Secure Works Adapting Incident Response to Meet the













- Slides: 23

Secure. Works Adapting Incident Response to Meet the Threat Jeff Schilling Director, Global Incident Response and Digital Forensics

Agenda • • • Why change your approach? Do you really know your environment? Do You really know/understand your threat? Where to focus your efforts to respond? Measuring success

My Press Box View My view as the Director of the Army’s Global Network Security Team My view as the Director of the Dell Secure. Works Incident Response Practice

The Dell Secure. Works Incident Response Practice • 300+ projects last year Ø 42% of our engagements were with Medium-sized business Ø 58% were large enterprise customers Ø 70% of our engagements were active Incident Response Ø 30% were proactive engagements Ø 20% of our projects involved Advance Persistent Threat (Targeted Threat) • Our observations from 2012 engagements: Ø End users still the primary targets (51% of the time) Ø Servers and applications running second (39% of the time) Ø 20% of our engagements involved insider threat activity

Do I need to change my approach?

Getting to “yes” • • Do you rarely see the same activity on your networks with the same success? Do you conduct trend analysis of your security incidents? Have you analyzed the things you can control and the things you can’t? ü People ü Processes ü Technology For the things you can’t control, have you calculated the risks or outcomes? Have you insured or transferred that risk? Do you make adjustments to your security controls based on trends? Do you have a plan or playbook to address your most common Incidents? Do you rehearse and update these plans?

Do you really know your environment?

Which picture best describes your network? OR • • • Do you have an updated/accurate network diagram? Are you a part of the change management process so you know when it changes? Have you studied your network flow to know what ports and protocols to accept and ones to deny? Do you validate with Pen Tests, Vulnerability Scans, Netflow Monitoring? Do you have defined network boundaries with the Internet? Do you Leverage Active Directory to assign risk and controls to Organizational Units? Is “white listing” embraced in your organization? Do you have a standard, secure image/baseline for hosts and servers? Do you centralize your event log monitoring? Do you limit workstation to workstation communication?

Do you really know your enemy?

Categories of threat May be some overlap in APT and Insider threat detection Commodity Threat • • Phishing with Dynamite Automated control for scale Can be defended with good Signature based controls Buys trade craft Can be sophisticated and polymorphic Favorite vectors ü Server compromises ü Non-targeted phishing ü Web drive bys Smash and grab • • Playing chess Human controlled (just for you) Custom trade craft Favorite vectors ü Highly targeted phishing ü Water holing web drive bys ü Some server compromises Highly targeted efforts Attempts to cover their tracks Will compromise partners to get to you Goal is to log on, become an insider • • • Fly on the wall Hardest to detect, tries to hide in normal activity Usually has elevated privileges In most cases, assumes not being monitored Rarely uses tradecraft: when they do, normally crawlers Usually has access to data that does not pertain to their job, that is what they take May use “close access” techniques Attempts to cover their tracks Managers/HR usually not surprised when insider is caught

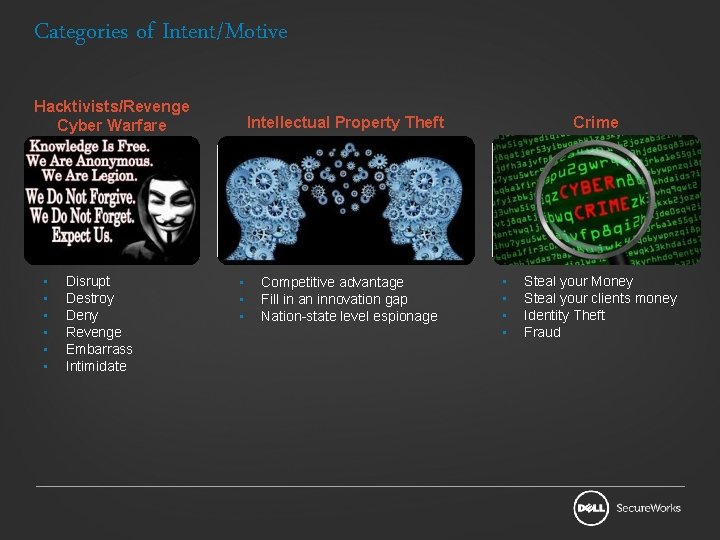
Categories of Intent/Motive Hacktivists/Revenge Cyber Warfare • • • Disrupt Destroy Deny Revenge Embarrass Intimidate Intellectual Property Theft • • • Competitive advantage Fill in an innovation gap Nation-state level espionage Crime • • Steal your Money Steal your clients money Identity Theft Fraud

