Secure Email An Implementation Success Story How Texoma




















- Slides: 42

Secure E-mail: An Implementation Success Story How Texoma Healthcare System Identified & Addressed its Secure E-mail Requirements Presented by Jeff Kerber, Former Corporate Privacy Officer and HIPAA Compliance Director Texoma Healthcare System March 8, 2004 1

Agenda ¨ A Brief History of E-mail ¨ The Obligatory HIPAA Review ¨ Vulnerabilities and Cryptography ¨ The THCS Experience ¨ The Highlights and “Take-aways” 2

Brief History of E-mail 2001 2000 1990 1980 1971 1960 il d ma un E- abo re cu ts c d” Se odu ate pr nd ma ium ts n“ ed un d tio an s m cco yp cr ss on l a e ati mai En sin ic bu un eb us mm n w ed ito co llio as iqu al mi ele n )r Ub so 10 r cy pe 97 iva Pr (19 a) od or Go , ud tty ies E re sit 88 (P er (19 P niv ent PG nu m e i rn us ove g ad re nd sp , a ide ch W ear d s se re lea re s PC nd ted M se IB lga on mu ins ro ml sp To rd ay da an ”R l St ted bo en sym h inv y arc il “ g @ d b ese ma sin he E- t u s nc d R fir au ce T l an NE Adv ency PA se g AR fen ts A De ojec Pr 3

The Obligatory HIPAA Review ¨ Defining Covered Entities ¨ The Privacy Rule and Security Rule – 164. 530(c)(1) and (2) a. k. a. “Mini-Security Rule – Security Rule, Technical Specifications 164. 312 (a)(2)(iv) (Addressable) – Security Rule, Technical Specifications 164. 312 (e)(2)(ii) (Addressable) ¨ April 14, 2003 and April 21, 2005 ¨ Reasonable Effort 4

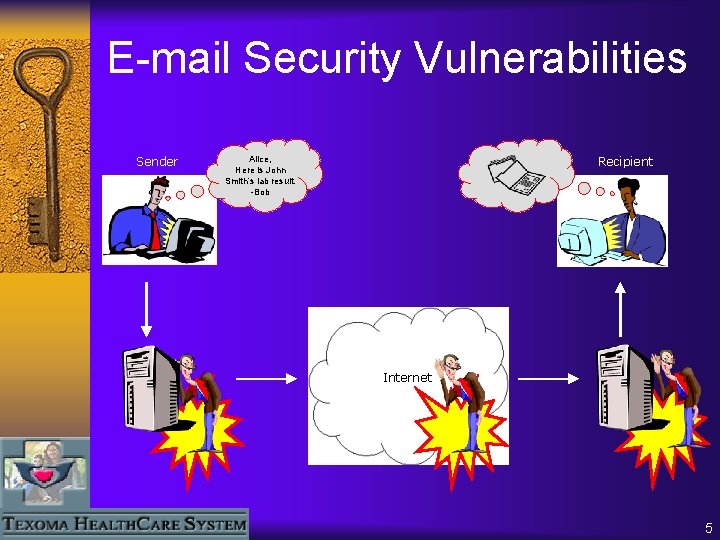
E-mail Security Vulnerabilities Sender Alice, Here is John Smith’s lab result. -Bob Recipient Internet 5

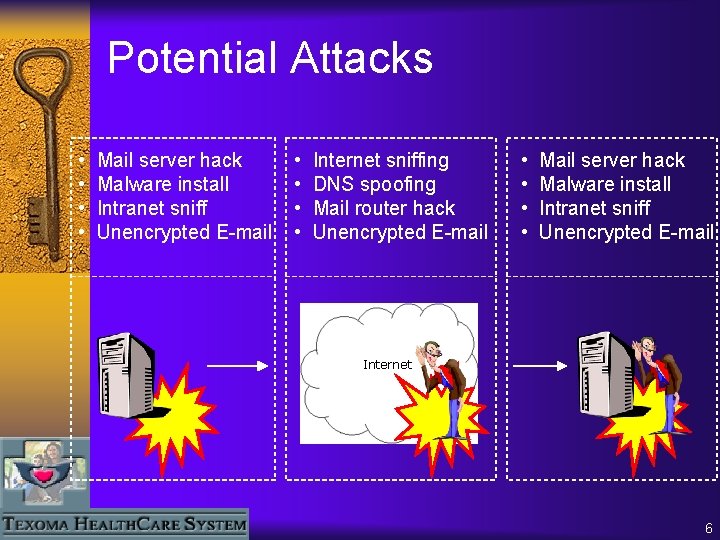
Potential Attacks • • Mail server hack Malware install Intranet sniff Unencrypted E-mail • • Internet sniffing DNS spoofing Mail router hack Unencrypted E-mail • • Mail server hack Malware install Intranet sniff Unencrypted E-mail Internet 6

