Secure Traffic Lights Replay Attack Detection for Modelbased

Secure Traffic Lights: Replay Attack Detection for Model-based Smart Traffic Controllers Pratham Oza, Mahsa Foruhandeh, Ryan Gerdes and Thidapat Chantem {prathamo, mfhd, rgerdes, tchantem}@vt. edu Electrical & Computer Engineering, Virginia Tech Aug 05, 2020
CONTENTS § § § Problem Overview System Model Threat Model Evaluation and Countermeasures Conclusion

01 Problem Overview
Problem Overview • Traffic lights are ubiquitous and critical infrastructure • Poorly managed traffic lights with no (or partial, historic) traffic information lead to congestions • Io. T framework integrates sensors to make traffic control ”smart” • Extract real-time traffic characteristics • Control techniques and algorithms that are adaptive to change in traffic Issue: • Most of these techniques were built on top of legacy traffic infrastructure • Systems and upgrades lack security by design Contributions: • Perform replay attack on the inductive loop sensors used to measure traffic flow • Explore the shortcomings of the existing model-based attack detectors • Validate the performance of our attack using VISSIM – a microscopic traffic simulator • Propose threshold-based countermeasures to detect such attacks 04 / PROBLEM OVERVIEW

02 System Model
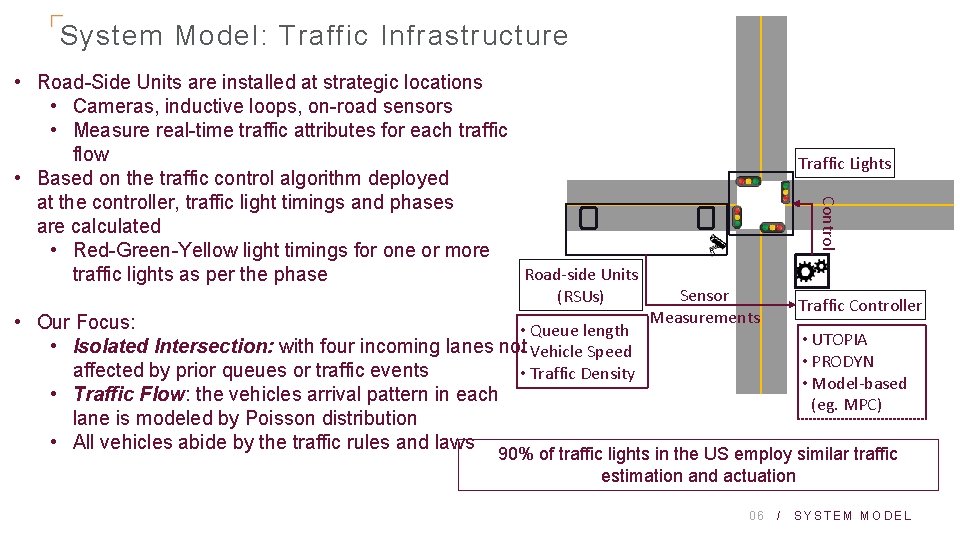
