Secure Routing in Sensor Networks Attacks and Countermeasures









- Slides: 24

Secure Routing in Sensor Networks: Attacks and Countermeasures Chris Karlof and David Wagner University of California at Berkeley First IEEE International Workshop on Sensor Network Protocols and Applications 5/11/2003

Security in sensor networks l Security is critical l l Military apps Building monitoring Burglar alarms Emergency response Yet security is hard l l Wireless links are inherently insecure Resource constraints Lossy, low bandwidth communication Lack of physical security

Our contributions l l Threat models and security goals New attacks against sensor network routing protocols l l Detailed security analysis of 15 routing protocols Countermeasure suggestions

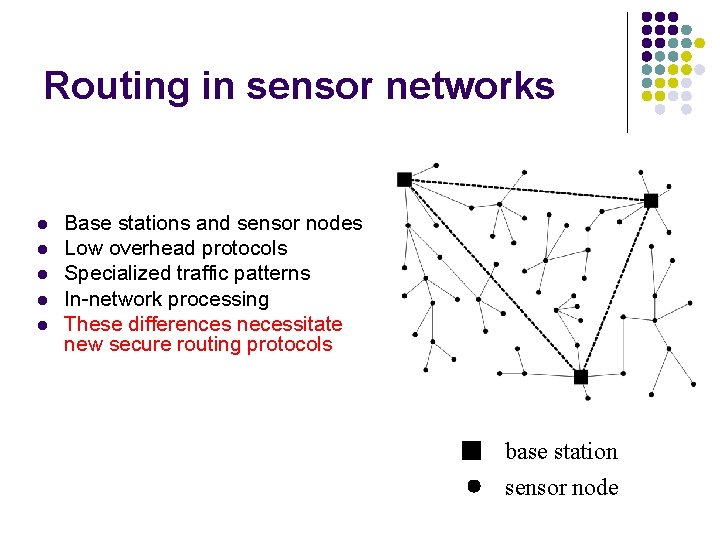
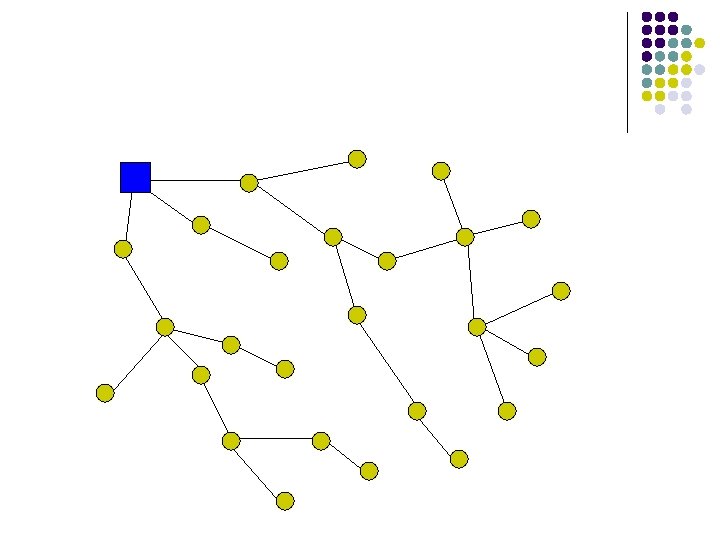
Routing in sensor networks l l l Base stations and sensor nodes Low overhead protocols Specialized traffic patterns In-network processing These differences necessitate new secure routing protocols base station sensor node

Secure routing goals and threat models l Security goals: l l l Confidentiality: messages are secret Integrity: messages are not tampered with Availability In-network processing makes end-to-end security hard Link layer security still possible Need to consider compromised nodes (insiders) and resourceful attackers

