: //scgi. ebay. com/ws/e. Bay. ISAPI. dll? Register. Enter. Info&siteid=0& co_partnerid=2&usage=0&ru=http%3 A%2 F%2 Fwww. ebay. com&raf. Id=0 &enc. Raf. Id=default ► http: //secure-ebay. com

Intelligent clientele “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 “May I point out that I do not have a tail and do not feel like being treated like a circus dog. ” “Why there are idiotic policies in place to forbid use of certain technologies? ” “I failed to pass the security courses, the questions were so stupid, that sometimes it's difficult to answer. If you want to meet with me personally, I can teach you computer security. ” “I fully recognise the importance of computer security at CERN. However, I am not sure that you have yet appreciated that computer security is not the raison d' être of CERN. Computer security must always be balanced with the need for CERN to carry out its experiments. I do not believe that [. . . ] poses a strong security risk and you have not explained to us why it does. ”

CERN Security Paradigm “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 Find balance between “Academic Freedom”, “Operations” and “Computer Security” “Academic Freedom” means “Responsibility” ►(I, as Security Officer, decline to accept that responsibility) ►Instead, computer security at CERN is delegated to all users of computing resources (sys admins, controls experts, secretaries, …) ►If they don’t feel ready, they can pass that responsibility to the CERN IT department using central services. The CERN Security Team acts as facilitator and enabler: ►No big sticks, no heavy rules.

“Security” is a People Problem! “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 “Security” is dealt with as with “Safety”. CERN aims for a “change of culture” & “a new mind set” ► Basic awareness training to everyone, esp. newcomers ► Every owner of a computer account must follow online security courses every 3 years. ► Provisioning of static code analyzers ► Dedicated training on secure development (Java, C/C++, Perl, Python, PHP, web, . . . ) ► Baselines & consulting Once people understand, the rest is easy: care, SLDC, use of standards, …

“Security” is a People Problem! “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 “Security” is dealt with as with “Safety”. e l p o e CERN aims for a ! p y t e i l i “change of culture” & “a new mind set” abl b i n s. e e n e ► Basic awareness training to everyone, o d r p f n s a r e esp. newcomers t o r f s i r i s s e e s ► Every owner of a computer account m th A mustefollow o c online security courses every 3 years. m t s u e s r s ► Provisioning of static code analyzers a e h y l T l development u ► Dedicated training on fsecure to (Java, C/C++, Perl, Python, PHP, web, . . . ) ► Baselines & consulting Once people understand, the rest is easy: care, SLDC, use of standards, …

Start Earlier! “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 We have to start sensibilization early! ► Being aware of risks is the first step towards mitigation ► Today‘s kids are the programmers of tomorrow Why are IT graduates still weak on “security”? ► They learn programming, O/S, DBs, … for their BSc, but “security” just comes later in the MSc curriculum Why can software vendors still ship out insecure applications / devices? ► Why can I sue [car vendor] for a non-working brake but not [software vendor] for a vulnerability? ► Who has to do due diligence?

Summary “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012 CERN’s Security Footprint is heterogeneous and vast. However, security events happen and will continue to happen. Defence-in-Depth is the key. PCS security must align with IT security. Make security part as functionality, usability, availability, performance, maintainability! “Academic Freedom” means “responsibility” Enable people to assume theirs.

Literature “Securing (or Not) Accelerator Control Systems“ — Dr. Stefan Lüders ― November 23 rd 2012