Securing Data with Strong Encryption and Access Controls






- Slides: 17

Securing Data with Strong Encryption and Access Controls Blair Semple Storage Security Evangelist Network Appliance Sept 12, 2007

Agenda 4 Understanding the Risks to Stored Data 4 Methodologies for Securing Data 4 Emerging Industry Standards 4 How Encryption and Access Controls Reduce the Risk

Storage Trends - The Scale of Exposure Single backup tape = 1 Terabyte = 20 million lbs. of paper = Every credit card in world

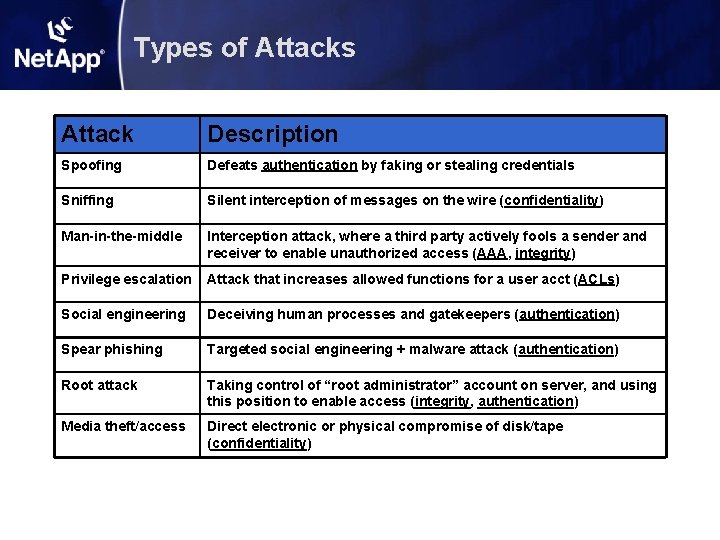
Types of Attacks Attack Description Spoofing Defeats authentication by faking or stealing credentials Sniffing Silent interception of messages on the wire (confidentiality) Man-in-the-middle Interception attack, where a third party actively fools a sender and receiver to enable unauthorized access (AAA, integrity) Privilege escalation Attack that increases allowed functions for a user acct (ACLs) Social engineering Deceiving human processes and gatekeepers (authentication) Spear phishing Targeted social engineering + malware attack (authentication) Root attack Taking control of “root administrator” account on server, and using this position to enable access (integrity, authentication) Media theft/access Direct electronic or physical compromise of disk/tape (confidentiality)

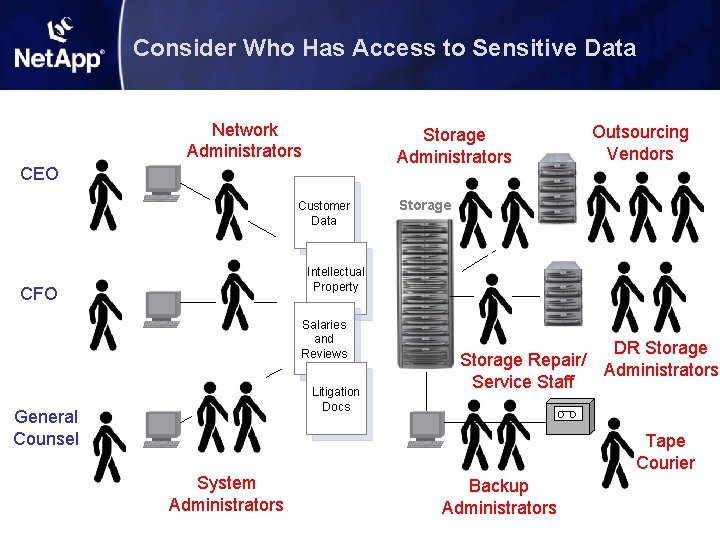
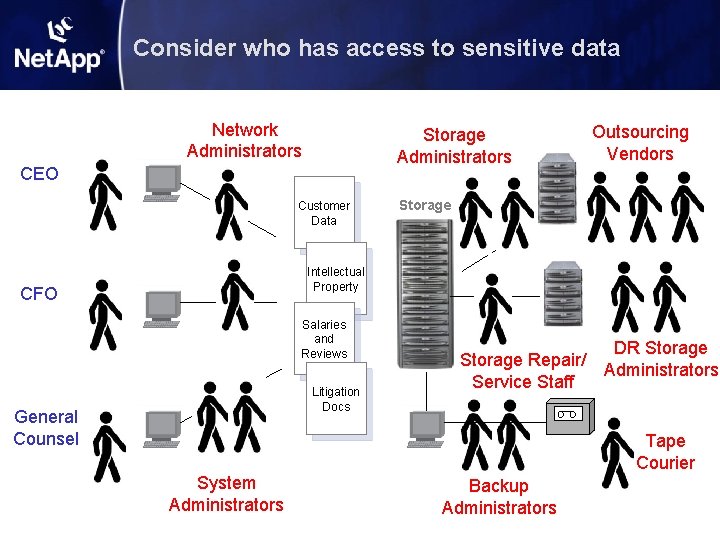
Consider Who Has Access to Sensitive Data Network Administrators Storage Administrators CEO Customer Data Outsourcing Vendors Storage Intellectual Property CFO Salaries and Reviews Litigation Docs General Counsel Storage Repair/ Service Staff DR Storage Administrators Tape Courier System Administrators Backup Administrators

