Secure Sockets SSLTLS ICW Lecture 6 Tom Chothia








- Slides: 18

Secure Sockets SSL/TLS ICW: Lecture 6 Tom Chothia

Last Lecture • How to make socket connections between computers. • Socket = (IP_from, port_from, IP_to, port_to) • java. io. Socket • java. io. Server. Socket

Introduction Why sockets aren't secure. How to make secure socket connections. The TLS/SSL protocol. TLS/SSL in Java javax. net. ssl. SSLSocket javax. net. ssl. SSLServer. Socket Authenticating the Server.

The SSL/TLS Protocol The Secure Sockets Layer (SSL) protocol has been renamed the Transport Layer Security (TLS). It provides encrypted socket communication and optionally authentication. It may use a range of ciphers (RSA, DES, DH, . . ) These are negotiation at the start of the run.

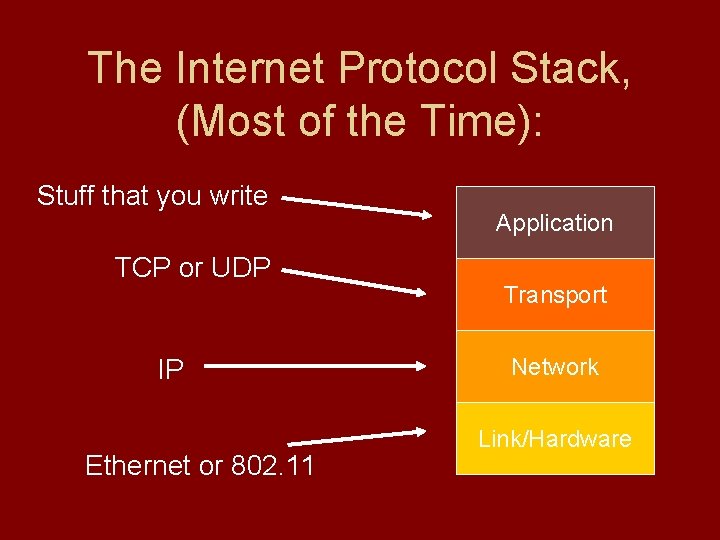
The Internet Protocol Stack, (Most of the Time): Stuff that you write TCP or UDP IP Ethernet or 802. 11 Application Transport Network Link/Hardware

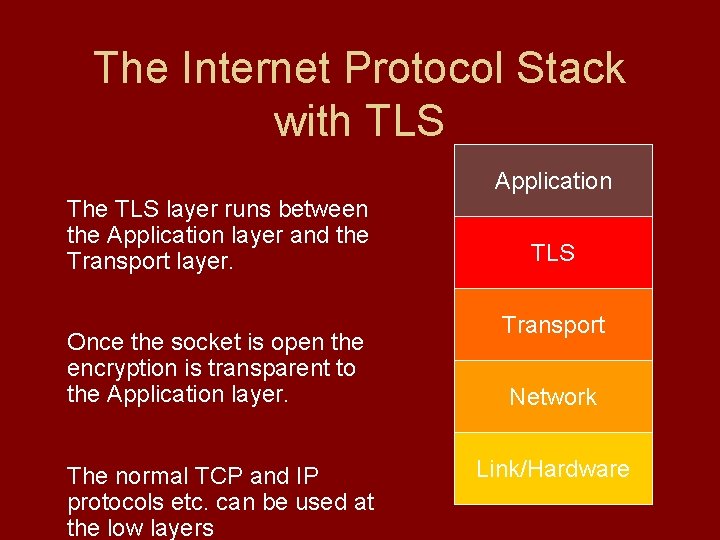
The Internet Protocol Stack with TLS Application The TLS layer runs between the Application layer and the Transport layer. Once the socket is open the encryption is transparent to the Application layer. The normal TCP and IP protocols etc. can be used at the low layers TLS Transport Network Link/Hardware

