Securing OPC Classic Control Systems Tofino OPC Enforcer











- Slides: 18

Securing OPC Classic Control Systems Tofino OPC Enforcer Technology Eric Byres, Chief Technology Officer, Byres Security Inc.

Why is OPC Classic So Hard to Secure?

OPC Classic • • OPC Classic is the world’s leading technology for integrating different automation products. Formerly known as OLE for Process Control, (where OLE stood for Object Linking and Embedding) Includes all OPC standards that are based on Microsoft's DCOM Technology (i. e. all but OPC-UA) Unfortunately OPC is famous for its poor security…

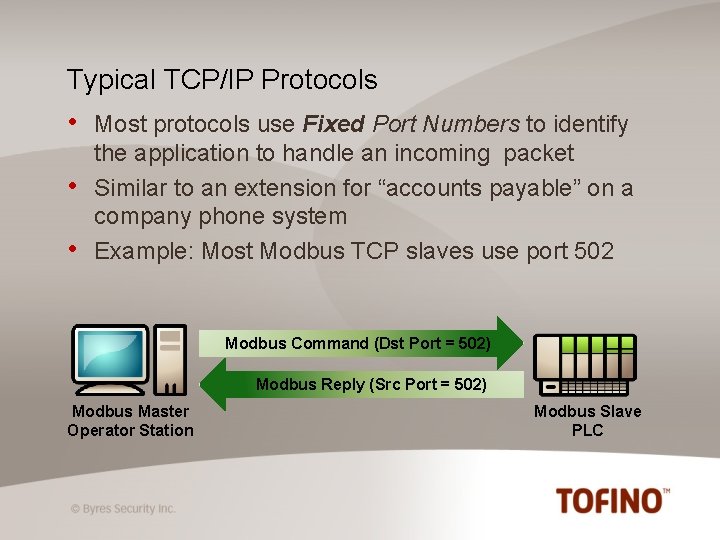
Typical TCP/IP Protocols • • • Most protocols use Fixed Port Numbers to identify the application to handle an incoming packet Similar to an extension for “accounts payable” on a company phone system Example: Most Modbus TCP slaves use port 502 Modbus Command (Dst Port = 502) Modbus Reply (Src Port = 502) Modbus Master Operator Station Modbus Slave PLC

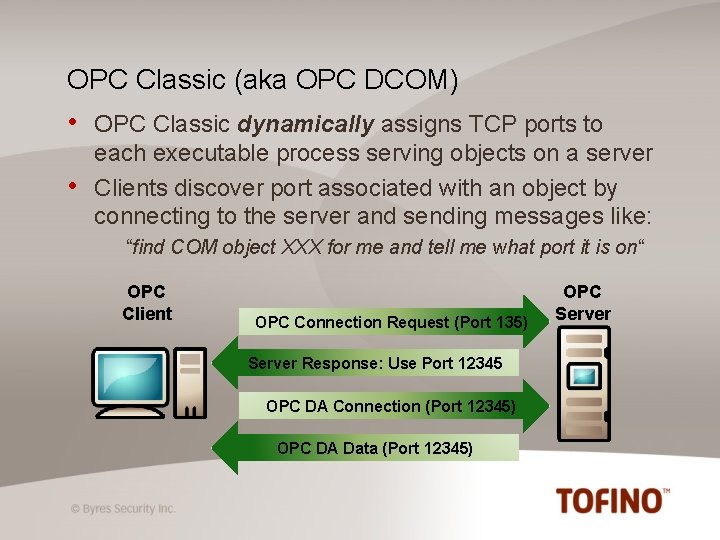
OPC Classic (aka OPC DCOM) • • OPC Classic dynamically assigns TCP ports to each executable process serving objects on a server Clients discover port associated with an object by connecting to the server and sending messages like: “find COM object XXX for me and tell me what port it is on“ OPC Client OPC Connection Request (Port 135) Server Response: Use Port 12345 OPC DA Connection (Port 12345) OPC DA Data (Port 12345) OPC Server

Until Now - An “Unfirewallable” Protocol • Because OPC is free to use any port between 1024 and 65535 it is “IT firewall unfriendly” • • You don’t know in advance what port the server will use So you can’t define the firewall rule You have to leave all ports open on your firewall Configuring your firewall to leave such a wide range of ports open creates a serious security hole 2222 Rockwell-CSP 2404 IEC 60870 -5 -104 5000 Mitsibishi MELSCQNA 5450 PI Data Historian 9100 Omron FINS And 1000’s more!