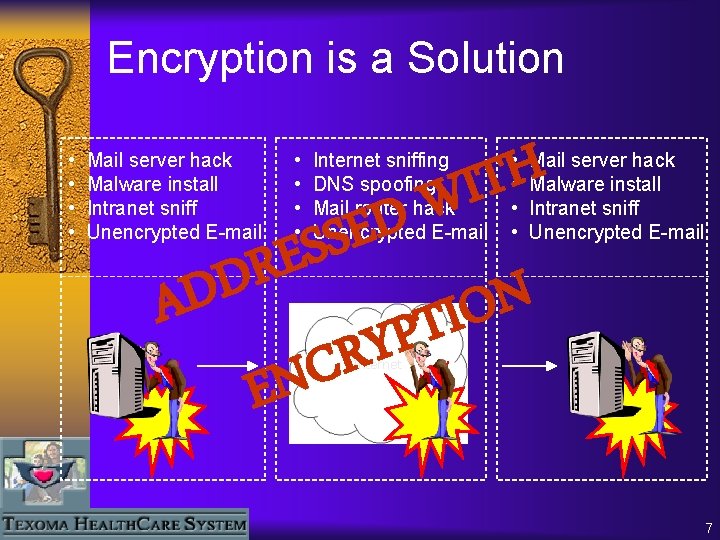
Encryption is a Solution • • Mail server hack Malware install Intranet sniff Unencrypted E-mail • • H T I W Internet sniffing DNS spoofing Mail router hack Unencrypted E-mail D E S S E • • Mail server hack Malware install Intranet sniff Unencrypted E-mail R D N AD O I T P Y R C EN Internet 7

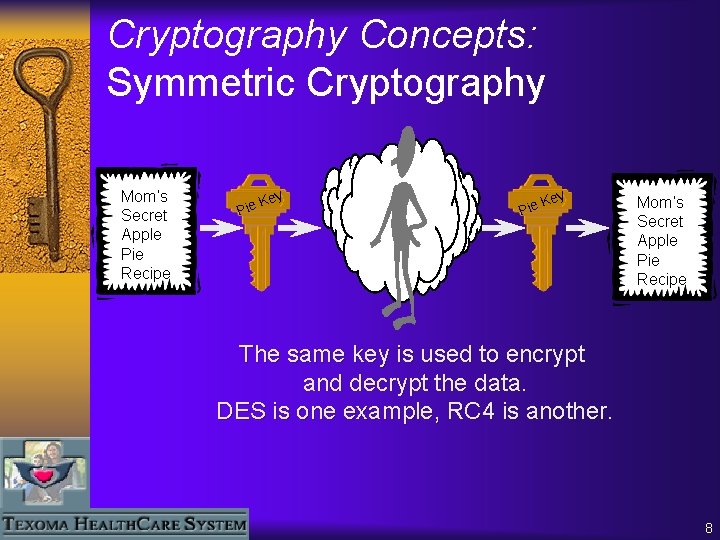
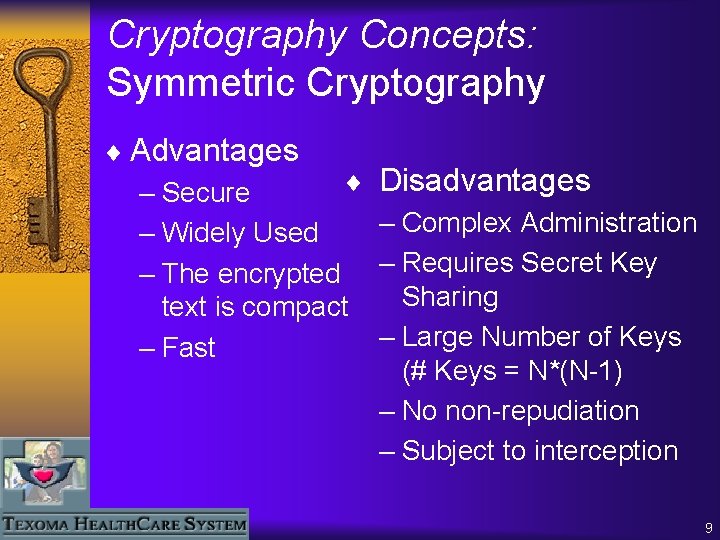
Cryptography Concepts: Symmetric Cryptography Mom’s Secret Apple Pie Recipe ey K Pie Mom’s Secret Apple Pie Recipe The same key is used to encrypt and decrypt the data. DES is one example, RC 4 is another. 8

Cryptography Concepts: Symmetric Cryptography ¨ Advantages ¨ – Secure – Widely Used – The encrypted text is compact – Fast Disadvantages – Complex Administration – Requires Secret Key Sharing – Large Number of Keys (# Keys = N*(N-1) – No non-repudiation – Subject to interception 9

