Securing Email Outline Electronic mail protocols n Electronic





![Electronic Mail: SMTP [RFC 5321] n n n uses TCP to reliably transfer email Electronic Mail: SMTP [RFC 5321] n n n uses TCP to reliably transfer email](https://slidetodoc.com/presentation_image_h/219a3d0ff70e9eb194b5d9c84978a131/image-7.jpg)





![n POP 3 [tcp port 110] § Can work with temporary network connections, view n POP 3 [tcp port 110] § Can work with temporary network connections, view](https://slidetodoc.com/presentation_image_h/219a3d0ff70e9eb194b5d9c84978a131/image-22.jpg)




















- Slides: 50

Securing Email

Outline Electronic mail protocols n Electronic mail content security n § PGP -- Pretty Good Privacy § PEM -- Privacy Enhanced Mail § S/MIME 2

n Structure of email servers § Usually the sender does not directly talk to the receiver § Dedicated mail server (in x. 400 structure, it is called message transfer agents: MTA) § The source and destination are called mail user agents (MUA) § The email could go through several MTAs 3

n Advantages of multiple store-andforward MTAs § Adaptable to temporary network partitions § Easy to form chain of trust § Easy to implement traffic control within a company § Easy to connect partitions of networks using different protocols 4

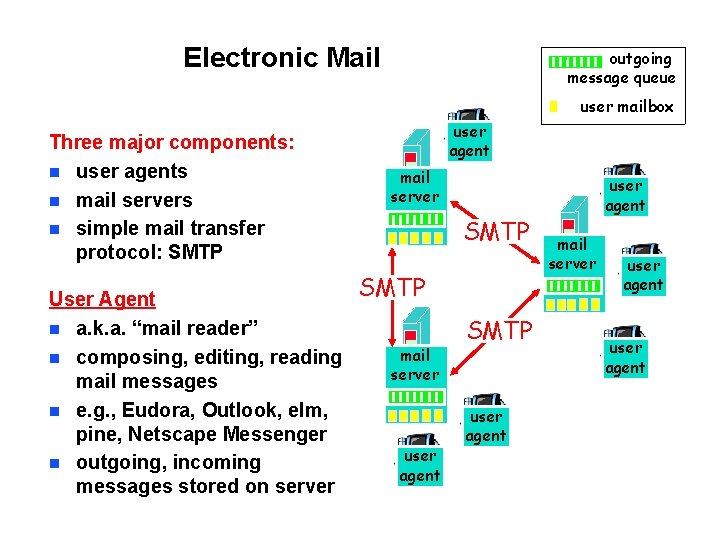
Electronic Mail outgoing message queue user mailbox Three major components: n user agents n mail servers n simple mail transfer protocol: SMTP User Agent n a. k. a. “mail reader” n composing, editing, reading mail messages n e. g. , Eudora, Outlook, elm, pine, Netscape Messenger n outgoing, incoming messages stored on server user agent mail server SMTP mail server user agent SMTP user agent mail server user agent

Electronic Mail: mail servers user agent Mail Servers n n mailbox contains incoming messages for user message queue of outgoing (to be sent) mail messages SMTP protocol between mail servers to send email messages § client: sending mail server § “server”: receiving mail server Note that “mail server” behaves both as SMTP server and SMTP client mail server SMTP mail server user agent SMTP user agent mail server user agent 6
![Electronic Mail SMTP RFC 5321 n n n uses TCP to reliably transfer email Electronic Mail: SMTP [RFC 5321] n n n uses TCP to reliably transfer email](https://slidetodoc.com/presentation_image_h/219a3d0ff70e9eb194b5d9c84978a131/image-7.jpg)
Electronic Mail: SMTP [RFC 5321] n n n uses TCP to reliably transfer email message from client to server, port 25/587 direct transfer: sending server to receiving server three phases of transfer § handshaking (greeting) § transfer of messages § closure command/response interaction § commands: ASCII text § response: status code and phrase messages must be in 7 -bit ASCII 7