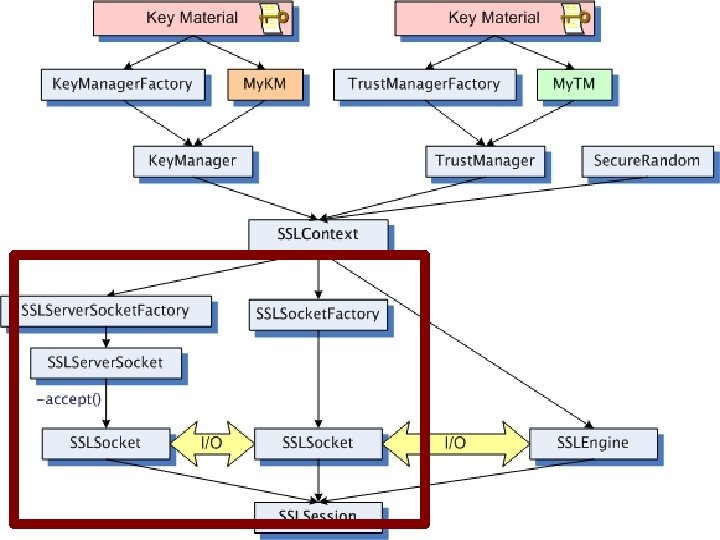
TLS in Java

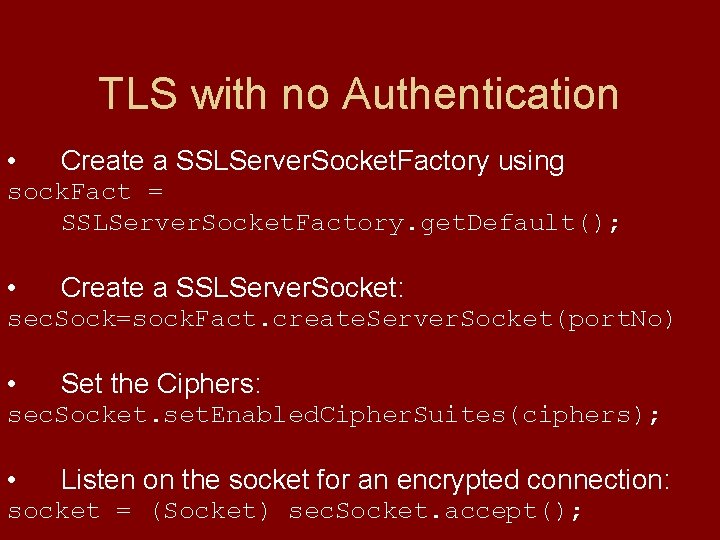
TLS with no Authentication • Create a SSLServer. Socket. Factory using sock. Fact = SSLServer. Socket. Factory. get. Default(); • Create a SSLServer. Socket: sec. Sock=sock. Fact. create. Server. Socket(port. No) • Set the Ciphers: sec. Socket. set. Enabled. Cipher. Suites(ciphers); • Listen on the socket for an encrypted connection: socket = (Socket) sec. Socket. accept();

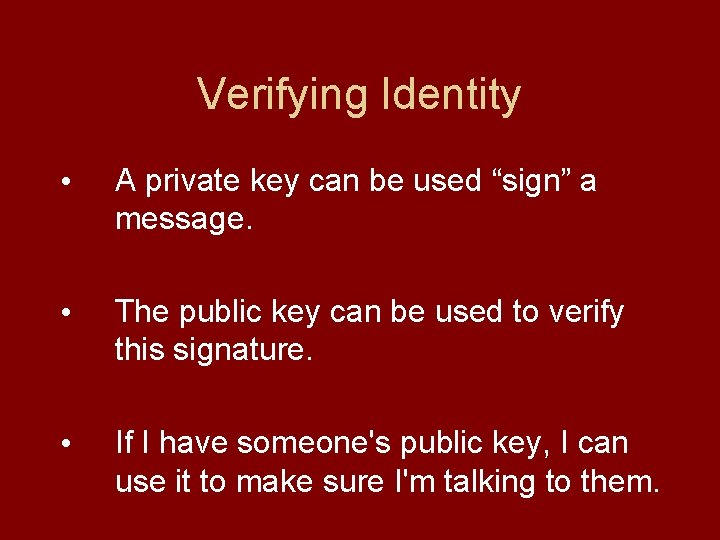
Verifying Identity • A private key can be used “sign” a message. • The public key can be used to verify this signature. • If I have someone's public key, I can use it to make sure I'm talking to them.