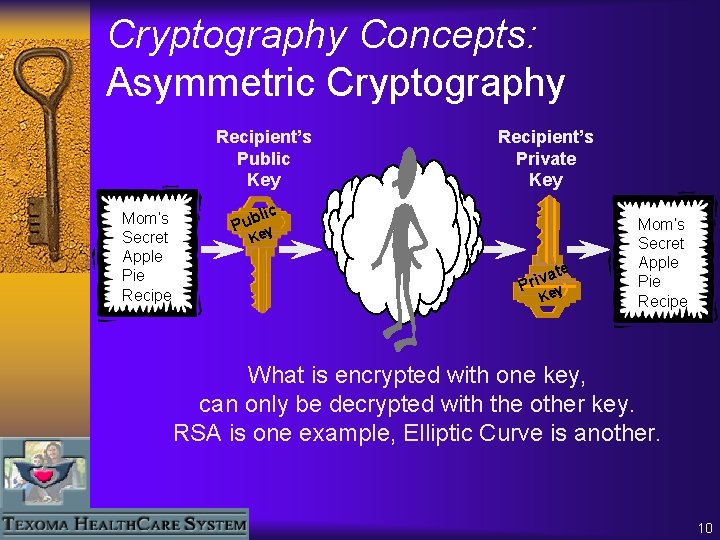
Cryptography Concepts: Asymmetric Cryptography Recipient’s Public Key Mom’s Secret Apple Pie Recipient’s Private Key lic Pub y Ke a Priv te Key Mom’s Secret Apple Pie Recipe What is encrypted with one key, can only be decrypted with the other key. RSA is one example, Elliptic Curve is another. 10

Cryptography Concepts: Trusting the Public Key X. 509 Digital Certificate “I officially notarize the association between this particular User, and this particular Public Key” 11

Cryptography Concepts: Asymmetric Cryptography ¨ Advantages – Secure – No secret sharing – No prior relationship – Easier Admin – Many fewer keys – Supports nonrepudiation ¨ Disadvantages – Slower than symmetric key – The encrypted text is larger than a symmetric version 12

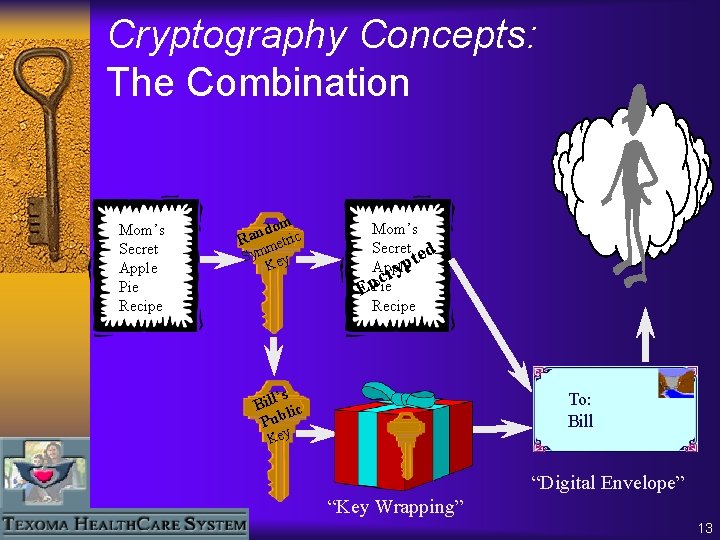
Cryptography Concepts: The Combination Mom’s Secret Apple Pie Recipe domic n a R etr m Sym ey K Mom’s Secret d te p Apple y cr n Pie E Recipe ’s Bill lic Pub To: Bill Key “Digital Envelope” “Key Wrapping” 13

Cryptography Concepts: The Combination ¨ You get the best of both worlds – The benefits of Symmetric Key • Speed • Compact Encrypted Text – The benefits of Public Key • Simpler Key management • Digital Signature • Non-Repudiation 14

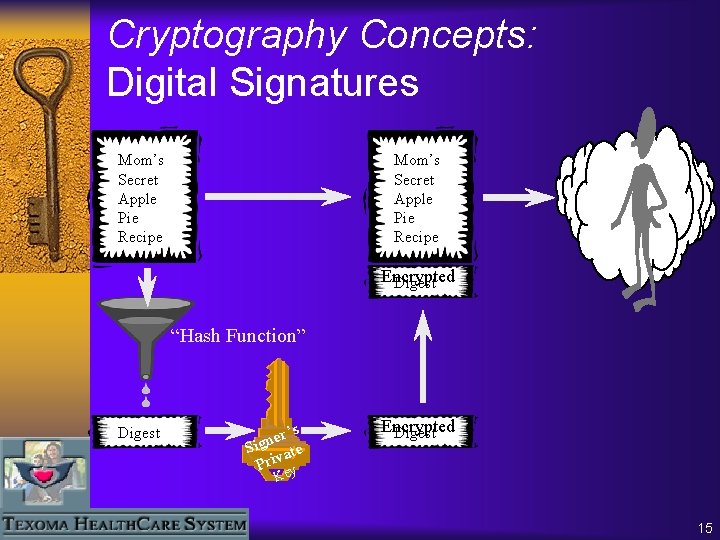
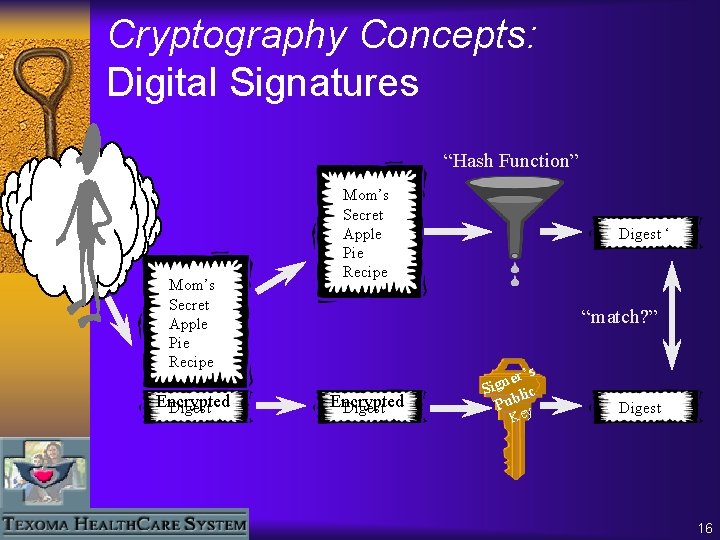
Cryptography Concepts: Digital Signatures Mom’s Secret Apple Pie Recipe Encrypted Digest “Hash Function” Digest r’s e n Sig ate Priv Encrypted Digest Key 15