Attacks

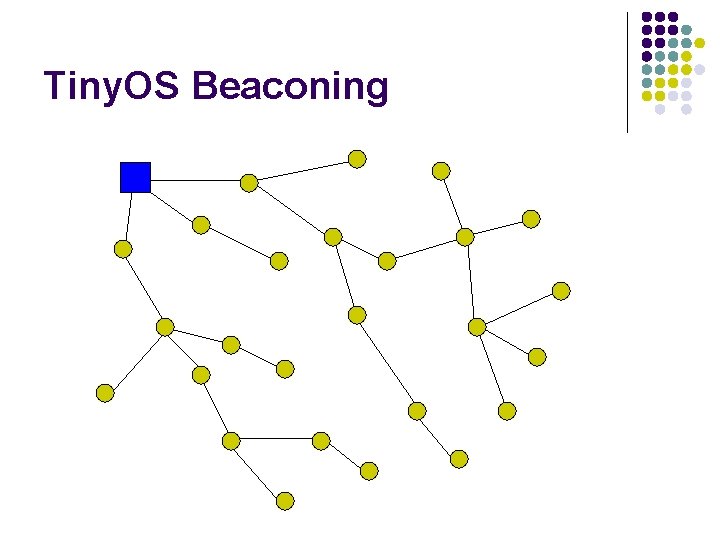
Tiny. OS Beaconing

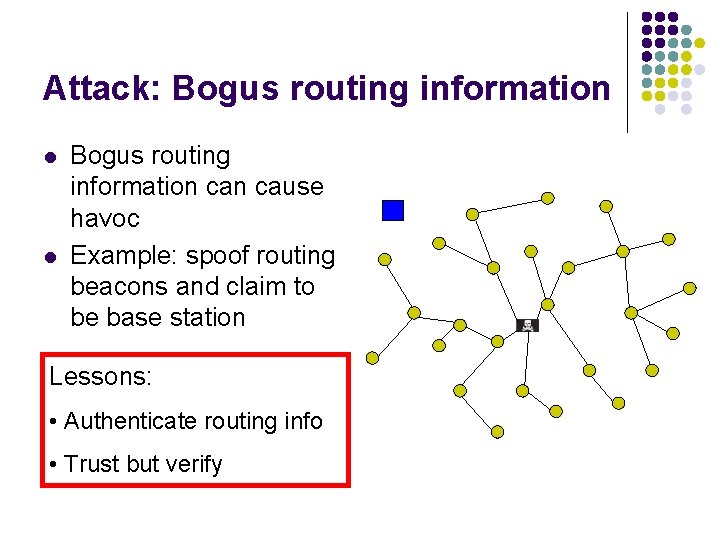
Attack: Bogus routing information l l Bogus routing information cause havoc Example: spoof routing beacons and claim to be base station Lessons: • Authenticate routing info • Trust but verify

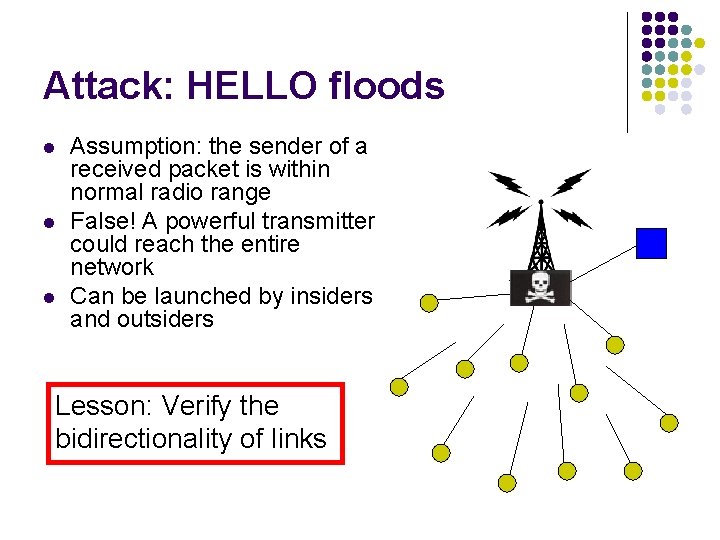
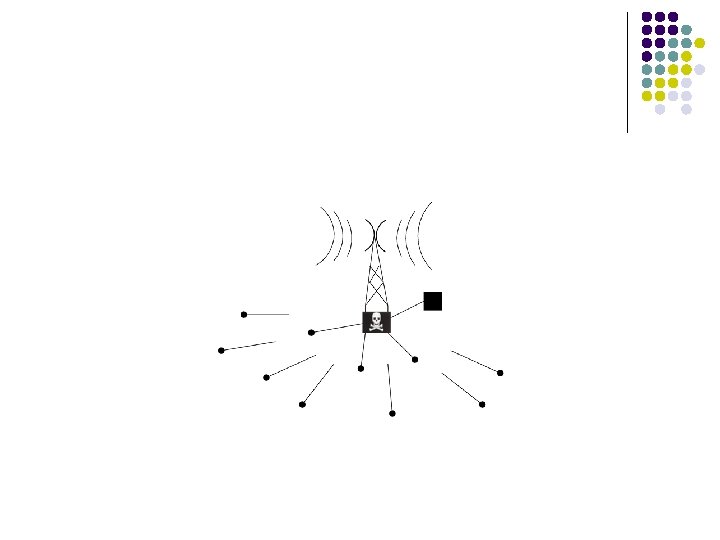
Attack: HELLO floods l l l Assumption: the sender of a received packet is within normal radio range False! A powerful transmitter could reach the entire network Can be launched by insiders and outsiders Lesson: Verify the bidirectionality of links