It Gets Worse! OPC/DCOM in the Real World • • • DCOM callbacks in OPC are not handled on the same connection that is used for client/server calls Some OPC servers reject the first few connection attempts after they tell the client to use a specific port, completely breaking most firewall state engines! All this has made the industry consider OPC Firewalls virtually impossible

The Tofino OPC Classic Enforcer

What is the Tofino OPC Classic Enforcer? • • Loadable security module that makes the Tofino Firewall “OPC-aware” Uses deep packet inspection technology to manage OPC traffic behind the scenes

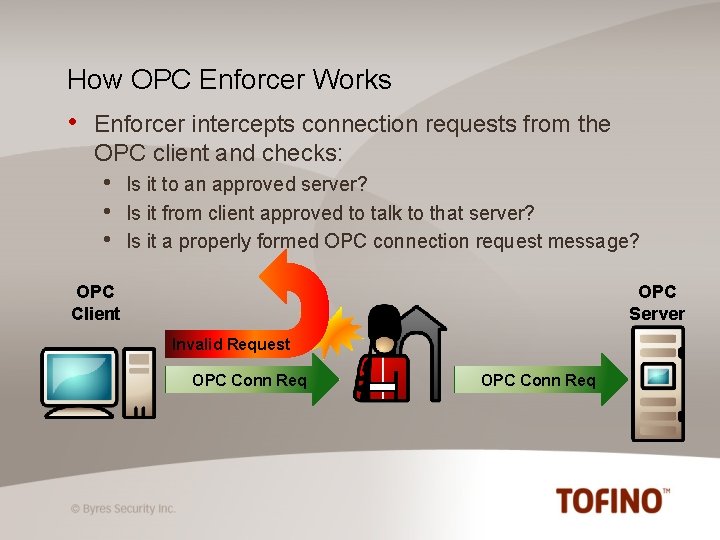
How OPC Enforcer Works • Enforcer intercepts connection requests from the OPC client and checks: • • • Is it to an approved server? Is it from client approved to talk to that server? Is it a properly formed OPC connection request message? OPC Client OPC Server Invalid Request OPC Conn Req

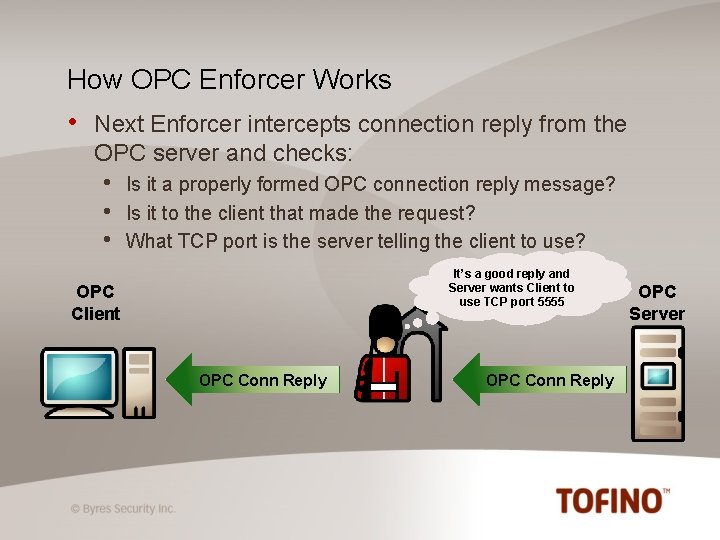
How OPC Enforcer Works • Next Enforcer intercepts connection reply from the OPC server and checks: • • • Is it a properly formed OPC connection reply message? Is it to the client that made the request? What TCP port is the server telling the client to use? It’s a good reply and Server wants Client to use TCP port 5555 OPC Client OPC Conn Reply OPC Server

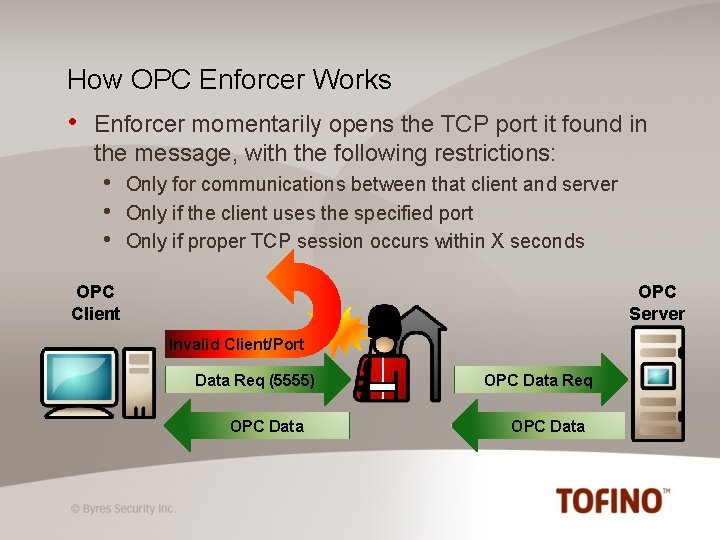
How OPC Enforcer Works • Enforcer momentarily opens the TCP port it found in the message, with the following restrictions: • • • Only for communications between that client and server Only if the client uses the specified port Only if proper TCP session occurs within X seconds OPC Client OPC Server Invalid Client/Port Data Req (5555) OPC Data Req OPC Data