Cryptography Concepts: Digital Signatures “Hash Function” Mom’s Secret Apple Pie Recipe Encrypted Digest Mom’s Secret Apple Pie Recipe Digest ‘ “match? ” Encrypted Digest er’s n g i S lic Pub y Ke Digest 16

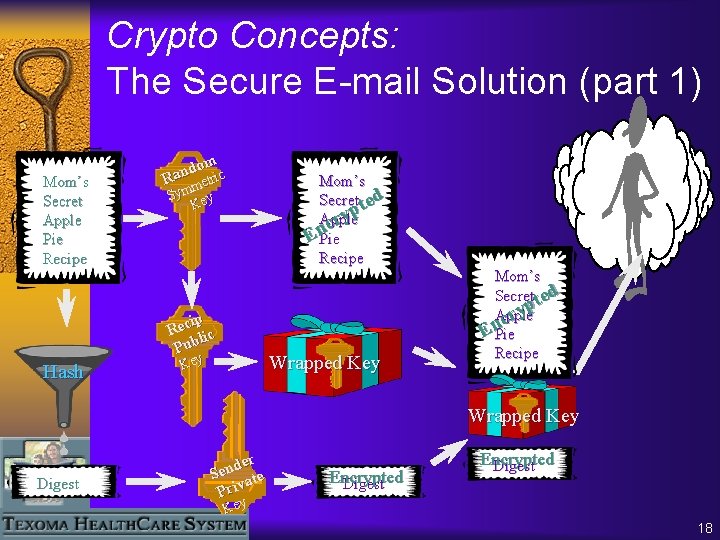
Cryptography Concepts: The Secure E-mail Problem ¨ What would the steps be to do send a message with the following properties: – It cannot be read by anyone but the intended recipient – The recipient can assure it was not modified in transit – The recipient can verify who authored the message – The recipient cannot later claim that they didn’t send it 17

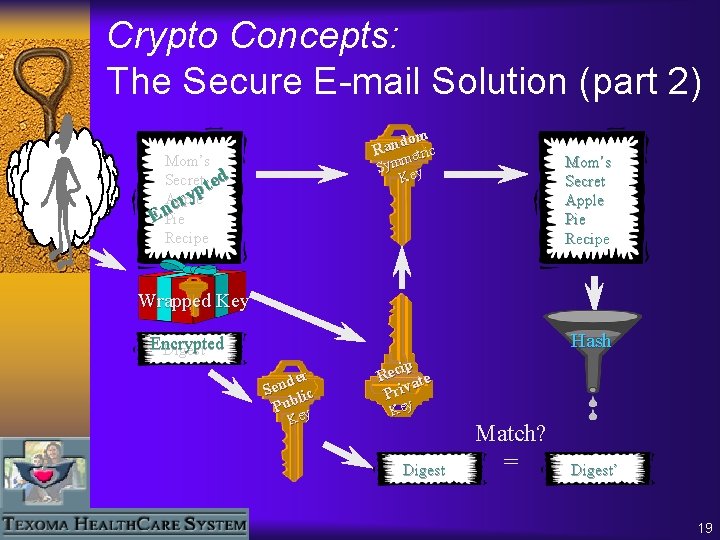
Crypto Concepts: The Secure E-mail Solution (part 1) Mom’s Secret Apple Pie Recipe om d n Ra etric m Sym ey K ip Rec lic Pub Hash Mom’s Secret ted yp Apple r c En. Pie Recipe Wrapped Key Mom’s Secret ted p y Apple r c En. Pie Recipe Wrapped Key Digest der n e S ate v i r P Encrypted Digest Key 18

Crypto Concepts: The Secure E-mail Solution (part 2) dom Ran etric Mom’s Secret ted yp Apple r c En. Pie Recipe m Sym ey K Mom’s Secret Apple Pie Recipe Wrapped Key Hash Encrypted Digest der n e S lic b u P Key ip Rec ate Priv Key Digest Match? = Digest’ 19

