Secure email r How do you do it






- Slides: 15

Secure e-mail r How do you do it? m Need to worry about sniffing, modifying, enduser masquerading, replaying. m If sender and receiver have shared secret keys, then straightforward. m Can use public-key cryptography to distribute keys. m But users do not want to hassle with certificate authority. 1

Secure e-mail: PGP r PGP = Pretty Good Privacy r It is availiable free on a variety of platforms. m inventor, Phil Zimmerman, was target of 3 -year federal investigation. r Based on well known algorithms. r Not developed or controlled by government or standards organizations 2

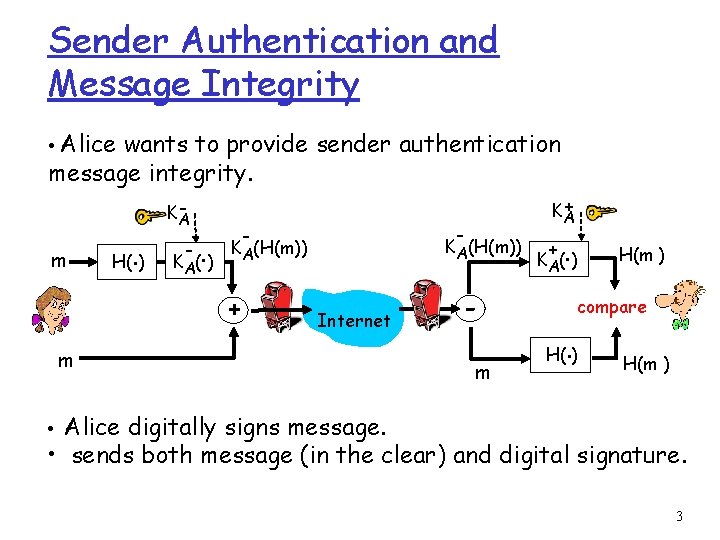
Sender Authentication and Message Integrity • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m m + . K A( ) H(m ) compare . H( ) H(m ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. 3

PGP r Hash: m SHA-1 m 160 bits r Public key cryptography: m RSA r Question: Why digital signatures for authentication? Why not a MAC? m Could use public-key crypto to get a shared key. m But if there are 100 recipients? Need to distribute 100 MAC keys. 4

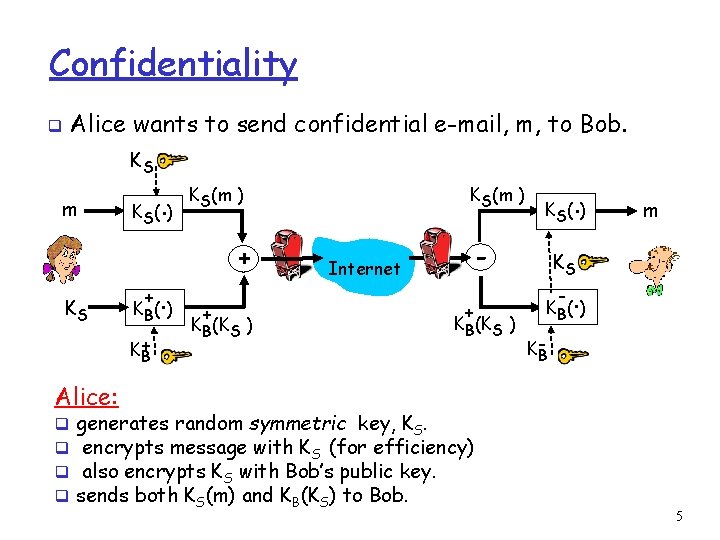
Confidentiality q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) m KS - . K B( ) KB Alice: q q generates random symmetric key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob. 5

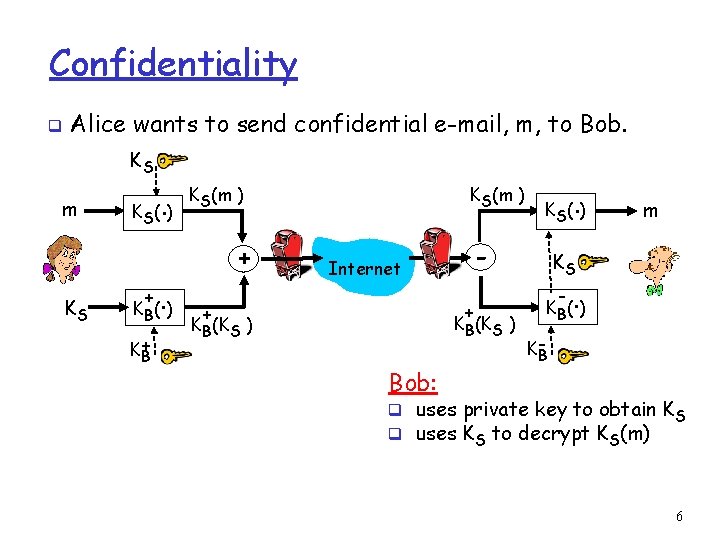
Confidentiality q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . K B( ) K+ B KS(m ) + - Internet + + KB(KS ) Bob: . K S( ) m KS - . K B( ) KB q uses private key to obtain KS q uses KS to decrypt KS(m) 6