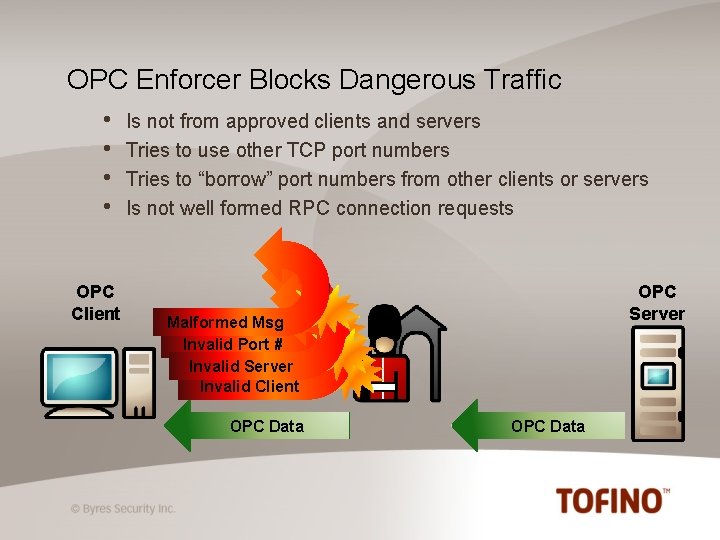
OPC Enforcer Blocks Dangerous Traffic • • OPC Client Is not from approved clients and servers Tries to use other TCP port numbers Tries to “borrow” port numbers from other clients or servers Is not well formed RPC connection requests OPC Server Malformed Msg Invalid Port # Invalid Server Invalid Client OPC Data

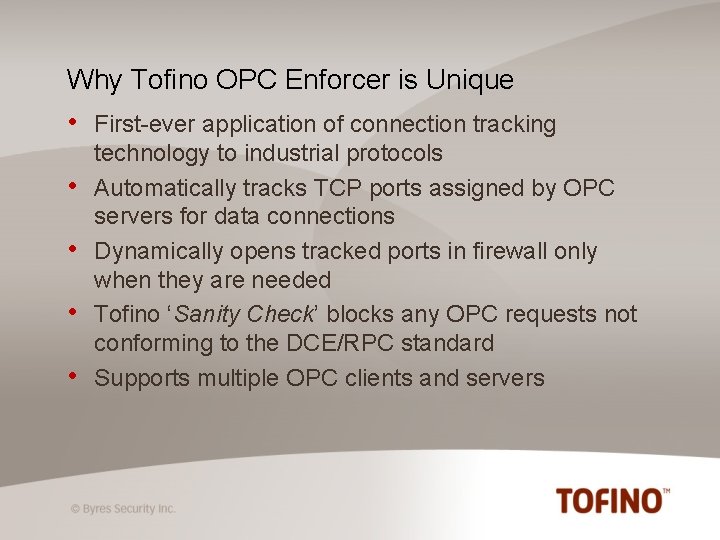
Why Tofino OPC Enforcer is Unique • • • First-ever application of connection tracking technology to industrial protocols Automatically tracks TCP ports assigned by OPC servers for data connections Dynamically opens tracked ports in firewall only when they are needed Tofino ‘Sanity Check’ blocks any OPC requests not conforming to the DCE/RPC standard Supports multiple OPC clients and servers

Typical Applications • • Manage all traffic on systems that use OPC DA, HDA or A&E Secure data transfers to and from data historians and supervisory applications Protect safety instrumentation systems Combine with Tofino VPN LSM for ultra secure remote OPC connections

Benefits of Tofino OPC Enforcer • • • Simple to use – no changes needed to any OPC servers or clients Just install on the network and configure which servers and clients you want to communicate Works with OPC DA, HDA and A&E standards Secures against both accidental and malicious traffic Endorsed by the OPC Foundation

Ordering the Tofino OPC Enforcer • Tofino OPC Enforcer LSM • • Requirements: • • Available Now Tofino Security Appliance Tofino Central Management Platform version 1. 6 or better Tofino Firewall LSM Additional Resources: • • www. tofinosecurity. com/opc OPC Foundation Endorsed White Paper, “Securing Your OPC Classic Control System”