The THCS Experience ¨ Our decision-making team – CIO and CFO – HIPAA Compliance Officer, CPO – Operations – Decision Support – Network Manager – IS Support Services 20

The THCS Experience ¨ Requirements Analysis – Ease of use – Zero client footprint (senders and recipients) – Key distribution and management – Proven encryption technology – Control of message store 21

The Three Challenges of Secure E-mail q THCS users can’t use encryption—it’s too difficult! q How do we send secure messages to recipients with no digital certificate? q Manual certificate exchange is impossible to manage with our business partners. 22

The THCS Experience ¨ Minimum system requirements for Secure. Messenger message retrieval – Message retrieval is intuitive – Message links are common industry practice (airlines, banks, greeting cards) – Works with AOL, Yahoo!, Hotmail ¨ Can’t assume recipients will be able or willing to download, install, or use a plugin or separate secure E-mail application – Individual recipients – Physicians – Business Associates 23

The THCS Experience ¨ Product Review and Selection – Concentrated on secure messaging vendors – Avoided complicated PKI vendors – Understood HIPAA regulations – Demos – In-house trials 24

The THCS Experience ¨ Implementation and Integration – Well-documented install preparation and process – Drop it in and go – Excellent training 25

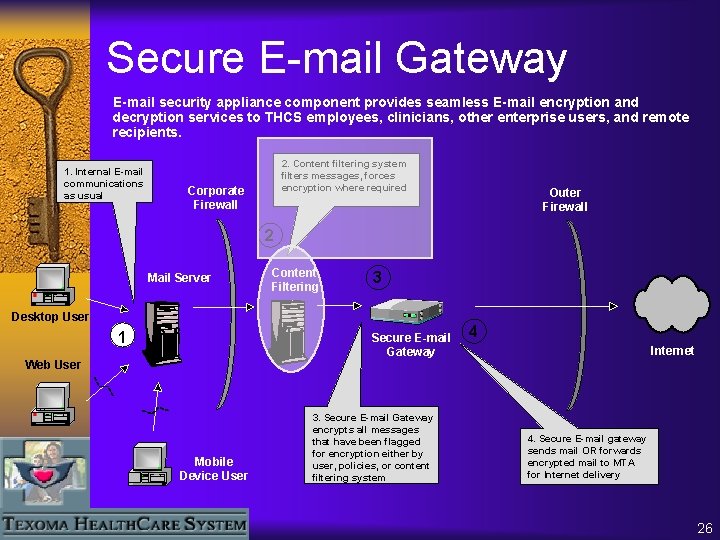
Secure E-mail Gateway E-mail security appliance component provides seamless E-mail encryption and decryption services to THCS employees, clinicians, other enterprise users, and remote recipients. 1. Internal email E-mail communications as usual 2. Content filtering system filters messages, forces encryption where required Corporate Firewall Outer Firewall 2 Mail Server Content Filtering 3 Desktop User 1 Secure E-mail Gateway Web User Mobile Device User 3. Secure E-mail Gateway encrypts all messages that have been flagged for encryption either by user, policies, or content filtering system 4 Internet ä 4. Secure. Mail Secure E-mail Gateway gateway sends mail OR forwards encrypted mail to MTA for Internet delivery 26

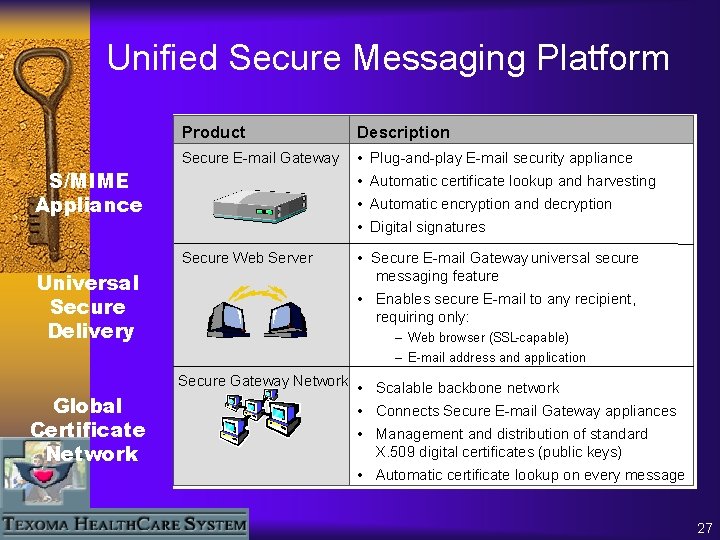
Unified Secure Messaging Platform Product Description Secur. E-mail Secure E-mail Gateway ™ • Plug-and-play Plug-and. E-mail security appliance S/MIME Appliance • Automatic certificate lookup and harvesting • Automatic encryption and decryption • Digital signatures Secure. Messenger™ Secure Web Server Universal Secure Delivery • Secure E-mail Gateway universal secure messaging feature • Enables secure E-mail to any recipient, requiring only: – Web browser (SSL-capable) – E-mail address and application Global Certificate Network Secure. Tier™ Gateway Network • Scalable backbone network • Connects Secure E-mail Gateway appliances • Management and distribution of standard X. 509 digital certificates (public keys) • Automatic certificate lookup on every message 27