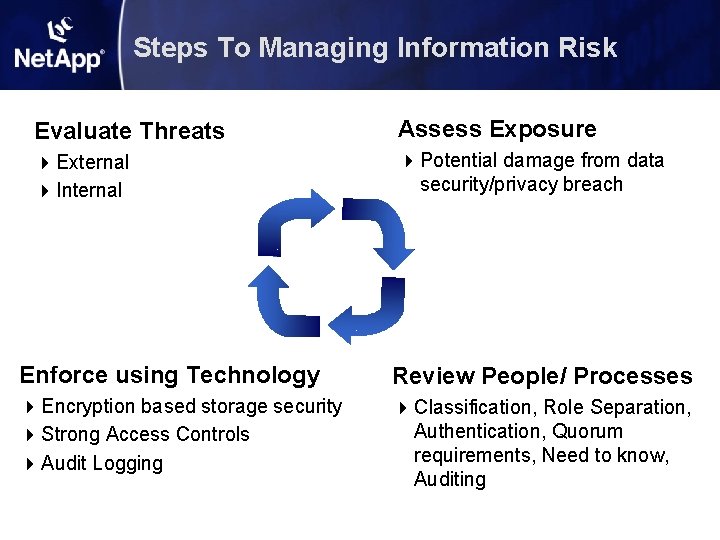
Steps To Managing Information Risk Evaluate Threats Assess Exposure 4 External 4 Internal 4 Potential damage from data security/privacy breach Enforce using Technology Review People/ Processes 4 Encryption based storage security 4 Strong Access Controls 4 Audit Logging 4 Classification, Role Separation, Authentication, Quorum requirements, Need to know, Auditing

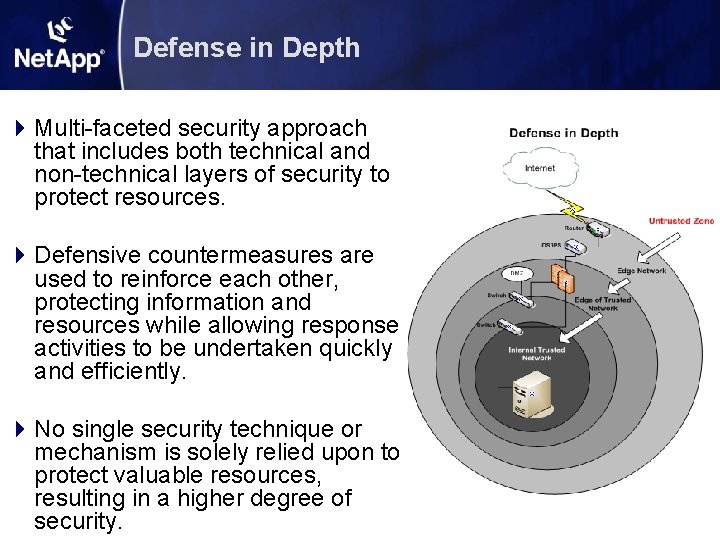
Defense in Depth 4 Multi-faceted security approach that includes both technical and non-technical layers of security to protect resources. 4 Defensive countermeasures are used to reinforce each other, protecting information and resources while allowing response activities to be undertaken quickly and efficiently. 4 No single security technique or mechanism is solely relied upon to protect valuable resources, resulting in a higher degree of security.