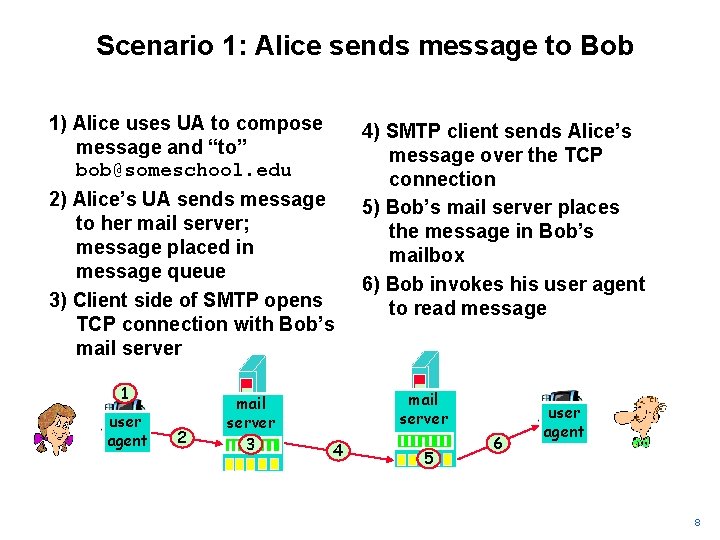
Scenario 1: Alice sends message to Bob 1) Alice uses UA to compose message and “to” bob@someschool. edu 2) Alice’s UA sends message to her mail server; message placed in message queue 3) Client side of SMTP opens TCP connection with Bob’s mail server 1 user agent 2 mail server 3 4) SMTP client sends Alice’s message over the TCP connection 5) Bob’s mail server places the message in Bob’s mailbox 6) Bob invokes his user agent to read message mail server 4 5 6 user agent 8

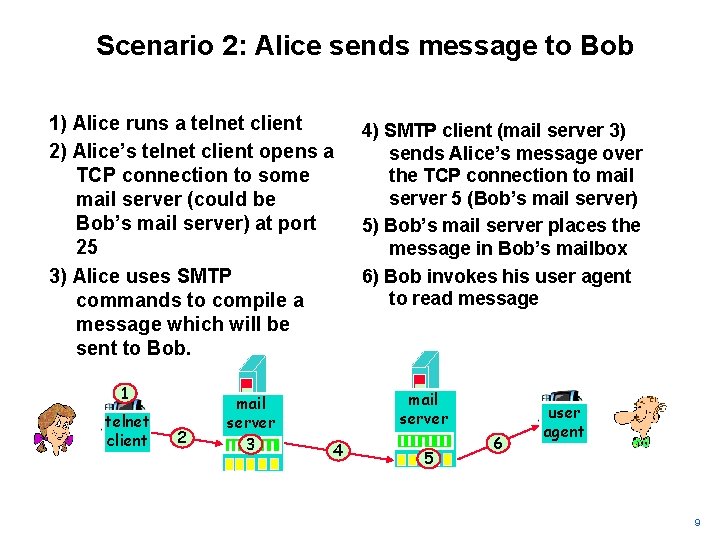
Scenario 2: Alice sends message to Bob 1) Alice runs a telnet client 2) Alice’s telnet client opens a TCP connection to some mail server (could be Bob’s mail server) at port 25 3) Alice uses SMTP commands to compile a message which will be sent to Bob. 1 telnet client 2 mail server 3 4) SMTP client (mail server 3) sends Alice’s message over the TCP connection to mail server 5 (Bob’s mail server) 5) Bob’s mail server places the message in Bob’s mailbox 6) Bob invokes his user agent to read message mail server 4 5 6 user agent 9