The THCS Experience ¨ Authentication of Non-S/MIME Recipients – Establishing a pass phrase – Communicating the pass phrase 28

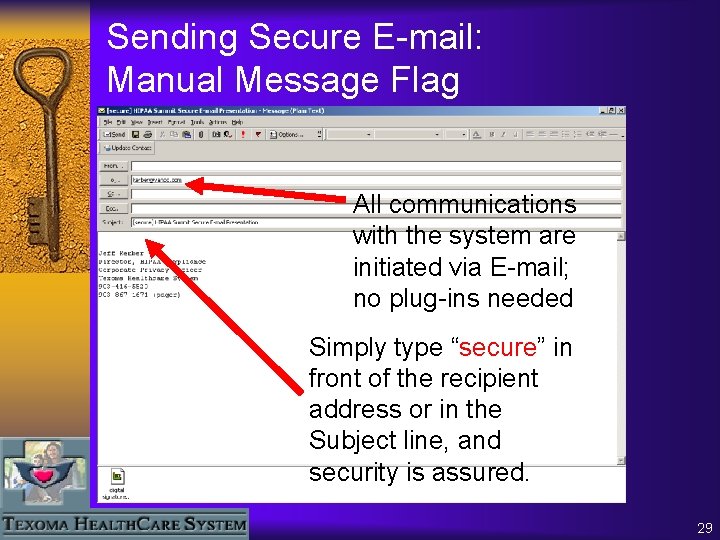
Sending Secure E-mail: Manual Message Flag All communications with the system are initiated via E-mail; no plug-ins needed Simply type “secure” in front of the recipient address or in the Subject line, and security is assured. 29

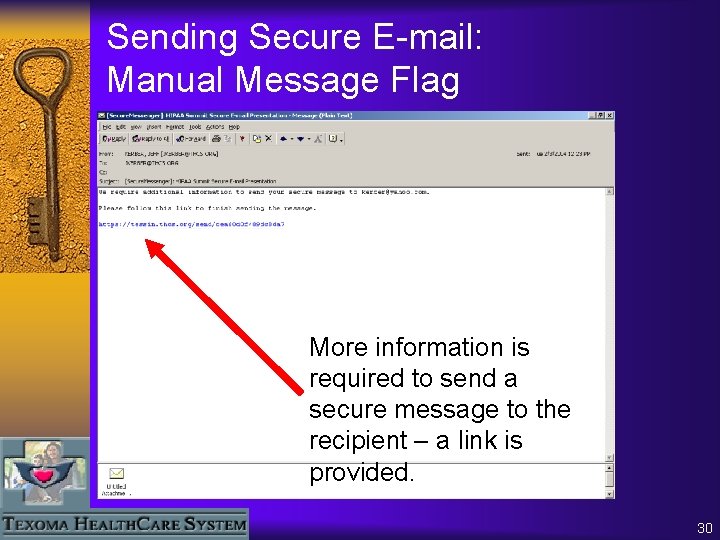
Sending Secure E-mail: Manual Message Flag More information is required to send a secure message to the recipient – a link is provided. 30

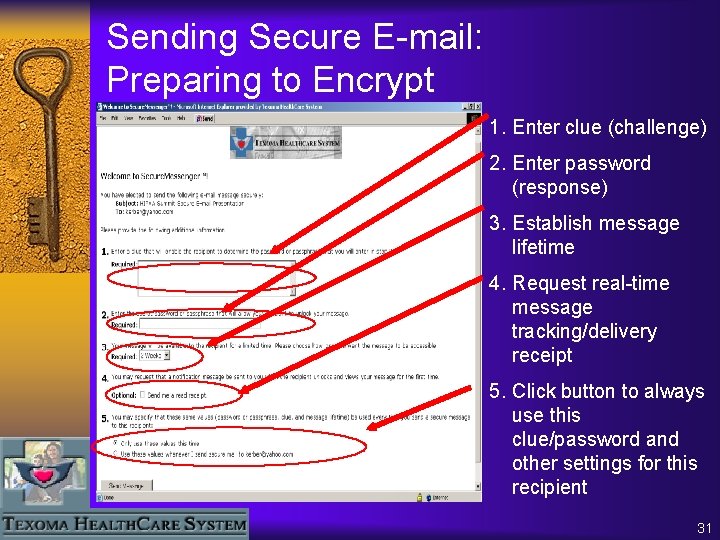
Sending Secure E-mail: Preparing to Encrypt 1. Enter clue (challenge) 2. Enter password (response) 3. Establish message lifetime 4. Request real-time message tracking/delivery receipt 5. Click button to always use this clue/password and other settings for this recipient 31