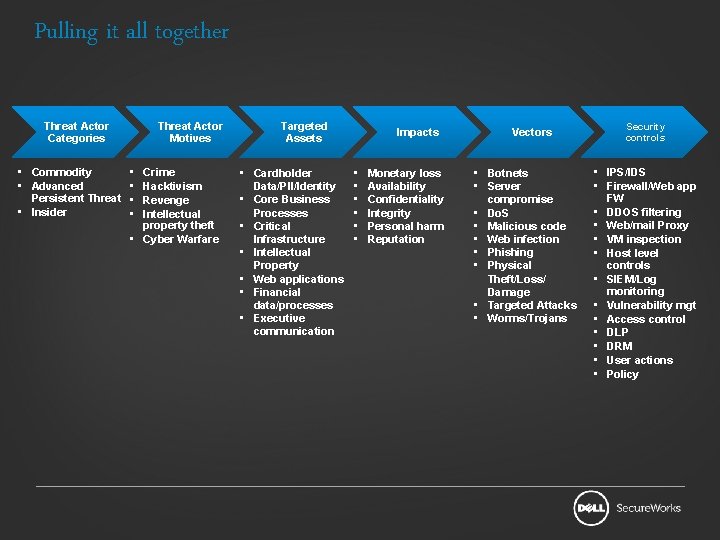
Pulling it all together Threat Actor Categories • Commodity • Advanced Persistent Threat • Insider Threat Actor Motives • • Crime Hacktivism Revenge Intellectual property theft • Cyber Warfare Targeted Assets • Cardholder Data/PII/Identity • Core Business Processes • Critical Infrastructure • Intellectual Property • Web applications • Financial data/processes • Executive communication Impacts • • • Monetary loss Availability Confidentiality Integrity Personal harm Reputation Vectors • Botnets • Server compromise • Do. S • Malicious code • Web infection • Phishing • Physical Theft/Loss/ Damage • Targeted Attacks • Worms/Trojans Security controls • IPS/IDS • Firewall/Web app FW • DDOS filtering • Web/mail Proxy • VM inspection • Host level controls • SIEM/Log monitoring • Vulnerability mgt • Access control • DLP • DRM • User actions • Policy

What should an IR plan look like? • Base document (Policy and Guidelines, does not change very often) – Roles and responsibilities – Description of the overall process – Identification of Incident Types – Work flows – Identification of third party providers • Playbooks/Appendix/Run Books (Procedures, constantly updated) – One for each Incident Type › Criteria for declaring an incident › Checklist driven actions › Point of Contact Lists – Key players on the Security team – Key players on the IT staff (if separate from the Security team) – Key decision makers outside of Security and IT – Third party providers (ISP, outside consulting, etc)