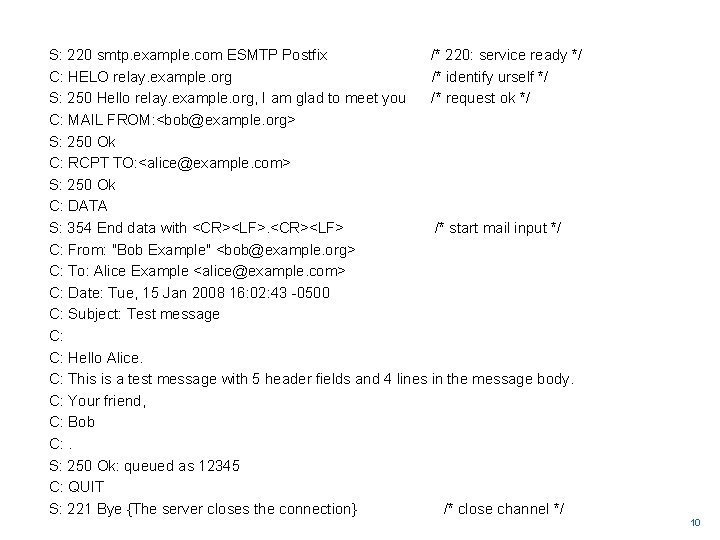
S: 220 smtp. example. com ESMTP Postfix /* 220: service ready */ C: HELO relay. example. org /* identify urself */ S: 250 Hello relay. example. org, I am glad to meet you /* request ok */ C: MAIL FROM: <bob@example. org> S: 250 Ok C: RCPT TO: <alice@example. com> S: 250 Ok C: DATA S: 354 End data with <CR><LF> /* start mail input */ C: From: "Bob Example" <bob@example. org> C: To: Alice Example <alice@example. com> C: Date: Tue, 15 Jan 2008 16: 02: 43 -0500 C: Subject: Test message C: C: Hello Alice. C: This is a test message with 5 header fields and 4 lines in the message body. C: Your friend, C: Bob C: . S: 250 Ok: queued as 12345 C: QUIT S: 221 Bye {The server closes the connection} /* close channel */ 10

SMTP: final words n n n SMTP uses persistent connections SMTP requires message (header & body) to be in 7 -bit ASCII SMTP server uses CRLF to determine end of message (CRLF stands for carriage return and line feed) Comparison with HTTP: n n HTTP: pull SMTP: push n both have ASCII command/response interaction, status codes n HTTP: each object encapsulated in its own response msg SMTP: multiple objects sent in multipart msg n 11

n Distribution lists § You may need to send to a group of people § Can be summarized as distribution lists § How to map a single list name to a group of real email address: § Remote exploder § Local exploder § Can form a hierarchy: list in list 12

Two distribution lists may contain each other: we need to handle duplicated sending n Advantages of local exploder: n § It is easy to prevent mail forwarding loops § It is easy for the sender to avoid sending multiple copies to the same user § It is easier to handle billing issues 13

n Advantages of remote exploder § You can send email to a list of users whose identities are not known to you § Reduce the amount of traffic sent by sender § Improve efficiency: multiple lists can be handled by different DL maintainers 14

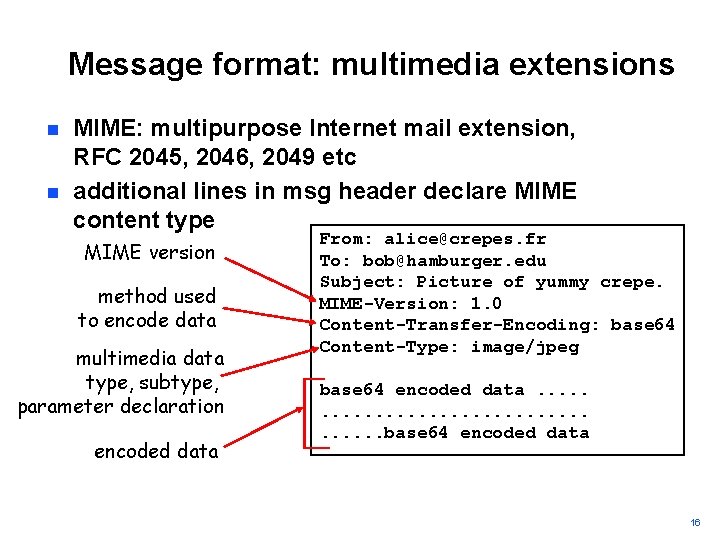
Mail message format SMTP (RFC 5321): protocol for exchanging email msgs RFC 822: Standard for the header format of ARPA Internet text messages: n header lines, e. g. , § To: § From: § Subject: different from SMTP commands! n blank line body § the “message”, ASCII characters only 15