System Model: Traffic Infrastructure (RSUs) • Our Focus: • Queue length • Isolated Intersection: with four incoming lanes not • Vehicle Speed affected by prior queues or traffic events • Traffic Density • Traffic Flow: the vehicles arrival pattern in each lane is modeled by Poisson distribution • All vehicles abide by the traffic rules and laws Traffic Lights Control • Road-Side Units are installed at strategic locations • Cameras, inductive loops, on-road sensors • Measure real-time traffic attributes for each traffic flow • Based on the traffic control algorithm deployed at the controller, traffic light timings and phases are calculated • Red-Green-Yellow light timings for one or more Road-side Units traffic lights as per the phase Sensor Measurements Traffic Controller • UTOPIA • PRODYN • Model-based (eg. MPC) 90% of traffic lights in the US employ similar traffic estimation and actuation 06 / SYSTEM MODEL
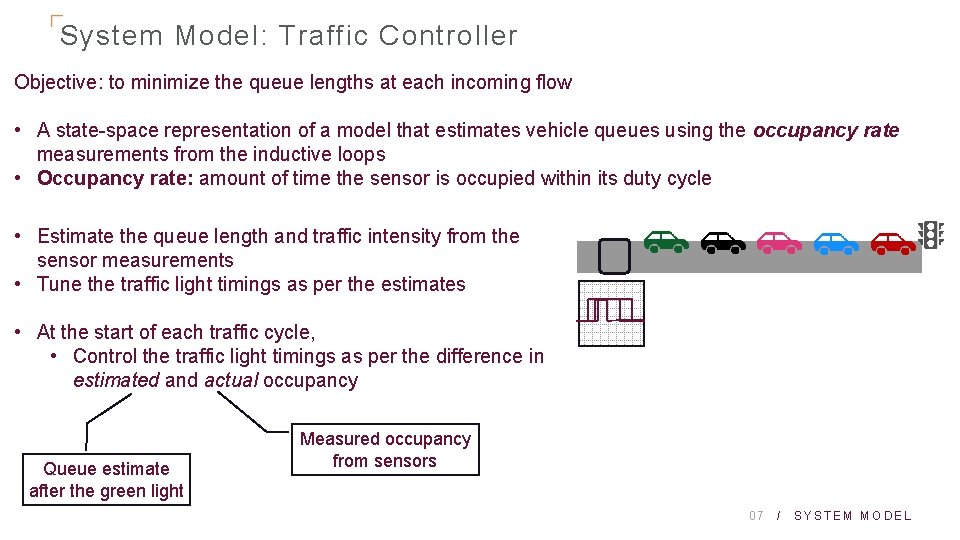
System Model: Traffic Controller Objective: to minimize the queue lengths at each incoming flow • A state-space representation of a model that estimates vehicle queues using the occupancy rate measurements from the inductive loops • Occupancy rate: amount of time the sensor is occupied within its duty cycle • Estimate the queue length and traffic intensity from the sensor measurements • Tune the traffic light timings as per the estimates • At the start of each traffic cycle, • Control the traffic light timings as per the difference in estimated and actual occupancy Queue estimate after the green light Measured occupancy from sensors 07 / SYSTEM MODEL