Confidentiality: PGP r Session key: 128 bits r Symmetric encryption: m CAST-128 or IDEA or 3 DES r Public key encryption m RSA 7

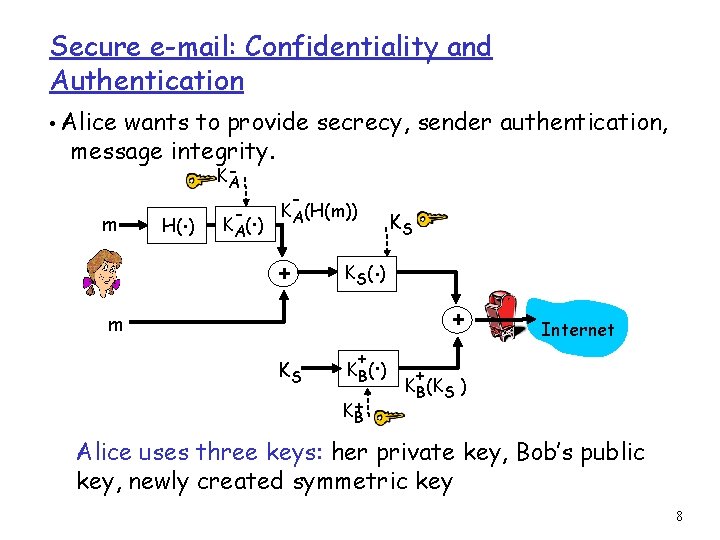
Secure e-mail: Confidentiality and Authentication • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key 8

PGP key rings r Each node has two key rings: m Public/private key pairs owned by that node m Public key of other users r For the keys of other users, for each key track: m user id: e-mail address, name, address, etc. m public key m timestamp: date when key was generated m key ID m key legitimacy m signatures 9

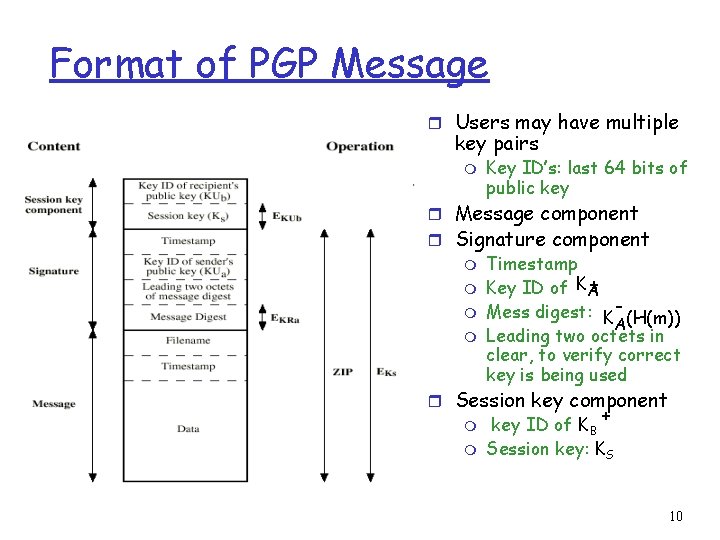
Format of PGP Message r Users may have multiple key pairs m Key ID’s: last 64 bits of public key r Message component r Signature component m Timestamp + m Key ID of KA m Mess digest: K- (H(m)) A m Leading two octets in clear, to verify correct key is being used r Session key component + m key ID of KB m Session key: KS 10

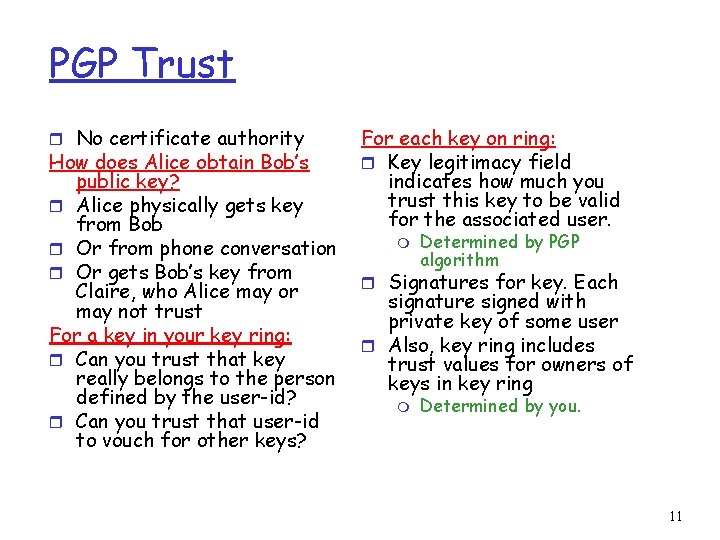
PGP Trust r No certificate authority How does Alice obtain Bob’s public key? r Alice physically gets key from Bob r Or from phone conversation r Or gets Bob’s key from Claire, who Alice may or may not trust For a key in your key ring: r Can you trust that key really belongs to the person defined by the user-id? r Can you trust that user-id to vouch for other keys? For each key on ring: r Key legitimacy field indicates how much you trust this key to be valid for the associated user. m Determined by PGP algorithm r Signatures for key. Each signature signed with private key of some user r Also, key ring includes trust values for owners of keys in key ring m Determined by you. 11