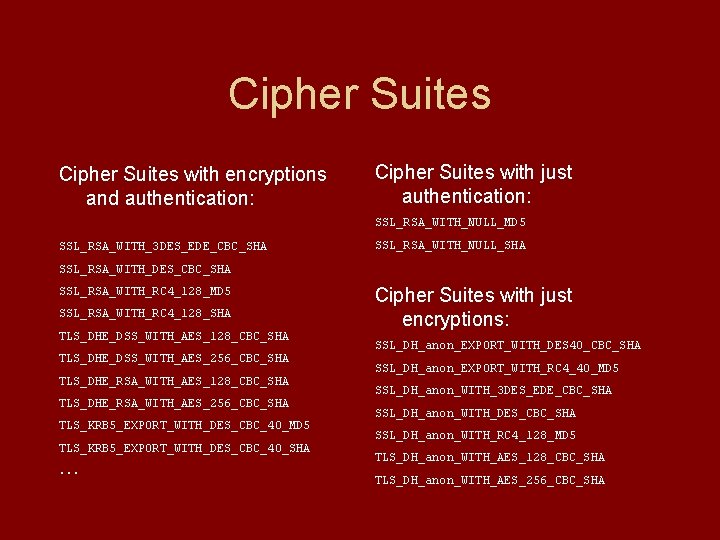
Cipher Suites with encryptions and authentication: Cipher Suites with just authentication: SSL_RSA_WITH_NULL_MD 5 SSL_RSA_WITH_3 DES_EDE_CBC_SHA SSL_RSA_WITH_NULL_SHA SSL_RSA_WITH_DES_CBC_SHA SSL_RSA_WITH_RC 4_128_MD 5 SSL_RSA_WITH_RC 4_128_SHA TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_256_CBC_SHA TLS_KRB 5_EXPORT_WITH_DES_CBC_40_MD 5 TLS_KRB 5_EXPORT_WITH_DES_CBC_40_SHA. . . Cipher Suites with just encryptions: SSL_DH_anon_EXPORT_WITH_DES 40_CBC_SHA SSL_DH_anon_EXPORT_WITH_RC 4_40_MD 5 SSL_DH_anon_WITH_3 DES_EDE_CBC_SHA SSL_DH_anon_WITH_DES_CBC_SHA SSL_DH_anon_WITH_RC 4_128_MD 5 TLS_DH_anon_WITH_AES_128_CBC_SHA TLS_DH_anon_WITH_AES_256_CBC_SHA

TLS in Java

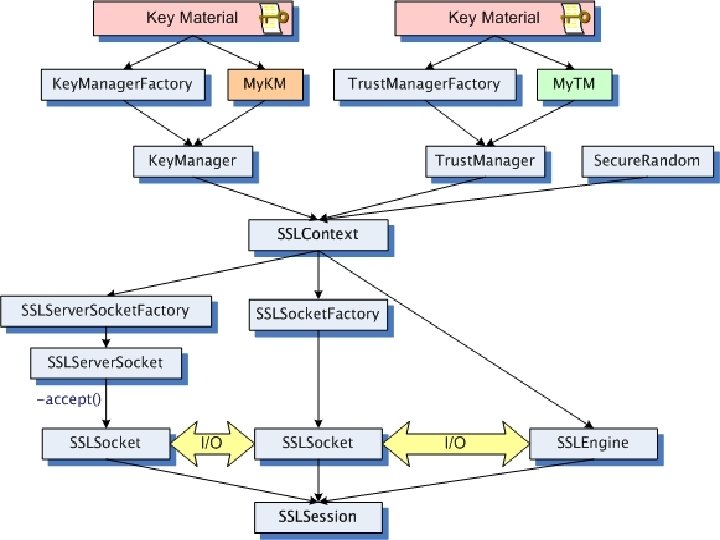
SSL/TLS contexts and Trust SSL/TLS can set up a secure connection with someone if we have their public key. The SSL context can be loaded with the keys used to identify yourself. the public keys of people we trust.