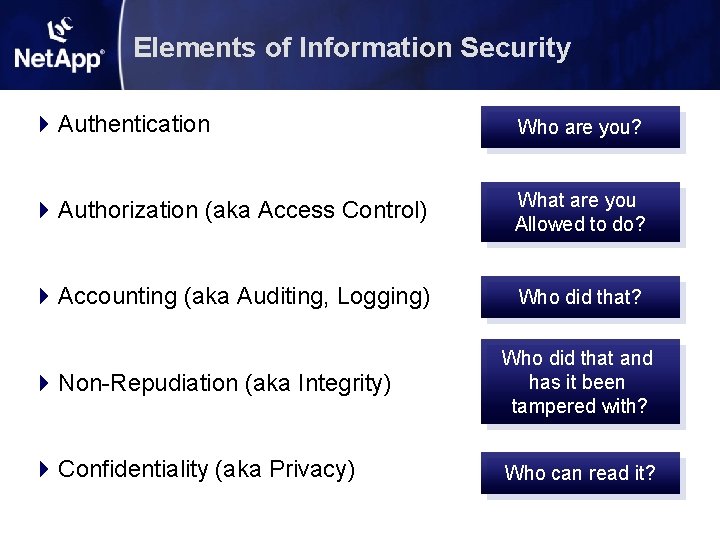
Elements of Information Security 4 Authentication Who are you? 4 Authorization (aka Access Control) What are you Allowed to do? 4 Accounting (aka Auditing, Logging) Who did that? 4 Non-Repudiation (aka Integrity) Who did that and has it been tampered with? 4 Confidentiality (aka Privacy) Who can read it?

Storage Security with Encryption 4 Dramatically simplifies security planning 4 Ensure only authorized personnel access assets 4 Allow ‘maintenance’ without risking exposure 4 Audit and track access to valuable assets 4 Copies automatically protected 4 Loss of physical custody no longer a threat

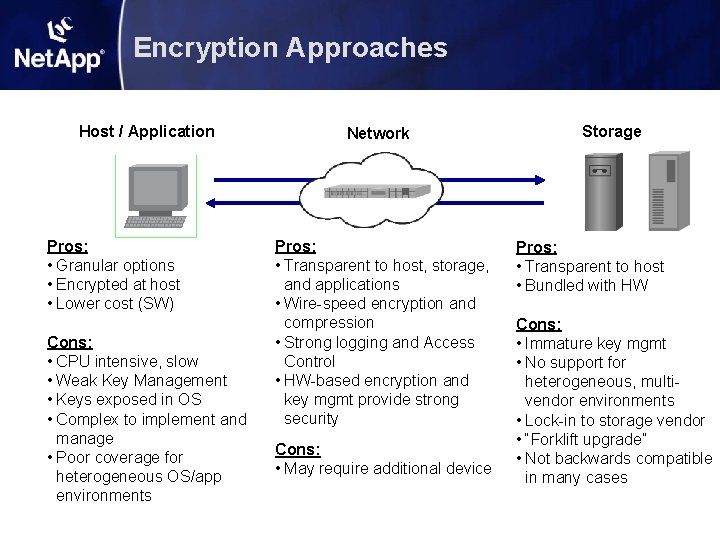
Encryption Approaches Host / Application Pros: • Granular options • Encrypted at host • Lower cost (SW) Cons: • CPU intensive, slow • Weak Key Management • Keys exposed in OS • Complex to implement and manage • Poor coverage for heterogeneous OS/app environments Network Pros: • Transparent to host, storage, and applications • Wire-speed encryption and compression • Strong logging and Access Control • HW-based encryption and key mgmt provide strong security Cons: • May require additional device Storage Pros: • Transparent to host • Bundled with HW Cons: • Immature key mgmt • No support for heterogeneous, multivendor environments • Lock-in to storage vendor • “Forklift upgrade” • Not backwards compatible in many cases