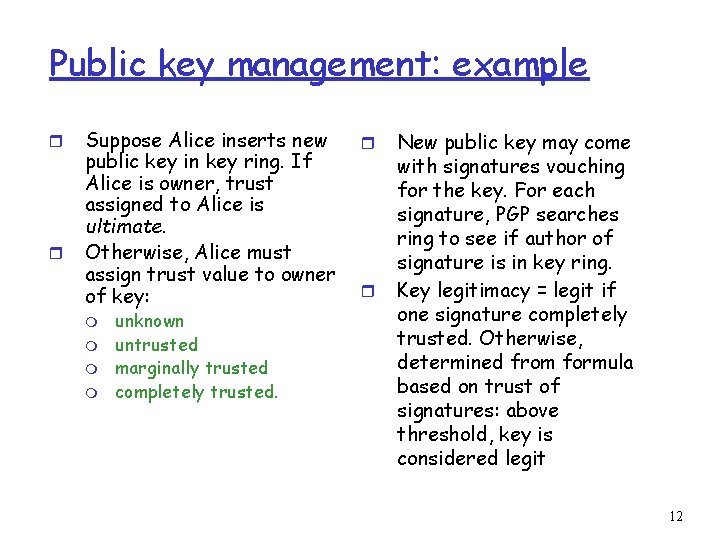
Public key management: example r r Suppose Alice inserts new public key in key ring. If Alice is owner, trust assigned to Alice is ultimate. Otherwise, Alice must assign trust value to owner of key: m m unknown untrusted marginally trusted completely trusted. r r New public key may come with signatures vouching for the key. For each signature, PGP searches ring to see if author of signature is in key ring. Key legitimacy = legit if one signature completely trusted. Otherwise, determined from formula based on trust of signatures: above threshold, key is considered legit 12

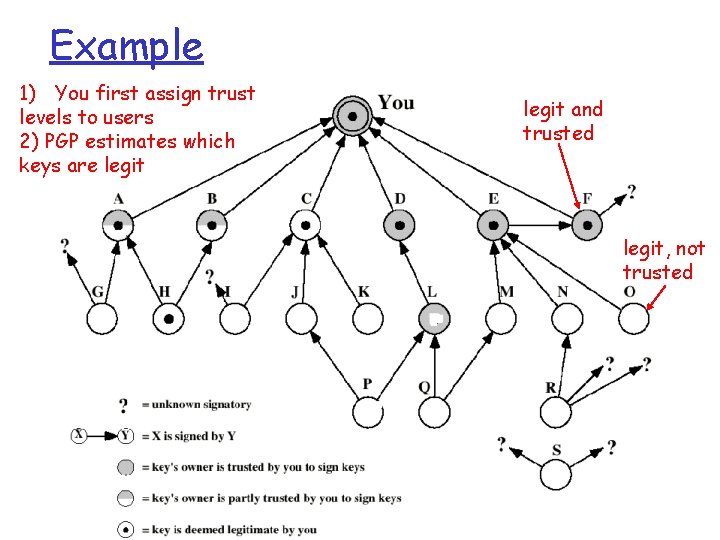
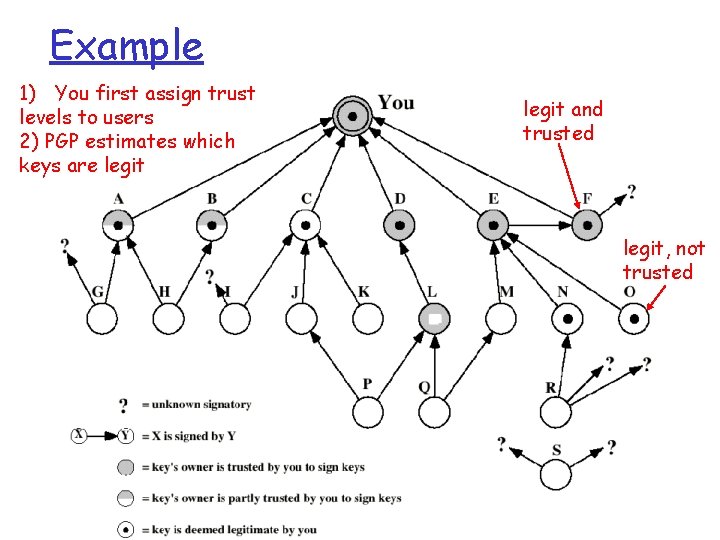
Example 1) You first assign trust levels to users 2) PGP estimates which keys are legit and trusted legit, not trusted 13

Example 1) You first assign trust levels to users 2) PGP estimates which keys are legit and trusted legit, not trusted 14

PGP summary r PGP provides security at the application layer to a single application r Provides: m Authentication, integrity, confidentiality r Public key verification m Web of trust 15