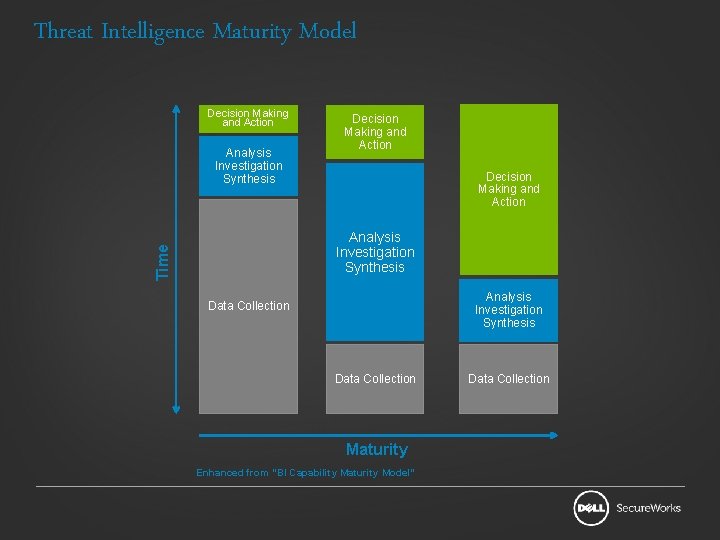
Threat Intelligence Maturity Model Decision Making and Action Analysis Investigation Synthesis Decision Making and Action Time Analysis Investigation Synthesis Data Collection Maturity Enhanced from “BI Capability Maturity Model” Data Collection

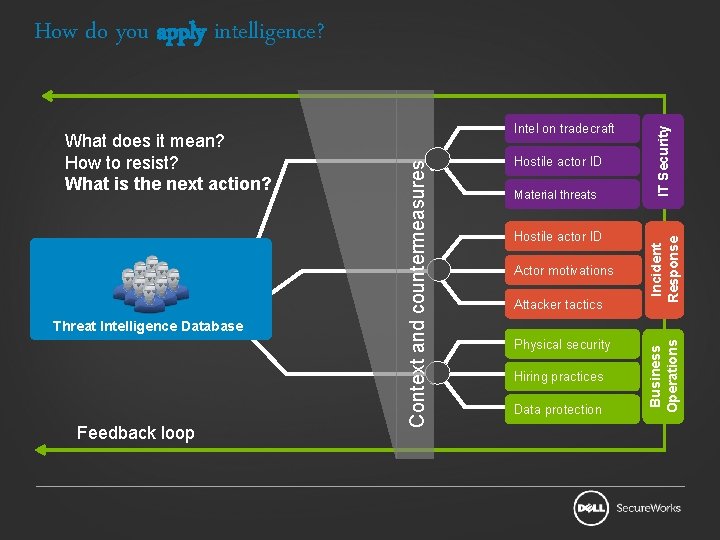
Feedback loop Material threats Hostile actor ID Actor motivations Attacker tactics Physical security Hiring practices Data protection Incident Response Hostile actor ID Business Operations Threat Intelligence Database Intel on tradecraft Context and countermeasures What does it mean? How to resist? What is the next action? IT Security How do you apply intelligence?

Where to focus your Response Efforts?

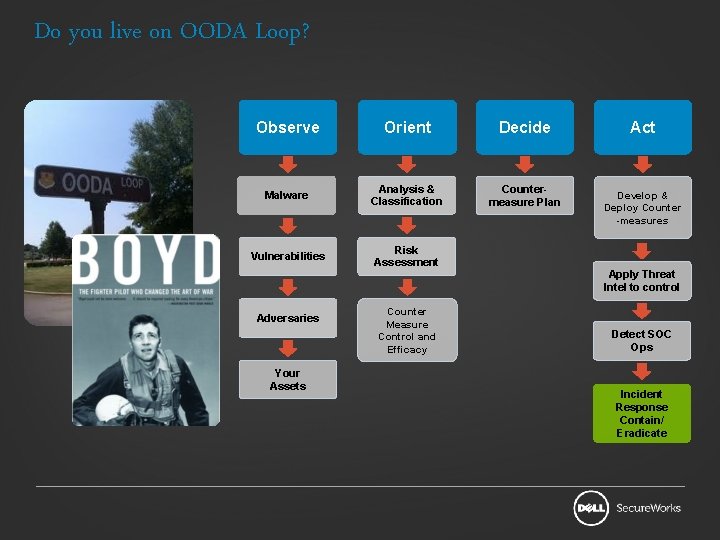
Do you live on OODA Loop? Observe Orient Decide Malware Analysis & Classification Countermeasure Plan Vulnerabilities Risk Assessment Adversaries Your Assets Counter Measure Control and Efficacy Act Develop & Deploy Counter -measures Apply Threat Intel to control Detect SOC Ops Incident Response Contain/ Eradicate

