Secure Print Protocols in a Traditional Printing Environment













- Slides: 16

Secure Print Protocols in a Traditional Printing Environment David. Staal@Barr. Systems. com February 24, 2004

Contents n The Production Printing Environment ¨ What is ‘Production Printing? ’ ¨ Protocols and Platforms Used ¨ Security Needs in Production Printing n Possible Security Solutions ¨ IPP with TLS (SSL) ¨ IPSec ¨ Encryption for LPR/LPD and Raw Socket

Introduction Barr Systems provides print management software for the Production Printing industry. n Our customers are becoming more concerned about security as their printing moves to TCP/IP networks. n

What is Production Printing? n n Production Printing is a phrase used to describe the traditional printing world started by IBM and Xerox. Production Printing is characterized by: ¨ Large data centers, often outsourced ¨ High-speed, 100 ppm+ printers ¨ Large volumes of print in small windows of time ¨ Typically statements, bills, checks

More about Production Printing n Organizations that do Production Printing: ¨ Banks and Credit Card companies ¨ Mutual Fund companies ¨ Insurance companies ¨ Hospitals ¨ Phone companies ¨ Many branches of Government and Military ¨ Just about any large corporation

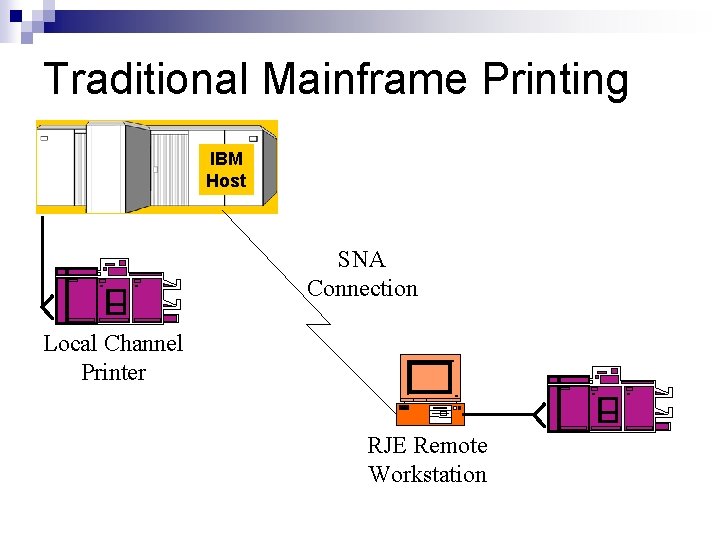
Traditional Mainframe Printing IBM Host SNA Connection Local Channel Printer RJE Remote Workstation

Traditional Printing Environment n n Data originates on IBM Mainframes Prints on local channel-attached Xerox, IBM or Oce’ printers Mostly EBCDIC Line Data (text), and some IPDS Connections to remote print sites use: ¨ SNA connections ¨ Channel extension over dedicated lines

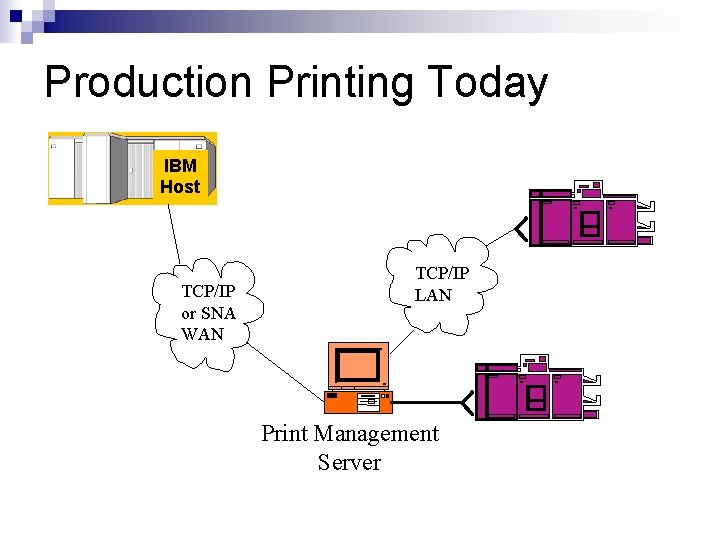
Production Printing Today IBM Host TCP/IP or SNA WAN TCP/IP LAN Print Management Server

Production Printing Environment n n Data still originates on IBM Mainframes, or other large hosts, such as Unix systems Prints on Xerox, IBM and Oce’ printers, but many now with TCP/IP interfaces EBCDIC Line Data (text), and IPDS Connections to remote print sites use: SNA over TCP/IP ¨ TCP/IP LPR/LPD or Raw Socket (Port 9100) ¨ n PC-based or Unix Print Management software used to manage multiple printers at print sites

Why Security Now? In the past, the communications protocols were more proprietary, and in more closed environments. n Now, more and more print traffic moves over TCP/IP networks. n Lots of confidential data, credit card numbers, account information and medical information. n

What Kind of Security is Needed? n n Confidentiality is the pre-eminent need, to prevent stealing of private information. Message Integrity would also be useful. Authentication is not a priority, because these printers or print servers are not shared to other users, and use well established paths and fixed IP addresses. Encryption alone would provide what is needed most.

Possible Solutions for Secure Print IPP with TLS (SSL) n IPSec n Encryption for LPR/LPD and Raw Socket n

IPP with TLS (SSL) n n If fully implemented, IPP with security would solve the problem. Many products in the Production Print industry have not yet implemented IPP. The IBM host and Xerox printer implementations of IPP apparently don’t include security. The ‘special options’ for production print with LPR/LPD are not available in the IPP implementation on some systems.

IPSec n n n An IPSec secure tunnel would make sense in the Production Print environment, since the path and IP addresses are fixed. Most versions of Microsoft Windows support IPSec. z/OS on the IBM mainframe supports IPSec. The bigger Xerox printers run on Sun Solaris workstations, which should support IPSec. Smaller printers from Xerox and other vendors may not support it.

Encryption for LPR/LPD and Raw Socket n n n There is no current standard for security for these older protocols. An Encryption standard, such as AES, would provide what is needed. Some kind of key exchange, such as IKE, or a static key mechanism would be needed. Compression before Encryption would be effective in improving performance. Some vendors have already implemented this on their own.

Open Discussion What do you think of these approaches? n Are there other solutions? n What action, if any, should the PWG take? n