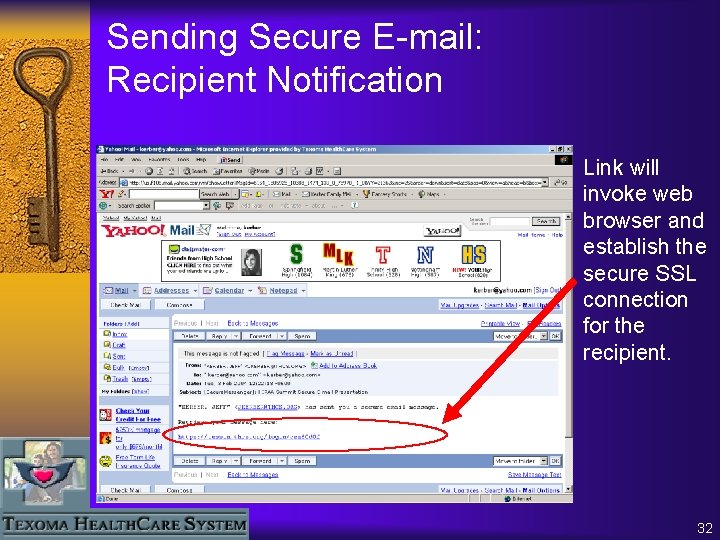
Sending Secure E-mail: Recipient Notification Link will invoke web browser and establish the secure SSL connection for the recipient. 32

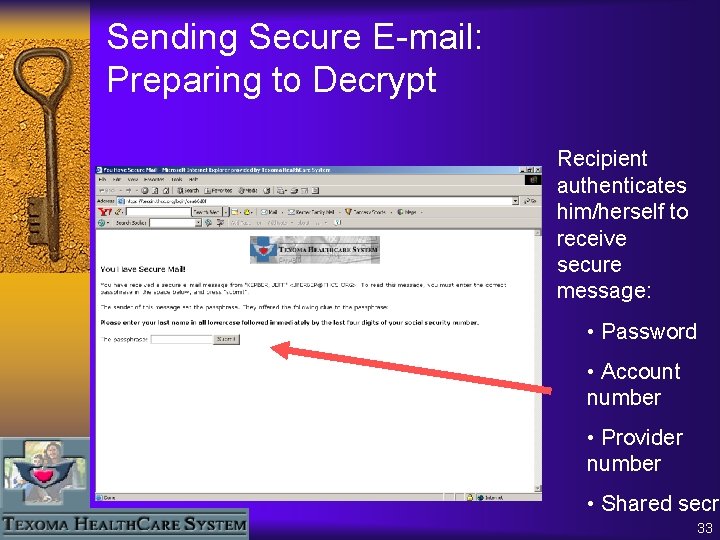
Sending Secure E-mail: Preparing to Decrypt Recipient authenticates him/herself to receive secure message: • Password • Account number • Provider number • Shared secre 33

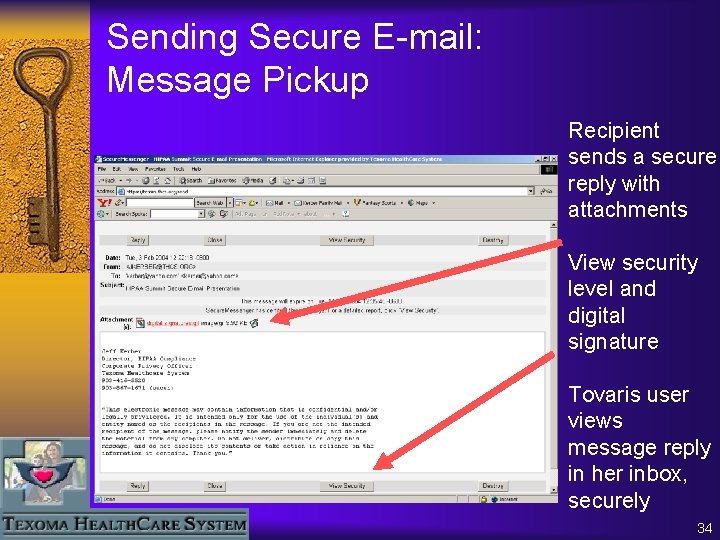
Sending Secure E-mail: Message Pickup Recipient sends a secure reply with attachments View security level and digital signature Tovaris user views message reply in her inbox, securely 34