Keystores: a Reminder • We saw keystores in the Crypto Lecture. • The Keystores password protected keys and certifications. • Use “java. security. Key. Store” or the “keytool” from the command line.

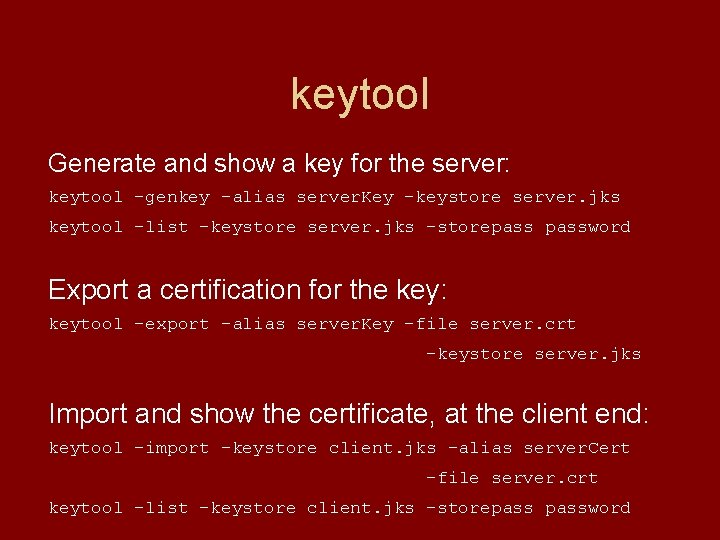
keytool Generate and show a key for the server: keytool -genkey -alias server. Key -keystore server. jks keytool -list -keystore server. jks -storepassword Export a certification for the key: keytool -export -alias server. Key -file server. crt -keystore server. jks Import and show the certificate, at the client end: keytool -import -keystore client. jks -alias server. Cert -file server. crt keytool -list -keystore client. jks -storepassword

Certificate Chains • The public keys are stored as certificates. • If we have someone's public key we can use it to check their identity. • But we can't have the public key of everyone on the Internet. : -(

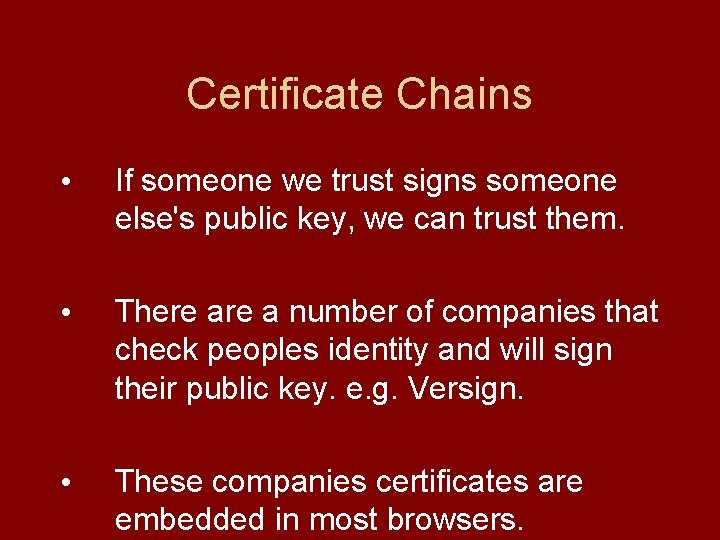
Certificate Chains • If someone we trust signs someone else's public key, we can trust them. • There a number of companies that check peoples identity and will sign their public key. e. g. Versign. • These companies certificates are embedded in most browsers.

Summary • SSL/TLS is the most common way to secure connections – – javax. net. ssl. SSLSocket javax. net. ssl. SSLServer. Socket • To Authenticate someone, you must have a certificate/certificate chains for the server. • Browsers come with certificates of Versign, etc. they will check your IS and sign your key for a fee.

Next Time: • XML and Java XML tools. • XML is the default file format of Internet systems. • The next lecture will tell you what XML is and how to manipulate XML in Java.