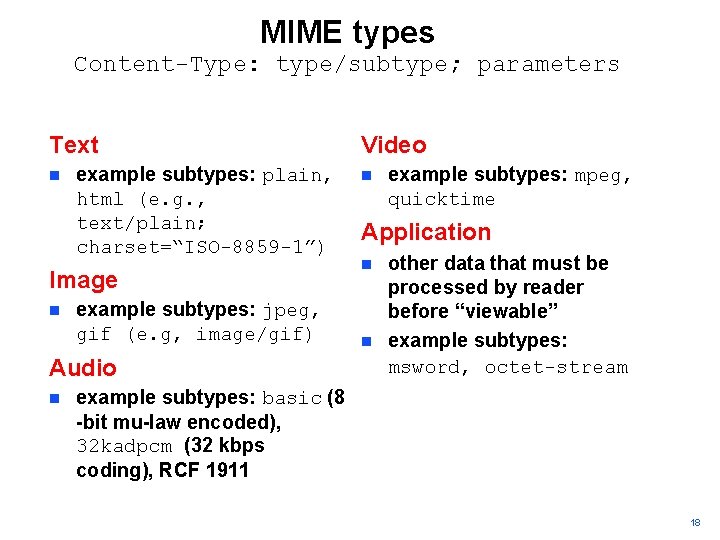
Message format: multimedia extensions n n MIME: multipurpose Internet mail extension, RFC 2045, 2046, 2049 etc additional lines in msg header declare MIME content type MIME version method used to encode data multimedia data type, subtype, parameter declaration encoded data From: alice@crepes. fr To: bob@hamburger. edu Subject: Picture of yummy crepe. MIME-Version: 1. 0 Content-Transfer-Encoding: base 64 Content-Type: image/jpeg base 64 encoded data. . . . . base 64 encoded data 16

n How is base 64 working: Turn every three bytes to four 6 -bit sequences n Each 6 -bit sequence is mapped to a printable character: A—Z, a—z, 0— 9, +, / How to handle padding n Add “=“ at the end n Number of “=“ depends on the original message n n 17

MIME types Content-Type: type/subtype; parameters Text n example subtypes: plain, html (e. g. , text/plain; charset=“ISO-8859 -1”) Image n example subtypes: jpeg, gif (e. g, image/gif) Audio n Video n example subtypes: mpeg, quicktime Application n n other data that must be processed by reader before “viewable” example subtypes: msword, octet-stream example subtypes: basic (8 -bit mu-law encoded), 32 kadpcm (32 kbps coding), RCF 1911 18

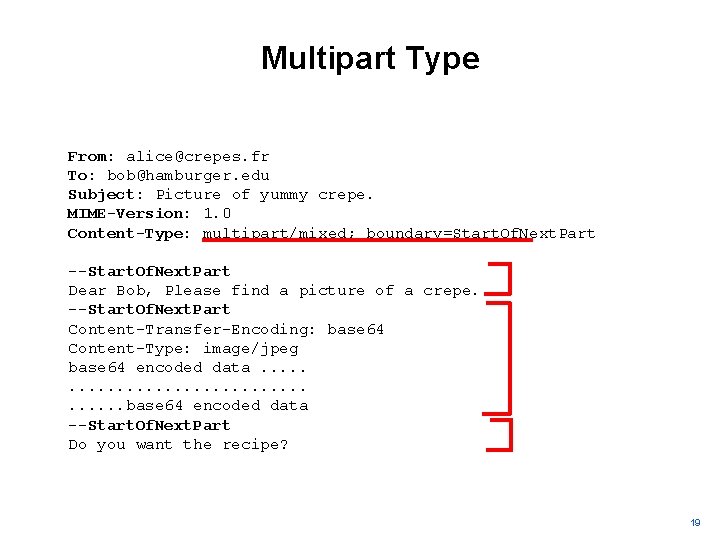
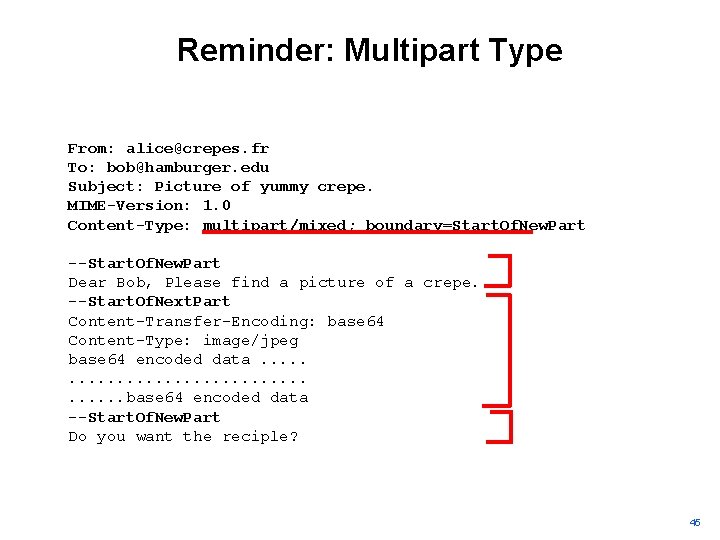
Multipart Type From: alice@crepes. fr To: bob@hamburger. edu Subject: Picture of yummy crepe. MIME-Version: 1. 0 Content-Type: multipart/mixed; boundary=Start. Of. Next. Part --Start. Of. Next. Part Dear Bob, Please find a picture of a crepe. --Start. Of. Next. Part Content-Transfer-Encoding: base 64 Content-Type: image/jpeg base 64 encoded data. . . . . base 64 encoded data --Start. Of. Next. Part Do you want the recipe? 19