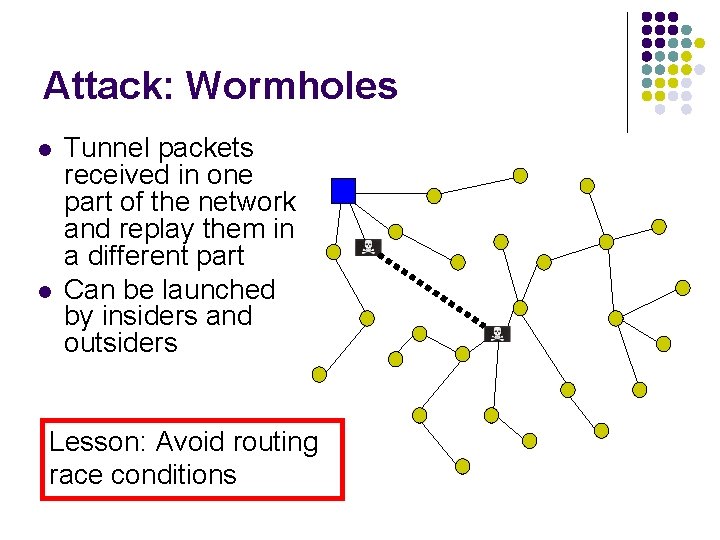
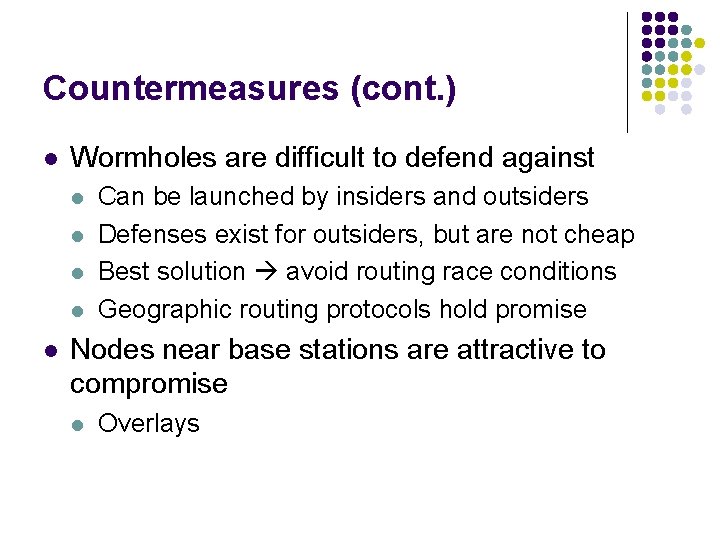
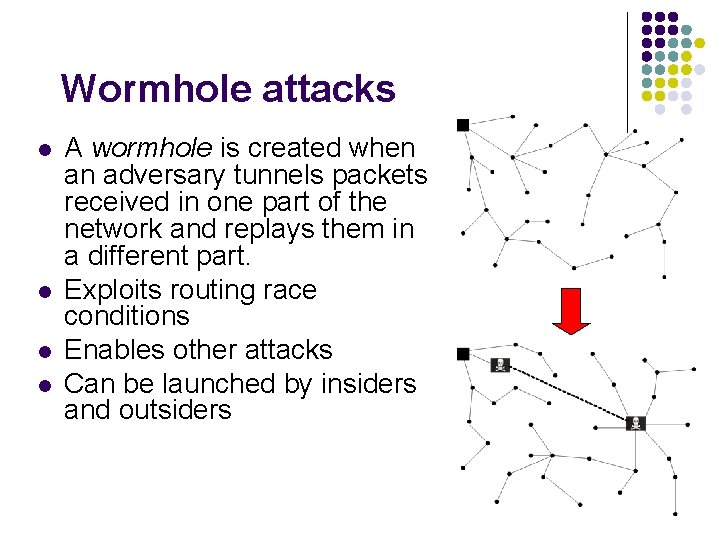
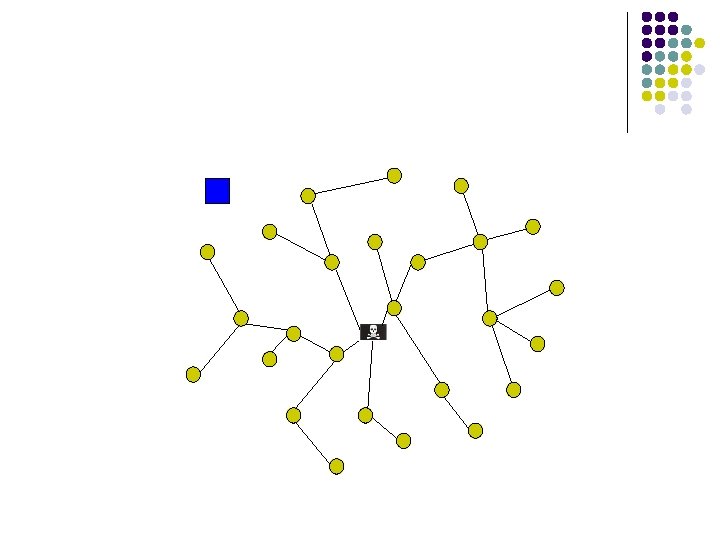
Attack: Wormholes l l Tunnel packets received in one part of the network and replay them in a different part Can be launched by insiders and outsiders Lesson: Avoid routing race conditions