The “Broken Windows” approach Questions Answers • • • Where is my most important data? Where are most of my incidents happening? Where am I most vulnerable? What is (are) the worst possible thing(s) that could happen? Can I detect where I am most vulnerable? Can contain where I am most vulnerable? Can I see the insider threat? • • • Identify your “broken windows” Establish network visibility Segment to protect critical assets, create security zones Layered defensive strategy ü Intelligence informed SIEM ü Network detection/prevention ü Host level detection/prevention ü Virtual machine detonation Get control of your elevated privileges, if you can Protect and leverage your Active Directory structure Whitelist your servers, protocols and ports Focus on SMTP and Web traffic Talk to managers and HR about high risk employees with elevated privileges

How do you measure success?

Success, Failure and False metrics Indication of Successful Trends Indications of Failing Trends • Increase of recurring incidents • Increased in dwell time • Increase # of incidents reported by the user v. detected by SOC • Increased number of root level and domain compromise • Increase number of compromised servers/web applications • Increase in the number of incidents involving CVE’s • Increase of business impact of Incident • Increase of incidents closed where root cause is indeterminate ! • Decrease in time between detection and containment • Decrease in the number of successful commodity infections • Decrease in number of incidents that spread to multiple host • Increase in the number of APT and Insider threat detection • Decrease in third party reporting of incidents (FBI, USSS, partners) • Reduction in successful Phishing False Metrics • Increase or decrease in number of incidents • Increase or decrease in number of detections • Investment on security technology

Conclusion • • Analyze your environment; Know your strengths and weaknesses Ensure you understand the threat’s capabilities, intent and vectors Focus your response on your “broken windows” Ensure you are achieving success and not reinforcing failure in your Incident Response processes

Resources • Dell Secure. Works Incident Response http: //go. secureworks. com/incident-response • SANS Incident Response Training http: //www. sans. org/course/advanced-computer-forensic-analysis-incident-response • White Paper - Accelerating Incident Response: How Integrated Services Reduce Risk and the Impact of a Security Breach • http: //www. secureworks. com/resources/articles/featured_articles/accelerating-incident-response-reducing-risk-and-impact • NIST Computer Security Incident Handling Guide http: //csrc. nist. gov/publications/nistpubs/800 -61 rev 2/SP 800 -61 rev 2. pdf If you suspect a security breach, contact the Dell Secure. Works Incident Response team at 877 -884 -1110.

Questions?
 Until we meet again prayer
Until we meet again prayer Incident objectives that drive incident operations
Incident objectives that drive incident operations Street works book
Street works book Personal narrative episode 4
Personal narrative episode 4 The watchman style of policing emphasizes
The watchman style of policing emphasizes Incident response technologies
Incident response technologies Rsa secops
Rsa secops Incident response playbooks
Incident response playbooks Incident response technologies
Incident response technologies Cscattt methane
Cscattt methane Principles of incident response and disaster recovery
Principles of incident response and disaster recovery Splunk incident management
Splunk incident management Osquery
Osquery Principles of incident response and disaster recovery
Principles of incident response and disaster recovery Ioc incident response
Ioc incident response Odot incident response
Odot incident response Gem incident management
Gem incident management Xforce iris
Xforce iris Incident response trailer
Incident response trailer How well are we adapting
How well are we adapting Adopting materials
Adopting materials The process of adapting borrowed cultural traits.
The process of adapting borrowed cultural traits. Adapting curriculum to bridge equity gaps
Adapting curriculum to bridge equity gaps 'adapting the message to your audience
'adapting the message to your audience