n Annoying text format issues § There is no single standard for text representation § E. g. : new line, line length, high bits, etc § Intermediate server may change your email format § Problem: email ruined, integrity and signature not working § Reformat data for such issues 20

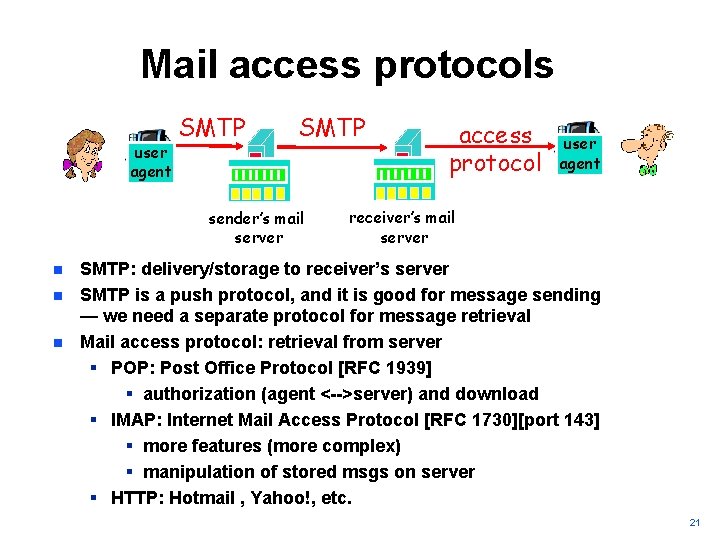
Mail access protocols user agent SMTP sender’s mail server n n n access protocol user agent receiver’s mail server SMTP: delivery/storage to receiver’s server SMTP is a push protocol, and it is good for message sending — we need a separate protocol for message retrieval Mail access protocol: retrieval from server § POP: Post Office Protocol [RFC 1939] § authorization (agent <-->server) and download § IMAP: Internet Mail Access Protocol [RFC 1730][port 143] § more features (more complex) § manipulation of stored msgs on server § HTTP: Hotmail , Yahoo!, etc. 21
![n POP 3 tcp port 110 Can work with temporary network connections view n POP 3 [tcp port 110] § Can work with temporary network connections, view](https://slidetodoc.com/presentation_image_h/219a3d0ff70e9eb194b5d9c84978a131/image-22.jpg)
n POP 3 [tcp port 110] § Can work with temporary network connections, view and manipulate email offline § Retrieve and delete from the server § POP 3 UIDL can leave a copy § Use a unique identifier to represent an email § Support encryption through SSL or TLS 22

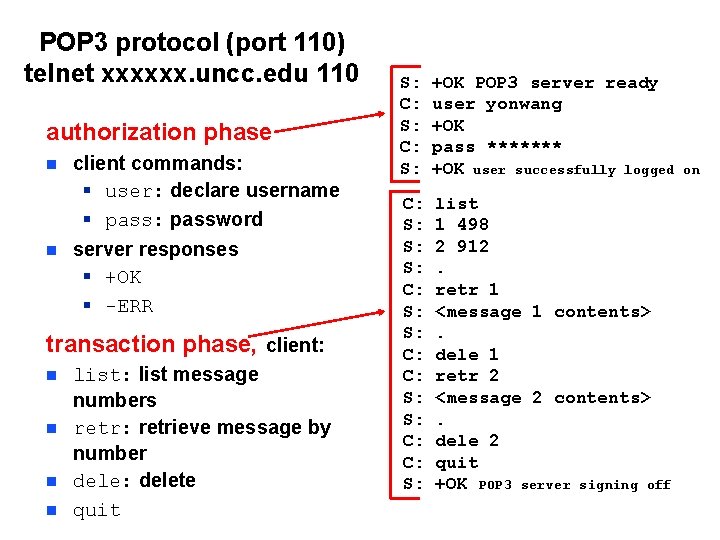
POP 3 protocol (port 110) telnet xxxxxx. uncc. edu 110 authorization phase n n client commands: § user: declare username § pass: password server responses § +OK § -ERR transaction phase, client: n n list: list message numbers retr: retrieve message by number dele: delete quit S: C: S: +OK POP 3 server ready user yonwang +OK pass ******* +OK user successfully logged C: S: S: S: C: C: S: list 1 498 2 912. retr 1 <message 1 contents>. dele 1 retr 2 <message 2 contents>. dele 2 quit +OK POP 3 server signing off on