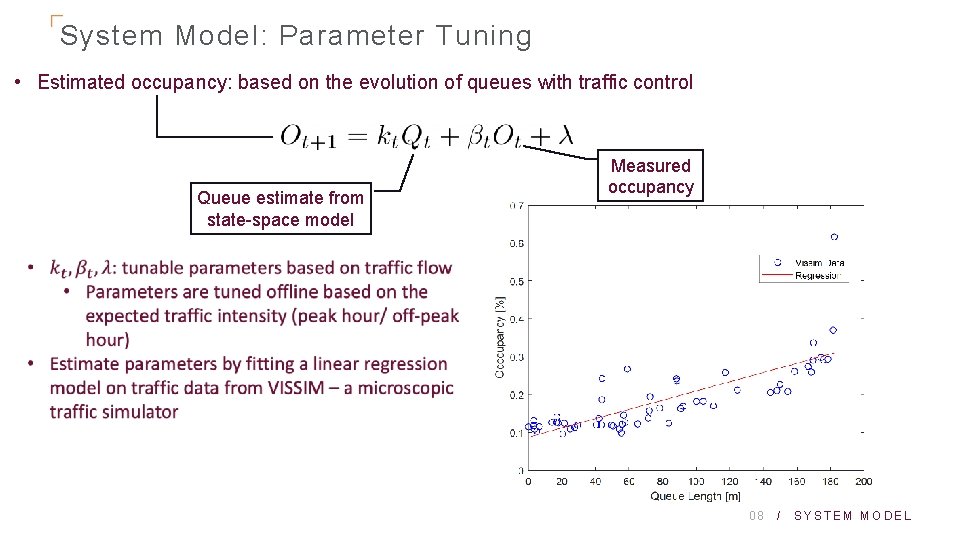
System Model: Parameter Tuning • Estimated occupancy: based on the evolution of queues with traffic control Queue estimate from state-space model Measured occupancy 08 / SYSTEM MODEL
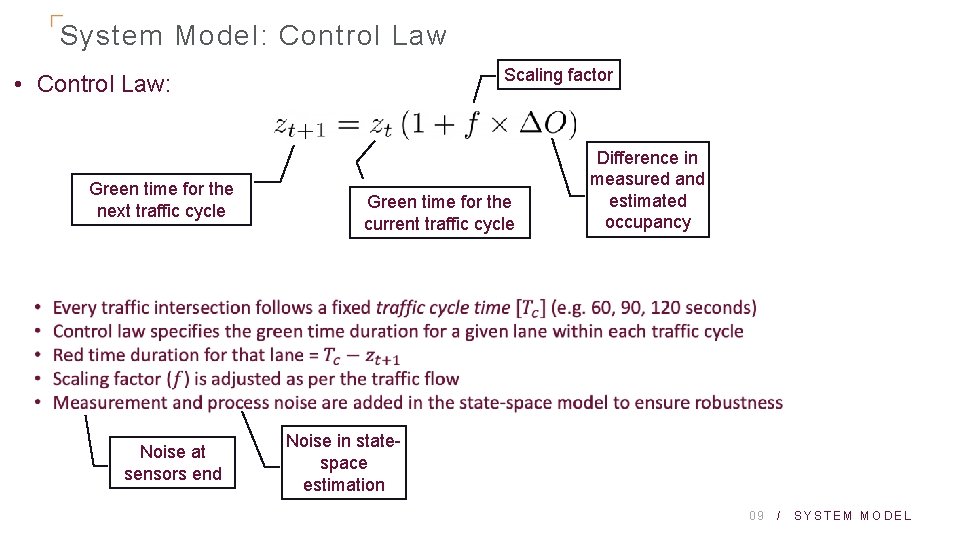
System Model: Control Law Scaling factor • Control Law: Green time for the next traffic cycle Noise at sensors end Green time for the current traffic cycle Difference in measured and estimated occupancy Noise in statespace estimation 09 / SYSTEM MODEL

03 Attack Model
Attack Model • Objective: disrupt the transportation network by maximizing the queue length • Foothold: the output of the inductive loop detector • Methodology: decrease the efficiency of traffic lights by manipulating the traffic controller • Hardware Requirement: an off-the-shelf microcontroller to read the sensor values and/or an inexpensive transmitter antenna to send out the falsified data • Capabilities: • affect the perceived occupancy rate • record and transmit the output of the sensor • wait until the proper conditions are present • cannot tamper with the sensor data (can only replay) 11 / SYSTEM MODEL
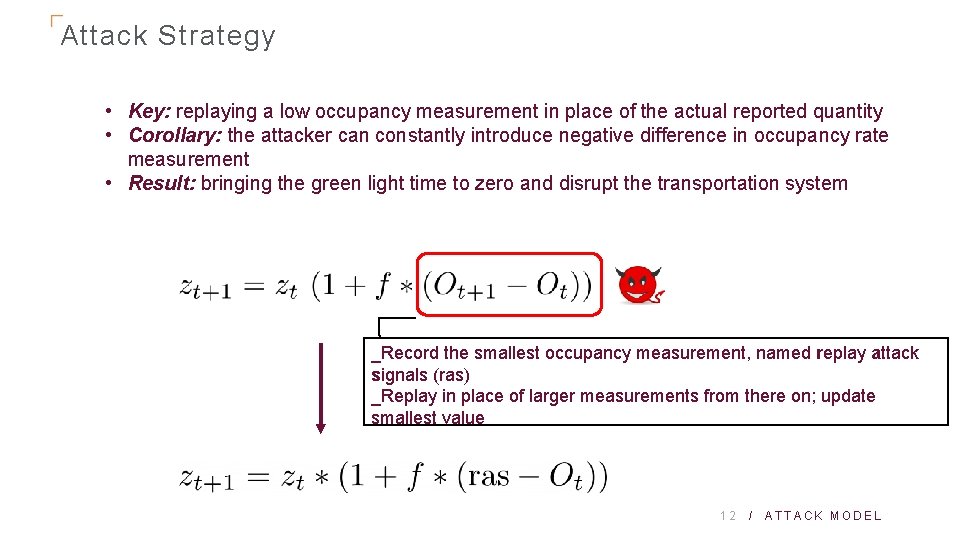