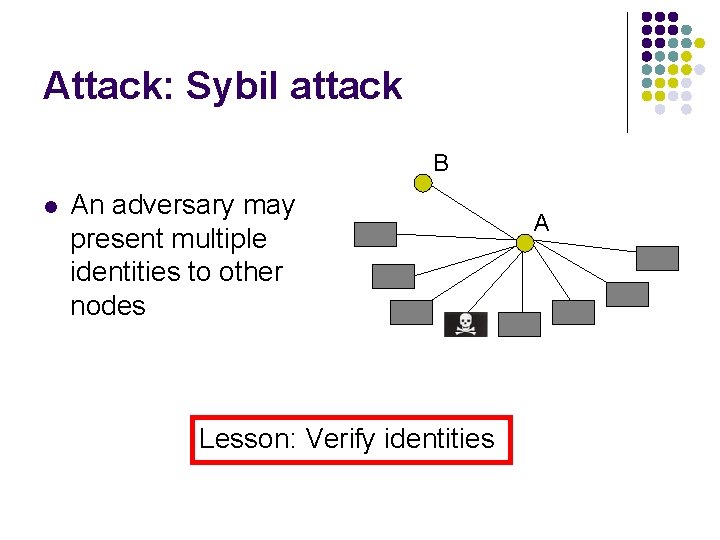
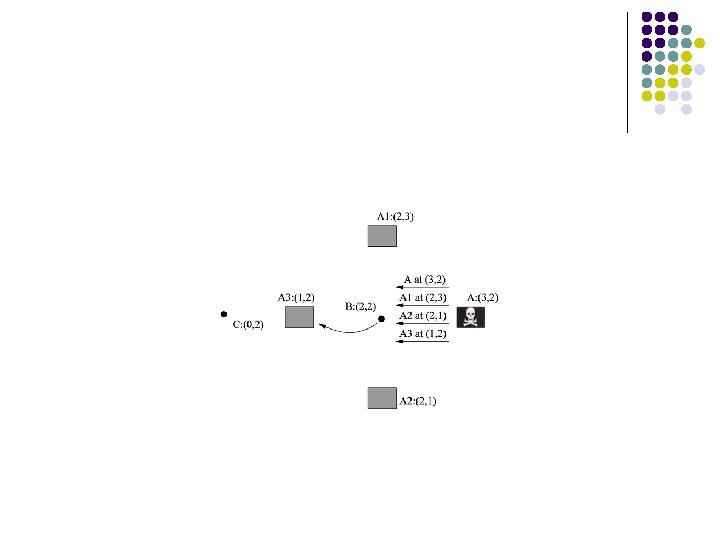
Attack: Sybil attack B l An adversary may present multiple identities to other nodes Lesson: Verify identities A