n IMAP: Internet Message Access Protocol § § § § Support both online and offline operation Leave copy of email on server Multiple clients access the same mailbox Support encrypted login Access to MIME parts and partial fetch Message state information Create directory in your mailbox Server side search 24

n Problems of IMAP § The search algorithm on the server can consume a lot of resources § Complexity of the software 25

POP 3 and IMAP More about POP 3 n n n Previous example uses “download and delete” mode. Bob cannot re-read e-mail if he changes client “Download-and-keep”: copies of messages on different clients POP 3 is stateless across sessions Create folders and see the same view from any computer? Not possible! IMAPv 4 (port 143) n n n Keep all messages in one place: the server Allows user to organize messages in folders IMAP keeps user state across sessions: § names of folders and mappings between message IDs and folder name 26

n Some expected security features of secure email § § § § Privacy: only the receiver can read the message Authentication: authenticate the sender identity Integrity Non-repudiation Proof of submission Proof of delivery Hiding the existence of the message Anonymity: even the receiver does not know who the sender is 27

n More features of secure email § Accounting § Self-destruct § Message sequence integrity 28

Details of secure email n Establishing keys § There are many possibilities of keys: sender, receiver, MTA, distribution list exploder, etc § Public key approach § Sender can get receiver’s public key by § Out-of-band mechanism § Through PKI § Piggybacking of certificates § Secret key approach § Through KDC or tickets 29

n Confidentiality § Many sources to violate email confidentiality: eavesdropper, MTA, company network administrator § End-to-end privacy § It is not efficient to use public key to encrypt the whole message § It is not efficient when you have multiple receivers § Solution: use a symmetric key to encrypt message, and use public key to encrypt the symmetric key 30

n Privacy with the distribution list exploder § Remote DLE: the sender only needs to share a key with the DLE § Local DLE: establish key with every receiver in the list 31

n Authenticating sender § Signing the message digest with sender’s private key § Encrypt the digest with pair wise key § Source authentication with distribution lists § It is easy if we use digital signature § If we are using secret key, DLE will attach its authentication information 32

n Message integrity § Most of time it is integrated with source authentication § Integrity without source authentication § Ransom § The problem when you sign a hash result § How is the hash result calculated (attack with the signatures) 33

n Non-repudiation § With public keys § With the digital signature § Deniability based on public key technology § § Alice generates a symmetric key E pub-B ( Sign-A (key) ) Use this key to encrypt the message Bob can prove that Alice generates the key, but not Alice sends that message § Non-repudiation with secret keys § through notary (trusted third party) 34

n Proof of submission § The sending MTA provides a signed digest of the email n Proof of delivery § Receiver signs a receipt n A famous problem in cryptography § Simultaneous contract signing 35

n Anonymity § § Through a proxy Onion routing issues Anonymous email service: craigslist Anonymous IETF mailing list 36

Possible attacks n Spoofing (unbelievably easy!) § a third party may impersonate Alice and send a fake/modified message to Bob n Eavesdropping § a party sitting between Alice’s UA and Bob’s mail server may peep communications between them n Replay § a party sitting between Alice and Bob may re-send to Bob an old message from Alice n n Attacks on mail access protocols such as POP 3, IMAP, etc Other attacks such as Do. S Traffic analysis Last one: should Bob trust his mail server? Or in another word: do you trust the postman who delivers a letter to you? 37