Attack Strategy • Key: replaying a low occupancy measurement in place of the actual reported quantity • Corollary: the attacker can constantly introduce negative difference in occupancy rate measurement • Result: bringing the green light time to zero and disrupt the transportation system _Record the smallest occupancy measurement, named replay attack signals (ras) _Replay in place of larger measurements from there on; update smallest value 12 / ATTACK MODEL

04 Evaluation and Countermeasures
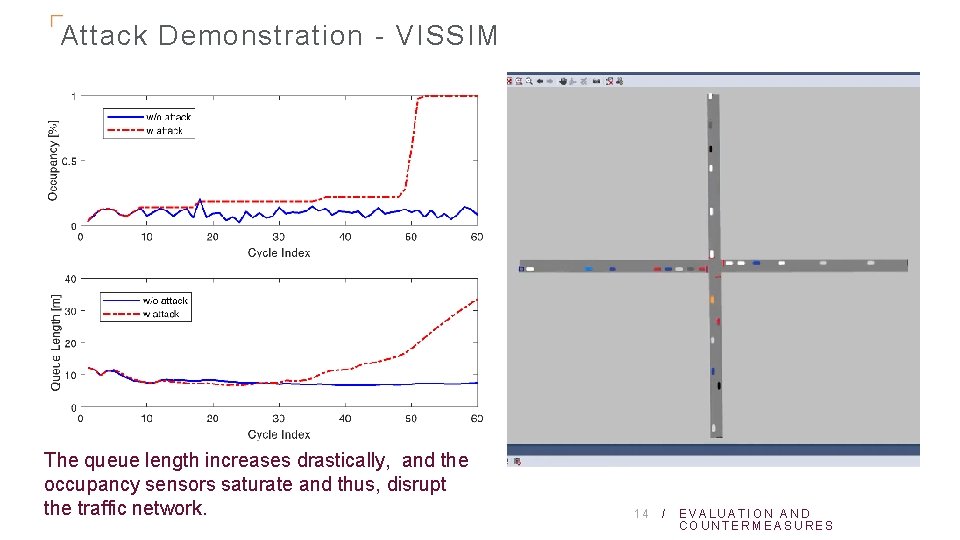
Attack Demonstration - VISSIM The queue length increases drastically, and the occupancy sensors saturate and thus, disrupt the traffic network. 14 / EVALUATION AND COUNTERMEASURES
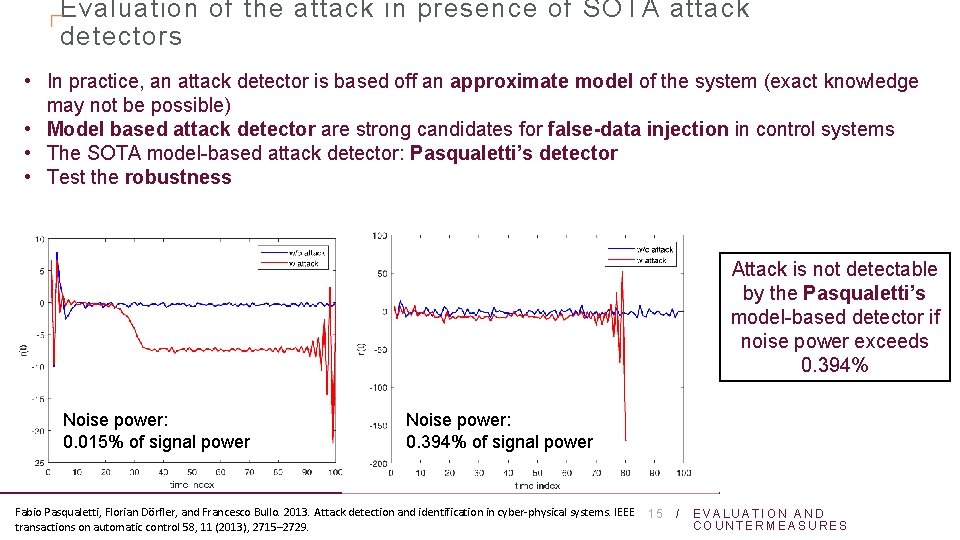
Evaluation of the attack in presence of SOTA attack detectors • In practice, an attack detector is based off an approximate model of the system (exact knowledge may not be possible) • Model based attack detector are strong candidates for false-data injection in control systems • The SOTA model-based attack detector: Pasqualetti’s detector • Test the robustness Attack is not detectable by the Pasqualetti’s model-based detector if noise power exceeds 0. 394% Noise power: 0. 015% of signal power Noise power: 0. 394% of signal power Fabio Pasqualetti, Florian Dörfler, and Francesco Bullo. 2013. Attack detection and identification in cyber-physical systems. IEEE transactions on automatic control 58, 11 (2013), 2715– 2729. 15 / EVALUATION AND COUNTERMEASURES