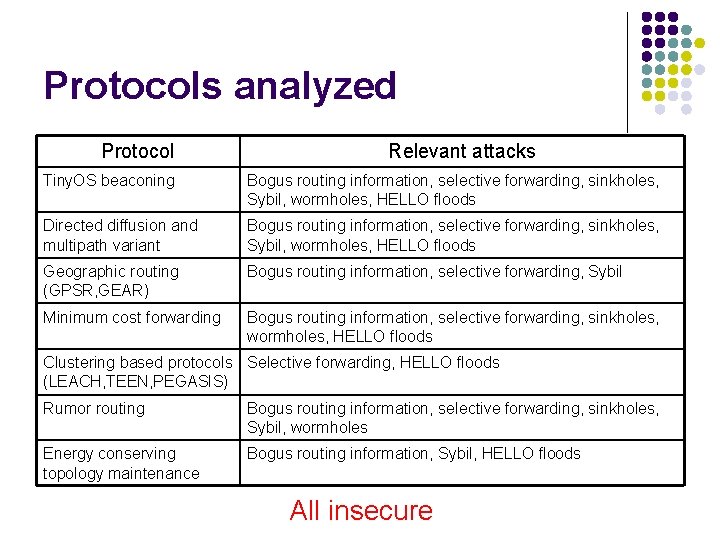
Protocols analyzed Protocol Relevant attacks Tiny. OS beaconing Bogus routing information, selective forwarding, sinkholes, Sybil, wormholes, HELLO floods Directed diffusion and multipath variant Bogus routing information, selective forwarding, sinkholes, Sybil, wormholes, HELLO floods Geographic routing (GPSR, GEAR) Bogus routing information, selective forwarding, Sybil Minimum cost forwarding Bogus routing information, selective forwarding, sinkholes, wormholes, HELLO floods Clustering based protocols Selective forwarding, HELLO floods (LEACH, TEEN, PEGASIS) Rumor routing Bogus routing information, selective forwarding, sinkholes, Sybil, wormholes Energy conserving topology maintenance Bogus routing information, Sybil, HELLO floods All insecure

Countermeasures l l We have countermeasure suggestions and design considerations See paper for details

Conclusions End-to-end security is limited in sensor networks l Link layer security is important l It is not enough l Design time security l

Questions?

Extra Slides

Countermeasures l Access control with link layer crypto l l Verify neighbors’ identities l l Prevents Sybil attack Verify bidirectionality of links l l Globally shared key outsiders Per link keys insiders Authenticated broadcast and flooding Prevents HELLO floods Multipath and probabilistic routing l Limits effects of selective forwarding

Countermeasures (cont. ) l Wormholes are difficult to defend against l l l Can be launched by insiders and outsiders Defenses exist for outsiders, but are not cheap Best solution avoid routing race conditions Geographic routing protocols hold promise Nodes near base stations are attractive to compromise l Overlays

Why is this a problem? l Wireless security has been spotty l l l WEP/802. 11 b GSM Secure routing mechanisms for ad-hoc wireless networks are not necessarily applicable l l l Too much functionality any-to-any routing Not enough functionality sensor nets are often app. specific Too much overhead public key cryptography

Wormhole attacks l l A wormhole is created when an adversary tunnels packets received in one part of the network and replays them in a different part. Exploits routing race conditions Enables other attacks Can be launched by insiders and outsiders