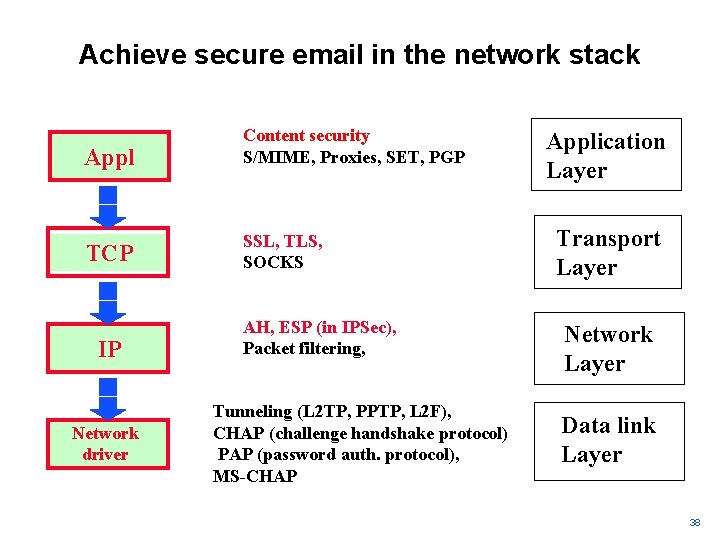
Achieve secure email in the network stack Appl Content security S/MIME, Proxies, SET, PGP TCP SSL, TLS, SOCKS IP Network driver AH, ESP (in IPSec), Packet filtering, Tunneling (L 2 TP, PPTP, L 2 F), CHAP (challenge handshake protocol) PAP (password auth. protocol), MS-CHAP Application Layer Transport Layer Network Layer Data link Layer 38

Use electronic mail securely n Preventing spoofing and replay § Digital signature with one-way hash § Timestamps etc. n Preventing eavesdropping § Encryption (transport layer or application layer) n Preventing attacks on mail access protocols § SSL (open. SSL) n Preventing other attacks: general network security problems (Do. S on a mail server) 39

Use Email securely n Content layer security: § § Transparent on the underlying layer PEM PGP S/MIME 40

Privacy Enhanced Mail (PEM) Attempt to add security to SMTP n Text only: MIME didn’t exist yet n Attempt to build a CA hierarchy along X. 500 lines n § Hierarchy with a single root !! n Solved the data formatting problem with base 64 encoding § Encode 3 binary bytes as 4 NVT ASCII characters § The same encoding was later used in PGP 2. X, mime. . . 41

n PEM certificate hierarchy § Want to use a centralized root § Three types of certificate authorities § High assurance § Discretionary Assurance § No Assurance 42

PGP By Phil Zimmermann n Check out http: //www. pgp. com or http: //web. mit. edu/network/pgp. html Available for Windows/Linux/Macintosh n Getting the PGP and install it on your computer n Crypto is useful only if it is USED!! n 43

S/MIME n Who will win? § PGP for personal email security § S/MIME for commercial and organization use Standards page: http: //www. ietf. org/html. charters/smim e-charter. html n Main RFCs: 2630, 2632, 2633 n 44

Reminder: Multipart Type From: alice@crepes. fr To: bob@hamburger. edu Subject: Picture of yummy crepe. MIME-Version: 1. 0 Content-Type: multipart/mixed; boundary=Start. Of. New. Part --Start. Of. New. Part Dear Bob, Please find a picture of a crepe. --Start. Of. Next. Part Content-Transfer-Encoding: base 64 Content-Type: image/jpeg base 64 encoded data. . . . . base 64 encoded data --Start. Of. New. Part Do you want the reciple? 45

S/MIME n n Similar to PGP, offers signature and encryption functions. It cryptographically protects MIME entity Based on CMS (cryptographic message syntax) § Encapsulation syntax for data protection 46

Protocols Content encryption algorithm: 3 DES (DES EDE 3 CBC), RC 2/40 (more algorithms are being added) n Key encryption algorithm: Diffiehellman n Message digest algorithm: SHA-1, MD 5 n Signature algorithm: DSA, RSA n 47

User Agent n S/MIME user agents should handle the following tasks: § Key generation § Registration § Certificate storage and retrieval including certificate management 48

Applications Secure e-mail n EDI (Electronic Data Interchange) n Online Services n Healthcare applications n Internet push products n Indeed, used for any kind of data content protection n 49

Adopted in: Microsoft Exchange n Lotus Notes n Novell Groupwise n Netscape Communicator n Eudora n etc. . n 50