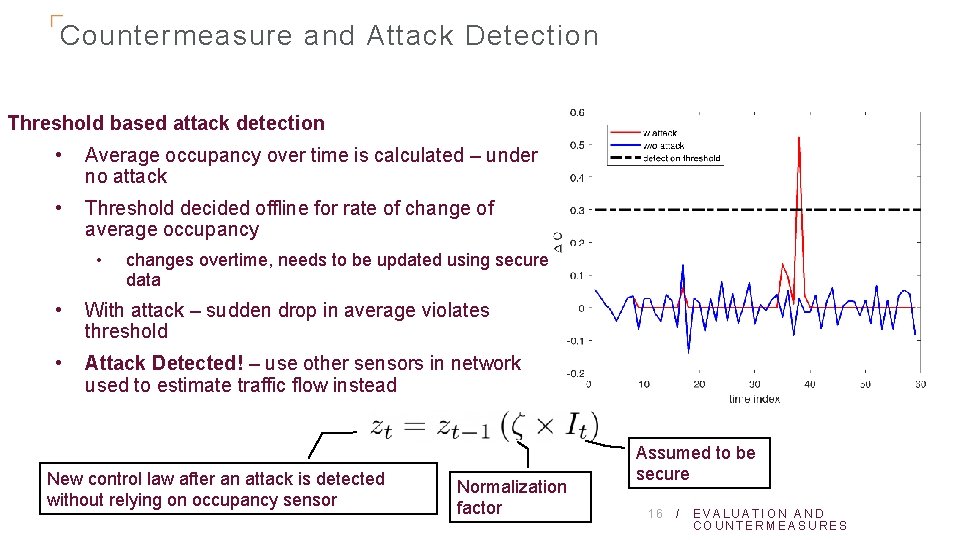
Countermeasure and Attack Detection Threshold based attack detection • Average occupancy over time is calculated – under no attack • Threshold decided offline for rate of change of average occupancy • changes overtime, needs to be updated using secure data • With attack – sudden drop in average violates threshold • Attack Detected! – use other sensors in network used to estimate traffic flow instead New control law after an attack is detected without relying on occupancy sensor Normalization factor Assumed to be secure 16 / EVALUATION AND COUNTERMEASURES

05 Conclusions

Conclusion • We introduce a replay attack on the inductive loop sensors (occupancy sensor measurements) which are used for traffic control in an isolated four-way intersection • Using the attack, we modify the green light timings and thereby maximize the queue lengths in at least one of the lanes • Show the effectiveness of the attack using VISSIM traffic simulator • Demonstrate the shortcomings of the SOTA model-based attack detector (Pasqualetti’s detector) • We put forth a threshold-based attack detection, which observes the occupancy sensor data over time and raises a flag when threshold is violated • The complexity of the threshold-based detection is O(n) • We keep the system functional by updating the control law upon detecting an attack using other secure sensors 18 / CONCLUSION

Thank You
- Slides: 19