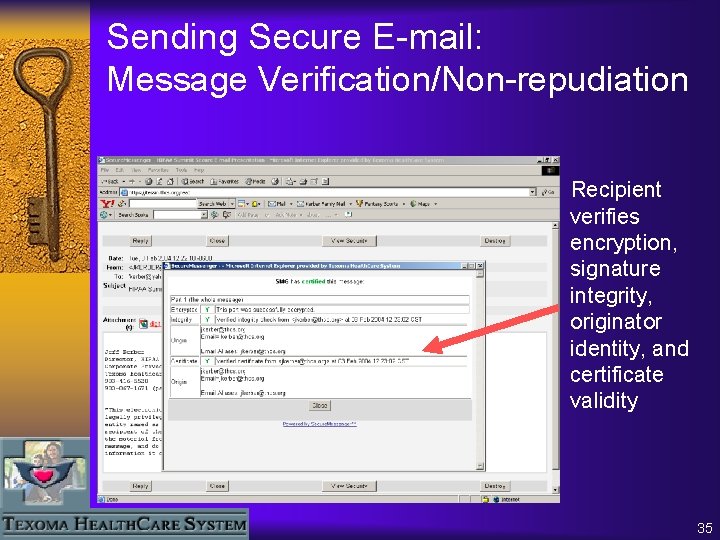
Sending Secure E-mail: Message Verification/Non-repudiation Recipient verifies encryption, signature integrity, originator identity, and certificate validity 35

Sending Secure E-mail: Replies by the Recipient • Recipient can reply securely back to sender, with unlimited file attachments. Original sender receives secure message in his own inbox when message has been replied to by recipient. Sending Secure E-mail: Message Tracking • Sender receives instant, secure notification by E-mail when Secure Messenger message has been retrieved by recipient. 36

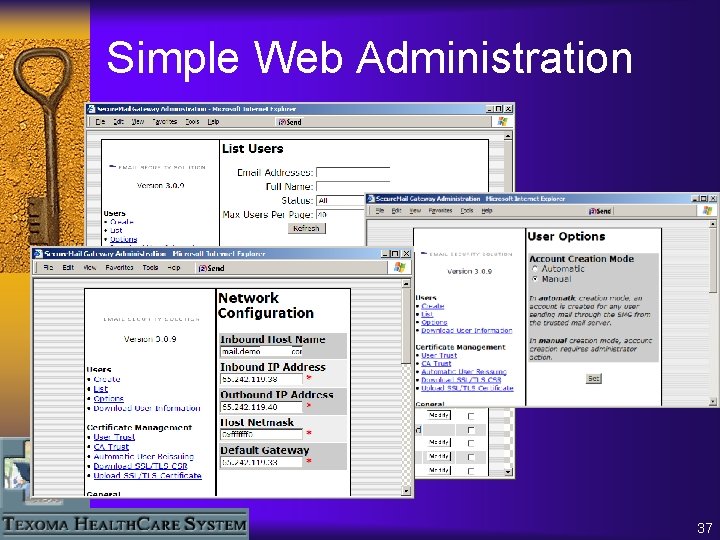
Simple Web Administration 37

The THCS Experience ¨ Usage and Maintenance – What maintenance? – Measuring usage – Assuring usage 38

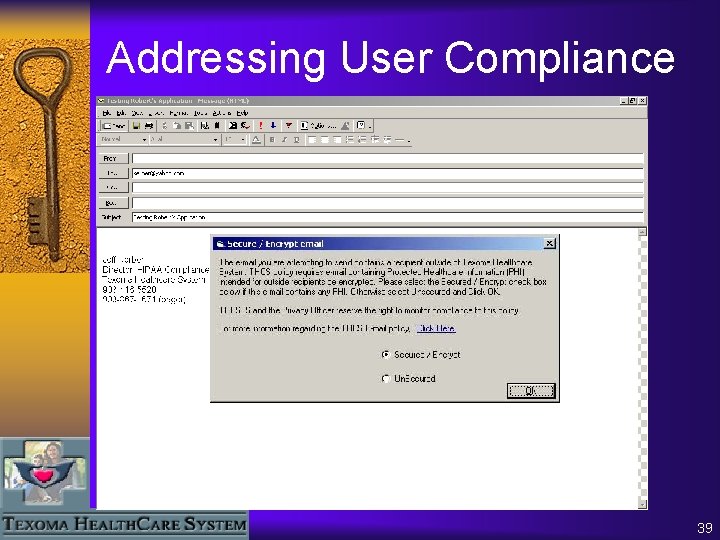
Addressing User Compliance 39

Addressing Three Secure E-mail Challenges x THCS users can’t use encryption—it’s too difficult! ü No client application or plug-in—Secure E-mail Gateway is a fully integrated E-mail security device x How do we send secure messages to recipients with no digital certificate? ü Secure Messenger Web delivery to all recipients with no remote storage of keys or messages x Manual certificate exchange is impossible to manage with our business partners. ü Certificate harvesting and Secure Network automates certificate distribution, retrieval and management activities 40

Key “Take-aways” ¨ ¨ ¨ “Reasonable effort” toward HIPAA compliance Turn-key E-mail security with little user overhead Able to send secure E-mail to any recipient Little to no ongoing management burden Able to find and retrieve recipients’ certificates by default on every message sent ¨ Able to integrate secure E-mail with mail system, antispam/virus and content filtering systems ¨ Plug into existing data sources for seamless web delivery and authentication 41

Secure E-mail: An Implementation Success Story How Texoma Healthcare System Identified & Addressed its Secure E-mail Requirements Presented by Jeff Kerber, Former Corporate Privacy Officer and HIPAA Compliance Director Texoma Healthcare System March 8, 2004 42