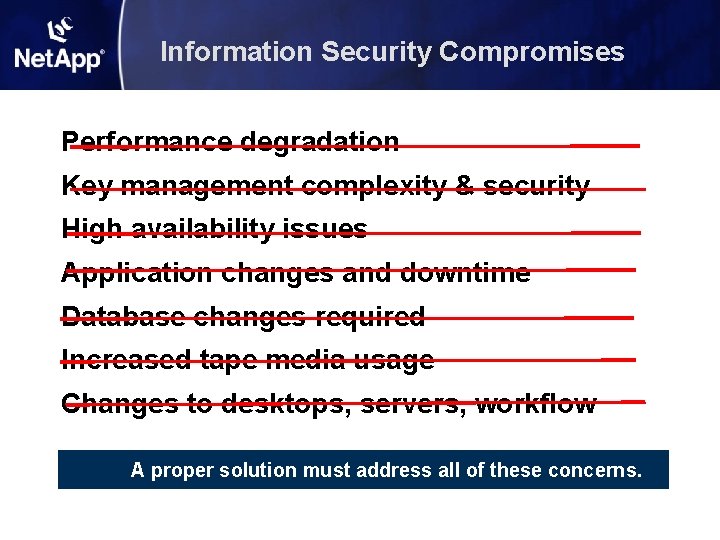
Information Security Compromises Performance degradation Key management complexity & security High availability issues Application changes and downtime Database changes required Increased tape media usage Changes to desktops, servers, workflow A proper solution must address all of these concerns.

Emerging Standards for Storage Security 4 The IEEE Security in Storage workgroup (SISWG) is working on standards for encrypted storage media. 4 Members of the groups include: Brocade Cisco EMC Hifn HP IBM Optica PGP Seagate Stanford Net. App/Decru Hitachi Neo. Scale Quantum SUN 4 P 1619 (disk) – Draft 17 in Ballot, with due date of 9 Aug 4 P 1619. 1 (tape) – Draft 21 expected to enter Ballot in mid-Aug 4 P 1619. 2 (wide block for disk) – Drafts in progress 4 P 1619. 3 (key management) – Draft 1 being worked

IEEE P 1619. 3 - Key Management Infrastructure for Cryptographic Protection of Stored Data 4 HP and Net. App/Decru have jointly submitted a draft proposal for key APIs (largely based on our Open. Key standard) to the IEEE P 1619. 3 committee. 4 This draft was accepted unanimously. 4 Decru will continue to work with HP, and other storage vendors, to ensure interoperability, as well as continue working toward an industry standard.

Value of Information Security 4 As back-end IT complexity increases (e. g. replication, networking, sharing…), this dramatically increases the “attack surface” 4 Data encryption reduces attack surface: everything behind the encryption is opaque 4 By narrowing the number of people and devices that can see data, encryption can simplify overall system security 4 Separates ability to manage data from ability to read it 4 Encryption and AAA (Authentication, Authorization, Auditing) can be combined in a single device, or can be deployed in adjacent layers (e. g. storage and application layers)

Consider who has access to sensitive data Network Administrators Storage Administrators CEO Customer Data Outsourcing Vendors Storage Intellectual Property CFO Salaries and Reviews Litigation Docs General Counsel Storage Repair/ Service Staff DR Storage Administrators Tape Courier System Administrators Backup Administrators

About Network Appliance

Delivering Customer Success $3. 0 B FY 07: $2. 8 Billion 4 Worldwide, enterprise customers 4 Fastest growing storage company – Outpacing the industry by 3 x 4 Data Center proven solutions portfolio $2. 0 B 4 Industry-leading partners 4 Comprehensive professional services 4 Global support $1 B • 6500+ Employees • Fortune 1000 • Distributed in 138+ countries • S&P 500 • 94, 000+ installed systems • NASDAQ 100